The world of cyber threats is continually evolving, and the range of targets is constantly expanding. Fortunately, cybersecurity is rapidly progressing as well. In August 2023, two different U.S. government organizations published new reports about what to expect moving ahead, suggesting regulations and standards: CISA's Strategic Plan for FY24- FY26 and NIST SP 800-204D.
While these publications originate from two different U.S. agencies, both point to the same overarching path to securing our vital infrastructure and enterprise applications into the future. CISA lays out a broad vision with measurable goals we should be striving towards, whereas NIST provides actionable, tactical procedures. When read side by side, these publications suggest the next few years will bring a focus on hardening our defenses, improving our tooling for faster detection and remediation of threats, and transparent measurement with attestation.
Let's dig in on what these publications contain and how they complement one another. From there, we can identify some top priorities CISOs and security leads will need to address in the coming technology cycles.
CISA
The Cybersecurity and Infrastructure Security Agency, CISA, was created by a presidential act in 2018 with a mission of "leading the national effort to understand, manage, and reduce risk to the cyber and physical infrastructure that Americans rely on every hour of every day." Their mission expands across three primary areas: cybersecurity, infrastructure security, and emergency communications.
CISA's Strategic Plan Goals
In their publication, CISA's Strategic Plan for FY24- FY26 presented a new vision for cybersecurity grounded in collaboration, innovation, and accountability. They explain, "We aim to operationalize an enduring and effective model of collaborative defense that equitably distributes risk and responsibility and delivers a foundational level of security and resilience for our digital ecosystem."
The plan lists three main large goals:
- Address Immediate Threats.
- Harden the Terrain.
- Drive Security At Scale.
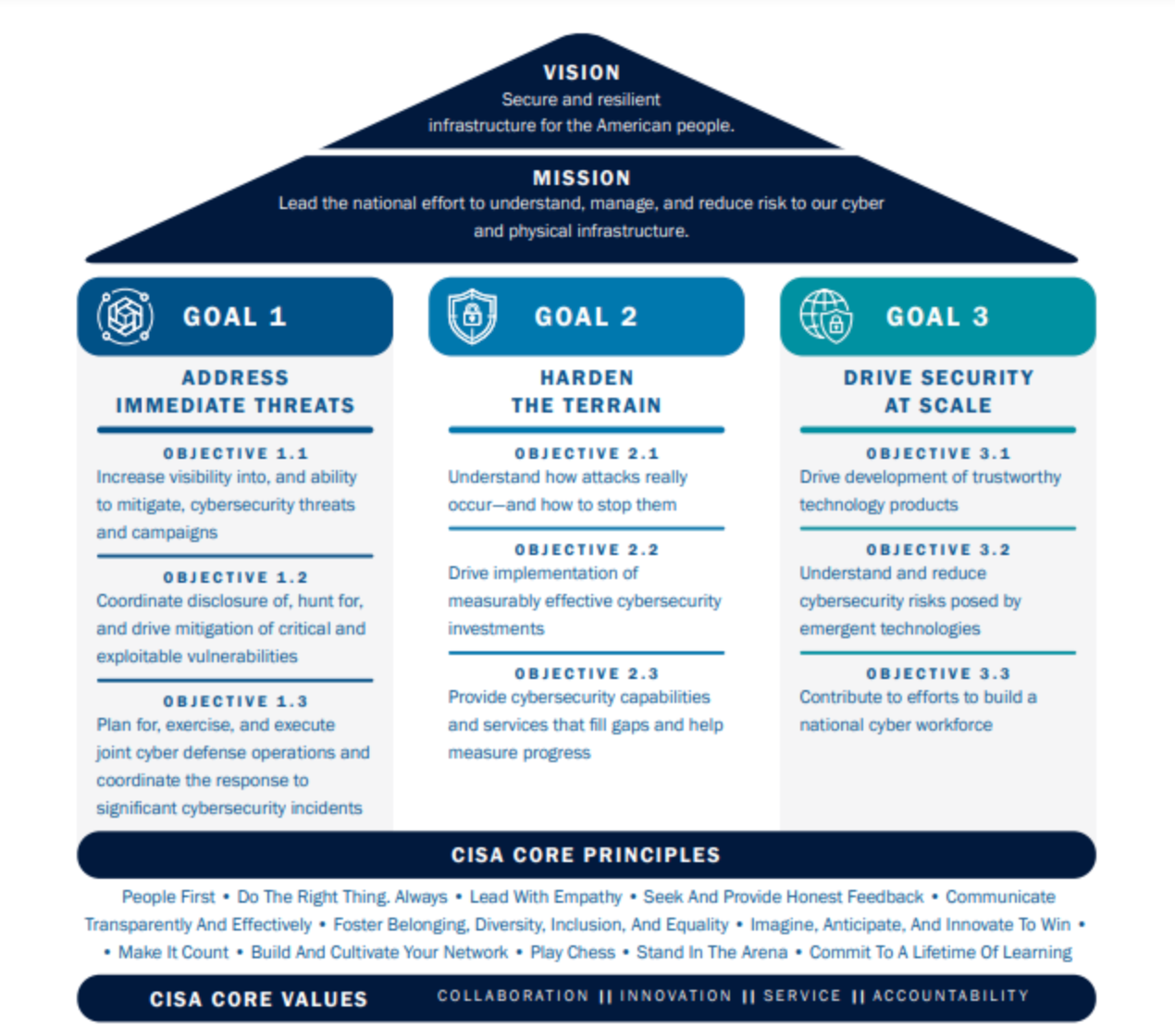
Each of the goals names key objectives to achieve by 2026, with definitions for measuring effectiveness. These effectiveness measurements include:
- Objective 1.1, goal 1 - Reduction in our time-to-detect adversary activity affecting federal agencies and critical infrastructure partners.
- Objective 1.1, goal 2 - Reduction in the time-to-remediation across each identified intrusion.
- Objective 1.3, goal 3 - Increase in post-incident after-action reports demonstrating that actions developed in cyber defense plans reduced negative outcomes.
- Objective 2.2, goal 3 - Increase the number of organizations outside of the FCEB that have adopted applicable requirements in CISA directives.
