This quarter, we leaned deep into securing collaboration tools, expanding our coverage to new platforms, and embedding security where modern development actually happens, inside the IDE, not just the dashboard.
From historical scanning in Microsoft and Atlassian ecosystems to a new MCP server for Agentic AI environments, GitGuardian continues to bring powerful detection, smarter context, and streamlined workflows to where you work and build.
But perhaps the most game-changing development? We’ve unified how you defend your entire perimeter, including the parts you don’t control.
Here’s a look back at what we shipped in Q2.
More Coverage, Fewer Blind Spots
Microsoft Teams, SharePoint, and OneDrive are now under watch
Secrets don’t just live in code. They hide in chat logs, shared documents, and cloud drives. This quarter, GitGuardian added hardcoded secrets detection for Microsoft Teams, along with SharePoint and OneDrive support. That means you can now scan real-time and historical conversations, files, and content across your Microsoft ecosystem to surface exposed credentials before attackers do.
Whether it’s an accidental API key in a shared spreadsheet or a forgotten token buried in a comment thread, GitGuardian makes sure nothing slips through.
Read how to enable secrets detection for these sources
Historical scanning for Confluence and Jira Data Center
Secrets leaked months or even years ago still pose a threat. Now, historical scans are live for Confluence Data Center and Jira Data Center, as well as Confluence Cloud and Jira Cloud, extending our retrospective detection capabilities across your Atlassian stack. No more blind spots in your collaboration tools.
These additions are crucial in preventing dormant credentials from becoming future vectors of breaches.
Read how to enable secrets detection for Jira Cloud
Read how to enable secrets detection for Confluence Cloud
Public Monitoring Now Integrated
Your Security Perimeter Just Got Bigger
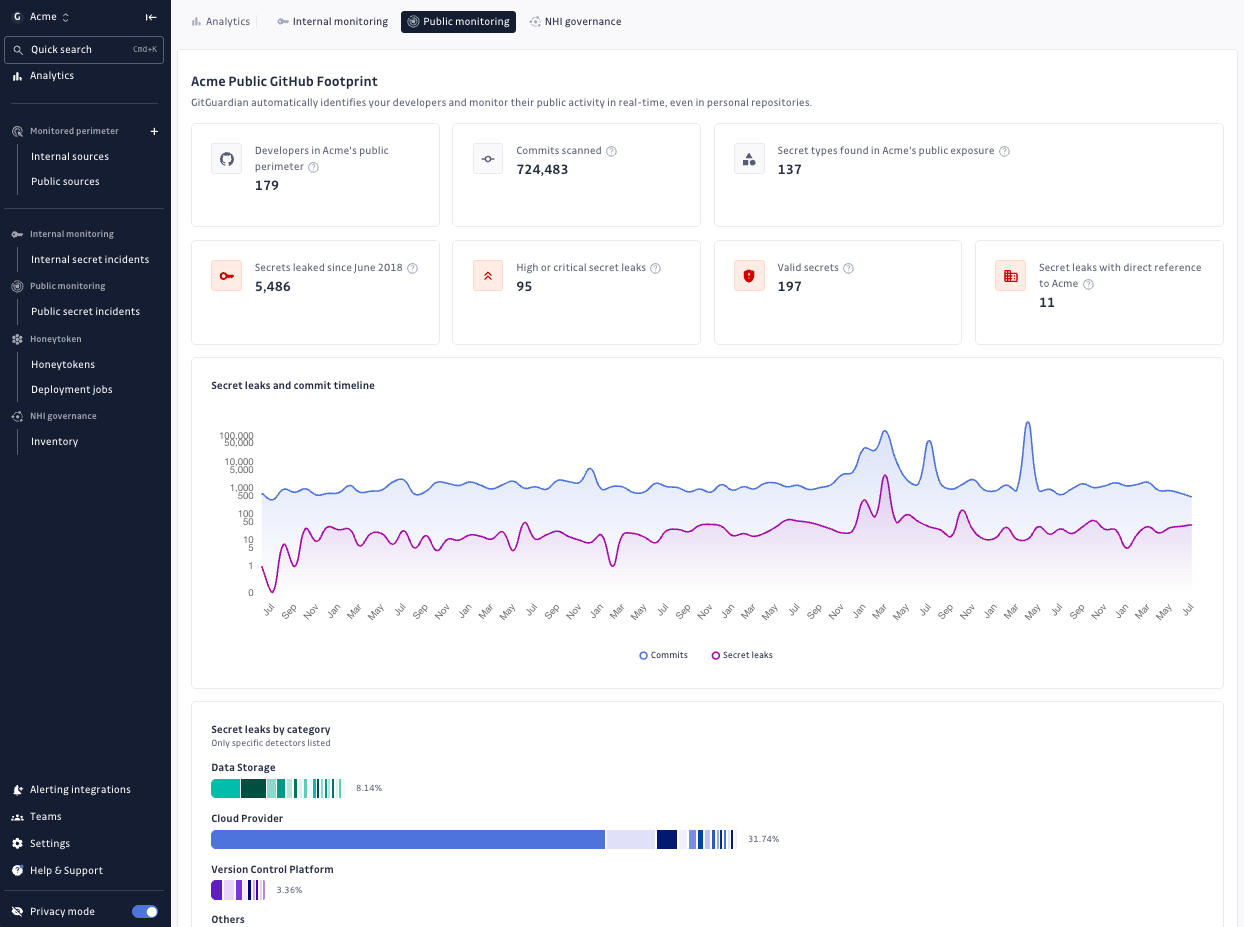
Q2 also marked a major milestone for our platform: the integration of Public Monitoring directly into the GitGuardian platform. This means you can now scan public GitHub repositories for exposed secrets tied to your organization, all from the same unified interface.
