As organizations embrace cloud-native architectures and microservices, the number of machine identities such as applications, containers, CI/CD pipelines, and IoT devices has exploded. Security experts call this a "machine-first world" where non-human actors vastly outnumber human users.
This transformation has exposed the fundamental weakness of traditional secret management. For decades, organizations have relied on static secrets like API keys, passwords, and tokens that function as unique identifiers for workloads. While this approach provides clear traceability, it creates an operational nightmare of manual lifecycle management, rotation schedules, and the constant risk of credential leakage.
What Are Managed Identities
Rather than embedding static credentials into applications, modern platforms now provide identity services that issue short-lived, automatically rotated credentials to authenticated workloads. This includes cloud providers, CI/CD systems, and other infrastructure platforms.
How Major Platforms Are Eliminating Static Credentials
Each major cloud provider has developed sophisticated managed identity systems, though their approaches differ significantly. AWS pioneered the concept with IAM Roles for EC2 instances, where the metadata service automatically provides temporary credentials without requiring any static keys. This pattern has expanded to Lambda functions, EKS clusters through IAM Roles for Service Accounts (IRSA), and virtually every AWS service.

Azure took this concept further with Managed Identities that extend across their entire service portfolio. A Function App can seamlessly authenticate to Key Vault, Storage, and other Azure services using its managed identity, eliminating the need for connection strings entirely. Google Cloud's approach centers on Service Accounts enhanced with Workload Identity Federation, enabling sophisticated scenarios where workloads running outside Google Cloud can authenticate using their existing identities.
The revolution extends beyond cloud providers to CI/CD platforms. GitHub Actions now supports OpenID Connect (OIDC) tokens that allow workflows to authenticate directly to cloud providers and other services without storing long-lived secrets. Similarly, GitLab's OIDC provider enables CI/CD pipelines to obtain temporary credentials for cloud deployments, eliminating the need to store AWS access keys or Azure service principal secrets in pipeline variables.
The evolution is perhaps most visible in Kubernetes, where service accounts have transformed from simple static token holders to sophisticated identity bridges that can map to cloud IAM roles without ever exposing static credentials.

