The first railroad bridge to span the Mississippi River was built between Davenport, IA, and Rock Island, IL in 1856. It burned down just 15 days later. It was the victim of a steamboat collision stemming from a simmering conflict between rival modes of commerce. In hindsight, this disaster wasn’t a structural failure; it was a breakdown in communication and a clash of trust boundaries. Like that doomed bridge, many of our cybersecurity defenses are one misalignment away from collapse. Fixing those issues and making our systems more resilient was very top of mind for everyone who gathered in Davenport for CornCon 11.
Over 400 security practitioners gathered to take part in this three-day event that featured over 50 sessions from more than 70 subject matter experts, 4 workshops, and a capture-the-flag. The first of the three days was a CISO summit, gathering the security leads of dozens of companies to talk about how to lead companies towards better security posture while dealing with the realities of tighter budgets and AI everywhere. CornCon also hosts a Kids’ Hacker Camp, helping the next generation of defenders get an early start. And of course, there was a lot of fun and amazing hallway conversations. Here are just a few highlights from CornCon 11.

Sustainability Over Perfection
In "Cybersecurity Doesn’t Need a Six-Pack: Embrace the Dadbod," Douglas Brush, Cyber & Privacy Personal Trainer and CISO Whisperer at Brush Cyber, started with what honestly sounded like a joke: “Cybersecurity needs to embrace the Dadbod.” But as Douglas walked through his story, his point became rather serious, as he laid down a challenge to the entire aesthetic of security success.
At the heart of his talk was culture, and that we’ve been fed a lie for decades, that elite security looks flawless. We worship hacker heroes and burn ourselves out chasing zero-risk illusions. He took aim at the Gen X “train through the pain” mentality and the toxic pride in 80-hour work weeks. Douglas argued that this mindset is unsustainable, and it’s killing programs and people alike.
After a health crisis, he realized he’d been tracking the wrong metrics, vanity measures that didn’t improve outcomes in his personal life. He realized he had also been focused on the wrong metrics as a CISO. He took a step back and realized he needed to refocus on fundamentals, such as defensibility over decoration and things like rolling out and enforcing MFA everywhere before going after SOC2. In his analogy, AI tools are like steroids, powerful, flashy, even transformative, but dangerously easy to abuse when the core isn’t strong.
Douglas left us with the reminder that security programs should look less like Marvel superheroes and more like reliable, resilient dads. Not flawless, but always there when it counts.

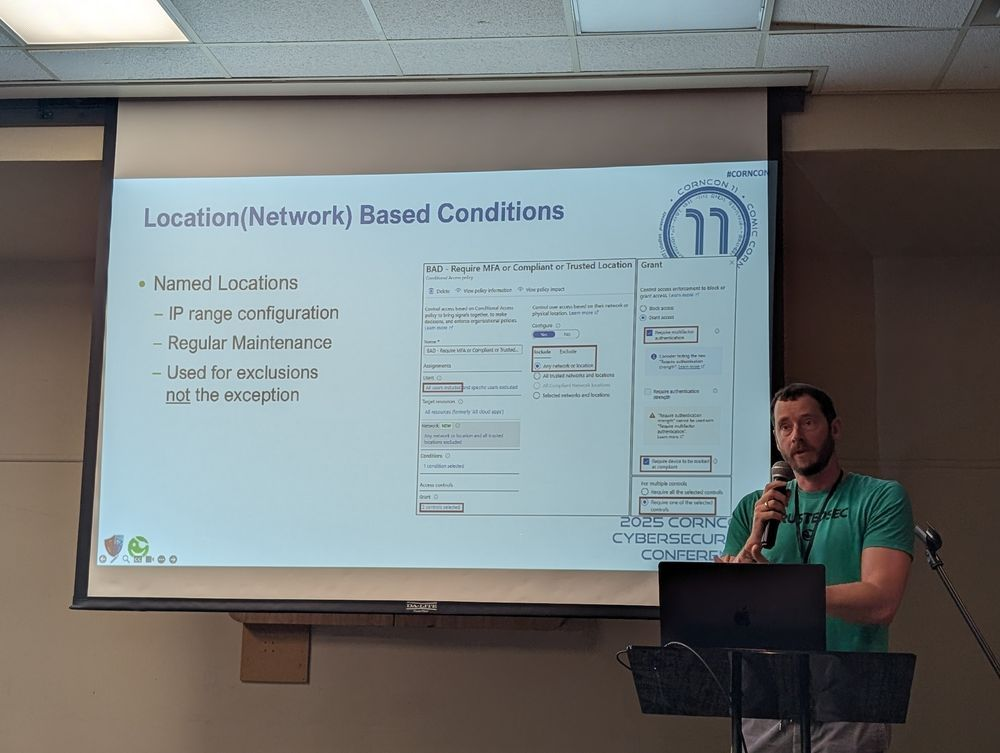
When Conditional Access Becomes Conditional Exposure
In his talk "Abusing Holes in Entra Conditional Access," Brandon Colley, Senior Security Consultant at TrustedSec, explained how Microsoft Entra Conditional Access policies are meant to enforce boundaries, but misconfigurations can open some unexpected security holes. The way most orgs implement Conditional Access is unmanageable, inconsistent, and dangerously complex.
The first major issue Brandon discussed was "policy sprawl," where teams keep adding new policies, sometimes ending up hitting the upper limit of 195. The more policies that exist, the harder it is to understand. To make matters worse, teams tie multiple policies together using the "AND" operator, leading to very complex situations where it is hard to tell if a role is covered in all circumstances.
He encouraged everyone in the audience to, at a minimum, require MFA for real admins. Entra ships with over 100 roles, not just the 14 defaults. Check to make sure you have locked down the critical ones: Authentication Policy Administrator, Directory Writers, External Identity Provider Administrator, Hybrid Identity Administrator, Identity Governance Administrator, and Intune Administrator.
Branden also walked through some of the tools he uses for finding security issues and tuning Entra policies. The Conditional Access What If tool gives you a playground to test things, telling you how a policy evaluates for a specific user and client. MFASweep is a security tool that can flag accounts without MFA enabled and show when PowerShell can be accessed. He also encouraged us to check out maester.dev, which provides a test automation framework for tuning Microsoft Conditional Access.
Every Villain Has an Origin Story
In the intro to her entertaining and informative session "Cyber Super Villains: The Real-Life Threats Lurking in Our Digital World," Paige Hanson, Co-Founder of SecureLabs, asked us "what makes a great adversary?" Throughout the rest of her talk, she used comic book archetypal villains to explain how real-world threat actors work.
She started with the X-Men villain Mystique, whose shape-shifting maps to impersonation scams and voice cloning. Magneto’s obsession with control parallels ransomware gangs and crime-as-a-service economies. From the DC universe, Scarecrow's fear tactics echo the psychological chaos of water plant shutdowns and phishing-driven panic. Even Brainiac’s data weaponization now feels tangible in the age of AI-enhanced fraud.
Paige reminded us that, unlike these fictional villains, attackers are not solo geniuses; they’re part of modular, scalable crime ecosystems where we have seen do-it-yourself fraud turned franchise. Crime today is composable and AI-driven.
But there are parallels to heroes on the other side, trying to protect us all. This included an obvious comparison of Captain America with governance bodies like CISA and NIST. Batman and Deadpool, who work in unconventional ways to get the job done, mirror our real-world heroes who focus on ethical hacking, uncovering vulnerabilities and exploits before the attackers can succeed.
Ultimately, we need to act like the Avengers, where everyone brings their skills to the table to defeat evil, no matter what form it takes.

