Denver, Colorado, is home to beautiful mountain views and an airport with an interesting Wikipedia page. You might know it as home to multiple sports teams or as the Mile High City (1.34 KM High City) due to its famous elevation. Or you might know it as the home of the Great American Beer Festival. While that last one sounds like a wonderful community to be part of, another impressive community of over 400 security-focused professionals gathered to talk about securing our futures and how we can empower our teams to improve security at SnowFROC 2024.
SnowFROC's name is a combination of "Snow," as the event is in winter when it normally snows, and "Froc," which stands for Front Range OWASP Conference. Their site describes the event as Denver's premier application security conference, and anyone who attended would likely agree. With three speaking tracks, 17 sessions, and four different workshops, there was something for everyone.
While there was no official theme for the event, most all the talks went beyond describing the problems of today and delved into how to solve the issues we are going to be facing tomorrow. Here are just a few highlights from this awesome OWASP community event.
Your job is hard, and AI will make it harder
In the opening keynote, "Make Shift Happen," Rob Lee, Chief Curriculum Director at the SANS Institute, stated it plainly: "Your job is about to get all that much harder."
Technology has never progressed faster than it is right now, and we, as biological beings, are struggling to keep up. Rob said the label for this phenomenon is "Future Shock" which is also the name of the book in which the idea was introduced in 1970 by Alvin Toffler. We also get the term "information overload" from Mr. Toffler's work. AI and machine learning are only accelerating the mountain of things to know. Fortunately, we are seeing some helpful frameworks emerge to help us understand how to think about AI security at scale, such as the MITRE ATLAS framework.
Rob focused on the speed of change to help us understand that if we feel stressed about the growing amount of stuff to know, we are not alone. Everyone seems to be in this exact situation. When he polled the room to ask, 'Who feels like they are faking it when it comes to AI security knowledge? ' a full 70% of hands went up.
He left us with a call to action to learn daily and push ourselves to stay tech-literate. Very importantly, he reminded us there is no shame in saying, "I don't know." If we admit it, we can then do something about it. The future of security depends on it.

