Senior security leaders in banking and financial services operate in a continuous translation role. Security organizations generate high volumes of alerts, findings, and technical metrics. Boards of directors, audit committees, and supervisory authorities evaluate performance through a different lens: enterprise risk, regulatory exposure, and operational resilience. Alignment depends on whether security activity can be translated into those terms in a credible and repeatable way.
The board's role is to define risk appetite, allocate capital, and ensure the institution can continue operating through disruption. Security teams must demonstrate measurable influence over loss exposure, supervisory confidence, and service continuity when thinking about selecting or implementing a specific technology or program. Controls, architectures, and tooling are inputs. Reduced likelihood of material loss and improved resilience are the outcomes that security leadership should strive to achieve.
In regulated financial institutions, compliance frameworks often serve as the initial proxy for risk management. They provide defensibility and a shared vocabulary in environments where the consequences are material. We can call this governance, and it shows that risk is intentionally managed, not just that security work is being performed.
Governance maturity develops when compliance evidence is consistently connected to changes in impact. That connection increasingly runs through identity governance and secrets security.
What Audit and Control Failures Have Cost Financial Institutions
Let's take a look at the realities that keep enterprise leaders up at night. The financial consequences of regulatory enforcement clearly show what is at stake:
- OCC (2020) – Capital One Bank
An $80 million civil money penalty was imposed for information security deficiencies and noncompliance with "Interagency Guidelines" following a major unauthorized access incident. - FCA (2018) – Tesco Personal Finance
A £16.4 million fine after a cyber attack enabled unauthorized transactions. The FCA cited deficiencies that exposed customers to avoidable harm and highlighted weaknesses in access controls and monitoring. - SEC (2022) – Morgan Stanley Smith Barney
A $35 million penalty related to failures to safeguard customer personal information, with regulators pointing to deficiencies in protective controls and oversight mechanisms. - Poland DPA via EDPB (2025) – mBank
An administrative fine of €928,498.06 related to GDPR Article 34 violations.
Across jurisdictions, the pattern is consistent. Regulatory cost increases when unauthorized access occurs, when access privileges are weakly governed, or when institutions cannot demonstrate that controls operate effectively and consistently over time. The absence of evidence often matters as much as the presence of technical safeguards.
Why Risk Framing Determines Security Credibility
Vulnerabilities, misconfigurations, and exposed credentials are operational observations. Security professionals need to articulate how those observations translate into potential losses, how likely those losses are to occur, and what factors influence their magnitude.
Boards, regulators, and auditors all focus on loss outcomes. Their concerns center on customer harm, financial impact, service disruption, regulatory notification thresholds, and reputational damage. Security updates gain relevance when they clearly show how changes in tools and programs drive those risks down.
Risk models, such as Open FAIR, provide a shared structure for this conversation by defining risk as "the probable frequency and probable magnitude of future loss." Frequency is influenced by threat activity and the strength of resistance measures you have implemented. Loss magnitude is shaped by reachability, privilege concentration, and the speed and effectiveness of containment.
Within financial institutions, identity failures frequently act as the enabling mechanism for loss. This is magnified when you consider the scale of non-human identities (NHIs) outnumber humans: at least 80:1. Exposed credentials and poorly governed non-human identities provide direct access paths into systems that process payments, store customer data, or support trading, clearing, and settlement activity.
Auditors assess whether controls operate consistently and whether their operation plausibly reduces loss frequency or magnitude. Evidence accumulated over time forms the basis for that assessment, not isolated point-in-time attestations. And that reassurance, that over time risk has and will go down, is exactly what the board wants from security.
How Financial Regulation Reinforces Identity and Secrets Governance
Regulations, especially for the financial services industry, emphasize outcomes rather than prescribing specific technologies. Across jurisdictions, supervisory expectations repeatedly focus on understanding, controlling, monitoring, and recovering access pathways.
In the United States, Gramm-Leach-Bliley Act (GLBA) and the Federal Reserve's Interagency Guidelines Establishing Information Security Standards tie program adequacy to safeguards that protect customer information from unauthorized access.
SEC Regulation S-P: Privacy of Consumer Financial Information and Safeguarding Customer Information formalizes expectations for preventing and responding to unauthorized access within SEC-regulated entities.
Some states have their own regulations, such as New York State Department of Financial Services 23 NYCRR Part 500, which establishes explicit requirements around access privileges, authentication, governance, and ongoing monitoring.
