The world of cybersecurity is facing a growing and unsolved challenge: secrets sprawl. As cloud adoption, AI, and automation accelerate, the number of secrets – API keys, tokens, credentials – has exploded. This proliferation, especially with the rise of Non-Human Identities (NHIs), has left security teams struggling to maintain control, and we at GitGuardian understand how difficult this can be. This struggle arises from limited visibility, fragmented secrets management, and a lack of governance over the lifecycle of NHIs, resulting in a security crisis where leaked credentials are now a leading cause of data breaches.
Today, GitGuardian, the first and only enterprise-ready secrets security provider, is proud to announce the launch of its NHI Governance product. This solution provides unified visibility and comprehensive lifecycle management for NHIs and their associated secrets, empowering organizations to reduce risk and secure their digital transformation.
Understanding the Complexity of NHIs
Non-Human Identities (NHIs), also known as machine identities, such as service accounts, API keys, and authentication tokens, are digital references used for machine-to-machine access. They are essential for automation and cloud computing, but they also introduce unique complexities compared to human identities, which can make them harder to manage.
Let's break down some of the key differences:
Authentication methods: Unlike human users, NHIs lack the additional security layer of multi-factor authentication, and they authenticate using secrets such as API keys, tokens, and certificates—credentials that, once exposed, can be exploited by attackers.
Lifecycle management: Human identities follow structured onboarding and offboarding processes, but NHIs often persist indefinitely, leading to orphaned, high-risk credentials.
Ownership challenges: Unlike human identities with clear owners, NHIs frequently lack defined accountability, making it difficult to track and manage them effectively.
Exponential growth: NHIs outnumber human identities in enterprises by as much as 100 to 1, contributing to secrets sprawl, where credentials are scattered across repositories, CI/CD pipelines, vaults, and even chat platforms.
This complexity, combined with factors like limited visibility, fragmented management, and a lack of standardization, makes NHIs a prime target for attackers. As GitGuardian's "State of Secrets Sprawl 2025" report shows, the problem is accelerating, with a 25% increase in secrets detected on GitHub in the past year. This trend is concerning, and we want to help you get ahead of it.
AI Agents Increase Secrets Exposure Risks
We see that the rapid adoption of AI agents adds another layer of complexity to this already challenging situation.
AI agents require broad access to functions, connecting to numerous systems (databases, services), each with its own credentials. They can extract secrets from the sources they access, like knowledge bases (which might themselves have varying levels of security), and then copy them to less secure locations. This is frequently exacerbated by the fact that these AI agent deployments are rushed or done in an uncontrolled manner and then copied to less secure locations (logs, third-party platforms).
It's critical to understand where these secrets end up:
Third-party infrastructure: Secrets can be transferred to the infrastructure/data storage of third-party providers. While these providers “might” be reputable, they still represent an external entity, reducing your direct control and introducing potential risks.
AI development environments: Secrets often end up with the teams developing the AI systems. This could include:
- Independent contractors.
- Teams outside of the core development group.
- Developers working with unsecured, "ghost" infrastructure (e.g., personal machines, temporary cloud instances without proper security).
RAG (Retrieval Augmented Generation) is a simple and common example: many companies use RAG to let AI search their internal knowledge base or to help their support teams.

To counter this, stronger NHI governance is essential in AI agent-enabled environments.
We're here to provide the solution.
Introducing GitGuardian NHI Governance
To address these challenges and provide you with better control, GitGuardian NHI Governance has been designed.
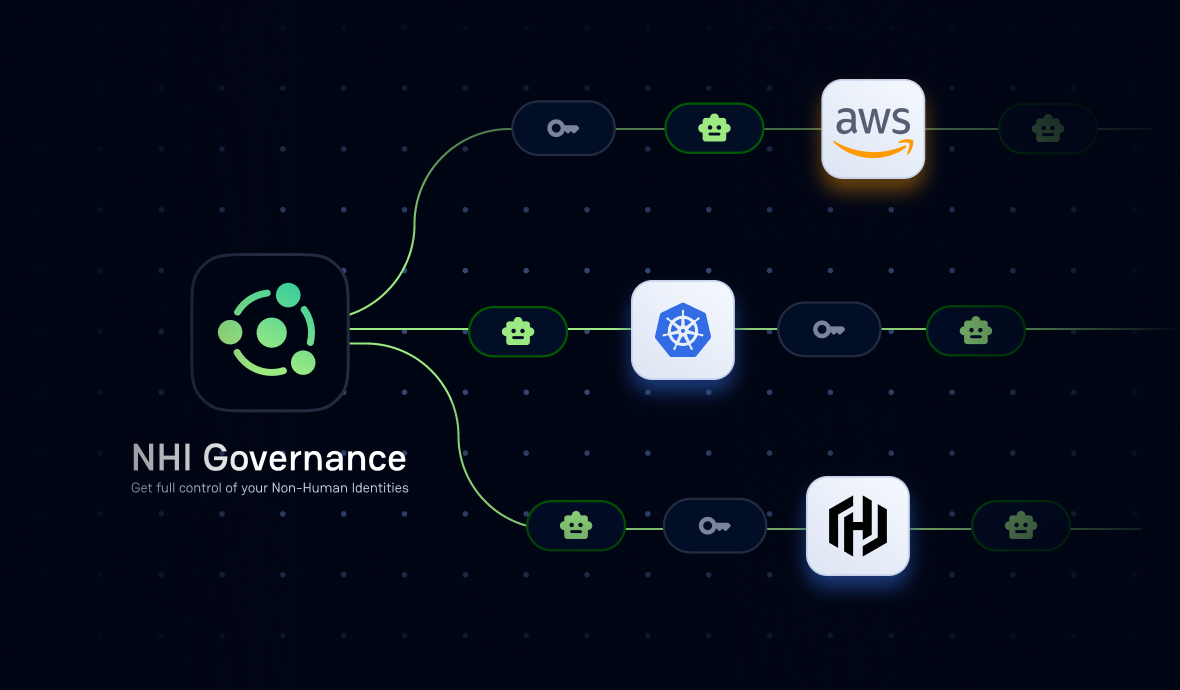
We understand that to truly tackle secrets sprawl and secure your NHIs, you need more than just detection – you need a comprehensive mapping of your entire secrets ecosystem, something that wasn't possible before in a sane, scalable way.