- Objective 2.3, goal 2 - Continuous Diagnostics and Mitigation: Percentage increase in agencies that have fully automated key vulnerability and asset management processes and can report advanced measurements such as time-to-remediate, scan frequency, and scan quality.
- Objective 3.1, goal 1 - Increase in the number of technology providers that have published detailed threat models, describing what the creators are trying to protect and from whom.
- Objective 3.1, goal 5 - Increase in the number of technology providers that regularly publish security-relevant statistics and trends, such as MFA adoption, use of unsafe legacy protocols, and the percentage of customers using unsupported product versions.
Improved testing, faster response, and more transparent reporting
While the above list of goals is only a partial representation of CISA's plan, they point to a future where security scanning, including SAST, IaC, and DAST, is at the forefront of our defensive strategy. While tooling will always continue to evolve, helping surface flaws in software, both at rest and at runtime, it is clear it will remain a constant for keeping our infrastructure safe.
Given the speed of attackers, especially after initial footholds are established, it will be vital also to acquire tools that detect breaches in near real-time. The good news is that, as an industry, we have been getting better at this, evidenced by recently reported record-low mean dwell times. The flip side of this improvement is that attackers have been getting swifter, too. But there is still a long way to go before all dwell times are reduced among all organizations across the board. It is evident that CISA hopes for wider tool adoption for breach and leak detection and remediation.
In addition, these scan and detection results will need to be more widely shared to build trust between organizations and consumers. While the word attestation, the declaration that something is true, is never directly used in the CISA publication, it feels accurate to use it to describe part of the vision they set forth. Just as SBOMs, such as those defined by OWASP's CycloneDX, exist to attest that software contents are what we claim to be, and signature authorities, such as Sigstore's Fulcio, exist to prove signatures are indeed trustworthy, it is easy to imagine a standard to emerge showing that proper security scans have been run and reporting is available.
NIST
Established in the pre-digital age of 1901, the National Institute of Standards and Technology, NIST, originally had a mission to provide standard weights and measures while serving as the U.S. National Physical Laboratory. In 1988, the mission was updated to "promote U.S. innovation and industrial competitiveness by advancing measurement science, standards, and technology in ways that enhance economic security and improve our quality of life." They have been working hard to attain the best solutions to multidisciplinary challenges ever since.
