As organizations grow more complex, secrets are increasingly leaking at various stages of the Software Development Life Cycle and across collaboration tools. Our State of Secret Sprawl report shows that this problem is only getting worse, with 12.8 million secrets exposed in 2023—a 30% increase from the previous year. This surge in exposed secrets creates serious security risks, especially as data breaches become more frequent and costly (averaging $4.88 million per breach, according to IBM).
Additionally, more secrets mean more alerts for security teams, contributing to an already overwhelming stream of notifications. Detection without remediation just adds noise, worsening alert fatigue and making it harder for teams to focus on real threats.
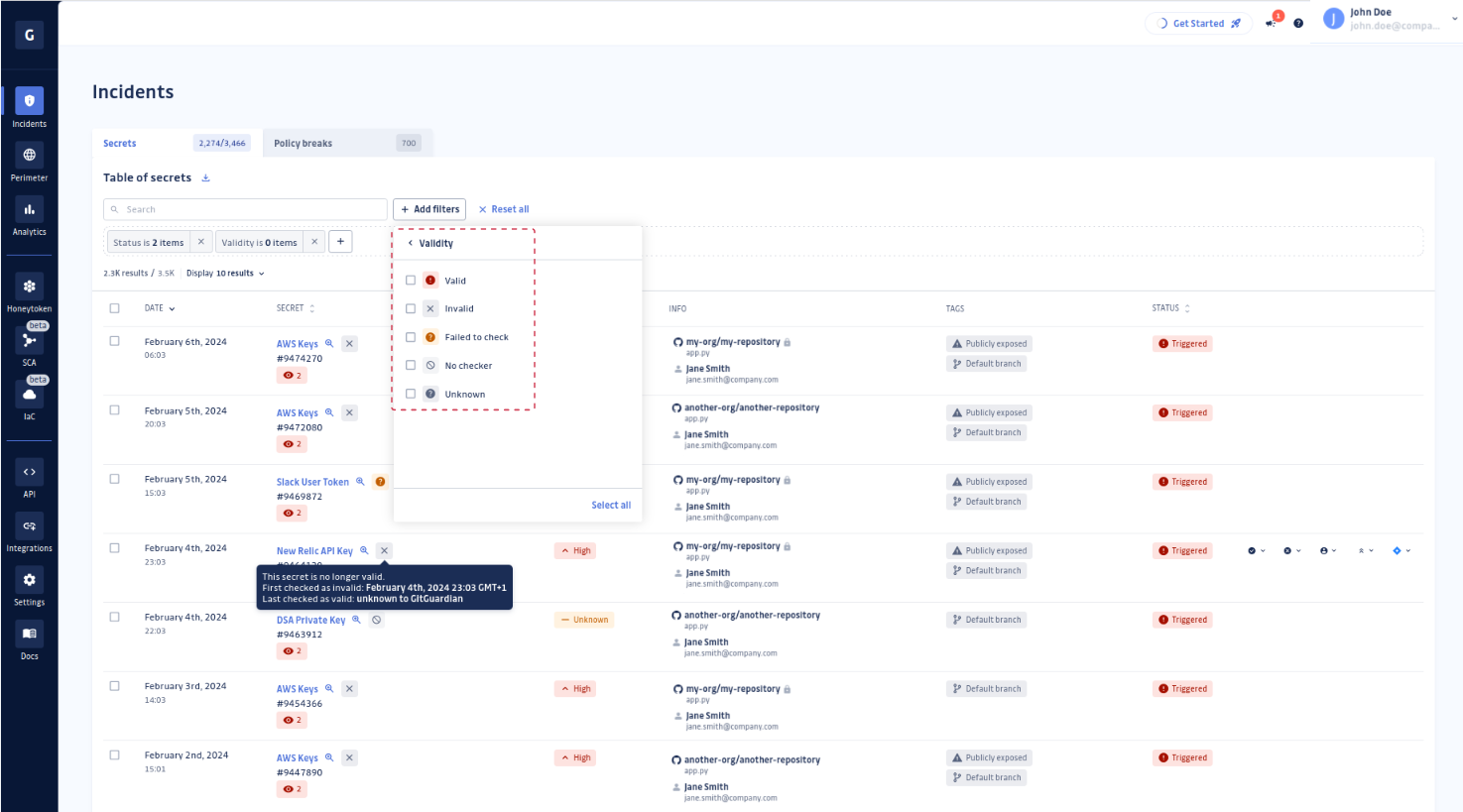
This is where validity checks come in: by identifying which secrets are still active, they allow teams to prioritize live threats and ignore inactive ones. While GitGuardian already performs these checks for SaaS platforms, our new custom host settings extend this capability to self-hosted environments, such as GitHub Enterprise and Bitbucket Data Center. Learn how your team can cut through the noise to focus on what matters most.
