Security is a very wide and ever-evolving field. Cybersecurity encompasses topics as varied as network defense, data encryption, and identity and access management, just to name a few. Even for someone whose full-time job might be to keep up with the world of cybersecurity, it can be daunting to try to stay updated about the latest vulnerabilities and patches, let alone emerging threats and trends. For DevOps and engineering folks, it can feel downright impossible to make time to fully research security at every stage of the software development lifecycle.
As security "shifts left", developers, platform engineers, and other teams working in CI/CD pipelines are faced with keeping up with new threats and software updates, while they are also responsible for testing, deployment builds, and operations; truly owning their software through the production pipeline. This comes at the same time Infrastructure as Code, IaC, has become the predominant way people approach DevOps, putting that much more pressure on individuals. For some organizations, it might not be clear where team members can even turn to for help when juggling the security side of things.
Fortunately, there is a super team of developers and security folks dedicated to helping the whole world with application security. It's called OWASP.
OWASP: The Open Web Application Security Project
OWASP is a non-profit, volunteer-run organization with a mission that can be summed up as "No more insecure software." Their full mission actually reads:
As the world’s largest non-profit organization concerned with software security, OWASP:
- Supports the building of impactful projects;
- Develops & nurtures communities through events and chapter meetings worldwide; and
- Provides educational publications & resources,
in order to enable developers to write better software, and security professionals to make the world’s software more secure.
It basically boils down to "OWASP helps developers make sense of application security while helping everyone feel less alone in the fight."
For the rest of this article, we are going to look at the various components that make up OWASP and some specific tools they provide you can start using, for free, today!
Projects
OWASP Projects are open-source, volunteer-built repositories that deal with specific areas and tasks through the SDLC. Every project has a vision, roadmap, and actionable tasks. OWASP currently has over 200 projects listed on their site, and new project applications are submitted every week.
Every project has its own webpage and community of people building and maintaining the repo. Projects fall into one of five maturity levels:
- Flagship Projects
- Production Projects
- Labs Projects
- Incubator Projects
- Newly proposed Projects
Let's quickly take a closer look at each category. Not every project will be listed in this article, but you can always access the full list at owasp.org/projects/
Flagship Projects
Per their website: "The OWASP Flagship designation is given to projects that have demonstrated strategic value to OWASP and application security as a whole."
This group of projects has the widest adoption, and the most supporting articles, tutorials, and other resources. There are currently 18 Flagship projects that cover tools, documentation, code, and communication. While all OWASP projects are worth checking out, this short list of well-maintained projects is a great place to start investigating what OWASP has to offer. More on that later…
Production Projects
OWASP Production projects are "production-ready" projects. This designation is intended to showcase battle-hardened projects that can meet larger organization needs as well as more stringent standards. This level is meant to supplement and eventually supplant the Flagship maturity level, making it easier to understand the strategic importance and usefulness of any project.
This is the newest maturity level that has just been announced in October 2022. As of this writing, there are no projects that have made it through the new review process.
Lab Projects
OWASP Lab projects represent projects that typically are less widely adopted, due to their focus on specific development languages, architectures or use cases. For example, the project Java HTML Sanitizer has tremendous value for anyone running Java in their stack, but maybe not as valuable for folks running everything in Go or Rust.
There are 34 Lab projects covering all the various types of projects. While all projects are open for pull requests and help from the community, Lab projects tend to have smaller teams working on them and can be a place to really make some impact.
Incubator Projects
OWASP Incubator projects are referred to as an "experimental playground" where conversations are happening in the code and in docs as much as in Slack or in person at events. This group is the fastest evolving and the first formal maturity level. These projects can be very use-case specific or cover just a single problem set. A couple of examples that show the variety of projects are Snow, the over-the-shoulder reading prevention tool, and Barbarus, a smartphone-based secure login authentication solution.
There are 97 Incubator projects right now. Getting involved in one of these groups can mean defining the tools and helping harden the definitions of the problem the project is focused on over time.
Newly proposed Projects
All OWASP projects come from the community and are built by volunteers. All of them started with an idea or a conversation about solving a need in the community. Any OWASP member can submit a project. New projects are often added, sometimes weekly. There are a number of steps a project must go through before it gets to the Incubator stage and OWASP has laid out the requirements in their handbook. Right now there are over 90 projects that are on their way toward Incubator status, covering many topics.
Projects For All Parts Of The SDLC
With so many projects you might feel a bit overwhelmed trying to determine when and where you could leverage each project. The folks at OWASP have thought of this and provided a quick reference map to show what tools relate to what area of the software development lifecycle.