What motivates a Security Champion?
In his session "Making Security Fun Again: Building a Proactive Security Culture," Deputy CISO at Fivetran, Dustin Lehr, started with the conclusion: "Prevention of security vulnerabilities and incidents requires proactive actions, which you can influence through behavioral science and human-focused design!" (emphasis his). There is a lot to that statement, but Dustin guided us through those ideas and the science underlying a successful champions program.
He said we often hear that "80% of breaches are caused by human error," and we answer that challenge, in general, by buying more technology. He believes we need to lean into the people side of things for a real opportunity for change. He explained how he built Fivetran's Champions Program by focusing on motivating people in a way that speaks to them as an individual. A Security Champion is a colleague who steps up to learn more about security and who can translate and filter security messaging to their teams.
He defined a simple equation for thinking about people's behavior: "Behavior = Motivation + Ability + Prompt (the things that remind the person to do the activity)." With this in mind, we can take a closer look at how people are motivated. He relies on the Octalysis Framework, which can help map a person's personality to eight specific factors.
One quality all Security Champions have is a natural curiosity about how things work and about security in general. If someone asks you for help to learn more about a security question, that person is likely a good candidate for an internal champion!
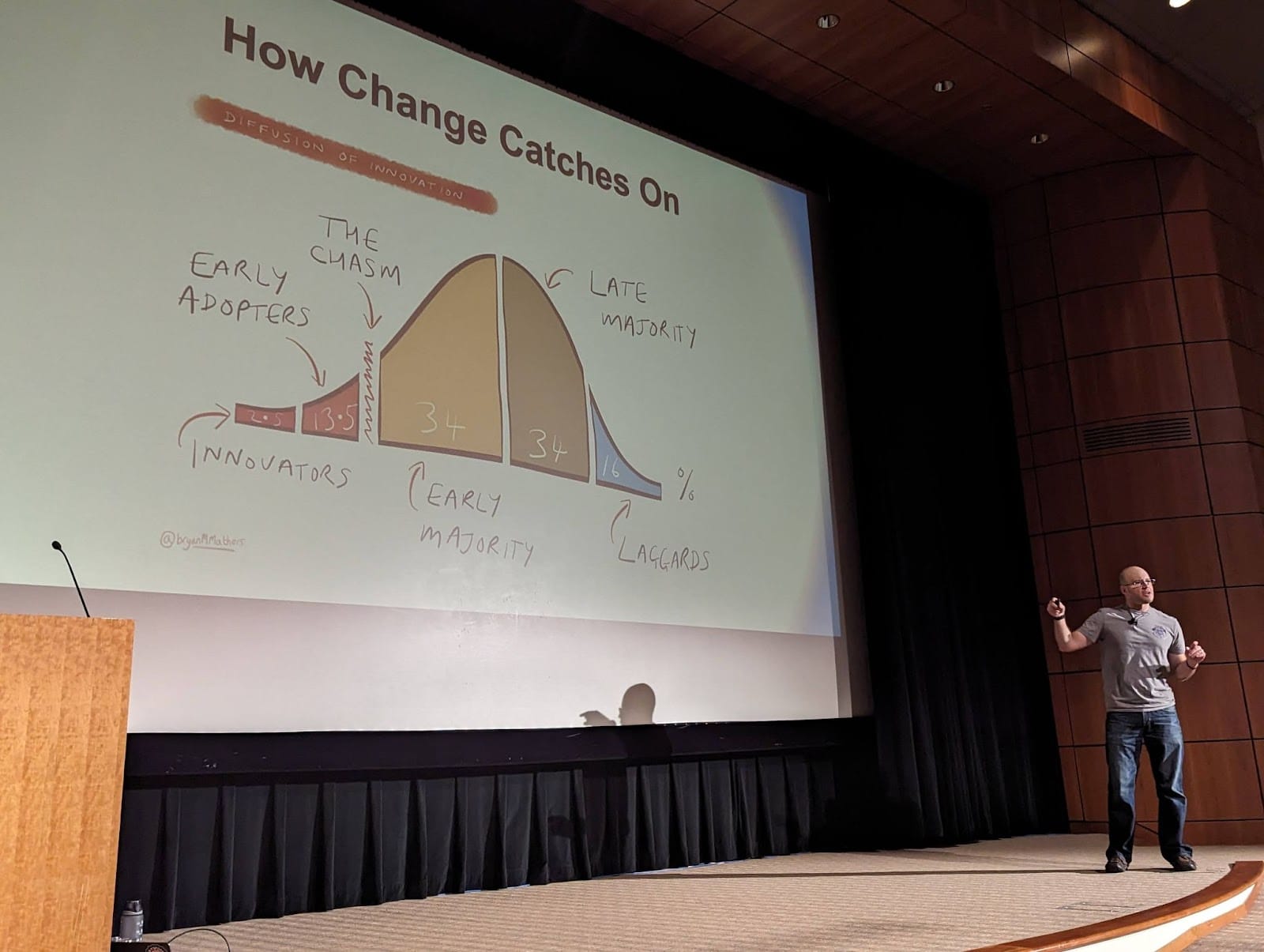
The role of a DIFF in supply chain security
Andy Lewis, the founder of the Front Range OWASP group and Solutions Architect at ReversingLabs, began his session "Software Supply Chain Calamity: the UA-Parser Saga" by reminding us that developers do not like to reinvent wheels. They are not paid to reinvent them, and there are free wheels that work on the internet. One of those wheels was called Log4J, and many, many developers simply used it without issue, until they all had the same issue called Log4Shell.
Another wheel that many developers use is UAParser.js, a powerful tool that can detect a user's browser, engine, OS, CPU, and even device type. With 1.2K forks and over 12 million downloads a week, this is a popular component that was unfortunately hijacked by a lone developer and spread malicious code. In telling the story of UAParser.js, Andy revealed some great tips on keeping your software supply chain safe.
He said we must invest in a testing process for our supply chains, detecting malware and any tampering where the integrity seems compromised. We must also look for behavior changes, such as a new phone home function with traffic going somewhere you do not know or understand or suddenly turning on the webcam and mic.
He emphasized that one of the best tools all developers already have in their arsenal is the simple DIFF, a built-in function in Bash, from which `git diff` was derived. A simple Diff between versions will show all the new code and expose any strange new behaviors in seconds. It is a tool that is priceless in the manual review process.

Finding API secrets in the front end
Secret sprawl was at the forefront of the session from Antoine Carossio, Cofounder CTO at Escape, "API Secret Tokens Exposed: Insights from Analyzing 1 Million Domains…" Antoine shared his research into looking into frontend components for hardcoded credentials and how pervasive this problem is.
Antoine explained how the front end is built, primarily using HTML5, CSS, and JavaScript, commonly shortened to JS. His research focused on the JS components that expose security risks. Modern JS frameworks like Angular, React, and VueJS allow developers to add all sorts of functionality to a web page, but just like with any other code, secrets can be added in plaintext.
He said the issue with most homegrown approaches to finding and eliminating secrets on the front end is they are mostly just variations on regular expression searches trying to identify high-entropy strings that might be secrets. JS code is full of high-entropy strings that are mostly not secrets. His approach to finding these secrets relies on leveraging an Abstract Syntax Tree. He built a simple engine that scanned 189.5M websites in just under 70 hours and uncovered 18,458 secrets in the front-end JS code.
Ultimately, his advice exactly lines up with GitGuardian's advice, which is to find and eliminate secrets as early as possible, shifting left. If a developer can find and remove a secret before it makes it into the commit, then it will never end up in the JS for him to find. And that makes a safer internet for us all.

An elevated community experience
Denver has a thriving tech scene, as evidenced by its many tech meetups. SnowFROC is a shining example of what a community should be. We learned a lot, sharing knowledge and swapping stories. Your author got to share his knowledge of the history of honeytokens and how to build them.
GitGuardian is proud to have participated in this event with sponsor and speaking roles. We love the OWASP community, and their focus on helping the world make more secure applications. If you are not yet part of a local OWASP community, we invite you to investigate the Meetups in your area or online. If you are in the Paris area, maybe we will see you in our office soon for a Meetup. Or maybe we will see you when GitGuardian comes to an event near you.







