Centralized discovery, contextual inventory, and automated auditing are critical.
Learn how modern solutions like GitGuardian address these challenges to reduce NHI risk, enforce zero trust, and maintain compliance.
Machine identities such as service accounts and API keys greatly outnumber human identities, but they tend to lag far behind when it comes to identity lifecycle management maturity.
NHIs are harder to centralize and automate than human identities, and we will explore the reasons for that in this article. However, we will also cover how the industry is starting to tackle this problem. By the end of this blog post, you will understand how you can improve your identity lifecycle management processes and reduce your NHI risk by utilizing secret inventory and discovery tools like GitGuardian.
Challenges with NHI lifecycles
Without a solid process for identity lifecycle management (ILM), you increase the number of NHI-related risks like:
- shadow credentials that aren’t stored in a vault
- zombie credentials that are no longer in use but still active
- excessive permissions that don’t adhere to zero trust practices
- sharing secrets over unsafe channels
- storing secrets in exposed locations
Identity lifecycle management is a really difficult thing to implement, though. In the following sections, we will explore the biggest challenges that cause NHIs to get lost, forgotten, and mismanaged.
Auditing and Monitoring NHIs
At the center of what makes non-human identities so complex to manage is the huge number of third-party systems that our apps interact with. All these systems have their own authentication flows, roles, and permission schemas, which makes it extremely difficult to have full visibility across every environment and tool.
So, how do you track non-human identities amid such a complex ecosystem of integrations? GitGuardian has a two-part answer to this question.
First, GitGuardian makes it easy to discover and create an inventory of your NHIs using their industry-leading secrets discovery capabilities. No matter the complexity of your third-party integrations or the number of NHIs you have, you can find all of them in the places they should be and the places they shouldn’t be.
Second, GitGuardian adds critical context to each NHI in your inventory using a tool they recently released called NHI Governance. With this new solution, GitGuardian integrates with third-party systems and helps you monitor your NHIs by:
- identifying which NHIs are active, vaulted, or exposed
- auditing how NHIs interact with resources across environments
- highlighting overprivileged NHI credentials
- defining who owns and is responsible for each NHI
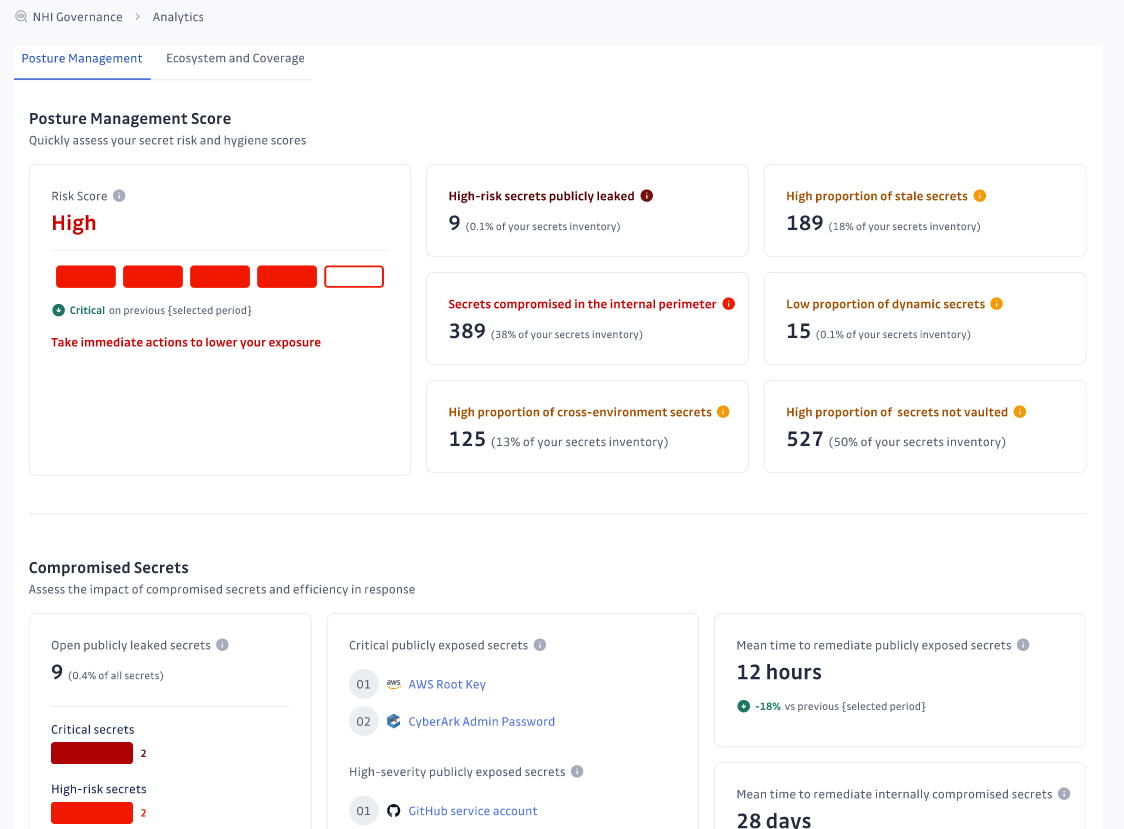
The screenshot below is an example report that highlights the new NHI auditing capabilities of GitGuardian:
Secret Rotation Complexity
Another challenge of identity lifecycle management is secret rotation. Every third-party integration has its own process for rotating secrets, and some platforms make secret rotation pretty difficult if you want to minimize downtime (see the Airbrake key example from the blog post How to Become Great at API Key Rotation).