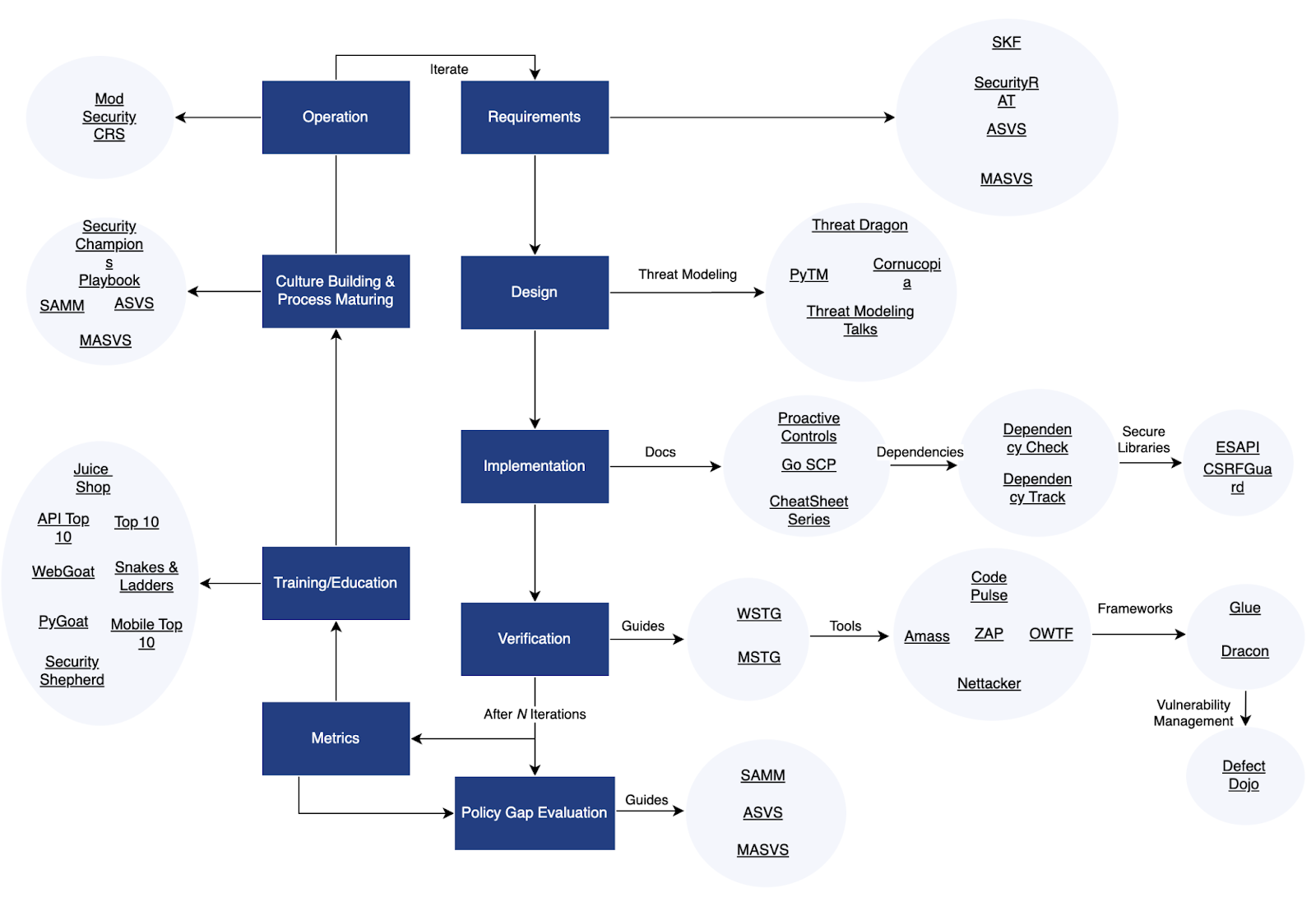
Are you in the design phase of a new project? They suggest checking out the Threat Dragon tool, PyTM threat model, as well as checking out their threat model toolkit talk. Ready to run your application in production? They suggest applying the ModSecurity Core Rule Set.
This helpful map is organized in part by how they relate to various requirements, as categorized by CRE.