Offensive Insight With A Defensive Heart
Sean Juroviesky, Senior Security Engineer at SoundCloud, delivered an honest assessment of offensive security’s current failings in their talk "Bridging the Gap: Delivering Offensive insights to the Blue Team." They explained that we keep finding the same things year after year in our pentesting reports because the current model is performative, not transformational.
Pentration tests are far too often checkbox exercises. Insurance-mandated and many customer contracts demand them, but they are done as one-off or annual exercises where the blue team is not adequately involved. This results in too few issues getting patched and continued deprioritization of the needed work. The average they found was that it took teams 3.2 years to resolve the most critical findings.
Sean advocated for a new model, one where red teams work with blue teams to identify targets that are both impactful and fixable. They emphasized aligning findings with business risk, not just technical severity. If a vulnerability could lead to a revenue-impacting event (a RIE), then it matters. If not, it’s probably noise.
Sean stressed that red teams can’t just drop reports, but instead need to diagram downstream impacts, highlight system interdependencies, and acknowledge when fixes are unrealistic. They can realistically only do that by working with the rest of the org to get the needed context. They reminded us that security is a long game, and every pentest should leave the organization not just knowing where they are exposed, but better equipped to make meaningful security changes.

Getting The Basics Right Has Never Been More Important
Throughout CornCon, one theme kept coming up in most talks: the tools matter, but the people using them matter more. Multiple speakers made a call for returning to the fundamentals as the industry keeps accelerating. Tech will not save us by itself. Security is a human discipline, and it gets stronger when we practice together and learn from each other.
Back to basics showed up in identity and operations. Conditional Access works when teams standardize names, require MFA for real admins, keep location rules precise, and treat exclusions as temporary. The CISO panel echoed that we need to communicate up and across the business. Putting a human in the loop means automation can accelerate good judgment instead of scaling bad processes.
Speakers talked about reframing programs around balance and sustainability instead of perfection theater. We need to build succession plans and coach our teams to speak revenue, risk, and recovery time so security reads as a partner, not a cost center. We need to work together to translate the red team's efforts into actionable plans, not just more reports to file away.
The theme of the weekend was not a new silver bullet. It was a return to craft. Basics done well. Teams equipped and trusted. Communities that make people better at their jobs and kinder to themselves. That is how you build security that lasts.
Your author was also able to give a talk about getting back to basics, where I argued for focusing on taming secrets sprawl. If we can focus on empowering our developers and DevOps teams to make safer authentication decisions, such as not hardcoding credentials, then we have a real hope of taking the machine identity mess we are facing.
Focusing On Simple Practices For Durable Resilience
CornCon 11 was a reminder that resilience is not a new tool. It is fundamentals practiced with discipline by people who trust each other. Earning that trust requires patience and real effort to bridge the gap between teams. We need to teach the 'why' behind the changes we want others to make, so the fixes stick when you are not in the room.
If you want lasting gains, invest in the humans. Let's work to build more places where practitioners can learn, vent, and trade playbooks without posturing. Tie findings to business outcomes so leaders see security as a partner. Keep the craft simple, repeatable, and humane. That is how you build defenses that hold when the river rises.