Response speed is a measurable regulatory variable. The OCC, FDIC, and other bodies have a 36-hour notification rule. Credential validity duration is part of the determination of whether some thresholds are crossed and whether incidents escalate into reportable events.
Operational resilience frameworks expand the scope further. European regulations, like DORA and GDPR, emphasize tested controls and third-party access governance. UK operational resilience guidance from the FCA explicitly links identity failures to the disruption of important business services. Comparable expectations globally appear in Singapore's MAS TRM, Australia's APRA CPS 234, Canada's OSFI Guideline B-13, and the global industry's SWIFT Customer Security Programme.
Across regions and countries, access governance and identity control effectiveness remain in scope even when terminology varies. The question remains consistent: can the institution demonstrate effective control over who or what can access critical systems, and how quickly that access can be withdrawn when conditions change?
The Structural Growth of Non-Human Identities in Banking
The emergence of non-human identities, and the scale and rate at which we are deploying them, represents a major shift in access governance across financial institutions. Designed for machine-to-machine interaction, these identities enable applications, services, automation, and APIs to access systems without human involvement. They underpin payment processing, reconciliation, trading operations, cloud infrastructure, and third-party integrations that require reliable, automated access at scale.
These identities authenticate using secrets such as API keys, tokens, certificates, and service account credentials. As automation expands, so does the number of secrets required to support it. This growth is often decentralized and poorly documented, leading to secrets sprawl across code, pipelines, configurations, and cloud services.
Each secret represents an access path. When exposed, attackers can gain machine-level access without compromising a human account, often bypassing controls designed for interactive users. NHIs lack direct human oversight, so misuse is much harder to detect. In otherwords, "Attackers are not breaking in, they're logging in."
As the number of NHIs increases with every new deployment, mismanagement becomes more likely. Secrets are frequently long-lived, over-permissioned, or reused. Some are orphaned, with unclear ownership and no clear path to revocation or remediation. Boards recognize this as a governance tradeoff between efficiency and risk. Auditors assess whether institutions can inventory access mechanisms, explain the scope of any access, and revoke access quickly when needed. This requires proofs throughout each NHIs lifecycle. Gaps in visibility and control increasingly surface as audit findings.
Connecting NHI Governance to Enterprise Risk and Resilience
Effective alignment depends on presenting secrets and non-human identity risks in a structure that aligns with regulatory expectations. Again, we can look to guidance from Open FAIR. Four dimensions consistently resonate with boards, auditors, and supervisors.
Exposure channels - Secrets appear across repositories, configuration files, CI/CD pipelines, collaboration platforms, ticketing systems, documents, containers, and cloud services. This distribution broadens the attack surface and complicates assurance.
Time - Risk increases with the duration a credential remains usable after exposure. Time-to-revoke becomes a practical proxy for incident response effectiveness and regulatory exposure.
Identity sprawl - Non-human identities expand faster than human identities, receive less routine review, and frequently hold elevated permissions. Governance frameworks increasingly associate this sprawl with operational resilience and third-party risk.
Containment - Loss magnitude depends on how quickly access can be revoked and how accurately the impact scope can be determined. Delays increase financial, regulatory, and reputational consequences.
Mapped to a risk model, exposure and sprawl influence resistance strength, time influences loss event frequency, and containment influences loss magnitude. Boards can evaluate these relationships. Auditors can test the associated controls.
Translating Security Activity Into Risk Reduction
Security activity supports governance and proves risk management when it directly addresses loss drivers rather than operational artifacts.
Eliminating exposed credentials reduces the probability that threat activity escalates into loss.
Shorter credential lifetimes reduce misuse frequency.
Constrained permissions limit potential impact.
Faster detection and revocation influence both frequency and magnitude.
When remediation is expressed in these terms, it demonstrates proactive risk management rather than reactionary operational cleanup. Reduced high-risk exposure, improved revocation speed, and defined accountability for non-human identities provide evidence that auditors can validate.
The history of regulatory enforcement, particularly in the financial industry, shows that supervisors examine these same outcomes when assessing control effectiveness, regardless of the underlying tooling.
Aligning GitGuardian Signals With Board and Audit Expectations
From an auditor or regulator's perspective, security programs are evaluated by their ability to produce credible, repeatable evidence of risk management. The goal is to assess whether access risk is actively governed, whether controls operate consistently, and whether trends demonstrate sustained improvement. GitGuardian supports this alignment by translating secrets exposure and NHI risk into signals that map directly to governance expectations.