The importance of validity checks in secrets security
Knowing a secret's validity status is critical for effective incident management. Validity information allows security teams to:
- Prioritize their efforts: Knowing a secret's validity status allows security teams to quickly assess the urgency of a threat. A valid secret poses an active risk and requires remediation, while an invalid (revoked or expired) secret can be safely disregarded. This helps reduce noise, allowing teams to focus on genuine risks.
- Verify remediation success: Validity checks also confirm whether remediation actions were successful. After revoking a secret, a validity check should indicate a change from valid to invalid, providing confidence that the threat has been neutralized. This verification step is essential for closing the loop on incident response.
Without validity checks, teams risk:
- Overlooking critical incidents: If a valid secret goes unrecognized, it may be mistakenly ignored, leaving a security gap that attackers could exploit.
- Chasing false positives: Without accurate validity checks, security teams may waste time investigating expired secrets flagged as threats. This can distract attention from real issues.
In short, validity checks enable security teams to focus on active risks, confirm successful remediation, and avoid unnecessary distractions—ultimately strengthening the organization's security posture.
The challenges with self-hosted instances
For many organizations, self-hosted environments are essential. Enterprises often choose self-hosted instances of platforms like Gitlab, Jira, or Sentry to meet regulatory requirements, ensure data sovereignty, and allow for custom configurations. However, this introduces new security challenges for managing secrets securely.
The need to extend validity checks to self-hosted secret providers
GitGuardian was the first solution to introduce validity checks for secrets, a breakthrough feature that allowed security teams to verify the status of secrets in real time. Initially, this capability was designed for SaaS environments, where GitGuardian could interact directly with cloud endpoints to check if a secret was still active.
However, secret providers may lack complete visibility into their on-premises versions. To address these blind spots, we’re extending this powerful capability to self-hosted environments, which are unique to each customer. Our users gain precise validity information for secrets across both cloud and on-premises systems, ensuring that no valid secret goes undetected.
Real-world example: the Cloudflare incident
A notable illustration of the challenges associated with this setup is the Thanksgiving 2023 Cloudflare security incident. Cloudflare used self-hosted Atlassian products, including Bitbucket, and some service tokens tied to these accounts were mistakenly left unrotated following an earlier breach involving a third-party service.
The unrotated secrets provided an entry point for an attacker, who exploited this oversight to gain access to 120 code repositories stored in Cloudflare's self-hosted Bitbucket instance. These repositories contained sensitive information about backups, network configuration, remote access, and more. While Cloudflare could not confirm whether these secrets were exploited, they treated them as compromised and launched an extensive investigation to assess the risks they posed.
Key Takeaway
This incident underscores the critical need for secret validity checks, even in self-hosted systems. With better visibility into the status of their secrets, Cloudflare could have identified and mitigated the breach sooner.
GitGuardian's custom host for validity checks
Guardian's new "custom host for validity checks" feature enables Business workspace owners to perform secret validity checks against each secret provider that supports validity checks and has a self-hosted version, gaining accurate, real-time information on whether a secret is still valid.
This feature also supports complex environments by allowing multiple custom hosts for a single detector, ideal for enterprises with multiple instances of the same platform (e.g., regional instances of GitLab).
Setting up a custom host in the GitGuardian dashboard: three simple steps
Setting up a custom host in GitGuardian is quick and straightforward. Here's how to do it:
Step 1: In the GitGuardian dashboard, navigate to detector settings.
Step 2: Enter the base URL of your self-hosted instance. For example, if you’re setting up a custom host for a self-hosted Confluence instance, enter the instance’s base URL, such as https://confluence.gitguardian.com/.