The Cross-Cloud Authentication Challenge: Why Static Secrets Don't Scale
The complexity of this transformation becomes apparent when organizations operate across multiple clouds. Consider the perspective of a DevOps engineer managing a multicloud environment: "Having a workload in Azure that needs to read data from AWS S3 is not ideal from a security perspective. Cross-cloud authentication and authorization complexity makes it hard to set this up securely, especially if we choose to simply configure the Azure workload with AWS access keys to access S3."
This real-world challenge has traditionally driven organizations toward centralized secret management solutions like CyberArk Secrets Manager or HashiCorp Vault, which provide a universal broker for secrets across platforms. While this approach offers centralized management and native synchronization capabilities, it perpetuates the fundamental problem: the proliferation of static secrets that require careful management and rotation.
Managed identities fundamentally change this equation by eliminating many of the secrets that require synchronization in the first place. Instead of managing database passwords, service API keys, and connection strings across multiple clouds, organizations can leverage native identity systems that handle authentication dynamically.
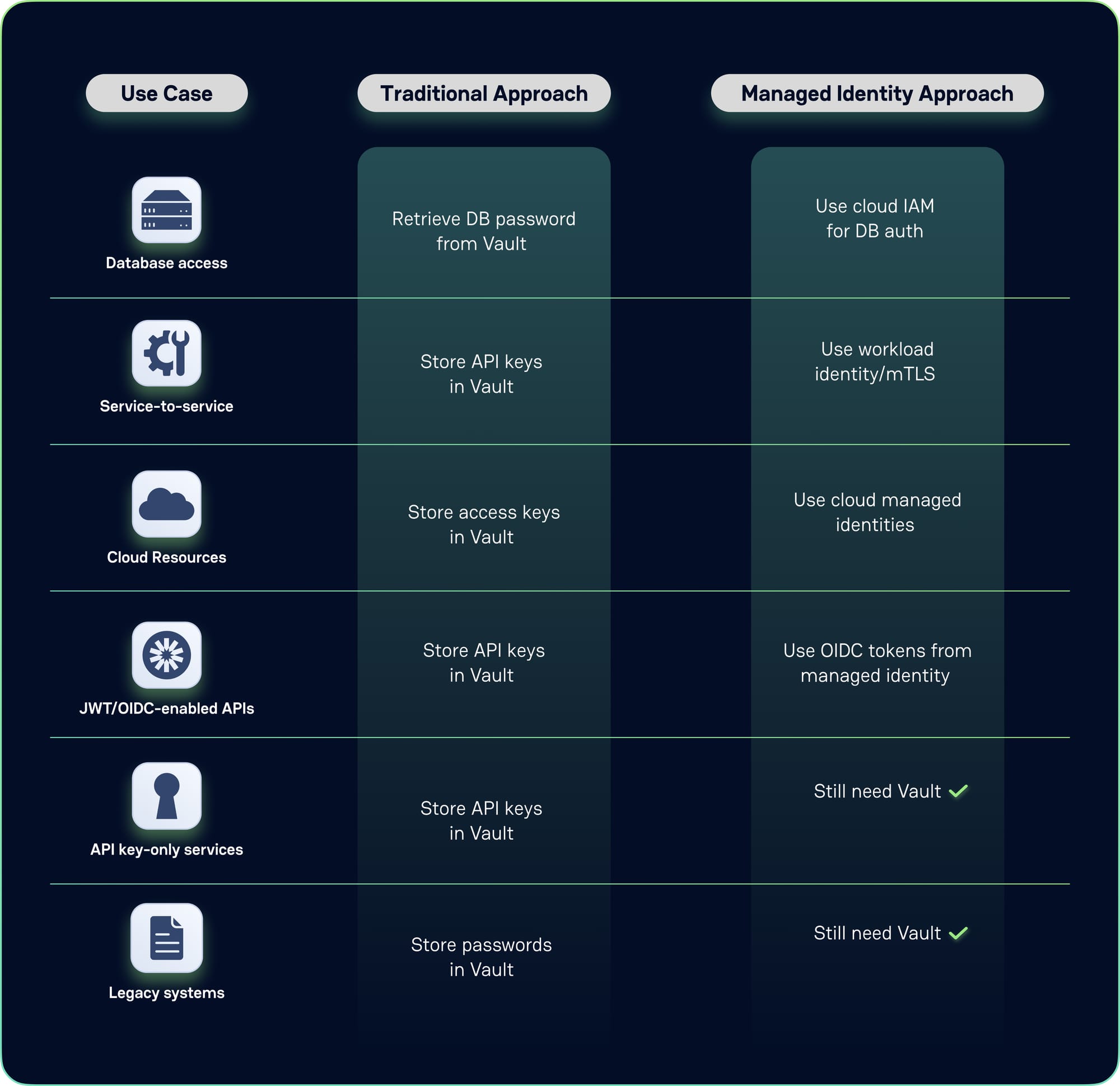
What Managed Identities Replace: From Database Passwords to API Keys
The transformation becomes clear when comparing traditional and managed identity approaches:
Traditional Approach:
Application → Static API Key → Database
Application → Static Password → External Service
Application → Connection String → Message Queue
Managed Identity Approach:
Application → Managed Identity → Database (no password needed)
Application → Workload Identity → External Service (no API key needed)
Application → Service Account → Message Queue (no connection string needed)However, the reality is more nuanced. While managed identities eliminate many secrets, they don't solve every authentication challenge. Third-party APIs still require API keys, legacy systems often can't integrate with modern identity providers, and cross-organizational authentication may still require shared secrets.
The authors of “Solving the Bottom Turtle — a SPIFFE Way to Establish Trust in Your Infrastructure via Universal Identity” say: "using a secret manager dramatically improves the security posture of systems that rely on shared secrets, but heavy use perpetuates the use of shared secrets rather than using strong identities". The goal isn't to eliminate secret managers entirely, but to dramatically reduce their scope.
