Boards of Directors (BoDs) do three things exceptionally well when cyber is framed correctly. They set risk appetite, they allocate capital, and they demand evidence that the business can withstand disruption without losing momentum.
Boards do not want a deep dive on token formats, vault policies, or why one Kubernetes access pattern is better than another. They care about outcomes that map to enterprise value, including material exposure, downtime, and regulatory risk. They care about customer impact, and they are deeply concerned about whether the company can keep operating under stress.
Many cyber conversations fail at the very first step. Security leaders too often walk into the boardroom with a pile of findings and expect trust. The board hears complexity, uncertainty, and loudest of all, costs.
Most BoDs want a small, stable set of business indicators that show risk is going down and resilience is going up over time. If leaders adopt that lens, the scope naturally broadens beyond “cybersecurity.” It becomes operational resilience, and it includes efficiency.
Why Cyber Keeps Becoming A Board Topic
A board generally spends the most time addressing cyber when they have to, not by choice. If there is a material incident, cyber temporarily becomes the board’s number one issue because disclosure, customer impact, and financial exposure collapse into one event.
For example, U.S. public companies are required by the SEC’s cybersecurity disclosure rules to disclose material cybersecurity incidents under Item 1.05 of Form 8-K, generally within four business days of determining materiality. They must also describe governance and oversight, including the board’s role, in annual disclosures.
Oversight expectations are also rising. Deloitte’s Audit Committee Practices reporting shows that cyber sits squarely in audit committee priorities, with 50% of respondents identifying cybersecurity as the number one area of focus for their audit committee over the next 12 months. That same report found that 62% said audit committees have primary oversight of cybersecurity risk.
Balancing Risk With Keeping Up With Tech
Boards are also pushing innovation. BDO’s 2025 Board Survey summary highlights that many directors see emerging technology as both an opportunity and a governance burden, with a meaningful share saying tech advancements will require significant board attention. The same report also notes that 63% of directors plan to increase strategic investment in cybersecurity in the year ahead.
Boards are balancing two pressures that often collide. They need to move faster on technology, while at the same time reducing exposure resulting from any change in technology. The only sustainable way to do that is to treat cyber as operational resilience rather than a separate technical function.
Operational Resilience Is The Bridge Between Board Priorities And Security Reality
Operational resilience is the ability to keep delivering strategy through disruption. That includes preventing incidents, but it also includes reducing fragility, shrinking blast radius, and maintaining delivery speed when conditions are imperfect.
This framing aligns with what boards already recognize:
- The organization can accept some risk, but only if you have controls, monitoring, and response capacity that keep losses within acceptable limits.
- The organization can invest in transformation, but only if transformation does not turn into operational chaos and cause spikes in costs.
- The organization can innovate, but only if the basics are disciplined enough to survive the consequences of change.
But this goal of investing wisely and safely in tech does not match the planning for many organizations. According to PwC’s Global Digital Trust Insights, only 24% of organizations report spending significantly more on proactive measures than reactive measures, while 67% report spending is roughly even across both categories. PwC explicitly frames proactive investment as the healthier posture, and warns that reactive costs are often underestimated because they are dispersed across the business.
Boards should understand this intuitively. They already know it is cheaper to maintain a factory than to rebuild it after a disaster. The same logic should apply to identity, access, and the infrastructure that keeps digital operations running. The disconnect is partly a result of how fast change is happening with regard to AI and non-human identity governance needs.
The Identity Layer Is Now The Operations Layer, Especially For Non-Human Identities
When boards talk about identity, they often default to humans and initiatives around MFA adoption, onboarding, privileged access reviews, and insider risk. Those are important, but they are no longer the whole identity story.
Modern businesses run on systems made up of non-human identities. Service accounts, API keys, CI tokens, OAuth apps, workload identities, and agent credentials now power all the integrations, automation, cloud workloads, and data pipelines that keep our customers using our digital products. As the number of machines and workloads needing access grows, the governance surface area continually expands.
CyberArk has reported that machine identities outnumber human identities by more than 80-to-1. Other estimates across the industry think we have crossed the 100-to-1 threshold as automation accelerates.
In most organizations, the majority of secrets exist because, traditionally, that was how legacy systems were safely connected to other systems. We needed an access mechanism for these identities, so we again reached for passwords, in the form of API keys and tokens, to get the job done. But those long-lived access keys, most of which grant more permissions than strictly necessary, have a tendency to sprawl by the millions.
In other words, "secrets sprawl," the leaking of credentials into plaintext across systems, is really a symptom of non-human identity sprawl.
The conversation needs to change from “how do we stop developers from making mistakes” to “how do we govern machine access at enterprise scale without slowing the business down.” Helping the board have this exact conversation is the difference between fighting for security budgets and finding paths forward for real organizational change.
Making The Business Case With Gitguardian's Insights
GitGuardian’s “Hidden Cost of Secrets Sprawl” report is useful precisely because it quantifies what boards tend to suspect: credential chaos is a productivity tax.