The map helps you trace the connections between secrets managers (where secrets are stored), consumers (services, scripts, jobs using the secret), accessed resources (targets and their permissions), and associated public and private secrets incidents.
Other key benefits of NHI Governance include:
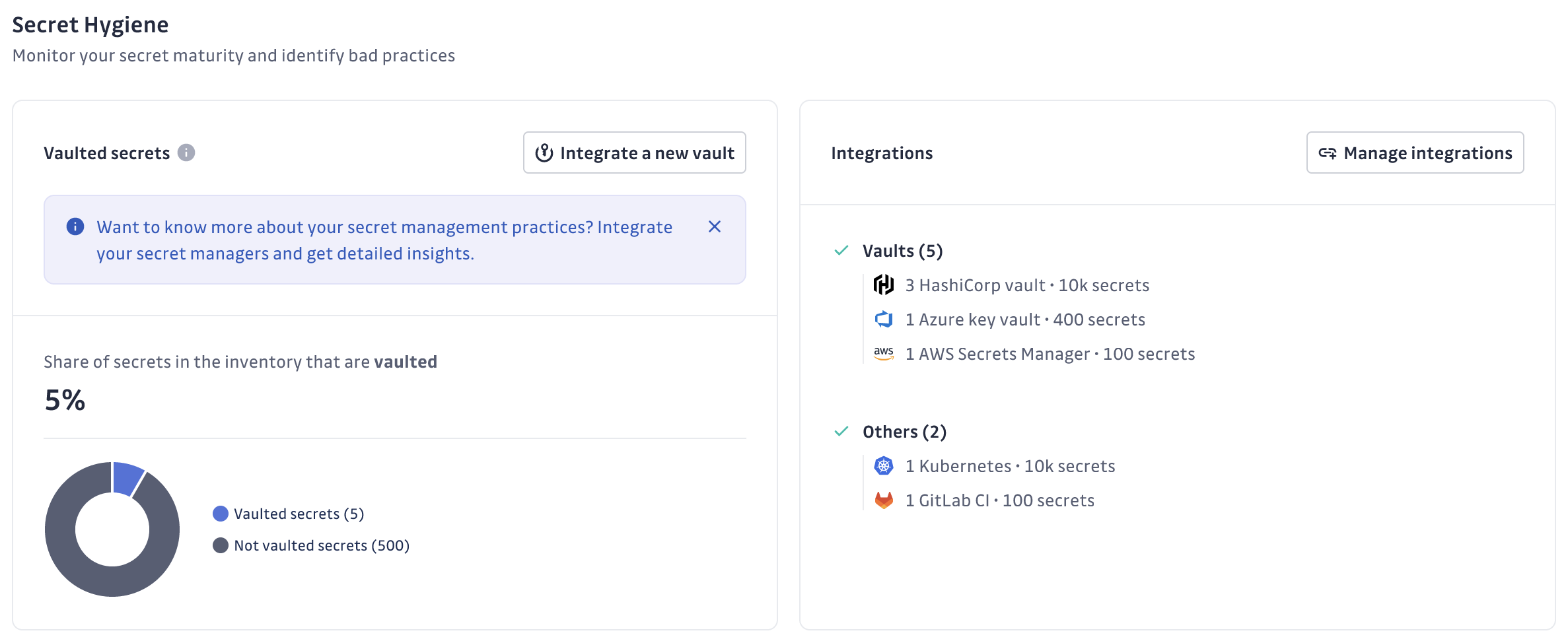
Centralized secrets inventory: Gain a comprehensive view of your secrets ecosystem by integrating with existing secrets management solutions like HashiCorp Vault, CyberArk Conjur, AWS Secrets Manager, Google Cloud Secrets Manager, Azure Key Vault, Akeyless, and Delinea. This provides a single source of truth for all secrets and NHIs, enhancing visibility and control.
