After years of perfecting our craft in secrets detection and remediation at GitGuardian, we have partnered with CyberArk, the leader in identity security and secrets management.
This is an industry first. It is the result of our longstanding commitment and drive to empower security and development teams to innovate while ensuring the safety of their secrets in multi-cloud, DevOps, and containerized environments.
“We're excited to partner with CyberArk, the leader in secrets management and identity security. As we all know–too often, it's human error and our failure to follow best practices that open up pathways for attackers. With our integration, security teams can be confident that they will be alerted when secrets are exposed and can take corrective action–drastically reducing the attack surface and improving their secrets security posture over time,” said Eric Fourrier, co-founder and CEO of GitGuardian.
The unique challenge of securing secrets in software development
Exposing a secret anywhere from source code to build systems and container images can allow attackers to wreak havoc inside the software supply chain. There's no shortage of examples where hardcoded secrets have been inadvertently posted to public code repositories and given attackers initial access (how a Toyota subcontractor left proprietary code and a secret exposed on GitHub for five years) or the freedom to move from one sensitive system to the next once they’re in.
The good news is application and infrastructure security teams are waking up to the reality that securing secrets is a priority and that protecting secrets by rotating, managing, and vaulting should be at the foundation of application security programs. And when developers follow best coding practices, including vaulting secrets and avoiding hardcoding, and when security teams regularly rotate them, there isn't much to worry about.
But we're all human, and we all know not every developer has security guardrails to protect them all the time. If they're prototyping an app or automation script for a quick demo, hardcoding credentials might be the path of least resistance. On the other hand, attackers don’t care that it's a simple script–they need that database credential or cloud API key. Of course, once rotated, the hardcoded secret is useless, but until that moment, it's an attack vector. Well, now, with the integration between GitGuardian and CyberArk, there's a new layer of defense.
Integrating CyberArk Conjur Cloud and GitGuardian Secrets Detection
Overview
We've created an integration to bridge GitGuardian Secrets Detection and CyberArk Conjur Cloud. This integration is a standalone service and is available as an open-source project on GitHub, providing a unique solution for security teams to detect leaks and manage their remediation.
“Working with GitGuardian, we can now provide an additional layer of defense to ensure vaulted secrets remain secure by helping security teams uncover if any of their secrets have been leaked, even when best practices have not been followed–such as when a secret was hardcoded before it was onboarded, or when a copy of a vaulted secret is exposed. We keep innovating to help ensure our customers can also innovate while staying secure. We are looking forward to what is possible with this thriving community,” said Kurt Sand, General Manager of DevOps Security at CyberArk.
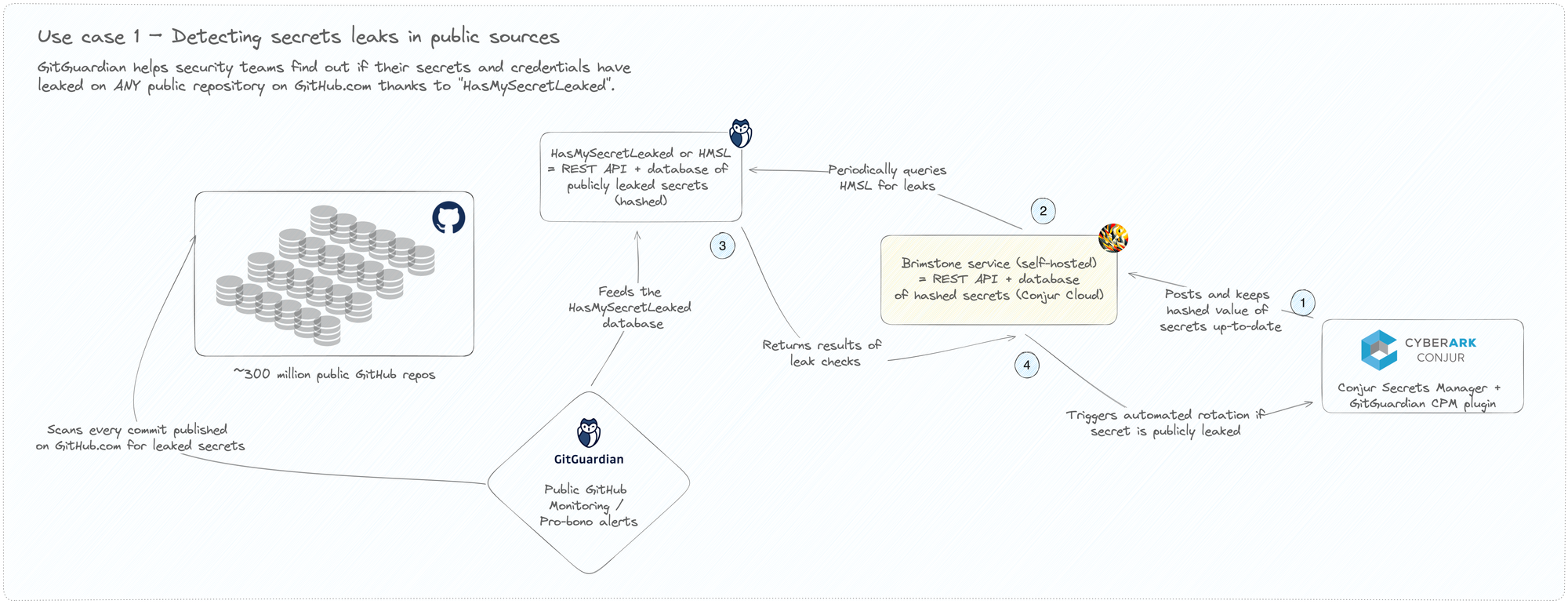
Detecting leaks in public GitHub
Our ongoing research since 2017 has led us to uncover over 20 million publicly exposed secrets on GitHub1, the world’s largest developer platform. A few months back, we announced the release of our free tool, HasMySecretLeaked, to help organizations proactively verify if their secrets have been exposed on any public GitHub repositories, gists, or issues in projects.