Secret managers like HashiCorp Vault and CyberArk Conjur provide built-in functionality to auto-rotate secrets for you, but they don’t cover every kind of NHI, and you must make sure that all your secrets are vaulted and configured for auto-rotation to take advantage of the features.
Beyond automation, there are other struggles that make secret rotation difficult. When you are dealing with a leaked NHI, it’s not always clear who the owner is that is responsible for doing the rotation.
GitGuardian aims to assist with the complexities of secret rotation too. GitGuardian’s detection platform has always helped identify the correct owner of a secret, and the new secret manager integrations allow you to audit whether an NHI’s credential is in any of your vaults. If the credential is in your vault, GitGuardian will also tell you whether it’s a dynamically rotated secret or not.
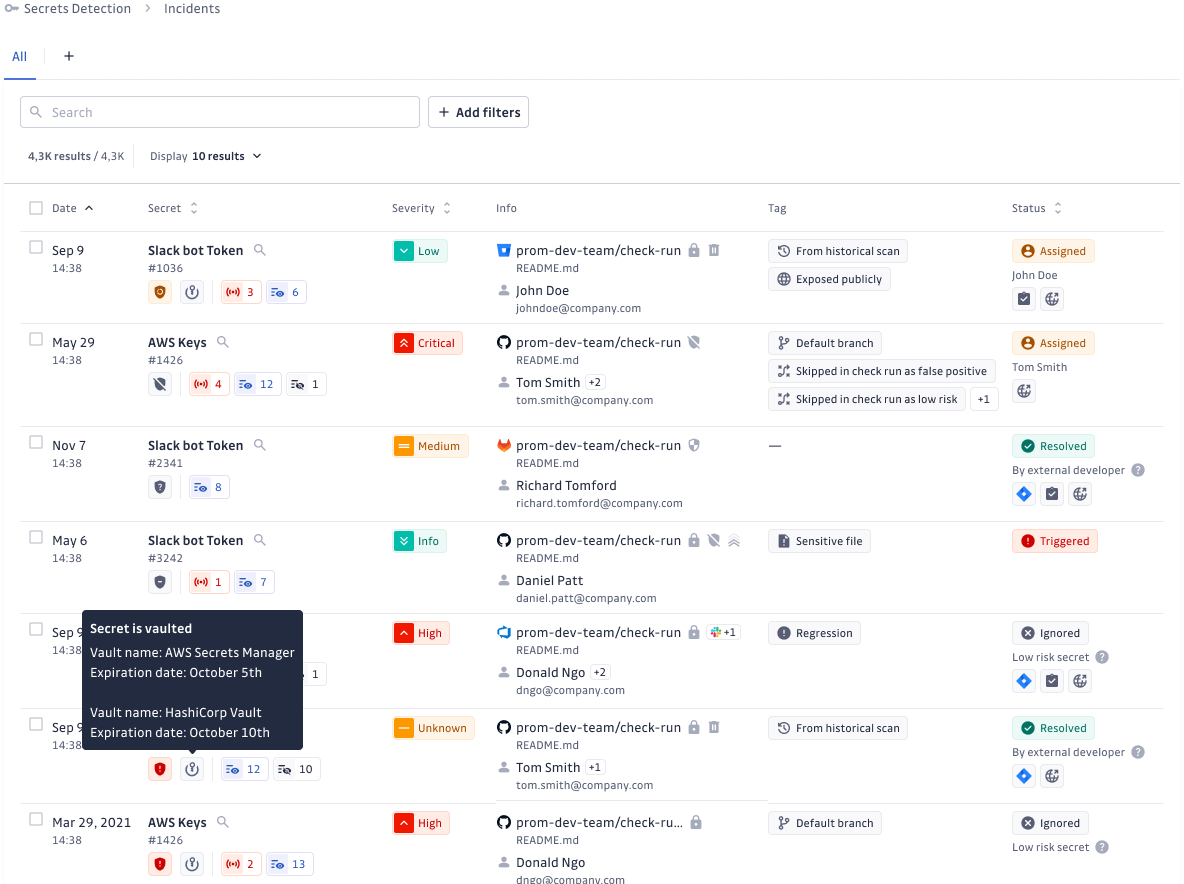
In the example above, we can see that a leaked secret was found to be stored in both AWS Secrets Manager and HashiCorp Vault. The usage of multiple secret managers brings us to our next challenge, and an additional benefit of GitGuardian that we haven’t covered yet.
