Credentials don’t live like they used to. Secrets that once stuck around for weeks or months are being replaced by tokens that vanish in minutes – or even seconds.
But the real question isn’t how long a credential lives. It’s whether it should have been issued in the first place. This is a key point that often gets lost in the push to modernize non-human identity and access management.
On the surface, ephemeral credentials seem like a cure-all: no more long-lived API keys to rotate, no stale secrets buried in Terraform files, no tokens lingering in CI/CD runners. A credential that expires in, say, 60 seconds feels inherently safer than one that persists. And in many ways, it is. Temporary credentials reduce the blast radius of breaches and make it harder for malicious hackers to reuse old tokens.
👉 Ephemeral identity refers to a security approach where workloads, applications, and other non-human identities are granted temporary, short-lived credentials that automatically expire after a brief period (typically seconds to hours) rather than using long-lived, static secrets.
Examples include AWS IAM temporary credentials, Kubernetes service account tokens, SPIRE/SPIFFE X.509 certificates (SVIDs), and OAuth 2.0 access tokens.
In popular cloud environments, such as GCP or AWS via native support for workload identity federation, or in self-managed systems using SPIRE to issue SVIDs, tokens really do last for a brief window. This introduction of ephemeral credentials – increasingly enabled by default – is largely a response to the operational strain and developer fatigue of distributing and securing secrets at scale across multiple clouds, dozens of SaaS tools, and hundreds or thousands of workloads.
Rotating shared secrets across multiple deployment environments breaks pipelines. Engineers riskily hardcode service tokens to keep things working. And secret managers, while effective in theory, often slow things down in practice, and can even lead to “vault sprawl,” when organizations turn to multiple vaults to manage secrets.The problem of secrets proliferation is real: In 2024 alone, 23.8 million secrets were leaked on public GitHub repositories – a 25% year-over-year increase, according to GitGuardian’s The State of Secrets Sprawl 2025 report.
Even more concerning, GitGuardian found that 70% of secrets leaked in 2022 remained active today, dramatically expanding the attack surface for threat actors.But it’s important to note: “short-lived” isn’t a synonym for “secure.” If a token is granted to the wrong workload, expiration doesn’t help. It just puts a timer on the mistake. And in cross-cloud environments, where identity is federated across systems that don’t speak the same language, the challenge gets harder.
The Architecture Behind the Promise
For ephemeral identities to deliver on their promise, the system behind them must answer three questions – every time access is granted:
1) Who is this workload?
The request must be authenticated based on verifiable identity. That could include attested metadata, signed binaries, trusted runtime environments, or cloud-native identity signals – not IP addresses or environment variables, which are easy to fake.
2) What is it allowed to access right now?
Identity alone isn’t enough. You need context: what environment it’s running in, what resource it’s accessing, what posture it presents. A valid identity in dev, for instance, shouldn’t access prod – and not all identities are equal at all times.
3) How do we know it’s safe to issue a credential?
Even if the identity and access request check out, the system needs to confirm that it’s safe to proceed: up-to-date scans and a secure runtime posture all matter.
Secret Zero Problem
And then there’s another catch to consider: Before any of these questions can be answered, the workload must start the conversation – and in most environments, that bootstrap step still relies on static trust. This is the secret zero problem: a hardcoded token, an environment variable, or a manually provisioned secret that serves as the initial credential to request others.
These initial secrets are rarely rotated, broadly scoped, and disconnected from any real-time identity enforcement. They persist because they’re easy, not because they’re safe – artifacts of an older model that conflict with the goals of ephemeral access.
Even in systems that issue short-lived credentials, the upstream trust decision often rests on this vulnerable foundation. If the wrong workload gets the right token, the credential’s lifespan doesn’t matter. It’s turtles all the way down.
