In the Detector of the month series, we feature our favorite projects or services GitGuardian’s secrets detection engine supports. For this second installment in 2022, we’re showcasing the PlanetScale database password and token detectors!
What is PlanetScale?
The story behind PlanetScale is quite an interesting one. Born at YouTube in 2010, Vitess is a database solution for deploying and managing large clusters of MySQL databases. It has helped the video-sharing platform scale to serve billions of users worldwide. Vitess went on to be released as an open-source project and now also powers the serverless databases offered by PlanetScale.
With Vitess and PlanetScale, enterprises can keep their existing MySQL databases and automatically scale them with zero migration of data, zero change in the application later, all without giving up any SQL features. With its Git-like workflows, PlanetScale seems to be the first database to be truly designed for developers!
If your MySQL database is starting to show its first signs of scale fatigue, it might be the right time to move to PlanetScale! Get started here.
Keep PlanetScale credentials out of your code with GitGuardian!
Secrets sprawl is still a hot issue for developers and security engineers. Last year, our monitoring of public GitHub revealed a two-fold increase in the number of leaked credentials, with more than 6 million exposed throughout 2021! In other words, 3 commits out of 1,000 exposed at least one secret.
At GitGuardian, we’re committed to helping developers reduce the risk of exposing their secrets, and here’s how we’re doing it:
- We notify developers whenever they misstep and leave plain text credentials in Git repositories, thanks to our library of 350+ built-in specific and generic detectors.
- We share with developers the best practices around code security and secrets management and how to implement them at both the individual and team levels.
The risks of secrets-in-code can never be overstated, especially when it comes to compromised credentials or tokens with access to databases in production environments. Organizations stand to lose a lot from exposing this critical component of their infrastructure and can become easy targets for ransomware or even make it to the headlines following customer and business data leaks.
How to handle hardcoded PlanetScale secrets?
Here’s what to do when you receive an alert from GitGuardian mentioning a leaked PlanetScale database password or token:
-
Understand the implications of the incident. A bad situation can be made worse if a secret is revoked without understanding how it is currently being used.
-
Rotate and revoke the secret!
- If it’s a PlanetScale database password
Go to your PlansetScale dashboard. Click on your database to access its dedicated console. Click on the settings tab, you will find a passwords item in the menu, click on it:
a. First, create a new password to replace the compromised one;
b. Second, select the exposed key and delete it so it can no longer be exploited.
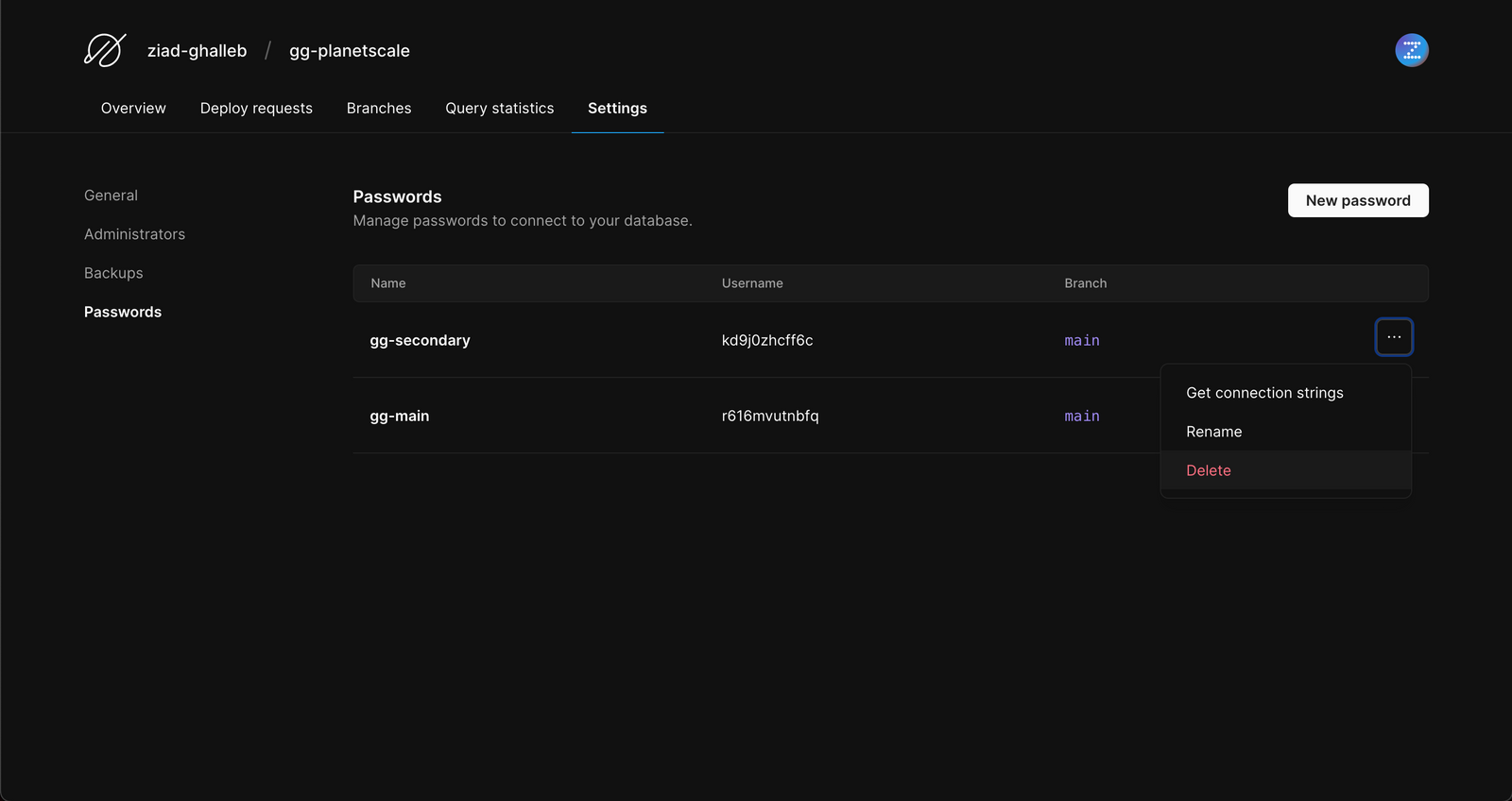
To learn more about PlanetScale database passwords, please visit the developer docs.