Fragmented Tooling
Unified observability over the lifecycle of all your NHIs is extremely difficult because most enterprises use multiple secret management tools. Within a single organization, you might find secrets that live in password managers, IAM tools, modern secret vaults, or even inappropriate places like documentation tools.
If you want to have proper lifecycle management for your non-human identities, a prerequisite is to have a comprehensive inventory of your NHIs that tells you where they all live. This takes a tool like GitGuardian that can integrate with all your secret management tools and find secrets where they shouldn’t be. Only then will you be able to manage the lifecycle of all your NHIs.
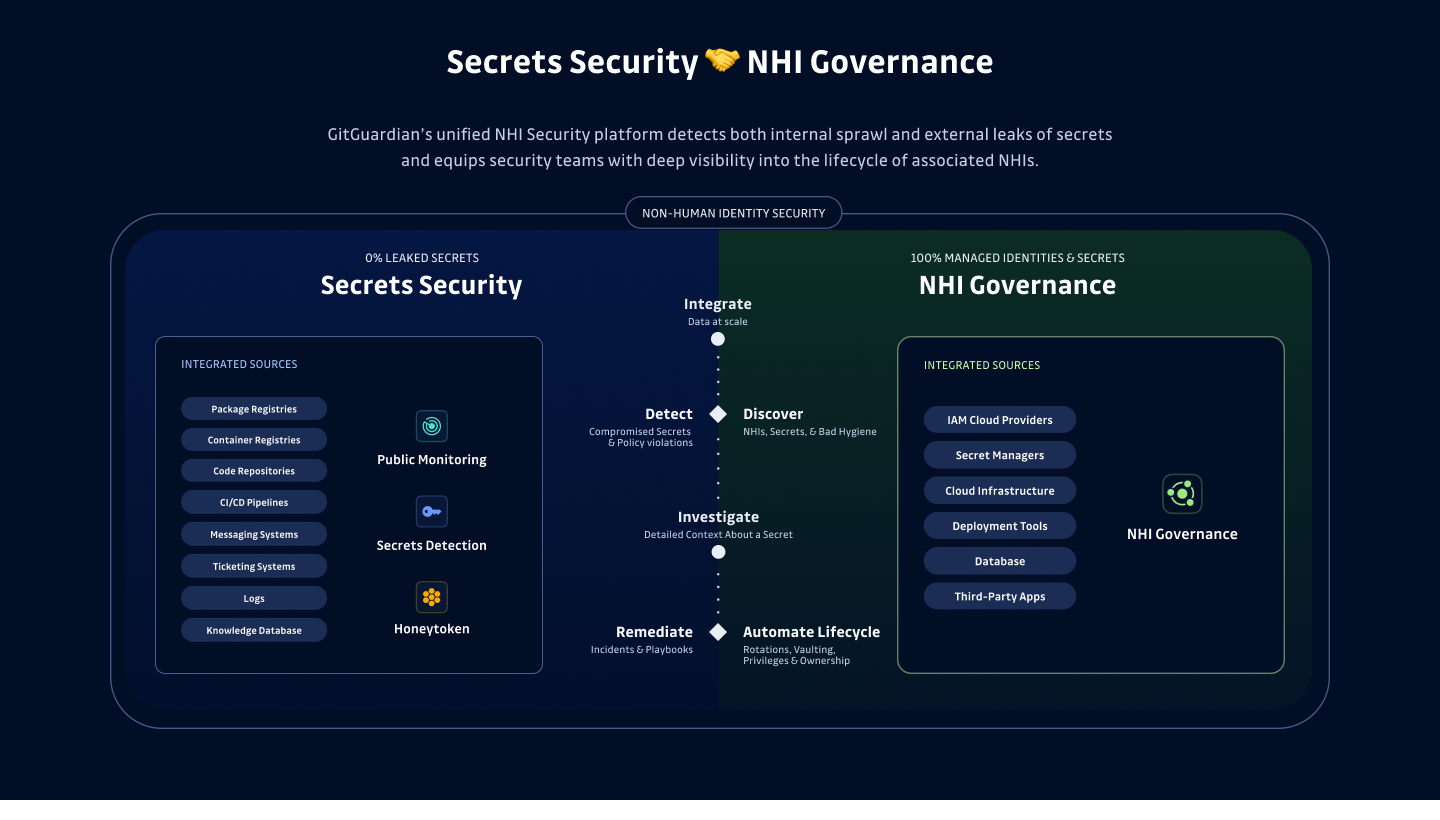
Once you have a comprehensive inventory of your non-human identities, you can start to use the additional context that we covered earlier to manage various stages of each identity’s lifecycle like creation, zero trust permissions, and storage.
Decommissioning NHIs
The last stage of a non-human identity’s lifecycle, decommissioning its credentials, can be easy to forget about. For digital human identities, the creation and deletion of an identity are closely tied to the onboarding and offboarding of the employee or user. For NHIs, the lifecycle is a bit more complex.
In an ideal world, every owner of every NHI would remember to revoke credentials when their application no longer needs access to a third-party system. In reality, factors like employee turnover, lack of observability, and secrets sprawl make it difficult to decommission an NHI. Luckily, governance solutions like GitGuardian are going after this too by telling you:
- When a secret was last rotated
- Whether it has gone stale
- Whether it has high permissions
Using these pieces of information across a comprehensive inventory of NHIs, you can identify which secrets need to be evaluated for decommissioning. No more zombie credentials!
The Five Phases of Identity Lifecycle Management
Identity lifecycle management phases provide a structured framework for governing digital identities from creation to decommissioning. The traditional model encompasses five critical stages: provisioning, authentication, authorization, maintenance, and deprovisioning. For NHIs, the provisioning phase involves creating service accounts, generating API keys, and establishing machine-to-machine authentication credentials. The authentication phase ensures these identities can securely verify themselves to target systems, while authorization defines what resources each NHI can access.
