With great power comes great responsibility Uncle Ben
This famous phrase is just as relevant in the realm of technology as it is in superhero comics. And when it comes to the power of infrastructure-as-code (IaC), the responsibility to secure it is particularly great.
In his latest Security Zines, Rohit Sehgal illustrates where and how things could go wrong if no guardrails are correctly set up to protect the cloud infrastructure of a company. Misconfigured systems and resources are the leading cause of security failures.
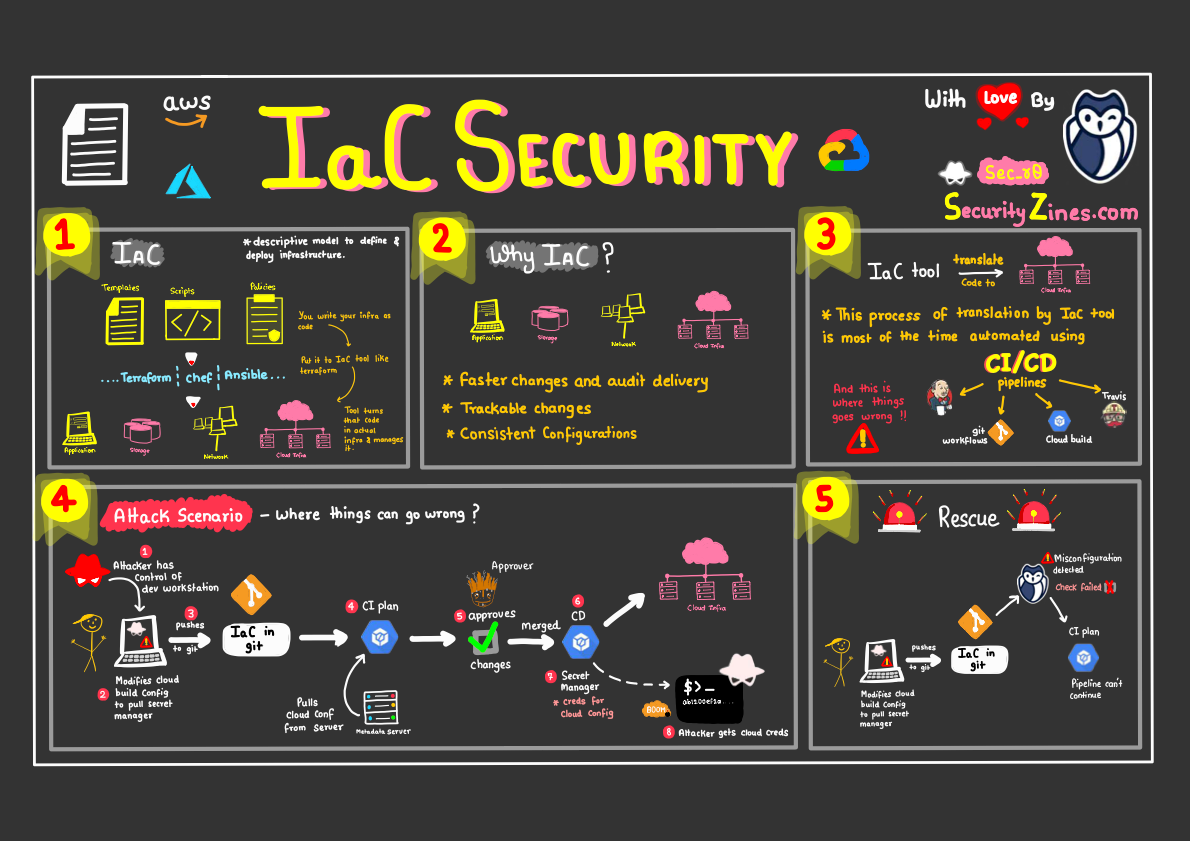
As a refresher, IaC allows organizations to define and manage their infrastructure using code, rather than manually configuring resources. This can greatly improve efficiency, automation, and consistency in managing infrastructure. However, it also introduces new security risks if not properly implemented and managed.
As with any powerful technology, it's crucial to approach IaC with a strong understanding of its potential risks and how to mitigate them.
Learn how to detect Terraform misconfigurations with ggshield
The GitGuardian's CLI, ggshield, was recently updated to support IaC misconfigurations scanning: it's as easy as ggshield iac scan path_to_iac_main_folder.
To get started with IaC Scanning, you only need a GitGuardian account! This feature is free for all GitGuardian customers at the moment.
Learn the best practices for infrastructure-as-code here:



Finally, check out our public documentation for more information on IaC security scanning capabilities.


![Infrastructure as Code Security [Security Zines]](/content/images/size/w2000/2022/12/blog-SecurityZines-iac-security.png)


![Precision & Recall [Security Zines]](/content/images/size/w600/2024/10/Recall-in-Detection.png)
![Honeytokens [Security Zines]](/content/images/size/w600/2024/09/Honeytokens.png)
![Software Composition Analysis [Security Zines]](/content/images/size/w600/2024/05/SOPS-Security-Zine--1-.png)
![SOPS [Security Zines]](/content/images/size/w600/2024/03/SOPS-Security-Zine.png)