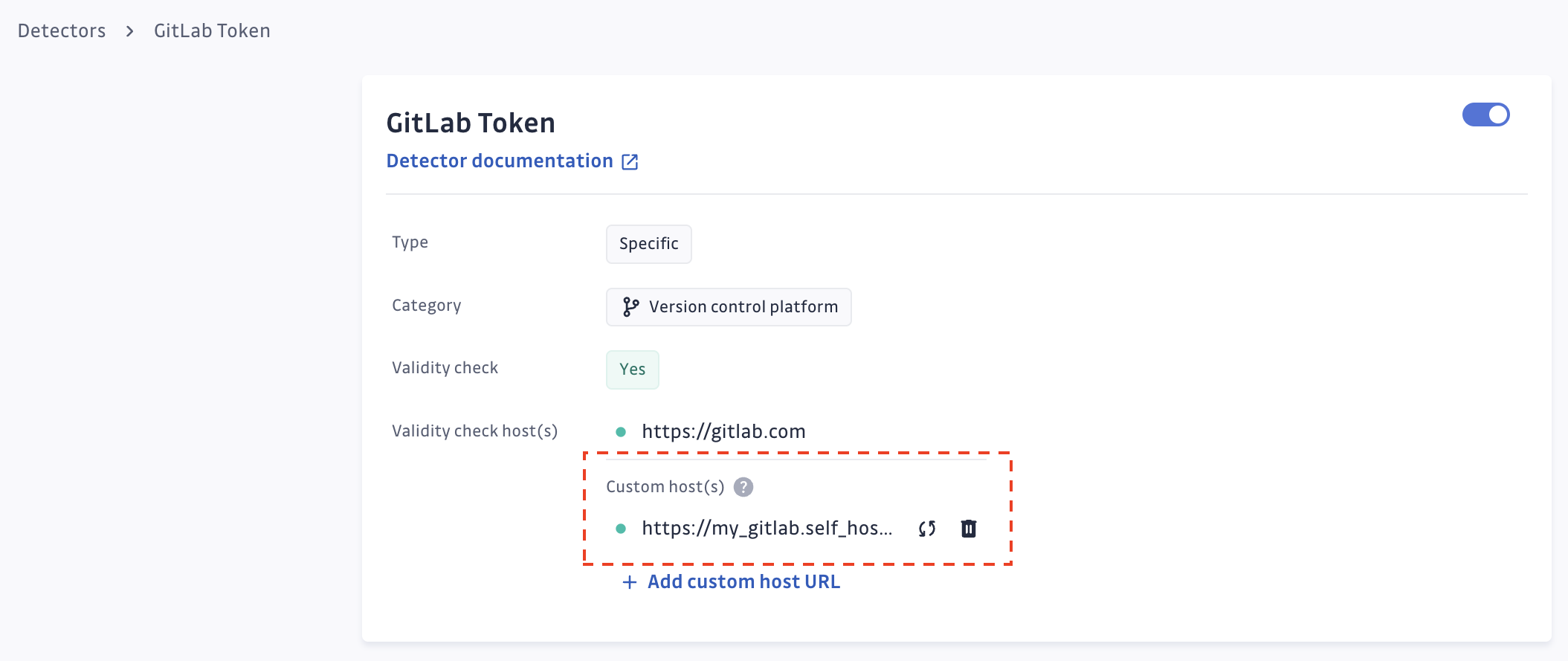
Users only need to specify the host (or base URL) of their self-hosted system, while GitGuardian automatically manages the rest of the endpoint configuration. This eliminates the need to handle complex paths or routes—GitGuardian takes care of that for you.
Step 3: Save the settings, and GitGuardian will perform validity checks for the secrets associated with that instance.