At the foundation is broad coverage across exposure channels. GitGuardian continuously monitors for leaked secrets in source code repositories, both publicly on GitHub and private repos on any major provider. The platform also connects with CI/CD pipelines, collaboration platforms, ticketing systems, and other systems. This visibility enables institutions to demonstrate where authentication artifacts are monitored and where residual gaps remain, a prerequisite for audit assurance. This problem of secret sprawl is, unfortunately, only getting worse.
GitGuardian NHI Governance platform adds contextual enrichment by associating secrets with repositories, services, environments, and identity types. This context clarifies reachability and privilege concentration, allowing governance stakeholders to understand not just that a secret exists, but what systems it enables and why it matters from a risk perspective.
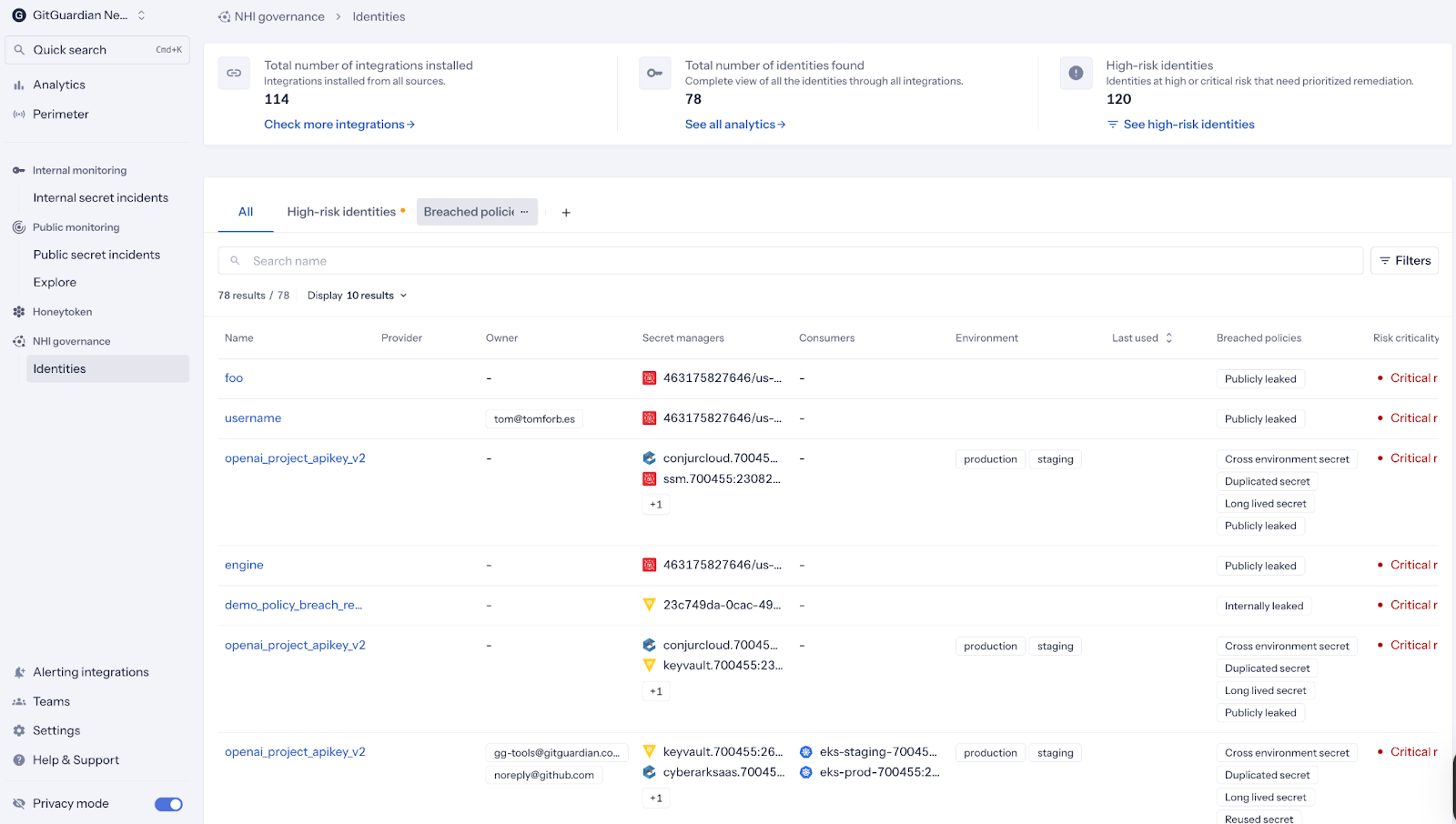
GitGuardian's new Risk Score classification capability, driven by machine learning, helps teams quickly distinguish between low-risk artifacts and credentials that represent active access paths. This supports prioritization based on potential loss impact rather than alert volume.
