Directly East of Orlando, Florida, sits the Kennedy Space Center. Home to one of the largest buildings on earth, covering 8 acres, it is best known as NASA's primary launch center of American spaceflight. The location is surrounded by the beautiful Merritt Island National Wildlife Refuge, home to many bird species, which makes it the perfect home for a museum and science center devoted to learning about our advances in flight and space travel. It was at the KCS Center for Space Education that cybersecurity professionals gathered to advance their skills and share knowledge at HackSpaceCon 2024.
With the word 'hack' right in the name, this conference was very much a red team and pentester-forward event. The keynote kicking off the event was from legendary offensive security leader Dave Kennedy, in which he shared some detailed stories from his time and the field and motivated us to look forward to the challenges ahead, especially as AI is changing the world. He encouraged us to lay traps and make some of our cyber deception efforts more obvious, as nothing scares an attacker more than being taunted by an obvious trap, basically saying, "Come at me."

Dave set the tone for the rest of the event. The dozens of workshops and over 50 talks throughout the event focused on getting ready to embrace the coming challenges in the age of AI and LLMs while also, at times, returning to the basics and how we still have a long way to go to keep all our systems and organizations secure. Here are just a few of the highlights from HackSpaceCon 2024.
AI is going to make it harder and easier to get our jobs done
In his presentation "Red/Blue/Purple AI: Practical AI for Security Practitioners," Jason Haddix, CEO and Founder of Arcanum Security, shared his explorations into improving our tools through artificial intelligence. He began by showing how AI-assisted phishing attacks have become far more sophisticated in a very short time, producing emails that even seasoned security professionals would fall for. AI models can now analyze vast amounts of personal data from social media to craft highly personalized and convincing phishing emails.
Jason also delved into AI's role in creating dynamic and adaptable malware payloads, which are specifically designed to evade detection by security systems like CrowdStrike and CarbonBlack. By constantly adapting and evolving, these AI-driven threats pose a significant challenge to existing cybersecurity defenses, underscoring the need for continuous advancements in AI security solutions.
But it is not all bad news. Jason also showed multiple examples of using ChatGPT and other AI tools to assist with defense. For example, since tools like Nuclei and Nessuss have pretty fantastic documentation, assist tools can be quickly trained to produce advanced policies. Jason said he also has been working on a SecGPT security bot, which he has been using to dig into security questions he did not want to ask in public, as a way to explore technology training. He concluded by saying we are generally safe from AI being a direct security threat for now. Still, things are evolving quickly, and we need to embrace leveraging AI with our tools before attackers gain the lead.

There is more critical infrastructure than you might think.
Soledad Antelada, Security Technical Program Manager Office of the CISO at Google, began her talk "Dissecting Critical Infrastructure Attacks – Cybersecurity Lessons from Real World Breaches," by explaining critical infrastructure involves far more than just power grids and water systems. It is anything that keeps our lives running as expected, from banking systems and internet service providers to oil and gas refineries and pipelines to election-related systems. Protecting it is not optional, and unfortunately, it has been targeted more and more in recent years.
Soledad discussed how digital transformation, combined with legacy systems that often go unpatched, creates a fertile ground for cyberattacks. She walked us through several landmark breaches, including the Stuxnet attack, the Colonial Pipeline ransomware incident, SolarWinds, and Dyn DDoS, which disrupted a large percentage of the internet. These examples show the sophisticated nature of modern cyber threats and the extensive preparation and execution involved. She said a multi-layered approach is absolutely necessary for defending critical infrastructure, which involves not only technological solutions but also regulatory compliance and cross-sector cooperation.
Cybersecurity measures and policies, such as MFA and biometrics, need to be introduced earlier in the planning and implementation phases of infrastructure projects. As we modernize older systems, we need to implement network segmentation and better role-based access as well as enforce patch management strategies. She concluded with a call for a proactive stance on cybersecurity with better security audits. She urged us all, no matter what organization we work in, to anticipate potential threats and embed security into the very fabric of our operational structures.

Getting on the same page about red teaming
Author, pentester, and podcast host Phillip Wylie started his talk "Offensive Security Awareness" by claiming that most security people assume everyone 'just knows this stuff' when it comes to security basics. But like everything else in life, no one is born knowing everything, so his goal was to get everyone on the same page, especially folks working on the 'red team' and get us in the state of mind of a threat actor.
Phillip said the overall goal of all of our efforts should be to identify and address security vulnerabilities before they are exploited. He defined terms like "offensive security," which involves assessing the security of in-scope targets from a threat attacker's perspective. He walked us through the differences between "vulnerability management" and "vulnerability assessment," where the latter also weighs exploitability. He compared the three major types of penetration tests, "black box," where you know nothing; "gray box," where you get certain details and is the most common type; and "crystal box," engagement, where you have full access to all documentation for the system.
Furthermore, Phillip stressed the necessity of continuous education and training in the cybersecurity field. He noted that many security breaches occur due to a lack of basic security knowledge among staff. Therefore, simplifying and disseminating offensive security concepts across all levels of an organization is crucial. His call to action was clear: equip individuals with the knowledge to understand and participate in the security process more actively. Folks looking to dive deeper into these topics can pick up a copy of his book "The Pentester Blueprint."