This report makes it clear that manual secrets management costs organizations $172,000+ annually per 10 developers. The math is grounded in three hours per week per developer, and a fully loaded cost model that puts senior developer time at around $120 per hour.

The more important point for a board is that the cost shows up in several predictable places across the lifecycle of delivery and response.
Costs show up in engineering throughput. When developers spend hours requesting, finding, rotating, or debugging credentials, they are not building features. GitGuardian describes how this friction compounds as organizations grow, turning a small tax into a competitive disadvantage.
Costs show up in security and operations bandwidth. Alert fatigue and manual investigation pull teams away from strategic work, and estimates show that automation can recover at least 1.2 FTE worth of capacity.
Costs show up in onboarding and time to productivity. Access and credential setup can stretch onboarding timelines, keeping new hires from becoming productive while they wait for access and learn informal processes.
Costs show up during incidents. When a key leaks, teams often lose time simply understanding what the key can touch, where it is used, and what needs to be rotated. GitGuardian includes customer examples that emphasize how long this mapping can take in real environments.
Costs show up in audit readiness. Audit prep is frequently a scavenger hunt for evidence of control and ownership, made worse when credentials and machine access are spread across teams and tools. This is an avoidable operational burden, not just a compliance annoyance.
The “hidden cost” is operational inefficiency that increases risk by consuming the exact bandwidth you need to improve resilience.
The Board Question To Anchor The Conversation
If you want to boil it down to one board-level question that forces clarity without dragging the room into technical weeds, it is this:
How are we governing non-human identities and their access, and what is our confidence in the inventory?
That single question ties to everything boards already care about:
- Risk appetite - unknown access creates unknowable exposure.
- Continuity - fragile access breaks operations during change.
- Accountability - “no owner” means “no control.”
- Cost - manual access work is a measurable operational drag.
- Crisis Response - containment speed depends on visibility and ownership.
The job of a security leader is not to get them to ask this specific question; it is to answer it proactively before they know to ask.
Framing security, DevOps, and IAM work as a unified front that can speed innovation while limiting risks sets you up for wider success than focusing on a single tool choice or team-siloed initiative ever could.
The Challenge Of Up-Front Investment To Move Away From Long-Lived Secrets
Boards are often comfortable with funding end states. But engineering teams live in transitions. Bridging that gap, without bogging down in the weeds, is the real challenge.
Moving from long-lived secrets to identity-based authentication for NHIs is a real modernization effort. It can require refactoring authentication patterns, adjusting CI pipelines, replacing brittle integrations, and introducing new controls like workload identity or signed assertions. It also requires building governance muscles that many organizations never had to build when credentials were informal.
That is why so many of these types of programs stall. The product always has to ship. Reliability work competes with feature work, and security initiatives compete with operational debt.
This is where board oversight becomes valuable. The board can do what engineering teams often cannot do alone, like protecting time for foundational work, insisting on measurable progress, and preventing risk from silently compounding while the company scales.
Prepping For Operational Realities
In practical terms, the board should expect a phased approach to stabilize what exists by reducing unmanaged long-lived credentials and improving discovery, ownership, and rotation discipline.
Part of the data BoDs should demand is exactly which systems are mission-critical, meaning they would cause loss if they were affected by an incident or outage. Shifting workloads and integrations toward short-lived, identity-based access takes time, so priority should be given to "critical" infrastructure and systems first.
Boards must expect the orgs' executives and leaders to institutionalize governance across NHIs. The goal is to ensure machine access does not drift back into chaos as teams change and new systems arrive. This is a goal most organizations are just beginning to grapple with, and where partnering with the right technologies can make a significant difference.
The board does not need to choose individual protocols or tools. BoDs need to fund the journey and demand evidence that the journey is reducing both risk and operational drag.
Move Toward Full NHI Governance With GitGuardian
GitGuardian can help you move towards true NHI Governance because our platform starts where the pain is most visible and measurable, then expands into where the long-term control must exist.
When most people think of GitGuardian, they immediately think of the State of Secrets Sprawl, our annual report on finding millions of publicly leaked credentials. That is indeed where we started our journey as an organization, focused on secrets. Along the way, we realized that secrets don't exist in a vacuum, and what we have really been tracking all along is access mechanisms for identities, in particular, non-human identities. This shift might seem subtle at first, but the sea change is evident in the platform's recent release notes, where we talk about expanding NHI Governance with integrations that discover and enumerate NHIs tied to platforms like Airbyte, Anthropic, N8n, OpenAI, CyberArk Secrets Manager Self Hosted, and Slack. The emphasis is on identity context, permissions, accessed resources, and an identity-first inventory view, not on new types of detectors.
And right before we ended 2025, GitGuardian expanded NHI Governance coverage into additional critical platforms, including Datadog, Snowflake, Okta, and Auth0. We are now helping teams close blind spots and enabling unified identity risk assessment.