The maintenance phase presents unique challenges for non-human identities, as it requires continuous monitoring of credential usage, permission reviews, and regular rotation schedules. Unlike human identities tied to employment status, NHI maintenance depends on application lifecycle events and business process changes. The final deprovisioning phase removes access rights and revokes credentials when applications are retired or integrations are discontinued. Organizations often struggle with this phase because NHI ownership may be unclear, leading to zombie credentials that persist long after their intended purpose has ended.
Identity Lifecycle Management vs Traditional IAM: Key Differences
While traditional Identity and Access Management (IAM) focuses primarily on human users, identity lifecycle management encompasses a broader scope that includes both human and non-human identities. Traditional IAM systems excel at managing employee onboarding, role-based access control, and offboarding processes tied to HR systems. However, these systems often fall short when managing the complex relationships between applications, services, and their associated credentials.
The fundamental difference lies in the lifecycle triggers and ownership models. Human identity lifecycles are typically driven by HR events, hiring, role changes, and terminations, with clear ownership and accountability structures. NHI lifecycles, conversely, are driven by application development cycles, infrastructure changes, and business process evolution. This creates a governance gap where NHIs may outlive their original purpose, accumulate excessive permissions over time, or become orphaned when development teams change.
Modern identity lifecycle management solutions must bridge this gap by providing unified visibility across both human and non-human identities, enabling organizations to apply consistent governance policies regardless of identity type while accommodating the unique characteristics of each category.
Implementing Zero Trust Principles in NHI Lifecycle Management
Zero trust principles fundamentally transform how organizations approach identity lifecycle management for non-human identities. The core tenet of "never trust, always verify" requires continuous validation of NHI credentials and permissions throughout their entire lifecycle. This means implementing just-in-time access provisioning, where NHIs receive minimal permissions for the shortest duration necessary to complete their tasks.