NIST Special Publication 800-204D
Beginning in 2019, NIST began publishing recommendations for cloud-native applications that are made up of multiple loosely coupled components, commonly called microservices. While specifically written for government agencies, it is also a widely regarded standard for any enterprise applications as well. August 2023 saw the 4th update to this publication, with this edition titled "Strategies for the Integration of Software Supply Chain Security in DevSecOps CI/CD Pipelines."
After SolarWinds, Log4Shell, and The President’s 2021 Executive Order (EO) 14028, the software supply chain, SSC, has been top of mind for anyone focused on security. This newest publication makes some specific recommendations for keeping our vital software delivery paths secure.
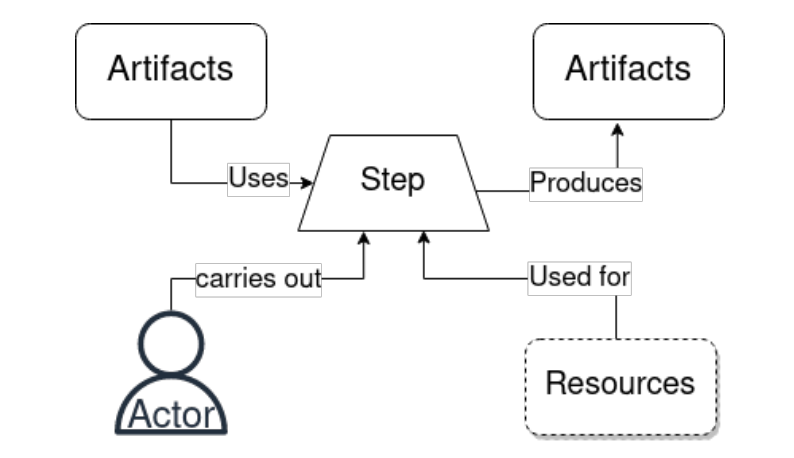
According to NIST in this latest publication, SSC attacks have two fundamental properties that make them appealing to attackers. First, they allow attackers to infiltrate highly regulated environments through less secure but legitimate channels. Second, due to the highly interconnected nature of supply chains, they allow for widespread damage in a short period of time.
They explain that an SSC attack is a three-stage process:
- Artifact, step, or actor compromise: An attacker compromises an element of the SSC to modify an artifact or information of such.
- Propagation: The attack propagates throughout the chain.
- Exploitation: The attacker exploits the target to achieve their goals (e.g., exfiltration of data, cryptojacking).
The main targets for attackers include:
- Source code.
- Credentials.
- Sensitive data.
Exploits in the context of attack vectors and targeted assets in an SSC environment typically include:
- Injection of vulnerabilities or malware into an SSC.
- Stolen credentials that grant access to other systems.
- Sensitive data leaked.
- Injection of malicious code into repositories.
- Lack of code integrity in public repositories.
Keep credentials out of source code
NIST specifically states organizations should implement an SSC security measure, required during code commits, to prevent secrets from getting into committed code. This is enabled by a scanning operation for secrets and results in a feature called push protection, which should satisfy the following requirements:
- If the committed code has an embedded secret, there should be a feature to generate an alert that contains information on the secret type (e.g., personal access token) and location, as well as the methodology to remediate the exposure.
- Push protection features should be enabled for all repositories assigned to an administrator.
- For code that is already in the repository and ready to be deployed, a security scanning sub-feature should be invoked to detect the presence of secrets in the code, such as keys and access tokens.
- Before merging pull requests, it should be possible to view the details of any vulnerable versions through a form of dependency review.
CISA vision + NIST procedures = needed strategy and tactics
Given that almost all modern software is built with third-party components, every development or DevOps operation necessarily has a supply chain. Cybersecurity is a complex and ever-shifting field, and it can be easy to focus either too limited or too broadly when contemplating strategy and planning within an organization. Relying on only the 'how' or just the 'why' will produce suboptimal results; we must take the bigger picture, contextual security view at each step of our journey.
CISA's main audience with their strategic plan is the U.S. federal government, but the hope is the core tenants are more widely adopted to unite us as a global technology community. Meanwhile, if you only narrowly read NIST standards and recommendations without context, it can feel like an overwhelming mountain of dos and don'ts. But when taken together, they present the 'why' and the 'how' that is required to attain an optimal security posture.