Architecture Patterns for the Real World
Modern multicloud architectures increasingly adopt a hybrid approach that strategically combines managed identities with traditional secret management:
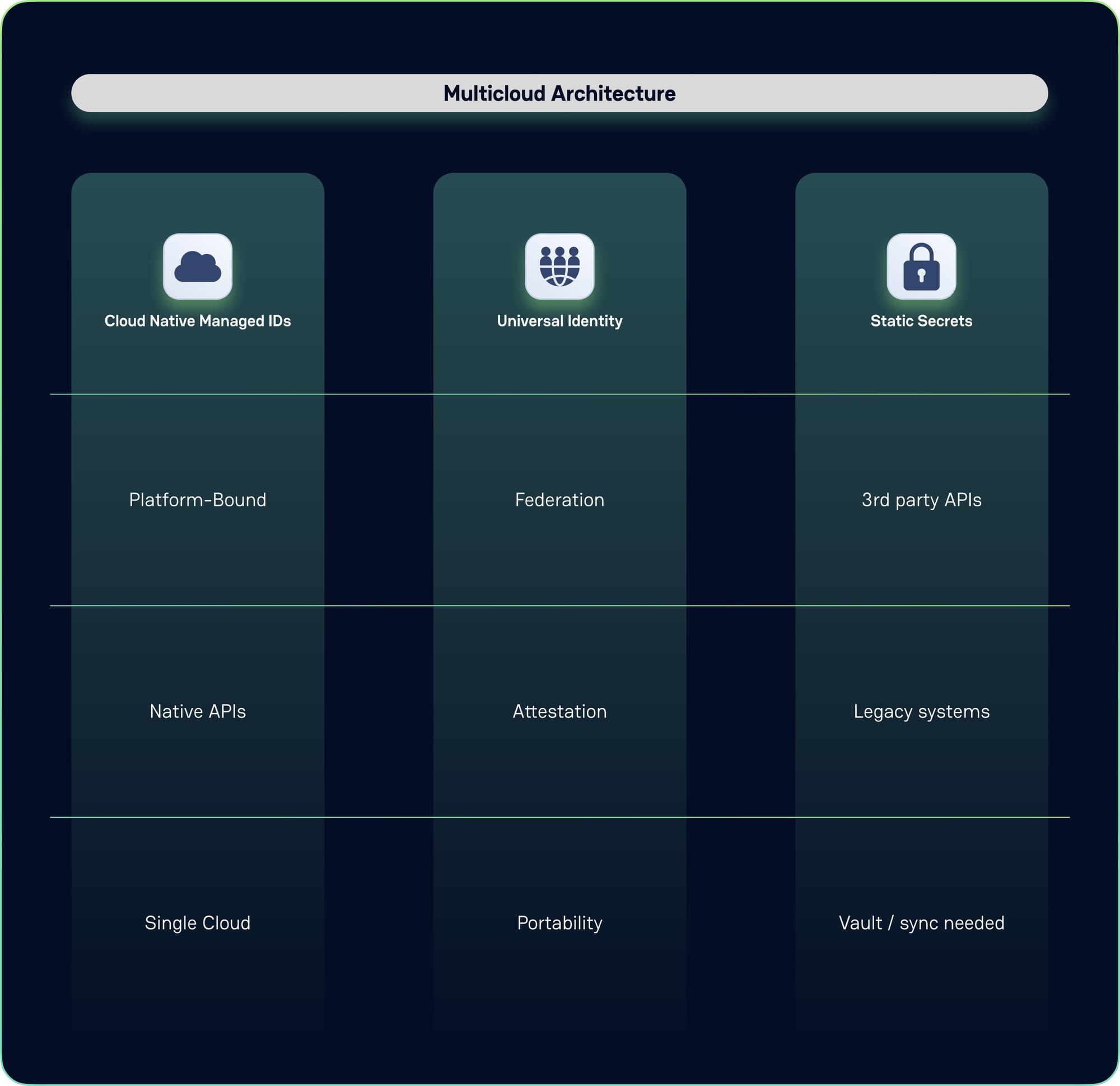
This architectural pattern reflects the practical reality. Some workloads can fully embrace managed identities. Others need hybrid approaches that bridge different identity systems. And some still require traditional secret management for legacy systems that can't be modernized.
The Economics of Identity
The business case for managed identities extends beyond security improvements. Organizations implementing these systems report dramatic productivity gains. Enterprise case studies document a 95% reduction in time spent managing credentials per application component, and a 75% reduction in time spent learning platform-specific authentication mechanisms, resulting in hundreds of saved hours annually.
The security benefits are equally compelling. By shifting from static credentials to cryptographic identities, organizations enable automatic rotation, reduce their attack surface, and create better audit trails. As one healthcare organization implementing managed identities noted, "We wanted to shift away from secret management practices in general. Instead of asking a service, 'what do you have,' we want to ask, 'who are you'".