In practice, zero trust NHI management involves dynamic credential generation, short-lived tokens, and continuous risk assessment based on usage patterns and environmental context. Organizations must establish baseline behaviors for each NHI and implement anomaly detection to identify suspicious activities that may indicate compromise. This approach requires integration between secrets management platforms, identity governance tools, and security monitoring systems to create a comprehensive view of NHI risk posture.
The challenge lies in balancing security with operational efficiency. While zero trust principles demand frequent credential rotation and minimal permissions, many legacy applications and integrations weren't designed for such dynamic environments. Organizations must gradually modernize their infrastructure to support zero trust NHI governance while maintaining business continuity and avoiding service disruptions.
Best practices
At this point, we’ve covered the main challenges of identity lifecycle management for NHIs, and we’ve touched on some of the processes and tooling that help address these challenges. Now, let’s step away from the specifics of GitGuardian for a moment and generalize some best practices for NHI governance:
- Centralize secrets management to control access to NHIs and enable automation.
- Implement tools that discover NHIs across the places they should live and the places they shouldn’t live.
- Centralize NHI observability to reduce silos and help inform identity lifecycle management.
- Enhance your catalog of NHIs with contextual information like where they live, whether they are active, and their permissions to improve your NHI security posture.
- Compare the permissions assigned to an NHI with the permissions that are actually used.
- Monitor NHI credentials for anomalous usage.
- Utilize auto-rotated and dynamic secrets where possible to limit exposure time when a secret is leaked.
If you start to think about what it takes to do each of these things well, you might realize that each item on this list is a mountain to climb. GitGuardian may not be the only solution to try and help customers with these best practices, but it is one of the most well-positioned for success with its foundation of secret discovery capabilities and integrations.
Conclusion
Hopefully, the challenges and solutions presented in this blog post have given you a clearer view of what it takes to manage an NHI’s entire lifecycle. Lifecycle management for NHIs is essential for securing critical enterprise systems, reducing risk, and maintaining compliance. If you are trying to follow zero trust principles, you cannot ignore the risk that your NHIs pose when mismanaged.
FAQ
What are the primary challenges of identity lifecycle management for non-human identities (NHIs)?
Key challenges include lack of centralized inventory, fragmented tooling, unclear ownership, difficulty in secret rotation, and the persistence of zombie credentials. NHIs often span multiple platforms and vaults, making unified governance and automation complex compared to human identities.
How does identity lifecycle management for NHIs differ from traditional IAM for human users?
Traditional IAM focuses on HR-driven events like onboarding and offboarding, with clear ownership and processes. In contrast, NHI lifecycle management is driven by application and infrastructure changes, often lacking clear ownership and consistent triggers, which increases the risk of unmanaged or orphaned credentials.
Why is secret rotation particularly complex for NHIs?
Secret rotation for NHIs is challenging due to diverse third-party integration requirements, inconsistent automation support across secret managers, and unclear credential ownership. This complexity can lead to stale or exposed secrets, increasing the risk of unauthorized access or credential compromise.
What best practices should organizations follow to improve NHI lifecycle management?
Best practices include centralizing secrets management, discovering NHIs across all environments, enhancing inventories with contextual metadata, monitoring for anomalous usage, enforcing least privilege, and leveraging automated secret rotation. These steps help reduce risk and improve governance across the NHI lifecycle.
How can zero trust principles be applied to NHI lifecycle management?
Zero trust for NHIs involves continuous validation of credentials, just-in-time access provisioning, dynamic credential generation, and ongoing risk assessment. Integrating secrets management, identity governance, and monitoring tools is essential to enforce least privilege and detect anomalous NHI behavior.
What role does tooling like GitGuardian play in effective identity lifecycle management for NHIs?
GitGuardian provides unified discovery, inventory, and monitoring of NHIs across fragmented environments. It integrates with multiple secret managers, identifies credential ownership, highlights overprivileged or exposed secrets, and supports automated remediation, enabling mature identity lifecycle management for NHIs.
This article is a guest post. Views and opinions expressed in this publication are solely those of the author and do not reflect the official policy, position, or views of GitGuardian, The content is provided for informational purposes, GitGuardian assumes no responsibility for any errors, omissions, or outcomes resulting from the use of this information. Should you have any enquiry with regard to the content, please contact the author directly.
Related Articles