- If it’s a PlanetScale token used for the CLI
Go to your PlanetScale dashboard. In the account settings page, you will find the service tokens section in the list:
a. First, create a new key to replace the compromised one;
b. Second, select the exposed key and delete it so it can no longer be exploited.
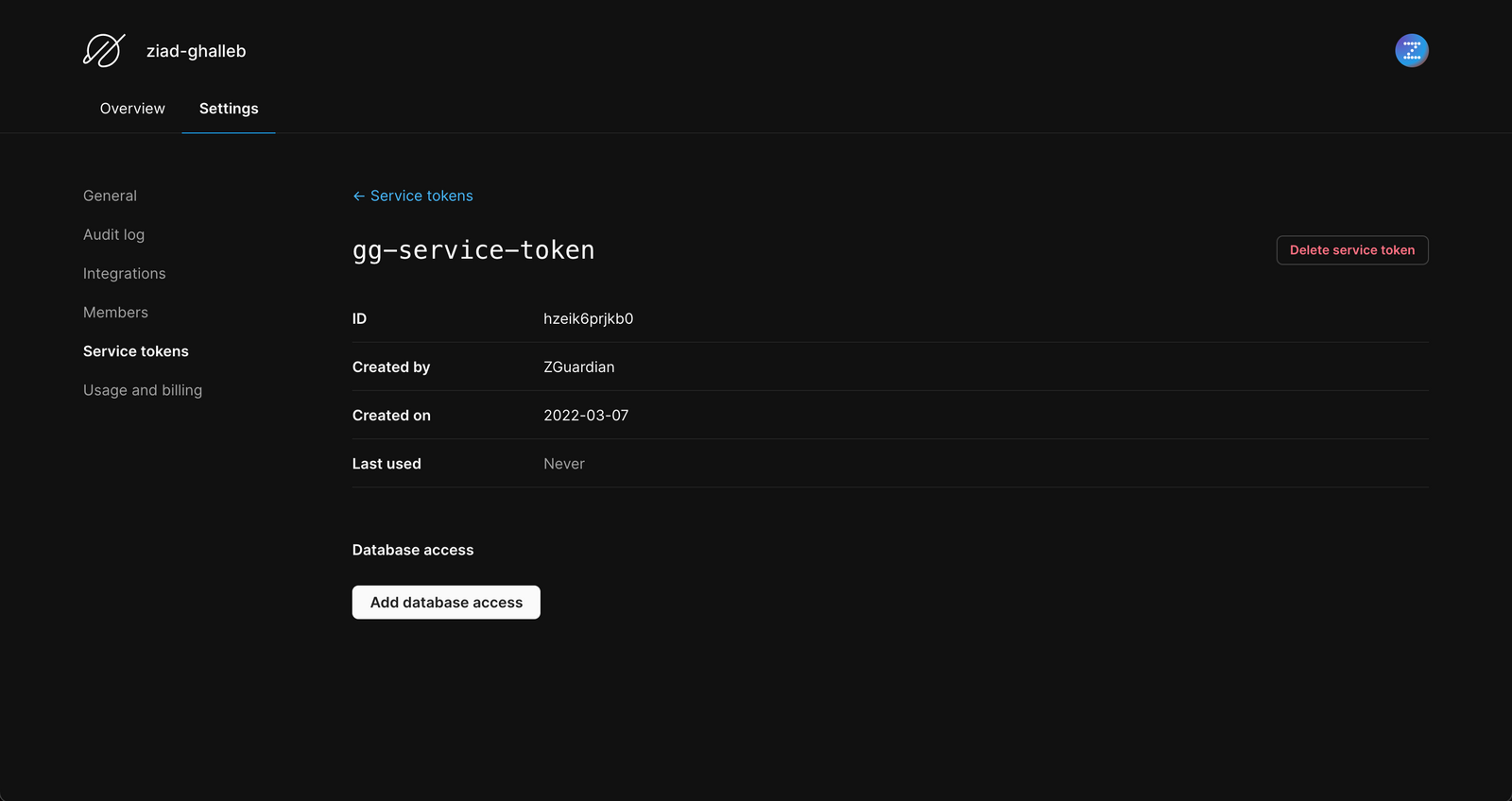
To learn more about PlanetScale service accounts, please visit the CLI reference docs.
- If it’s a PlanetScale database password
-
Manage your secrets. Use a dotenv file to hide sensitive environment variables or look for alternative secrets management solutions to avoid hardcoding database credentials in the future.
-
Review access logs. Check for suspicious activity in the log data of your services associated with the exposed secret.
-
Optional – Remove all evidence from your git history. Rewrite the git history or delete the entire repository. Such an operation is not trivial and needs to be discussed with your team members.
What about other secrets?
GitGuardian helps developers keep 350+ types of secrets out of source code. GitGuardian’s automated secrets detection and remediation solution secure every step of the development lifecycle, from code to cloud:
- On developer workstations with Git hooks (pre-commit and pre-push);
- On code sharing platforms like GitHub, GitLab, and Bitbucket;
- In CI environments (Circle CI, Travis CI, Jenkins CI, GitHub Actions, and many more);
- In Docker images.