Public Monitoring uniquely monitors Public GitHub, including developers' repos – a blind spot for most organizations. This provides critical visibility into company secrets exposed externally, so that they can remediate those exposed secrets as early as possible, before attackers find them.
Incidents from Public Monitoring now appear in the same dashboard as your internal findings, enabling centralized triage, streamlined workflows, and deeper correlations across sources.
You can see how a secret leaked in public GitHub relates to an internal repo, a CI pipeline, or a vaulted credential, right in the GitGuardian platform.
It's time to bridge the gap between your internal environments and the broader ecosystem. And for new customers, the unified experience is available starting today.
Secure AI Workflows As GitGuardian Joins the MCP Ecosystem
Introducing GitGuardian’s MCP Server for AI IDEs
We officially joined the Agentic AI frontier with the release of our GitGuardian MCP Server. This is a secure integration layer that brings our security tooling directly into AI-powered IDEs like Cursor and Windsurf.
Because AI agents are writing more code, calling APIs, and making decisions in real time. Our MCP Server lets them safely access GitGuardian's secret scanning, honeytoken generation, and incident data, without leaving the developer's environment.
Agents can now act on security signals instantly, while organizations retain full control over what tools agents can access and how.
We built it with tight read-only permissions, to prevent squatting and misuse. We occupied the namespace to protect it. As AI adoption accelerates, we believe safe-by-design infrastructure like this will be critical.
Check out these setup instructions
Streamlining Identity and User Lifecycle
SCIM now supports automatic onboarding and offboarding
Managing access shouldn’t be manual. With our new SCIM integration, you can now fully automate user provisioning and deprovisioning from your identity provider (Okta or Microsoft Entra ID).
Want to add a developer to your IdP? They’ll appear in GitGuardian, ready to triage incidents.
Want to remove them? Their access is revoked immediately.
This ensures real-time alignment between your IdP and GitGuardian, reducing risk, improving compliance, and cutting down on manual toil.
Explore our product documentation
Enhanced Detection Engine
30+ New and 50+ Updated Detectors Added
Q2 brought significant enhancements to our secrets detection capabilities, with over 30 new detectors and more than 50 updated detectors across emerging AI platforms, cloud services, and development tools. Key additions include comprehensive Artifactory security coverage, AI service detectors for Perplexity AI and Anthropic, expanded GitLab ecosystem support, and enhanced Kubernetes security detection.
We recommend re-scanning your repositories and other sources to benefit from these enhanced detection capabilities.
View all detector engine releases
Wrapping Up
This quarter, we pushed deeper into collaboration platforms, agentic AI, and public source monitoring, making it easier to detect, investigate, and remediate secrets no matter where they live or who leaked them.
By securing the modern development perimeter, from IDEs to Teams threads to SharePoint folders to public GitHub, we’re giving security teams full-spectrum visibility and the tools they need to stop breaches before they start.
Want a guided tour of what’s new? Reach out to your GitGuardian contact or book a demo.
And stay tuned. Q3 brings even more to NHI lifecycle automation, tighter ecosystem integrations, and new ways to enforce your secret security policies at scale.
Until then, keep your secrets safe.







