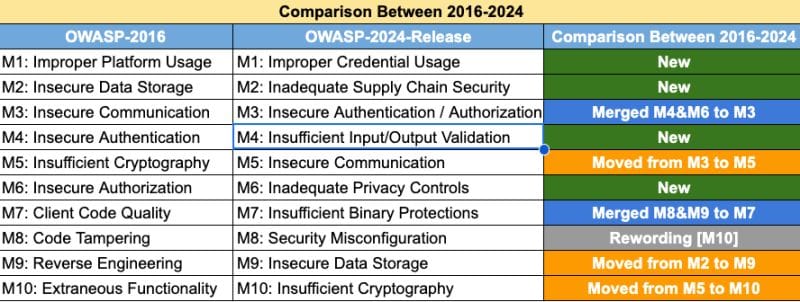
Recently, The Open Worldwide Application Security Project (OWASP) updated its Top 10 Risks for Mobile Applications for the first time since 2016.
Guess which security risk made it to the top this time? "Improper Credential Usage.”
This is not anecdotal. It’s a wake-up call to mobile app providers about the danger of hardcoded credentials and bad secrets hygiene in general.
Mishandling the secrets your application uses, especially in mobile apps, can lead to devastating security breaches. Let's take a closer look at this new top focus for securing our applications and what we can do together to address these concerns.
The Growing Threat of Improper Secrets Handling
Improper Credential Usage occurs when secrets like passwords or tokens are not properly secured, making them vulnerable to theft by attackers. Mobile apps, in particular, are notorious for leaking secrets. According to research from CyberNews, over 50% of mobile apps on platforms like Google Play Store have hardcoded secrets, which means these sensitive pieces of information can easily be uncovered by malicious actors.

If we look at the definition provided by OWASP, we quickly understand why this risk is particularly concerning:
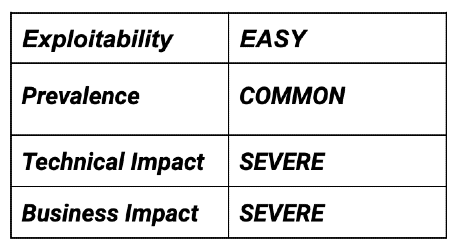
When secrets are exposed, attackers can use them to gain unauthorized access to services, data, or even entire systems. This makes secrets management a paramount concern for app developers and security teams alike.
Why Secrets Are the Primary Target
Secrets are attractive targets for attackers because they grant direct access to critical systems. Unlike other vulnerabilities that require further exploitation, once an attacker gains access to an API key or password, they often have a clear path to valuable resources.
For instance, hardcoded API keys in mobile apps can be extracted via static analysis tools and used to make unauthorized API requests. This not only compromises user data but can also incur financial losses, especially if these keys are tied to services that bill based on usage.
Client-Side Secrecy is Hard
One key point in understanding secrets management is that client-side secrecy is practically impossible. No matter how well secrets are obfuscated or encrypted in a mobile app, attackers with enough resources can reverse-engineer the app and retrieve them. This is because secrets, at some point, must be available in the app's memory for use. Through dynamic analysis, attackers can retrieve these secrets and exploit them.
As a result, the only safe way to manage secrets is to keep them off the client side entirely. Instead of embedding API keys or credentials in the app, developers should move this sensitive information to the backend, where they have more control over access and security.
Best Practices for Secrets Management
To address the challenge of secrets leakage, development teams must implement a range of best practices:
- Never Hardcode Secrets: Secrets should never be stored directly in the app's code. This includes API keys, authentication tokens, and any other sensitive data. Hardcoding secrets is one of the most common ways they are leaked and can lead to significant security breaches.
- Use Secure Storage APIs: For user secrets (e.g., passwords, tokens), developers should use secure storage mechanisms provided by mobile operating systems. For example, iOS offers the Keychain, and Android has the Keystore. These APIs allow for secure storage and access control of sensitive data on the device.
- Move Secrets to the Backend: Instead of handling secrets on the client side, mobile apps should use server-side logic to manage API keys and other sensitive data. By placing these operations on the backend, the risk of leaking secrets is drastically reduced.
- Rotate and Invalidate Secrets Regularly: Even with proper secrets management, secrets should be rotated regularly, and compromised keys should be invalidated immediately. This ensures that if an attacker does gain access to a secret, they cannot use it indefinitely.
- Certificate Pinning: When secrets are sent to the app at runtime, developers should use certificate pinning to ensure that the communication is secure. This adds an extra layer of protection by verifying the server's identity during the connection.
- Implement Secrets Detection across the SDLC: Managing secrets in the development lifecycle inevitably involves mistakes and leaks at some point. OWASP highlights the need for “a comprehensive security testing process.” It needs to enforce multiple layers of detection at the commit, push, and build stages and allow streamlined remediation in case of an incident.
It’s crucial to keep in mind a hardcoded secret doesn’t need to reach production to be a high-impact vulnerability. GitGuardian’s secret detection platform is the best tool to take control of an organization’s secrets security.

The Consequences of Leaked Secrets
When secrets are leaked, the consequences can be severe. Attackers can use exposed credentials to access sensitive data, manipulate business logic, or even take over entire systems. For instance, if an API key linked to a payment system is leaked, attackers could initiate fraudulent transactions, resulting in financial losses for both the business and its customers.
“Adversaries can exploit vulnerabilities in both hardcoded credentials and improper credential usage. Once these vulnerabilities are identified, an attacker can use hardcoded credentials to gain unauthorized access to sensitive functionalities of the mobile app. They can also misuse credentials, for instance, by gaining access through improperly validated or stored credentials, thereby bypassing the need for legitimate access.”