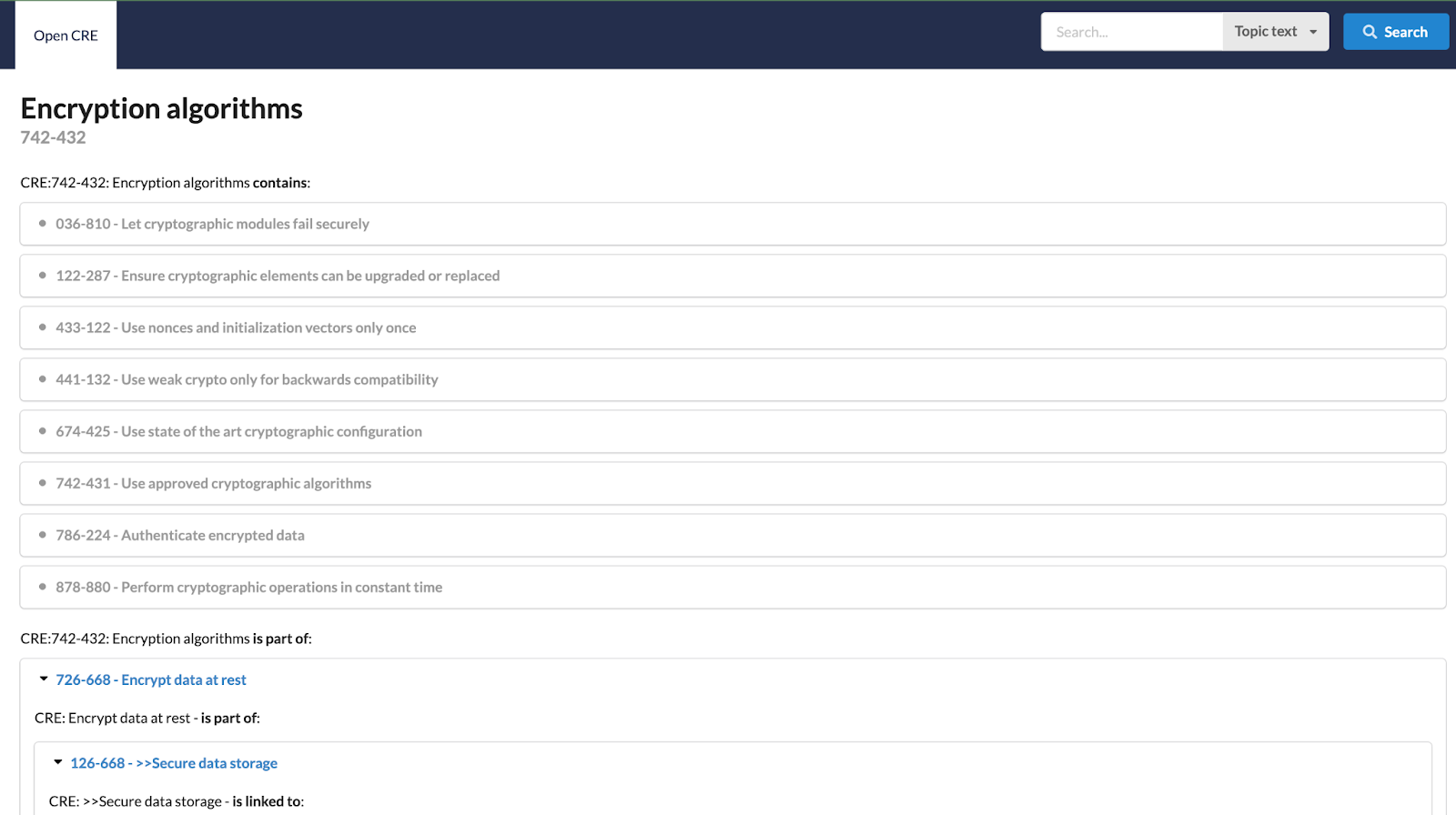
OWASP CRE
OWASP Common Requirement Enumeration, CRE, is a way to group content of standards and various guidelines for security concepts and concerns. OWASP explains it as "bringing together requirements, testing strategies, countermeasures, and links to existing repositories of threats and weaknesses".
There is a free searchable website https://www.opencre.org that attempts to link together various standards, like NIST, CWE, etc, in a coherent way. This 'meta level' categorization can really help clarify what each OWASP project is specifically addressing, as well as be a valuable research tool in and of itself to find interrelated vulnerabilities and security practices.
OWASP Communities and Events
Behind every awesome OWASP project there are groups of individual volunteers collaborating to make the world a better place. How each project communicates might vary, all rely on getting together in person from time to time in order to better talk through ideas and learn from one another. OWASP provides a couple of different paths to help organize these get-togethers, local chapter meetups, and larger-scale events.
Chapter Meetups
OWASP is a truly global community, with 269 active local chapters currently listed. These chapters are organized by 7 geographic regions:
- Asia
- Caribbean
- Central America
- Europe
- North America
- Oceania
- South America
While you might be out of luck if you are in Antarctica, there is a good chance you have an OWASP chapter near you. OWASP leverages the community coordination platform Meetup to make it easy to find, join and participate in your local chapter. Even if you are not an OWASP member you can still attend and ask questions. If there is one similarity between chapters, it is that these events are open and welcoming to all.
Every chapter is different and offers their own unique flavor of meetup, but typically there is a speaker and a chance to network with other security practitioners. Some have refreshments and some run full trainings and hackathons. Check out the events near you.
As a corporate support, GitGuardian is very proud to also host the French chapter's in-person meetup. We are happy to provide physical space for the community to meet in as well as supporting OWASP globally, providing resources to help bolster their mission.