CyberArk Conjur Cloud is the first secrets management solution to integrate with HasMySecretLeaked. This allows security teams to periodically cross-reference their secrets and credentials against the most extensive and only private database of public leaks.
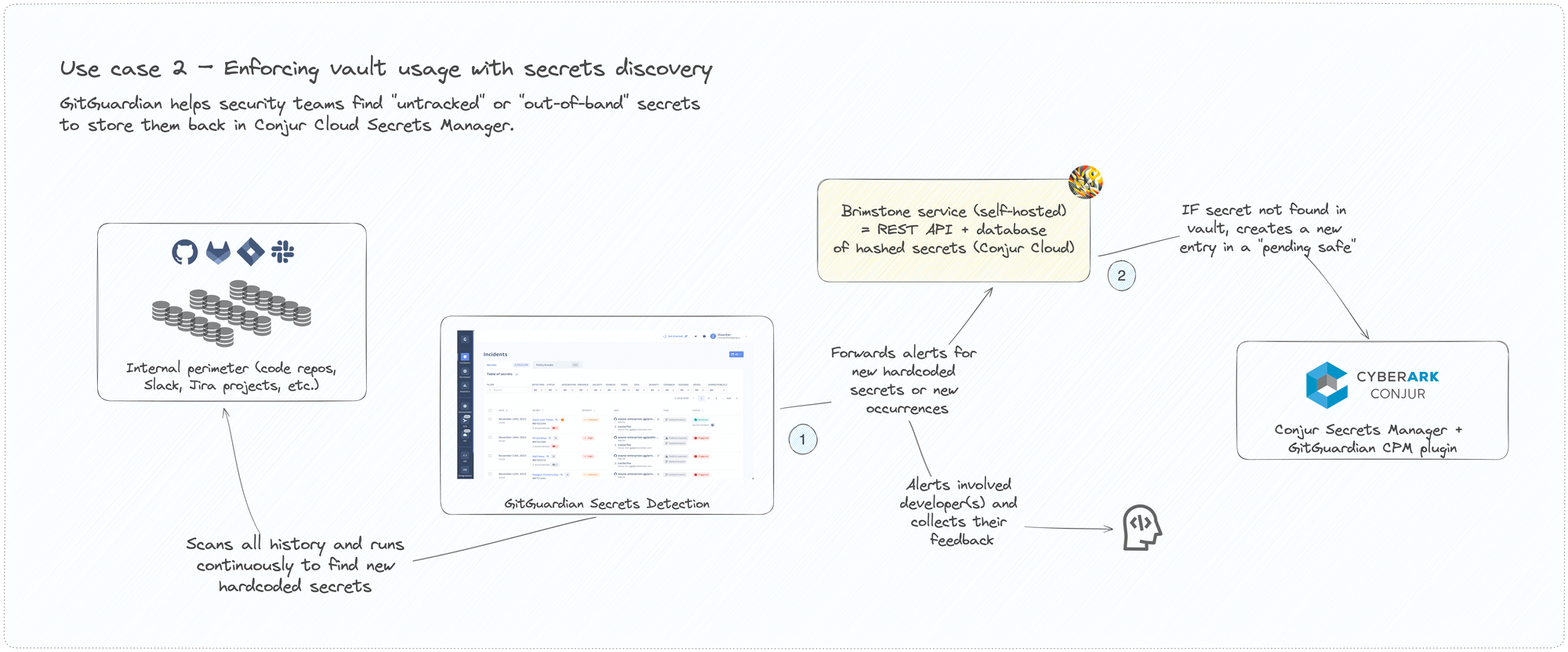
Enforcing secrets management policies
The security team can run a discovery phase to identify exposed secrets within their organization's internal perimeter. This maps the secrets attack surface and detects "shadow developer activity" and "out-of-band" secrets.