GitGuardian's vision
GitGuardian began its mission focused on secrets detection and remediation. This is still very much at the heart of what we do for our customers. But a quick look at the footer of our website tells you that "GitGuardian is the code security platform for the DevOps generation." This has been our guiding north star for all of the advances of our platform you have already seen and for what we have planned for the future. Let's review how our current offerings fit into the NIST and CISA strategy.
Secrets detection and remediation
As NIST makes plainly clear, the elementation of credentials from code and environments is a vital part of the overall plan to secure the software supply chain. Leaked credentials currently top the list of how attackers gain their initial foothold, according to multiple recent reports. Leaving plaintext secrets in code, communication tools, and shared documents means it is not a matter of "if" you get compromised but a matter of "how soon."
GitGuardian Secrets Detection can help you find over 400 types of credentials, both specific types and generic patterns. Our industry-leading validation engine can help you quickly tell if the majority of popular platform secrets we detect are still active and pose an elevated threat.
The GitGuardian workspace makes it easy to organize any incidents found, giving you much-needed insight into the presence, location, and frequency of each found credential. It also streamlines the remediation process, giving you a clear way to delegate and communicate within your organization to resolve the issues in a scalable and measurable way.
Intrusion and leak detection
CISA is clear from the first goals it sets in the report: we must get faster at detection and reaction to adversary activity. Setting traps that will lure attackers into alerting you to their presence is part of a great approach to achieving this goal. GitGuardian Honeytoken accomplishes exactly this.
With GitGuardian Honeytoken, you can easily create decoy credentials that let you know someone is lurking about through email or webhook alerts and through in-dashboard reporting. Get the malicious actor's IP address, user agent, what actions they were attempting, and the timestamps of each attempt will help you boot them from the system. Additionally, if a honeytoken is publicly leaked, and that was not in your plans, this will also set off alarms. Either way, early alerting from breaches or leaks will help keep your credentials from being leveraged for unauthorized access and nefarious purposes.
GitGuardian Honeytokens are centrally managed, meaning it is easy to report on your efforts to detect compromises faster. The platform even reports the overall coverage of your monitored repositories where you have deployed honeytokens, giving your team confidence to attest that all best efforts have been made in this area.
Misconfiguration scanning
While initial access through misconfiguration might not be the leading way attackers get a foothold at present, it is still a major issue. It is one that is magnified when the same mistakes are propagated across multiple deployments thanks to Infrastrucure as Code, IaC, becoming the norm for handling server and network engineering. This is exactly what we believe happened recently with Spring Boot config at a major car company. The wrong setting in one Terraform, CloudFormation, or Pulumi file can suddenly mean the door is open in the same way across the whole attack surface.
GitGuardian Infra as Code Security scanning can quickly identify over 100 of the most common and dangerous IaC misconfigurations. Customers using GitHub or GitLab can now see the results of our more than 100 automated scans in their dashboard and coordinate the remediation process. For anyone relying on another repository hosting platform or even for IaC files outside of source control, ggshield can immediately surface the same issues inside the development environment. Either way, it is easy to report on what you find and the potential vulnerabilities the found misconfigurations would have caused.
Securing the future together
While we can't predict what the future will bring, we can safely predict that threats will continue to unfold and that enterprises will continually need to secure their applications. We can also predict that NIST and CISA will continue paving the path forward to securing all of our vital infrastructure and environments. It is a future of continuous testing, reporting, and verifying that standards are being adhered to and that threats are being mitigated.
GitGuardian is here to help at every step of the way. Our vision is clear: to be your strategic partner to meet the code security demands driven by the modern threat landscape. We will do this by continuing to help teams detect and eliminate plaintext credentials while giving the needed insights and reporting enterprises require. We will do this through advanced cyber deception tooling via GitGuardian Honeytoken to shrink dwell times and response times to record speeds. We will continue innovating with IaC misconfiguration scanning to ensure organizations can attest they have done the work to secure their infrastructure. And we have many more innovations planned for the future.
As CISA states in the conclusion of its strategic plan, "We will do it together. The risks are severe and mounting, the hurdles are high. But they are surmountable. Through our shared efforts, we will…create a safer future for generations to come."