Online
In addition to meeting in person, many chapters open up their meetups to folks from outside their geographic region through online meetups. Just as every chapter is independently organized, each of these online experiences is unique to the volunteer teams running the event. These are great events for folks who can not travel due to other obligations but still want to share their thoughts and opinions while learning about security.
Events
While regional chapters are awesome ways to connect and work with folks in the same geographic area, advancing education and project work, some discussions and sessions merit a larger get-together. That is where OWASP Events come into play. These larger events fall into three major categories.
- Global Events
- AppSec Days
- Partner Events
Global Events
These are the event equivalent of Flagship Projects, both in scale and maturity. These premier events bring together hundreds of professionals to participate in trainings, enhance their skills, make new connections, and make working security a more human experience.
In the past few years, their online events have been added, such as 2022's OWASP December Webinar. You can see the current lineup of OWASP global events on their website.
AppSec Days
While perhaps smaller in attendees and scope, regional AppSec Days are just as engaging events as their larger Global event siblings. AppSec days take on many shapes and forms, ranging from single-day events to week-long training and hackathons. These events are put on by local OWASP volunteers all over the world. These events are an awesome way to connect with the larger security community and see a variety of sessions and trainings.
Partner Events
Since security is a need across all organizations, it makes sense that OWASP would partner with various other conferences and events throughout the world. OWASP members can get discounted tickets and other benefits.
Education and Training
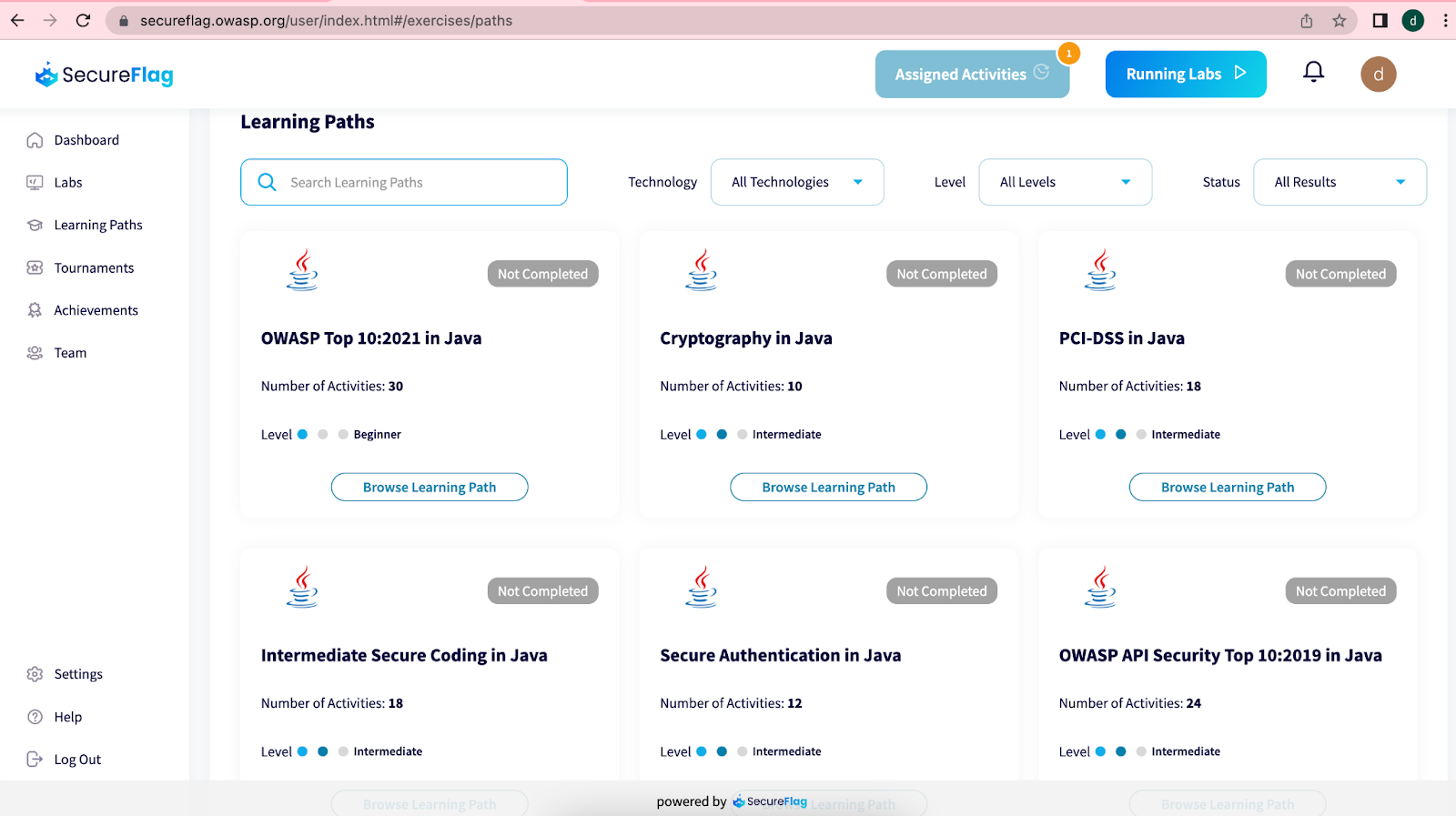
Sharing knowledge is at the center of OWASP's mission. It naturally follows that they would help formalize some paths to best learn about application security. There are a lot of trainings based on OWASP, though vendors like Udemy, just to name one platform. There are multiple training events run by OWASP as well. However, as someone who is new to OWASP, you will quickly discover that the largest and most accessible training collaboration is with the SecureFlag platform.