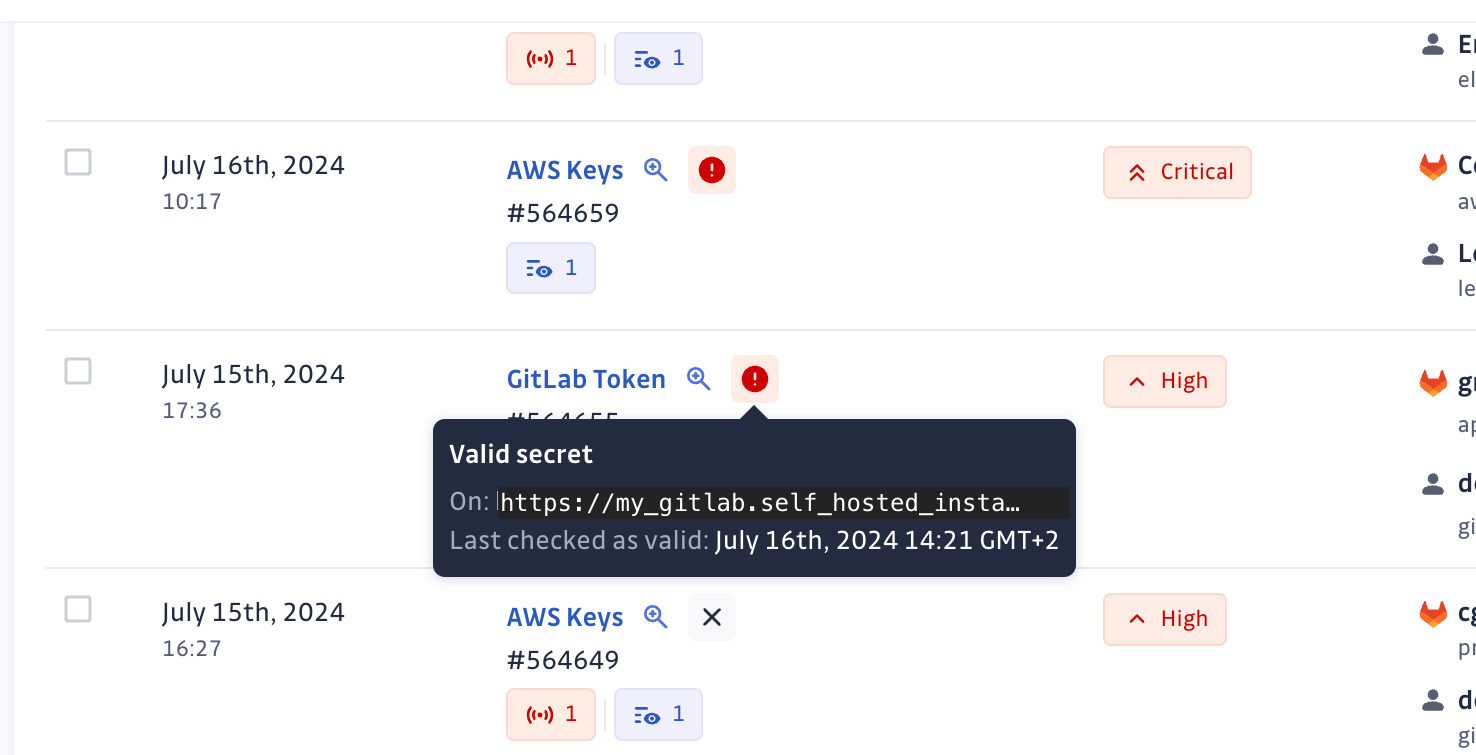
Once configured, GitGuardian will re-check the validity of existing incidents in your dashboard by performing the validity check against the custom host. Moving forward, GitGuardian will automatically verify the validity of all future incidents in real-time, using both the SaaS and custom host versions where applicable, ensuring your security teams have the most accurate, up-to-date insights into each secret’s status.
Accessible setup for all security teams
The setup process is simple enough for most security teams to handle without specialized technical expertise. GitGuardian ensures that even organizations with limited resources or smaller security teams can quickly gain visibility into their self-hosted environments.
A smarter approach to secrets management
In today's complex security landscape, knowing the validity status of secrets is essential for effective incident management. Validity information enables security teams to both prioritize incidents needing remediation and confirm the success of their remediation efforts.
By configuring custom hosts, security teams gain real-time visibility into the status of secrets in their self-hosted environments—even across multiple instances of the same platform.
As secrets sprawl continues to grow, GitGuardian remains committed to delivering adaptable, enterprise-grade solutions that keep pace with the evolving needs of modern organizations, no matter how complex their environments.