What Secure Ephemeral Access Actually Looks Like
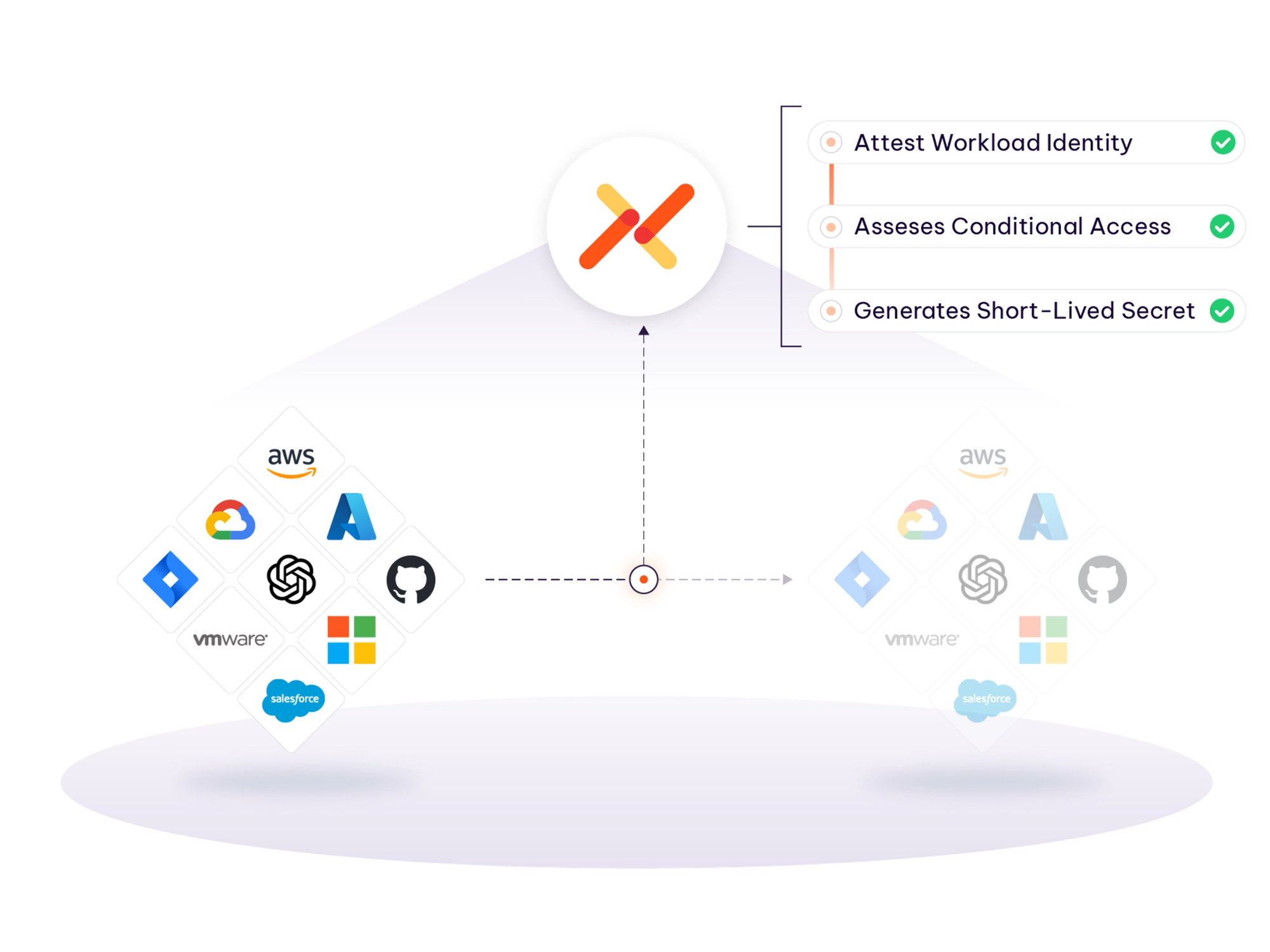
Ephemeral credentials only improve security – and solve the secret zero problem – when the access model around them enforces five principles, which are incorporated into workload IAM.
- Verifiable workload identity. Before issuing a credential, you need to know who (or what) is asking – even if you’ve never seen it before. That means trusting the environment where the workload runs, not just the request itself. Federation makes this possible: it lets you authenticate workloads based on signed code, cloud metadata, attested runtime posture, or CI/CD job “provenance,” while delegating identity proof to a trusted domain.
- Real-time policy enforcement. Ephemeral credentials should only be issued when the request matches a defined access policy: correct identity, correct context, correct resource. And policy should enforce not just who gets access, but when, how, and under what conditions.
- Posture-aware access. Just because a workload can request a token doesn’t mean it should. Ephemeral access should be gated by runtime posture – validated against agent status, software inventory, or vulnerability scans.
- Scoped, short-lived, and logged. Credentials should do one thing, expire quickly, and be tied to an auditable identity trail. If you can’t trace what was accessed and why, the expiration doesn’t help you.
- Cross-environment trust. In our multicloud world, the environment issuing the credential often differs from the one enforcing access, which introduces challenges around identity federation and consistent policy enforcement. Standards like OAuth and OIDC enable token exchange, but they don’t solve for everything – the underlying identity still needs to be validated, scoped, and checked against policy across trust boundaries.
Ephemeral Is a Means, Not an End
Replacing static secrets with ephemeral tokens is a step forward –- but only if the security architecture around them also evolves. The experience of cloud-based data storage giant Snowflake illustrates this well. Their shift away from static credentials required more than visibility into where secrets lived. It demanded a coordinated approach: GitGuardian helped uncover embedded secrets across development workflows, while Aembit enable a transition to identity-based, policy-enforced access that eliminated the need for static tokens in the first place.