OWASP describes SecureFlag as a "training platform created for developers to learn and practice modern secure coding techniques through hands-on exercises." SecureFlag is completely free to OWASP members.
Four Ways To Get Started With OWASP
If you are completely new to OWASP or have never taken the time to investigate the community and what it has to offer, then you might be feeling a little overwhelmed right now. I had the same feeling of information overload when I first encountered OWASP. Like with all things in security, it is good to focus on one aspect at a time.
Here are my top four recommendations for projects to investigate as you get started with OWASP.
Top 10
It is likely that If you have come across one OWASP project it was the OWASP Top 10. The project exists as a standard awareness document, designed to help developers and web application security flood stay up to date on the most common vulnerabilities and related threats to web applications.

The Top 10 is far from just an ordered list. Exploring any of the topics listed unveils a lot of information about the factors comprising the vulnerability, an overview of the threats, references, and, most critically, what you can do to prevent the most commonly associated incidents.
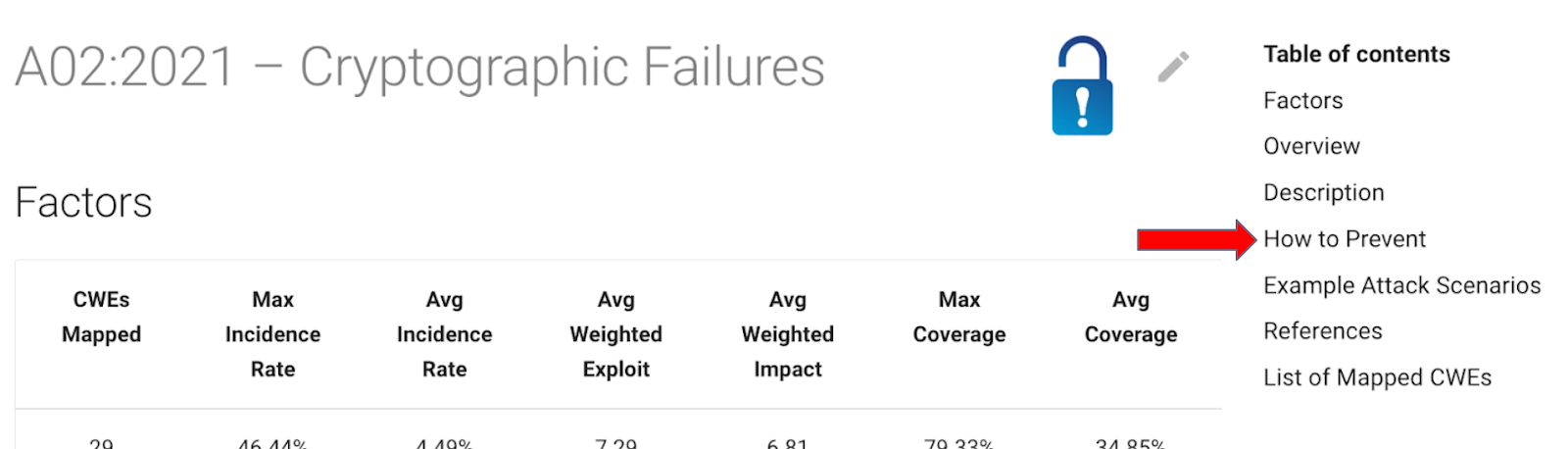
No matter what part of development or security you work in, familiarizing yourself with the OWASP Top 10 will help you build a baseline of knowledge and put you in a far better position to secure your application.
Cheat Sheets
The Cheat Sheet project provides simple, yet thorough guides for many areas of application development and security. Cheat sheets focus on "good practices that the majority of developers will actually be able to implement" rather than providing deeply detailed reports.

Cheat sheets can be a great way to begin your research into any area. For example, if you are getting started with Kubernetes, reading the Kubernetes Security Cheat Sheet will help ground you in security best practices while providing specific guidance for managing Kubernetes at every step of the software development lifecycle, including the initial investigation into the tooling and architecture.