The service will identify those non-tracked secrets and reintroduce them into the Conjur Secrets Manager's centralized vault (in a pending safe) in compliance with internal policies.
Closing the hardcoded secrets remediation loop
After the initial discovery phase, GitGuardian will continuously monitor code repositories, container images, and productivity tools to detect when secrets are initially inadvertently exposed by developers or others. Conjur administrators, whether from security or engineering teams, will receive instant notifications and will trigger the remediation process, including automated feedback collection via GitGuardian and secret rotation when possible.
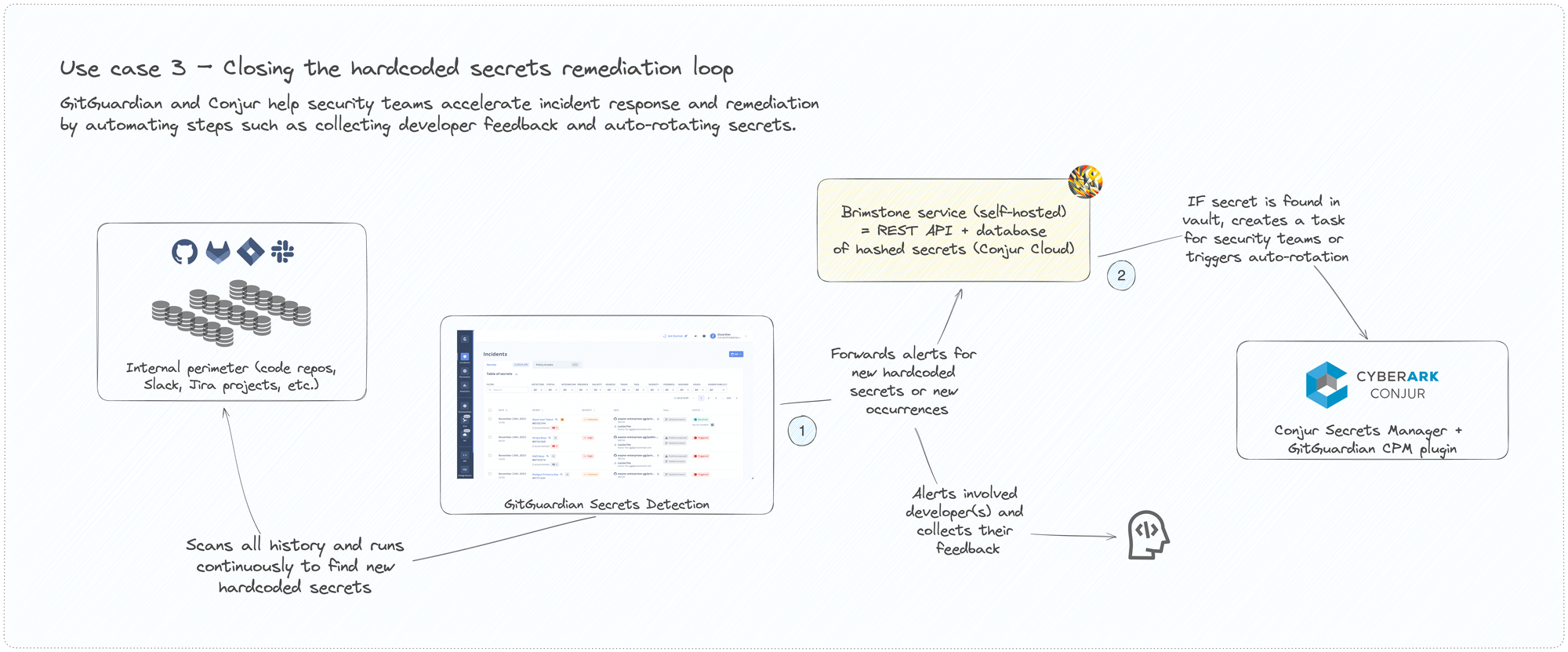
This process was designed to significantly reduce the mean time to remediation from weeks or days to mere minutes and to minimize the time window for exploitation. The integration between GitGuardian and CyberArk Conjur will help security teams address more incidents while giving back time to developers to focus on what they enjoy most–writing code.
Before you go
This is just the beginning. Our teams will keep building on top of our community integration to help organizations improve their secrets security posture.
If you want to witness our community integration in action, join us live on Thursday, February 29, 2023, at 11 AM EST for an engaging conversation with Mackenzie Jackson and special guests from CyberArk, Evan Litwak (Senior Director, DevSecOps Solution Strategy) and David Hisel (Global Solution Strategy DevOps)!
Additional Resources
- Enterprise Buyer's Guide For Secrets Detection: 10 key considerations for security decision-makers.
- GitGuardian Secrets Detection: Find and fix 350+ types of hard-coded secrets in Git repositories, CI/CD pipelines, and developer productivity tools.
- 2023 Gartner® Critical Capabilities for PAM: CyberArk scored highest for the Secrets Management use case in the Gartner® Critical Capabilities for PAM.