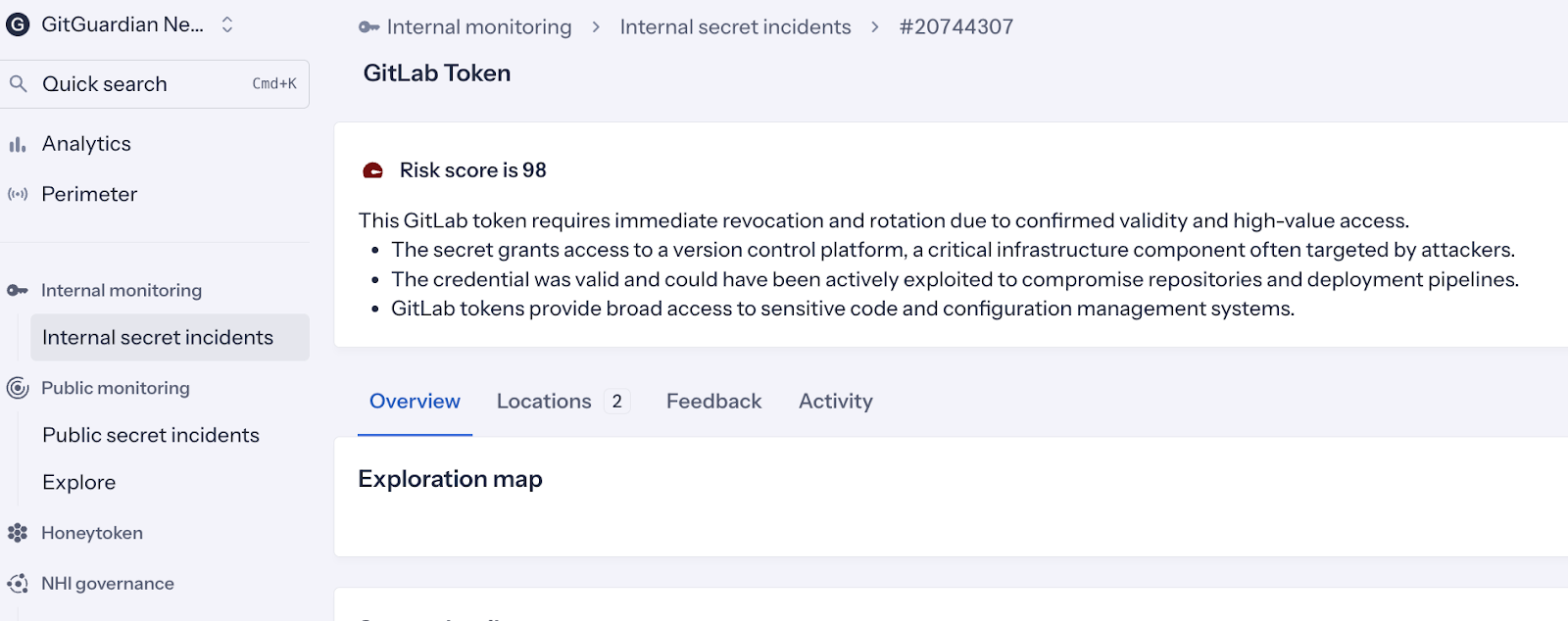
Risk-based prioritization and remediation signals further align security activity with governance outcomes. GitGuardian analytics provide metrics such as "Median time to remediate," which are measurable indicators of response effectiveness, particularly when notification thresholds depend on response speed. Workflow integration and ownership assignment reinforce accountability and support audit traceability.