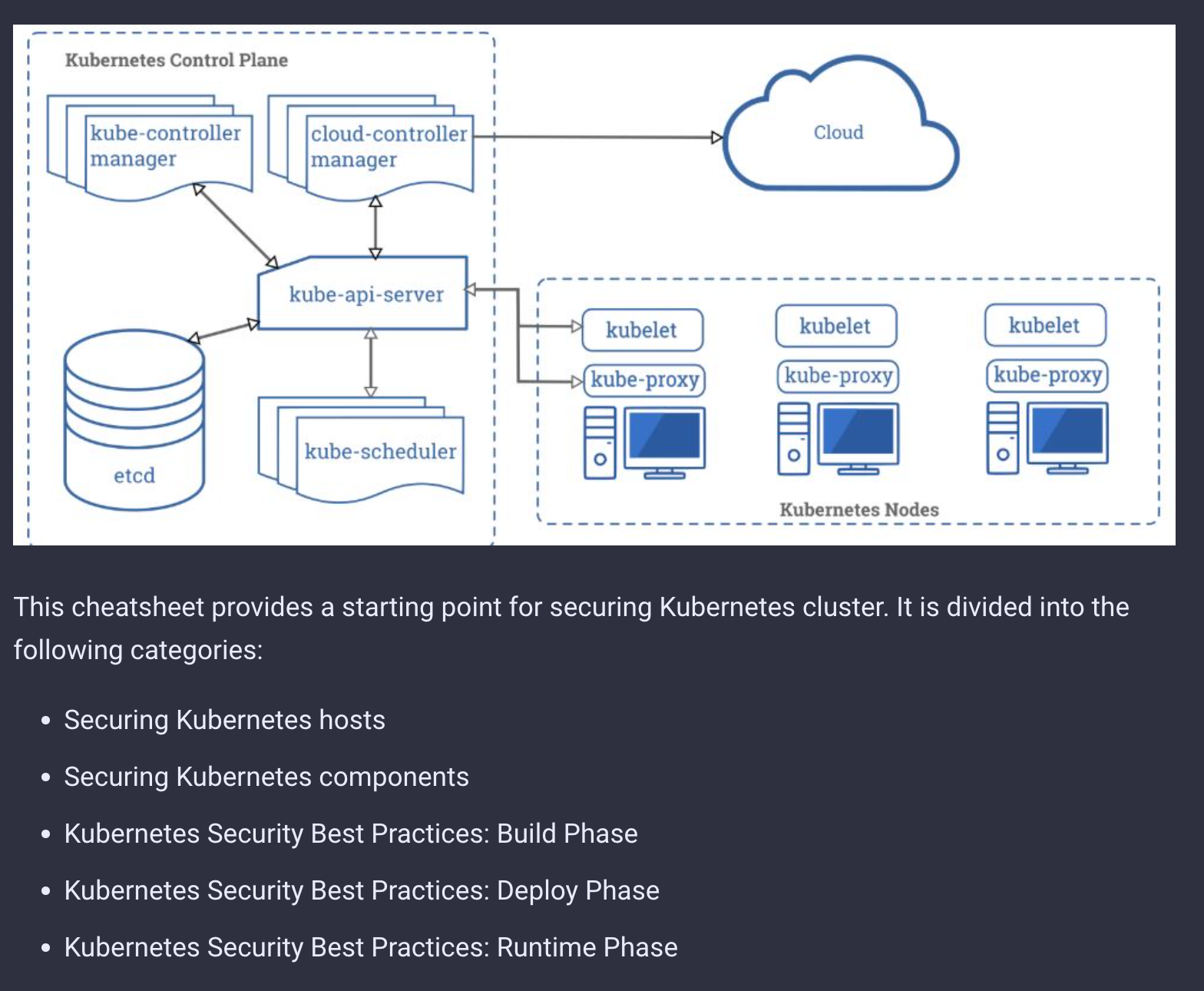
There are 78 cheat sheets available at this time, including one for each entry in the OWASP Top 10.
Goats and Juice Shop
Have you ever wanted to see what not to do when making a web application? Then you are in luck. The OWASP Goats are deliberately insecure applications for testing and training purposes. There are 2 Lab Project Goats we recommend checking out.
- WebGoat - Created as a project to ethically attack and test tools against.
- WrongSecrets - The Secrets Management-focused vulnerable/p0wnable app. Check out the webinar we recorded with the founder of the WrongSecrets project, Jeroen Willemsen.
