In the NHI era, organizations rely on APIs, cloud services, and automation to drive innovation and efficiency. Yet these same tools create opportunities for attackers to exploit exposed secrets. With 83% of security breaches involving compromised secrets, the risks have never been more significant.
Detecting exposed secrets alone is no longer sufficient. Many secrets are overly permissive or misconfigured, granting attackers far more access than necessary. With a single compromised secret, they can escalate privileges, exfiltrate sensitive data, or disrupt operations—causing widespread damage, financial loss, and potentially regulatory non-compliance. Mitigating these risks requires full context: what a secret can access, how much damage it could cause, and whether it's a critical threat. For example, a secret with minimal "read:profile" permissions is far less dangerous than one with unrestricted "read:everything" access. Without these insights, organizations are forced to rely on guesswork, delaying response efforts and leaving critical vulnerabilities unaddressed.
To bridge this gap, GitGuardian is introducing Secrets Analyzer, a powerful tool that delivers the contextual insights security teams need to take decisive action. By evaluating each secret's permissions, ownership, and impact, Secrets Analyzer enables teams to respond faster, reduce risks, and protect their most critical assets at scale.
Why Permission Scopes Are Critical in Secrets Management
Permission scopes define the level of access and control granted to an entity—such as a user, application, or API—within a system. They specify what actions can be performed (e.g., read, write, delete) and which data or systems can be accessed.
Permission scopes are most effective when paired with Role-Based Access Control (RBAC), which assigns permissions based on defined roles within an organization. RBAC ensures that entities are granted access strictly according to their responsibilities.
Example:
- A developer may only need "read" access to logs for troubleshooting purposes.
- An administrator, by contrast, might require "read" and "write" access to manage critical systems.
- RBAC enforces this separation, ensuring that each role receives the minimum necessary permissions to perform its duties.
By combining well-scoped permissions with RBAC, organizations can enforce least privilege access—a core cybersecurity principle that limits access to only what’s necessary.
How Attackers Exploit Overprivileged Secrets
To attackers, overprivileged secrets represent an open door to escalate their actions. By exploiting overly broad permissions, they can move laterally within systems, escalate privileges, and inflict widespread damage.
| Attack scenario | Impact | Example of broad permissions exploited |
|---|---|---|
| Privilege Escalation | - Gain admin-level control over systems. - Modify configurations, steal data, or disrupt operations. |
A leaked API key with unrestricted “admin” permissions could allow attackers to: - Exfiltrate customer data. - Shut down production environments. - Deploy ransomware. |
| Expanded Attack Surface | - Move laterally across systems. - Compromise entire infrastructure by chaining exploits. |
A CI/CD pipeline token with broad permissions could allow attackers to: - Inject malware into production builds. - Compromise other production systems. |
| System Disruption | - Corrupt critical resources. - Delete backups, preventing recovery. |
A cloud storage key with “read/write” permissions could allow attackers to: - Delete backup data. - Exfiltrate sensitive information. |
| Stealth and Long-Term Exploitation | - Avoid detection by mimicking legitimate activity. - Prepare for larger-scale attacks over time. |
An overprivileged API token could allow attackers to: - Query sensitive data under the guise of normal system behavior. - Incrementally modify configurations unnoticed. |
The Hidden Costs of Overprivileged Secrets
Overprivileged secrets don't just pose technical risks—they also have significant business and compliance implications.
- Compliance Violations: Regulatory frameworks like GDPR, HIPAA, and SOC 2 require strict enforcement of access controls and the principle of least privilege. Overly permissive secrets can result in audit failures, fines, and even legal action.
- Operational Costs: When secrets are overprivileged, the blast radius of a secret leak is significantly larger, leading to greater downtime and higher recovery costs in the event of a breach.
- Reputation Damage: Breaches caused by overprivileged secrets can erode customer trust and tarnish an organization's brand.
By effectively managing permission scopes, organizations can minimize these risks and protect their systems, data, and reputation. However, as secrets proliferate and infrastructures grow increasingly complex, manual scope management is no longer feasible. That's where solutions like GitGuardian's Secrets Analyzer come in, helping security teams identify overprivileged secrets, understand their impact, and prioritize remediation.
How GitGuardian Secrets Analyzer Simplifies Permissions Analysis
The Case for Automating Secrets Management
Before automated tools, identifying overly permissive secrets was labor-intensive and error-prone. Key owners had to log into provider interfaces, locate the API keys page, and manually map out resources and permissions. Many providers do not offer a centralized or clear way to view permissions tied to API keys, making the process cumbersome and time-consuming.
With secrets scattered across various environments, manual audits are no longer scalable. Security teams need automated tools to discover high-risk secrets with overly broad permissions and provide detailed insights to evaluate their impact.