Moreover, leaked secrets can compromise the integrity of a mobile app and lead to costly legal and reputational damage. For example, if a healthcare app leaks API keys that allow access to patient data, it could result in significant regulatory fines and erode customer trust.
Secrets Detection Tools
To help address the problem of secrets leakage, tools like GitGuardian’s Secret Detection Platform have become essential for modern app development. These tools scan code repositories, CI/CD pipelines, and production environments for exposed secrets, helping teams catch vulnerabilities before they are exploited.
GitGuardian’s platform allows for real-time monitoring of code changes, ensuring that secrets are not accidentally hardcoded during the development process. By integrating such tools into the development lifecycle, organizations can greatly reduce the risk of secrets leakage.
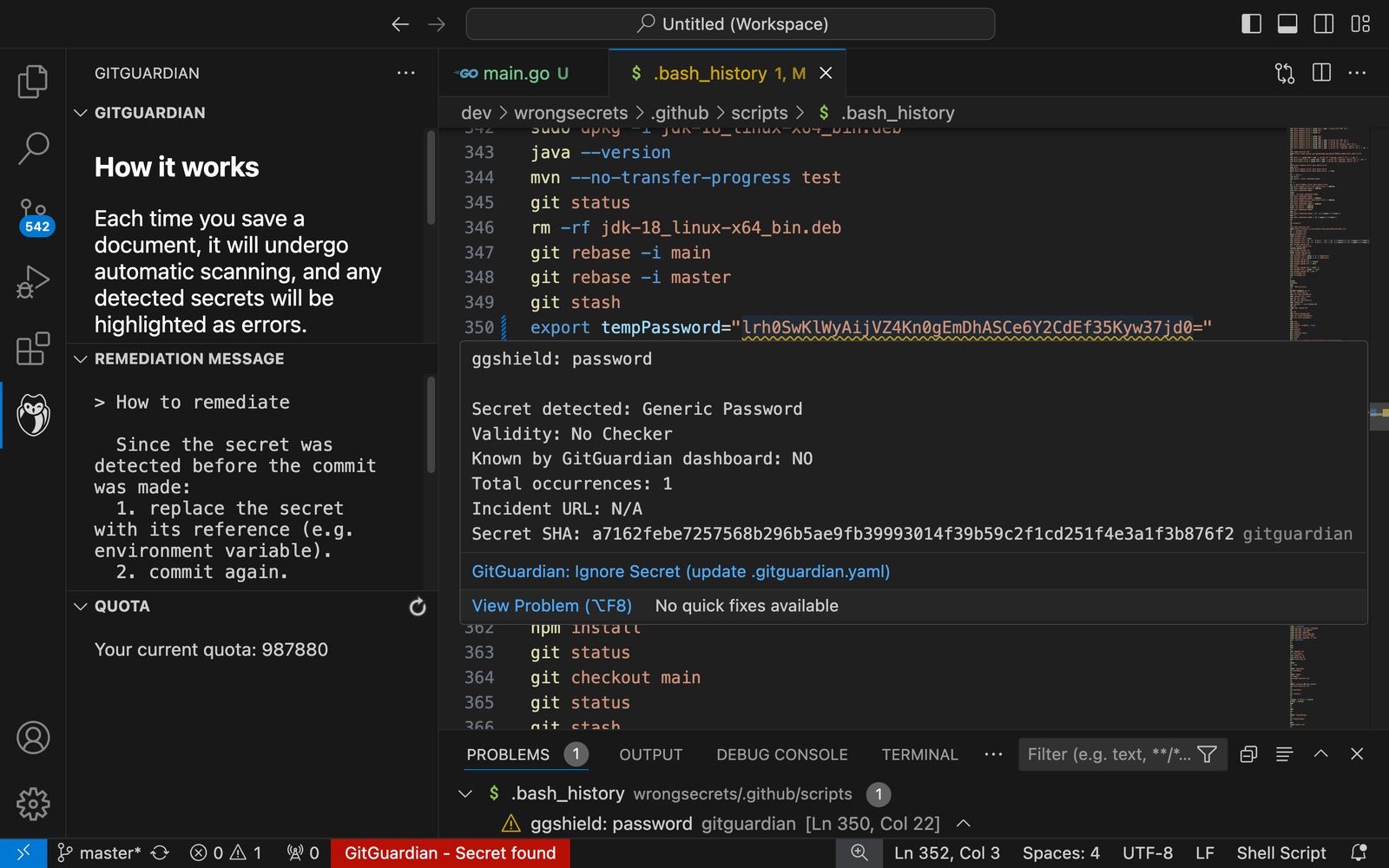
Even better, GitGuardian offered tools for developers to help them prevent ever adding a hardcoded credential in the first place. Developers can either install ggshield, the GitGuardian CLI, and install a pre-commit Git hook, which will scan their work when they try to commit their code changes and halt the Git workflow to let them fix their issue right then and there before it gets pushed into the shared Git history. Developers using VSCode can now install the GitGuardian VSCode extension and get a warning they have added a plaintext secret when they save the file, making it even easier to address secrets sprawl.
Secrets Security is a Journey We Are All On
Secrets management is not just a technical issue; it’s a critical security challenge that can have far-reaching consequences if not handled properly. By understanding the risks of improper credential usage, implementing best practices for securing secrets, and using tools designed to detect leaks, organizations can protect their sensitive data and reduce the likelihood of costly breaches.
As cyberattacks and breaches continue to make headlines, securing secrets is the most essential protective strategy to keep organizations and systems safe. Thank goodness OWASP volunteers are there to help us keep up with the ever-shifting cybersecurity landscape. GitGuardian is right there in the fight with you, helping you eliminate secrets sprawl at every stage of the software development lifecycle. Let's get a handle on secrets security together.