Meanwhile, emerging standards are playing a key role in shaping what secure workload identity should look like.
Frameworks like SPIFFE are laying the groundwork for verifiable workload identity using X.509 certificates and JWTs, helping define how identity should be issued and trusted within a domain. The IETF’s Workload Identity in Multi-System Environments (WIMSE) working group is tackling the harder problem: enabling secure identity, authentication, authorization, and accountability across clouds, services, and trust boundaries. WIMSE is stitching together what already exists: protocols like OAuth and OIDC, open-source tools, and community best practices. The goal is to help organizations apply fine-grained, least-privilege access controls to workloads – even in sprawling, distributed environments.It’s an important step.
Because identity is just the beginning – enforcement, posture checks, and auditability are what turn short-lived into secure in the messy reality of heterogenous environments.
Thus the most important question you should ask isn’t “How long does the token last?” It’s “Should it have been issued at all?”
Explore GitGuardian and Aembit’s solutions to take the next step in your journey toward secure, scalable machine identity management.
FAQ
What are ephemeral identities and how do they differ from traditional credentials?
Ephemeral identities are short-lived credentials that expire within minutes or even seconds, replacing traditional long-lived API keys and tokens that persist for weeks or months. While traditional credentials remain static and require manual rotation, ephemeral credentials automatically expire and are dynamically issued as needed. This approach reduces the blast radius of breaches and makes it harder for attackers to reuse old tokens, but the key benefit isn't just the shorter lifespan—it's the dynamic, context-aware access control that can accompany proper ephemeral identity systems.
What is the "secret zero problem" in ephemeral identity systems?
The secret zero problem refers to the bootstrap challenge where workloads need an initial credential to request ephemeral tokens. This often relies on static trust mechanisms like hardcoded tokens, environment variables, or manually provisioned secrets. These initial secrets are rarely rotated, broadly scoped, and disconnected from real-time identity enforcement. Even in systems issuing short-lived credentials, if the wrong workload obtains the right bootstrap token, the credential's lifespan becomes irrelevant—the security breach has already occurred at the foundational level.
What three critical questions must ephemeral identity systems answer for every access request?
Every ephemeral identity system must answer: 1) Who is this workload? - Authentication based on verifiable identity using attested metadata, signed binaries, or trusted runtime environments, not easily faked signals like IP addresses; 2) What is it allowed to access right now? - Context-aware authorization considering the environment, resource, and current posture, ensuring a valid dev identity can't access production; and 3) How do we know it's safe to issue a credential? - Safety validation including up-to-date scans and secure runtime posture before credential issuance.
What are the five principles that make ephemeral access truly secure?
Secure ephemeral access requires: 1) Verifiable workload identity - Authentication based on trusted environments and signed code rather than just requests; 2) Real-time policy enforcement - Dynamic access decisions based on identity, context, and conditions; 3) Posture-aware access - Gating credentials based on runtime security posture and vulnerability status; 4) Scoped, short-lived, and logged - Single-purpose credentials with quick expiration tied to auditable identity trails; and 5) Cross-environment trust - Consistent identity validation and policy enforcement across multicloud environments using standards like OAuth and OIDC.
Why isn't "short-lived" automatically synonymous with "secure"?
Short-lived credentials only improve security when the underlying access model is sound. If a token is granted to the wrong workload or based on compromised identity, expiration simply puts a timer on the mistake rather than preventing it. The critical question isn't "How long does the token last?" but "Should it have been issued at all?" Without proper identity verification, policy enforcement, and posture checks, ephemeral credentials can still enable unauthorized access—they just do it for a shorter duration.
What standards and frameworks are emerging to address ephemeral identity challenges?
Several standards are addressing ephemeral identity challenges: SPIFFE provides frameworks for verifiable workload identity using X.509 certificates and JWTs, defining how identity should be issued and trusted within domains. The IETF's WIMSE (Workload Identity in Multi-System Environments) working group tackles cross-cloud identity federation, building on existing protocols like OAuth and OIDC to enable secure identity, authentication, authorization, and accountability across trust boundaries. These frameworks aim to apply fine-grained, least-privilege access controls to workloads in distributed, heterogeneous environments.
This article is a guest post. Views and opinions expressed in this publication are solely those of the author and do not reflect the official policy, position, or views of GitGuardian, The content is provided for informational purposes, GitGuardian assumes no responsibility for any errors, omissions, or outcomes resulting from the use of this information. Should you have any enquiry with regard to the content, please contact the author directly.