When to Use Cloud-Native vs. Universal Identity Solutions
The decision framework for managed identities depends heavily on your architectural context:
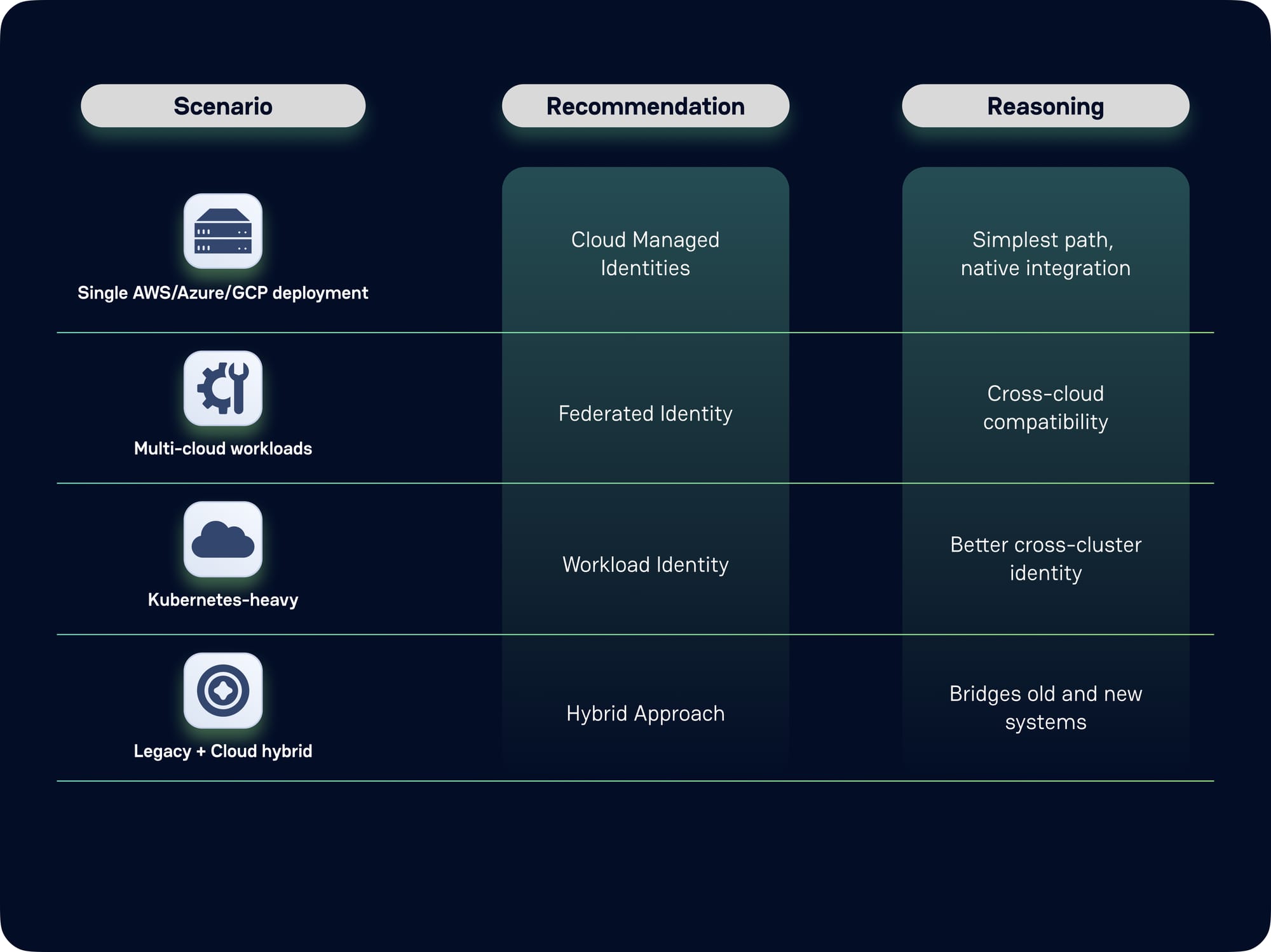
The migration path typically follows a predictable pattern: start with cloud-native workloads using platform-native managed identities, expand to cross-cloud scenarios through federation, and gradually reduce reliance on static secrets through automation and integration.