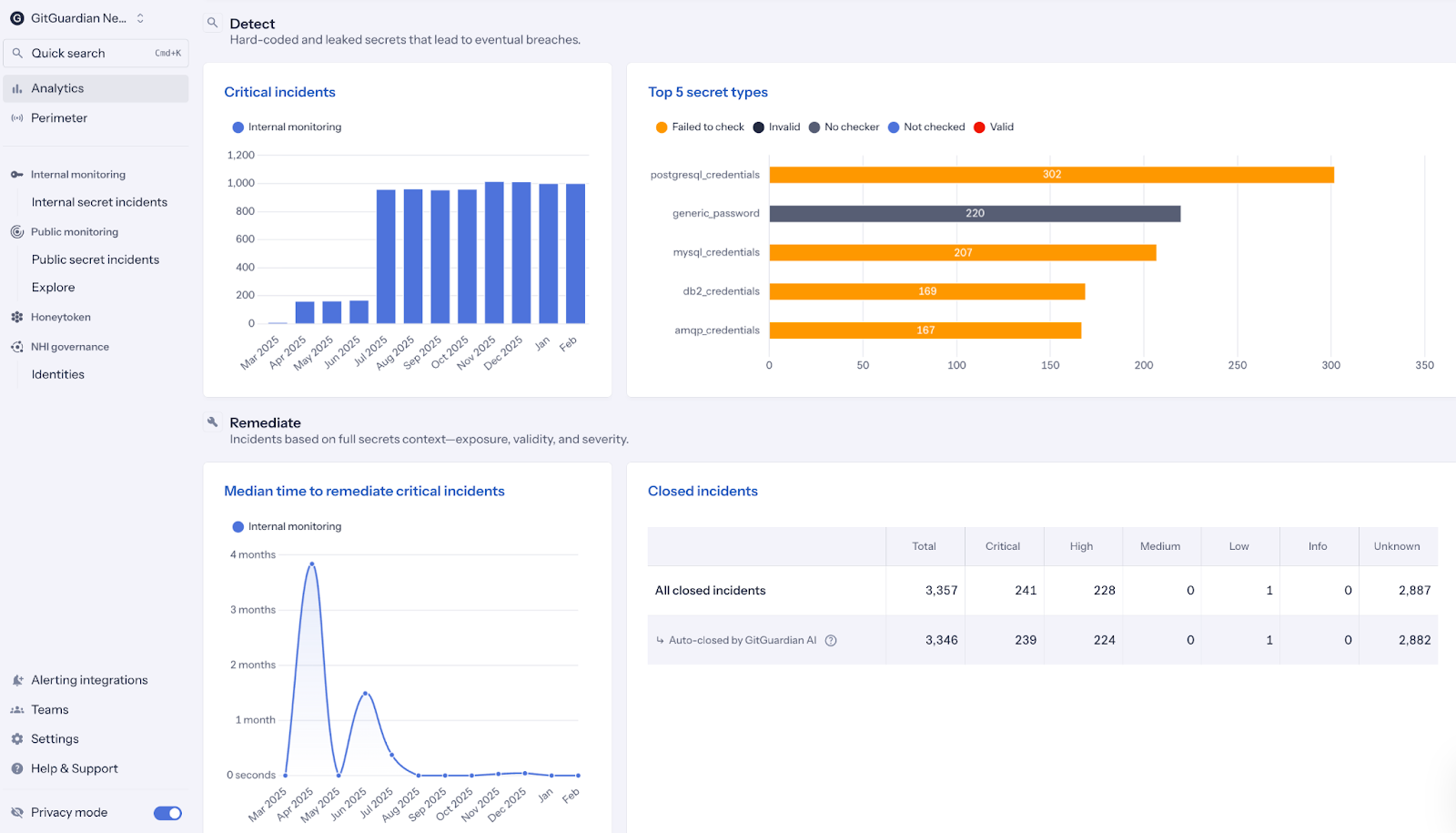
Over time, trend reporting converts operational activity into governance artifacts. Boards see directional risk reduction, auditors observe consistent control operation, and supervisors gain confidence that access risk related to non-human identities and secrets sprawl is actively managed.
In this way, GitGuardian functions as both a detection platform and a governance enabler, producing evidence that aligns security operations with enterprise risk oversight.
Communicating Security Risk With Boards and Auditors
Board reporting focuses on movement in risk drivers. Expecting exposure monitoring to expand and credential validity windows shrink. High-risk identities should get more controls implemented around them. And the evidence always needs to be available for review.
Audits emphasize structure and consistency. They need evidence that controls are in place and operate as designed. Trends from audits demonstrate improvement over time.
Financial services enforcement history demonstrates the cost of access control failures. Identity and secrets governance represent a domain where loss mechanisms are well understood and increasingly scrutinized.
When security signals align with loss frequency and magnitude, security leadership supports decision-making, audit outcomes, and regulatory confidence. At that point, security operations function as enterprise risk management.
We would love to help you get started with aligning your NHI governance with your compliance goals.