There are other similar applications as Incubator or proposed projects. However, there is one insecure application that rises above the rest and is the only one that has earned Flagship status: Juice Shop
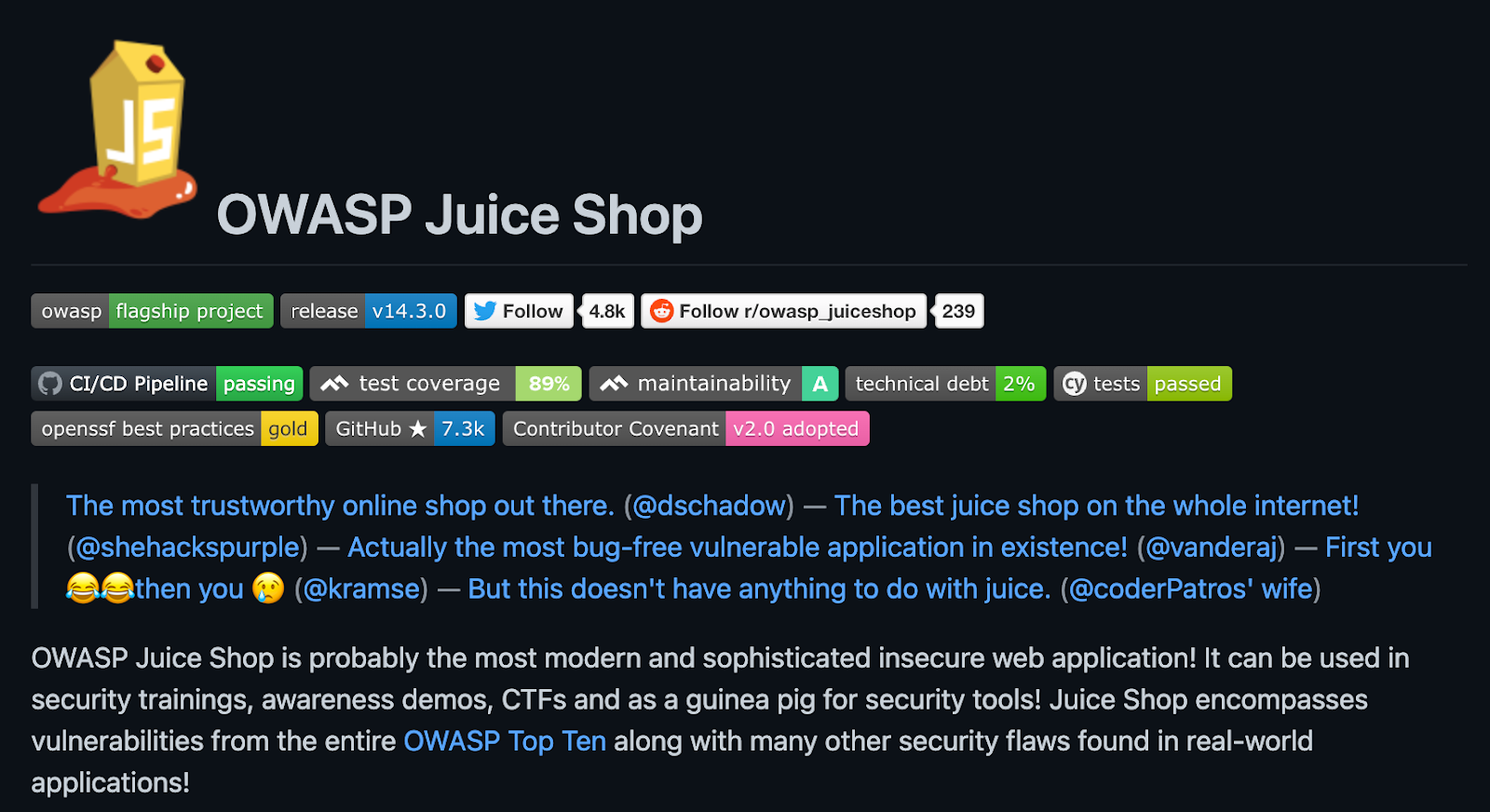
OWASP claims "Juice Shop is probably the most modern and sophisticated insecure web application!" This example application features vulnerabilities encompassing the entire OWASP Top Ten, among its many purposefully included flaws. You can get it running in containers in minutes and start testing to your heart's content. In case you are still at a stage where you are not sure where to start with security testing tools, that is where our last getting started suggestion comes in.
ZAP
ZAP stands for "Zed Application Proxy". OWASP claims ZAP is the world's most widely used web app scanner. It is a completely free and open-source tool anyone can run to test their applications for common vulnerabilities.