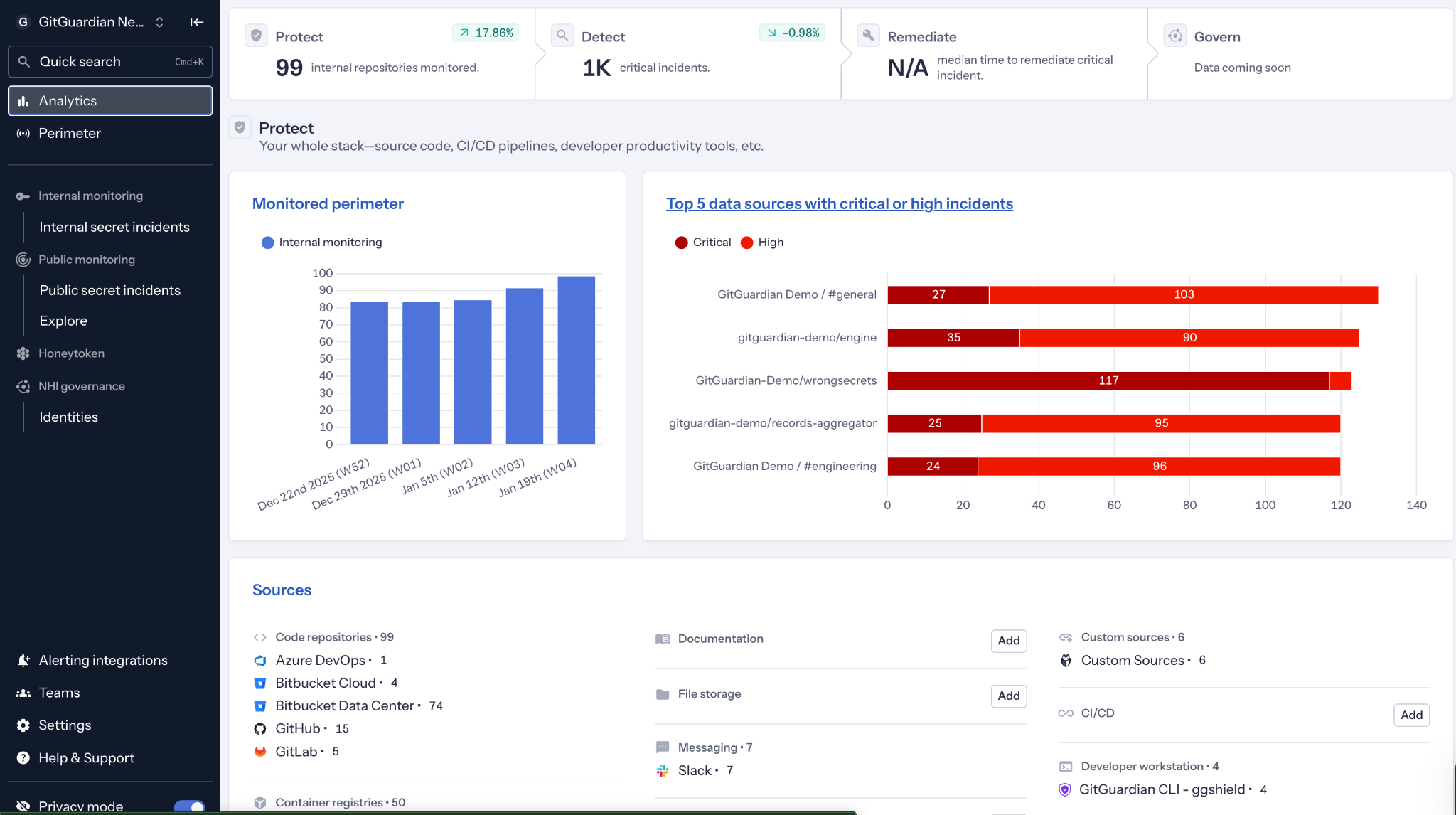
This aligns well with BoDs' mindsets. It begins with exposure and operational friction that is already costing money, then builds toward a durable identity governance layer that scales with the business.
What Boards Should Demand, And What Management Should Deliver
Boards do not need to become security architects. They need to govern the enterprise in the reality in which it operates. Today, that reality means identity is the control plane for resilience, and non-human identities are the fastest-growing part of it.
Non-human identities are now a core part of that resilience equation because they represent scaled access to systems, data, and automation. If they are unmanaged, your exposure is unknowable, and your operations are fragile. If they are well-governed, you reduce the blast radius and reclaim operational capacity at the same time. This is why GitGuardian matters when communicating risks and your strategy to your board.
Partnering with GitGuardian can help you report periodically on NHI governance with trend lines, not just point-in-time snapshots. This includes progress on your modernization path away from long-lived credentials. Our platform will help you treat incident readiness as a control, including containment speed and the ability to rotate or revoke access without downtime.
We would be happy to set up a demo and help you align your next board of directors conversations with your operational realities and needs.