This is where GitGuardian Secrets Analyzer steps in, providing the automation and insights security teams need to tackle these challenges efficiently.
Introducing GitGuardian Secrets Analyzer
GitGuardian's Secrets Analyzer enhances secrets detection by adding contextual insights about each secret. This includes details like roles, permissions, ownership, and perimeter metadata.
Secrets Analyzer automatically retrieves metadata, resources, and permissions directly from the API key, eliminating manual mapping. To minimize risk, GitGuardian's analyzers are configured to maximize read-only operations. When needed, they may use calls like POST or PUT during analysis, but we ensure through rigorous testing that these requests are intentionally malformed and will never result in successful or disruptive operations.
Why Secrets Analyzer Sets a New Standard for Secrets Security
GitGuardian's Secrets Analyzer shifts the focus from "What is exposed?" to "What does this exposure mean?" by delivering context, prioritization, and scalability to modern infrastructures. It allows security teams to:
- Automate permissions analysis, saving time and focusing resources on the most critical threats.
- Proactively address high-risk secrets with actionable, prioritized insights.
- Remediate over-permissioned secrets quickly to reduce response times and prevent breaches.
As cloud-native environments grow more complex, Secrets Analyzer provides a scalable approach to ensure security teams can manage risks effectively and prevent high-impact breaches.
How GitGuardian Secrets Analyzer Integrates into Your Workflow
GitGuardian Secrets Analyzer is designed to integrate seamlessly into your existing workflows, delivering immediate value without disruption.
Supported Analyzers: Staying Ahead of Evolving Risks
Secrets Analyzer currently supports a range of common secrets, ensuring broad coverage for today's security challenges:
- GitHub PAT (Fine-Grained)
- GitHub PAT (Classic)
- GitLab PAT
- Stripe API Keys
- PostgreSQL Credentials
- Slack Bot Tokens
- Bitbucket App Passwords
- Bitbucket Access Tokens
- MySQL URI
With more analyzers in development, GitGuardian Guardian ensures security teams stay ahead of emerging risks in diverse environments.
Exploring Secrets Incidents and Tied Permissions
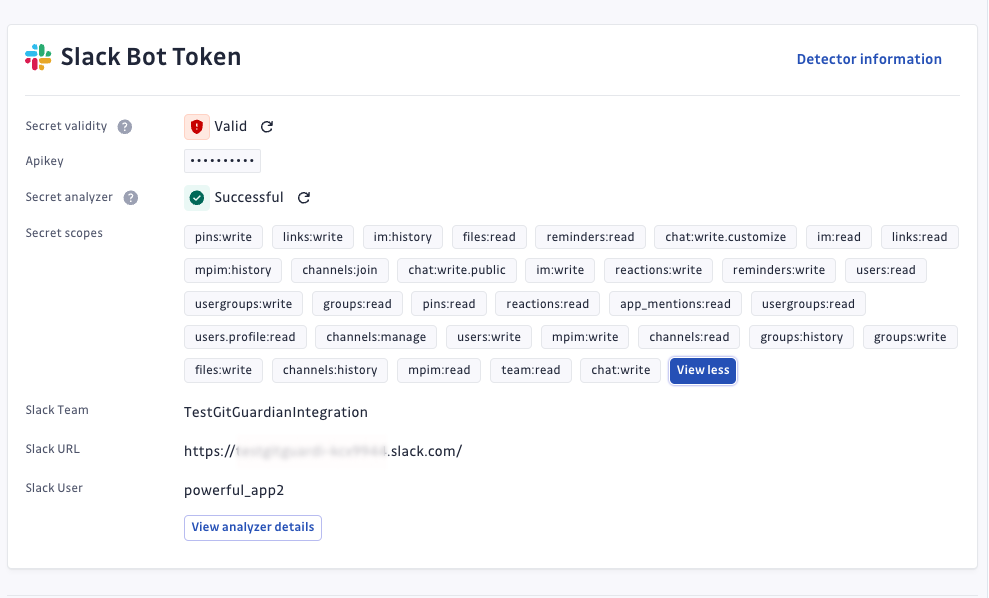
When investigating a detected secret, Secrets Analyzer provides as much contextual data as possible, including:
- The scopes (permissions) tied to the secret.
- Metadata such as roles, ownership, and perimeter.
This enriched incident view helps security teams:
- Quickly assess the level of access a secret provides.
- Evaluate its criticality within the system.
- Determine the most effective remediation strategy.
Helping Prioritize with Built-in Critical Scopes View
To streamline incident response, GitGuardian offers a built-in saved view called Critical Scopes. This view highlights incidents involving secrets with the most impactful permissions, enabling security teams to focus immediately on the highest-priority risks.