Hacking without exploiting technical vulnerabilities
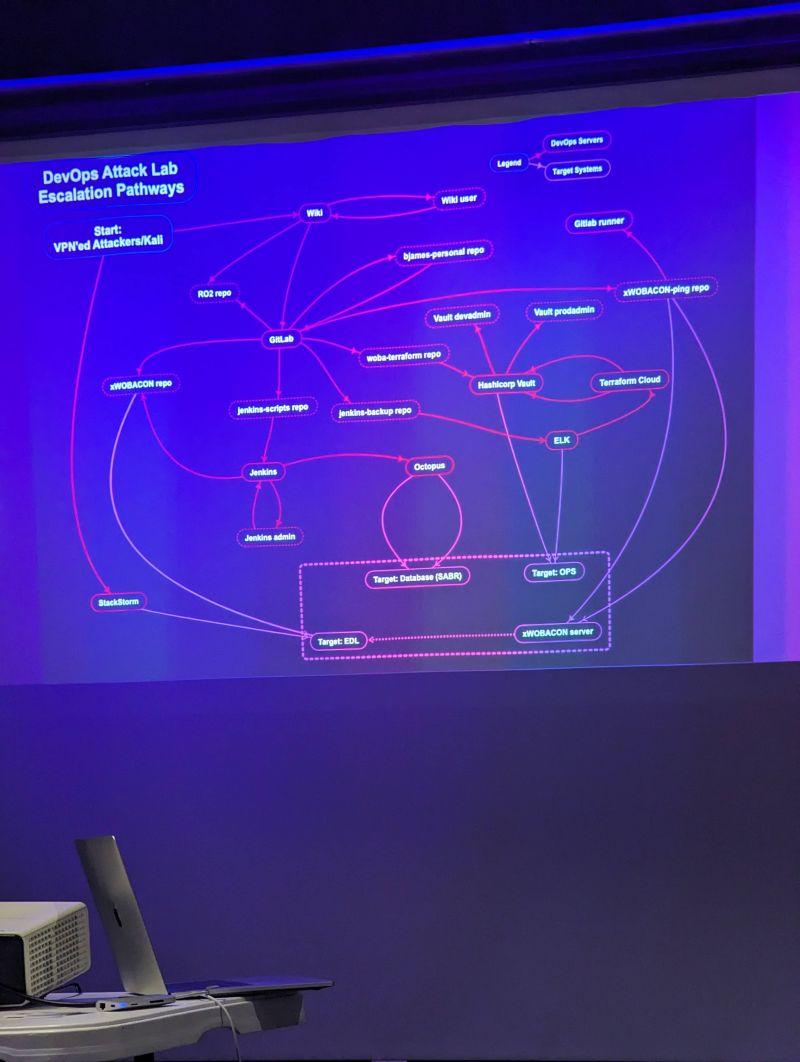
In the highly informative and baseball-themed workshop "Attacking DevOps Pipelines" delivered by Tom Porter & Colbert Zhu, both Security Consults at Accenture, we executed a full attack against a fictional company, all without exploiting a single technical vulnerability. The scenario they set up for this workshop was based on multiple real-world engagements they had performed and executed with just a browser, a terminal, and a handful of open-source tools found in Kali Linux. The factors they exploited were default and leaked credentials in every environment along the attack path.
After explaining some DevOps concepts, we jumped straight into the range they set up, a specific set of containerized environments meant to be attacked legally. Starting in the fictitious target company's wiki, we quickly uncovered a user who had never updated their default password and quickly gained access to many private files. With just the built-in search of the wiki, we were able to sleuth our way through access to GitLab, Jenkins, Octopus, and multiple other services throughout their production pipeline. Then using some pre-built tools and scripts easily found on GitHub, we were able to dump credentials and log files full of secrets from these systems, allowing us lateral movement, simulating how they carry out real-world pen tests.
The biggest takeaway from this session was that the problem of secret sprawl is very, very real. They stressed that they often see a much higher volume of leaked secrets in the wild than the handful they included in the exercise. While they admitted most attackers go after Active Directory in real-world attacks, that was not necessary to still be successful. They also said there was no need for any advanced technical knowledge of CVEs or technical exploits for most of their engagements, as the needed keys were easily uncovered as they went. I walked away thinking we are fortunate there are some great solutions out there to help you tackle the issue of secrets sprawl at scale.
Preparing for the future of cybersecurity, together
Across these diverse talks, a common theme emerged: the future of cybersecurity means nailing the basics while leveraging AI to assist us with our existing tools. One of those basics that came up in almost every talk was secrets security. Your author also gave a talk about better leveraging the automation platform Git Hooks, built into the world's favorite source control management system to keep secrets out of your commits.
HackSpaceCon 2024 also coincided with the launch of a SpaceX shuttle launch, which we were able to see as the weather cooperated and gave us a clear sky. It was just another way this group of cybersecurity professionals connected to form a real community. A community that is future-looking and proactively working to keep us all safe. I am already looking forward to next year's event and hope to see another shuttle launch, and you, there.