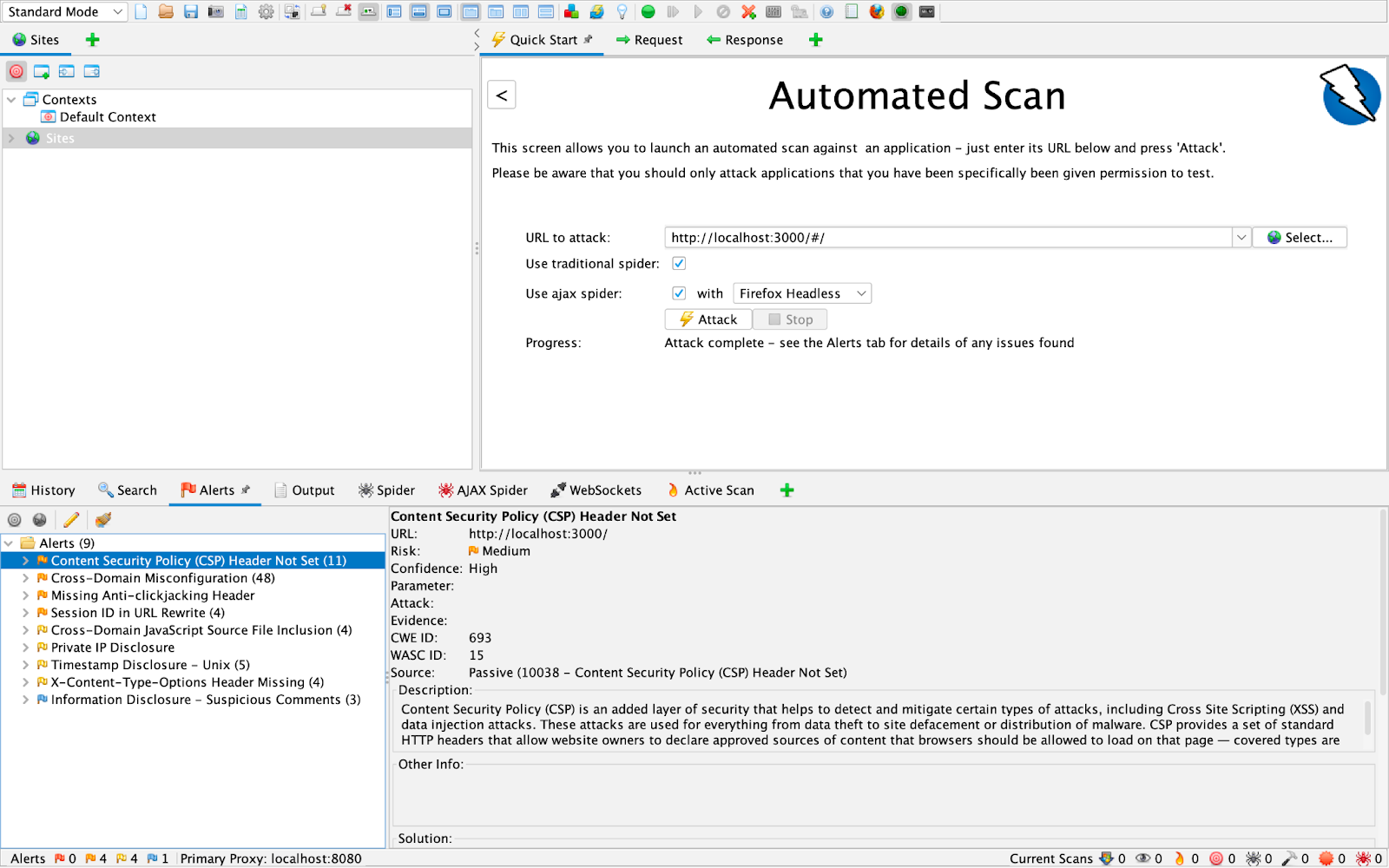
ZAP works by actively attacking an application; attempting a list of common exploits. It should only ever be run against applications you have full and complete permission to attack, such as Juice Shop. Speaking of that, attacking a local instance of Juice Shop reveals over 70 individual issues across 9 alert categories. Each alert is full of valuable information you can cross-reference with opencre.org and other standard models.
There is an awesome getting started guide and you can't beat the price, especially as this one tool can help you identify and tackle the most common vulnerabilities posing a risk to your applications.
You Are Not Alone In The Security Fight
GitGuardian Stands Behind Open Source
GitGuardian fully believes in the mission of OWASP. We are a Gold Corporate Supporter, financially backing the OWASP mission. In addition to hosting the Paris meetup, as part of our sponsorship, we support a few specific projects. We would like to give mention of them here.
1. OWASP WrongSecrets
2. OWASP Cheat Sheet Series
3. OWASP Security Knowledge Framework
4. OWASP Top Ten
5. OWASP Austin (Chapter)
GitGuardian also strives to provide open-source tools wherever possible, making it easier for open-source and small teams to get the tools they need to make their applications safer. You can read more about these open-source tools as part of the GitGuardian Labs. Our open source tools are also listed on the OWASP free for open source application security tools page.
OWASP Is There For You
No matter what part of the SDLC you focus on, or how long you have been working with application security, OWASP is there to make sure you have the right tools and the right information to stay safe. Beyond their awesome projects and tools, OWASP is a way to connect with others in the same boat on the journey to better security, helping many groups meet locally, at a larger event, or online.
If you are at the beginning of your journey or if there is an area you want to deep dive, be sure to take advantage of the training opportunities they make available. And if you are not sure where to start, then I would recommend going over the OWASP Top 10, as it serves as the baseline for many other OWASP projects.
We are all in security together, there is no reason you have to go alone.