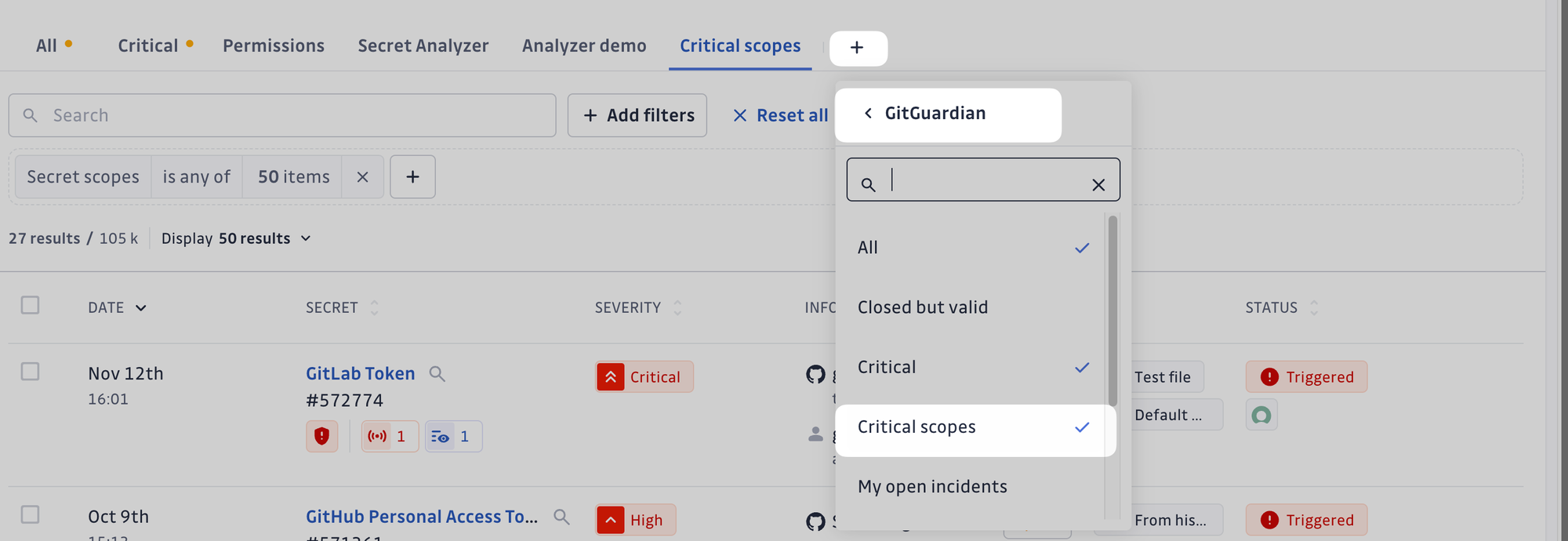
As new analyzers are added, the Critical Scopes view will evolve to include additional high-risk permissions, ensuring it remains a reliable tool for prioritization.
Enhanced Navigation with New Filters
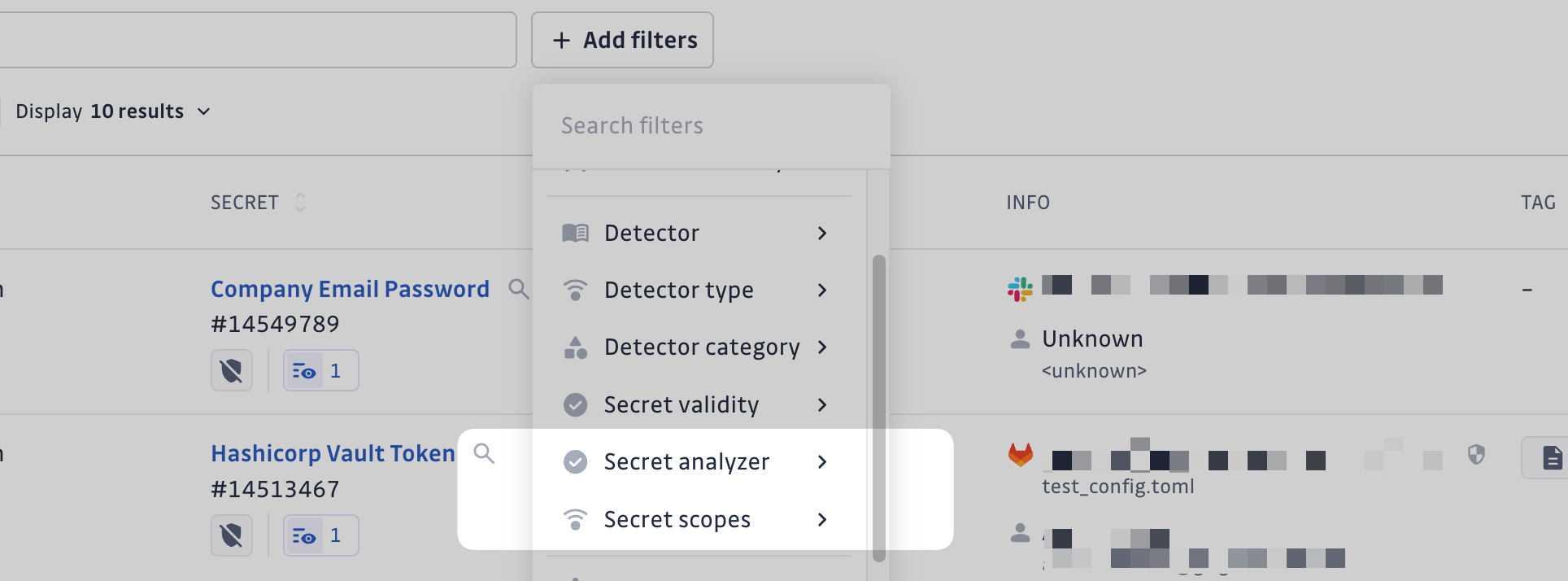
Secrets Analyzer introduces advanced filters to improve how incidents are managed:
- Secret Scopes Filter: Allows teams to filter incidents by specific permissions, making it easy to identify secrets with the most dangerous access levels.