Lifecycle management: Exercise granular control over the entire secrets lifecycle, enforcing best practices for rotation and revocation. This helps to automate some of the lifecycle management tasks and streamline workflows, increasing operational efficiency and reducing the risk of stale or cross-environment credentials.
Deep contextual understanding: Improve your understanding of the potential impact of a breach with actionable context around secrets, including permissions, owners, access patterns, and usage. This contextual information accelerates incident investigation and resolution. GitGuardian users report a reduction in remediation time from days or weeks to minutes or hours.
Detection and remediation: Identify internal sprawl and external leaks, and receive actionable remediation guidance directly within the platform. The integrations with secrets managers can be used to vault and rotate exposed secrets, reducing the risk of security breaches and improving overall secrets management hygiene.
Advanced analytics: Optimize permissions, identify overprivileged NHIs, and track hygiene trends with insightful analytics in our comprehensive dashboard. Monitor key hygiene metrics like vault coverage and secrets' age distribution.
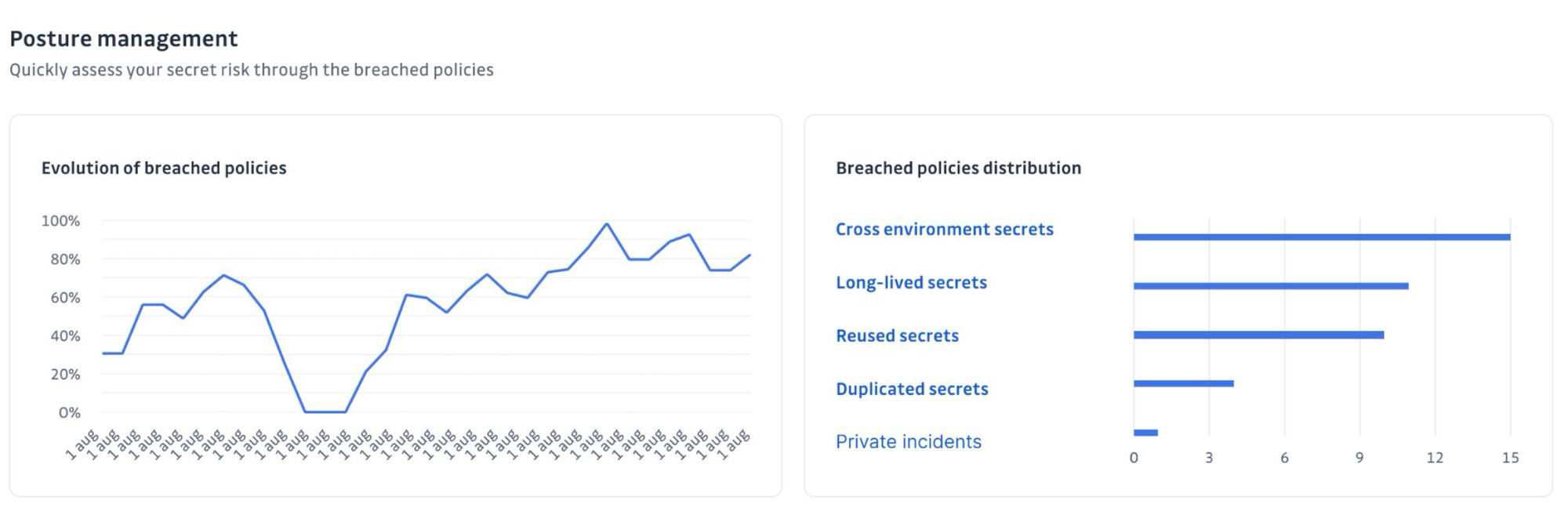
Policy enforcement: Track the evolution of breached policies over time, understand their distribution across your environment. Enforce consistent security policies across all vaults with a policy engine to assess your posture against regulations, including the OWASP Top 10, simplifying compliance.
Some Enterprise Use Cases
GitGuardian NHI Governance delivers significant value across various enterprise scenarios:
Security operations enhancement
Security teams can comprehensively inventory all API keys utilized by microservices, identify unprotected credentials, and implement secure vaulting and rotation protocols.
Identity access management optimization
IAM specialists can analyze permissions granted to secrets, identify excessive privileges, and implement precise access controls based on the principle of least privilege.
Regulatory compliance assurance
Compliance officers can leverage the centralized inventory and policy framework to demonstrate adherence to data security regulations and industry standards.
Incident response acceleration
During security incidents, response teams can rapidly identify affected systems, determine credential ownership and permission scope, and provide specific rotation guidance.
Vault migration support
Organizations transitioning between secrets management platforms can identify all existing credentials, their locations, and dependencies to ensure seamless migration without service disruption.
The Stakes Couldn't Be Higher
In a world where identities have become the new perimeter, controlling NHIs isn't just a security nice-to-have—it's survival. We understand the pressure your teams are under already. With each leaked secret potentially costing millions in breach remediation, reputation damage, and business disruption, the question isn't if you can afford to have secrets governance, but rather, can you afford not to?
To learn more about how GitGuardian NHI Governance can help your organization control secrets sprawl and secure your NHIs, and to see how we can make this process easier for you, request a demo!