It's important to understand how managed identities compare to other identity approaches. The choice isn't always binary - sometimes you need a combination of strategies:
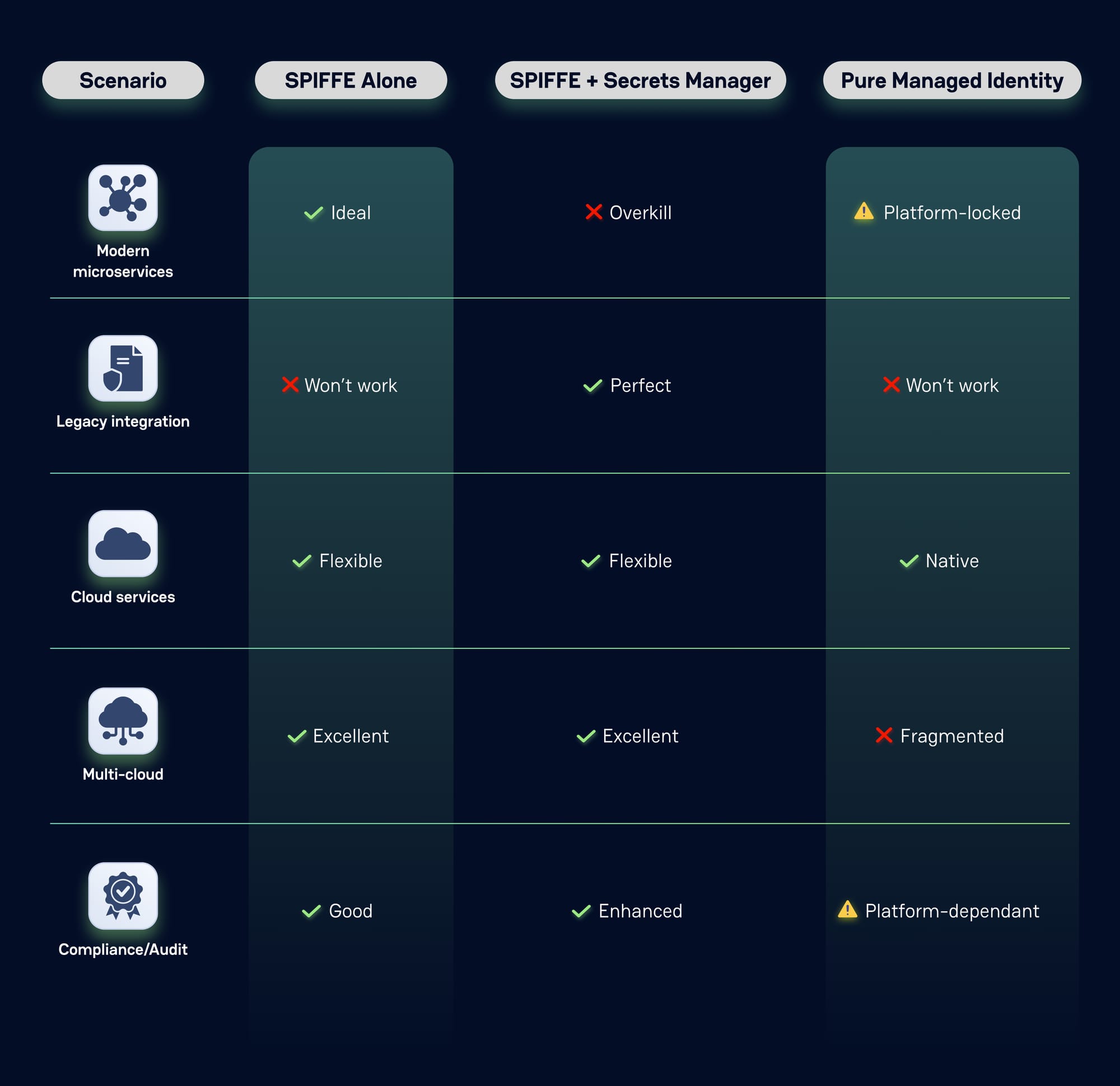
This comparison reveals why many organizations end up with hybrid approaches. Pure managed identities excel for cloud-native scenarios but struggle with legacy systems and true multi-cloud portability. Universal identity solutions provide flexibility but add operational complexity compared to simple, single-cloud managed identities.
Emerging Standards: Building Interoperable Identity Across All Platforms
The industry is converging on standards that will make managed identities even more powerful and interoperable. Emerging frameworks aim to create "a common language for workload identities across clouds and platforms," enabling standard translation between identity formats and eliminating the custom integration work that currently complicates multicloud authentication.
This standards-driven future promises to resolve the tension between vendor-specific managed identities and the need for universal, portable workload identity. Organizations that begin their managed identity journey today are positioning themselves to take advantage of these emerging standards as they mature.
The transformation from secret management to identity management represents more than a technical upgrade—it's a fundamental shift toward more secure, scalable, and maintainable authentication architectures. In a world where machine identities outnumber human users by orders of magnitude, managed identities provide the foundation for the automated, auditable, and secure systems that modern organizations require.