- Secret Analyzer Filter: Enables filtering by the analyzer's status, such as:
- "Successful": Incidents where permissions were retrieved successfully.
- "Failed to check": Incidents where the analyzer could not verify permissions, ensuring gaps are flagged for further investigation.
These filters enhance navigation, helping teams quickly locate and address high-priority threats without delays.
How to Minimize Risk with Smarter Permissions Management
Managing secret permissions effectively is critical to reducing the risks of exposure, privilege escalation, and breaches. By following these best practices, organizations can minimize the attack surface of their secrets, control access more effectively, and respond quickly to incidents.
| Best Practice | Description | Key Benefit | Implementation Details |
|---|---|---|---|
| Enforce the Principle of Least Privilege | Ensure that every user, application, or system has only the minimum permissions necessary to perform its tasks. | Reduces the potential damage if a secret is exposed or misused. |
- Regularly audit permissions for secrets. - Apply RBAC to enforce least privilege. - Use GitGuardian Secrets Analyzer to detect over-permissioned secrets. |
| Prioritize Remediation of High-Risk Secrets | Focus remediation efforts on secrets with the most dangerous scopes, such as admin-level permissions or write access to critical systems. | Ensures that the most critical vulnerabilities are addressed first, minimizing the potential impact. |
- Leverage the Critical Scopes view to identify secrets with dangerous permissions. - Revoke or rotate admin-level secrets immediately. |
| Rotate and Update Secrets Regularly | Regularly update and rotate secrets (e.g., API keys, tokens) to limit their validity period and reduce the risk of prolonged misuse | Reduces the window of exposure for compromised secrets. |
- Automate secret rotation using secret management tools (e.g., AWS Secrets Manager, HashiCorp Vault). - Notify stakeholders about updates for downstream configurations. |
| Use Environment-Specific Secrets | Assign unique secrets for each environment (e.g., development, staging, production) to compartmentalize access and limit the blast radius of a breach. |
- Limits the scope of potential damage if a secret is leaked. - Gives the organization time to respond and mitigate breaches. |
- Ensure secrets are specific to their environments. - Prevent cross-environment access with network segmentation and access controls. - Generate unique secrets for each environment. |
| Provide Regular Training and Awareness | Train developers and any audience using secrets on the importance of managing secret permissions and adhering to security best practices. | Builds a culture of security awareness and reduces human errors in secret handling. |
- Conduct periodic training sessions. - Provide secure coding guidelines and best practices for secret management. - Use real-world examples to illustrate potential risks. |
And if a secret ever gets compromised, don't worry—we've got you covered. Check out our step-by-step guide on what to do if you expose a secret to take immediate action and minimize impact.
Stay Ahead of Threats with Secrets Analyzer
In today's security landscape, credentials remain one of the most vulnerable entry points for attackers. Protecting secrets requires more than detection—it demands actionable context. GitGuardian's Secrets Analyzer delivers the insights security teams need to stay ahead of evolving threats, enabling swift, decisive action to prevent costly breaches.
Why This Matters for Your Organization
- Saves Time: Automates permission analysis and prioritization, eliminating manual audits and accelerating remediation.
- Reduces Costs: Proactively addresses risky secrets to avoid financial and reputational damage.
- Optimizes Resources: Actionable insights and tools like Critical Scopes help teams focus on the most pressing threats.
Don't wait until a breach happens—equip your team with the tools they need to stay ahead of attackers and protect your most critical assets.