This content has originally been published at darkreading.com.
We are pushing more code, faster than ever. That also means that vulnerabilities and security issues are piling up just as quickly as alerts fire nonstop.
When an incident involves a leaked credential, the response feels simple: Revoke access. Shut it down before someone uses it.
But what happens if your fix makes the issue worse, and you take down production?
In an ideal world, when any secret is found, we would find the developer, pull them into the incident, and ask, “Can I turn this off?” It is a slower response, but at least it does not unexpectedly break anything. However, in some cases, the credential in question could have been revoked with minimal or no inconvenience to anyone, but was useful to an attacker.
What we need is a more pragmatic and nuanced approach that sits at the intersection of incident response and secret management. We need governance around secrets that makes it clear what can be revoked, when, and at what cost.
The Problem with “Just Revoke It”
Most security teams are trained to think in containment first. A leaked credential represents an attack path via unauthorized access. Your instincts say to invalidate the credential. In theory, that is always the safest move. In practice, it is not.
The core issue is context. A token or key on its own does not tell you what system it is tied to, whether it is used in production, staging, or someone’s side project, or how often it is used or by which services.
Without that context, you might be revoking a long-lived production database password or breaking an integration that processes customer payments. You might be causing an impact that is riskier to the business than the exposure itself.
We always need to keep in mind that "business risk" is different from "security risk." Businesses run on risk.
Context Gathering Takes Time
To understand the larger risks involved, we need to get more information. Broadly, teams are told they need to track down the developer who created that secret and wait for them to provide guidance.
During an active incident, that delay feels bad. Worse yet, it might be letting that attacker exfiltrate data. This is hard to detect as the adversary logs in, instead of breaking in.
But what if there were clearer guidance on when it is OK to revoke in one source of truth?
Security Teams and the Vault
For years, secret management platforms lived squarely in the DevOps and developer world. These systems store and distribute secrets, such as API keys, database credentials, and certificates, in a centralized, controlled way.
Security teams need a clear view into that world.
If you want to move away from remediation extremes, you need at least two things:
- A real inventory of secrets across all vaults.
- Enough metadata to support decision-making in the middle of an incident.
That metadata might include environment tags, last rotation time, and where the secret is injected. With that, an incident alert can go from “This token leaked” to insightful info like “This token is a staging credential for a noncritical service,” or “This is a production key used by your core payment pipeline.”
At that point, “vault or revoke” becomes a guided choice, not a guess. Security responders can open the platform and see, in clear language, whether revoking is safe.
From blunt reaction to guided response
Alongside any technical solutions, we still need governance. We need improved playbooks that make it clear which scenarios warrant which response. The goal is to remove doubt so that anyone on the team would have confidence that, if this secret is:
- Noncritical and isolated - “Revoke immediately. No downstream services depend on this for production.”
- Critical but already managed in the vault - “Trigger rotation using this workflow. Existing services will pick up the new value automatically.”
- Unmanaged, not in production yet, and sitting in code or config - "Push to vault and tell the developer to update the hardcoded secret to use the new path.”
This is where security and development meet in a more sustainable way. Instead of every incident turning into a scramble to find “the right developer,” the platform carries institutional knowledge.
GitGuardian As The “Vault or Revoke” Brain
The GitGuardian NHI Governance can help turn noisy secret alerts into governed, repeatable decisions.
It starts on the detection side. GitGuardian continuously scans code, pipelines, collaboration tools, and public sources for exposed secrets, so incidents are triggered from real-time events, not from reacting to aging logs.
GitGuardian can add the missing context that most teams try to reconstruct by hand, maintaining an inventory of secrets across your vaults and identity sources. The platform can enumerate which secrets are vaulted, where they live, how they are used, and when they were last rotated.
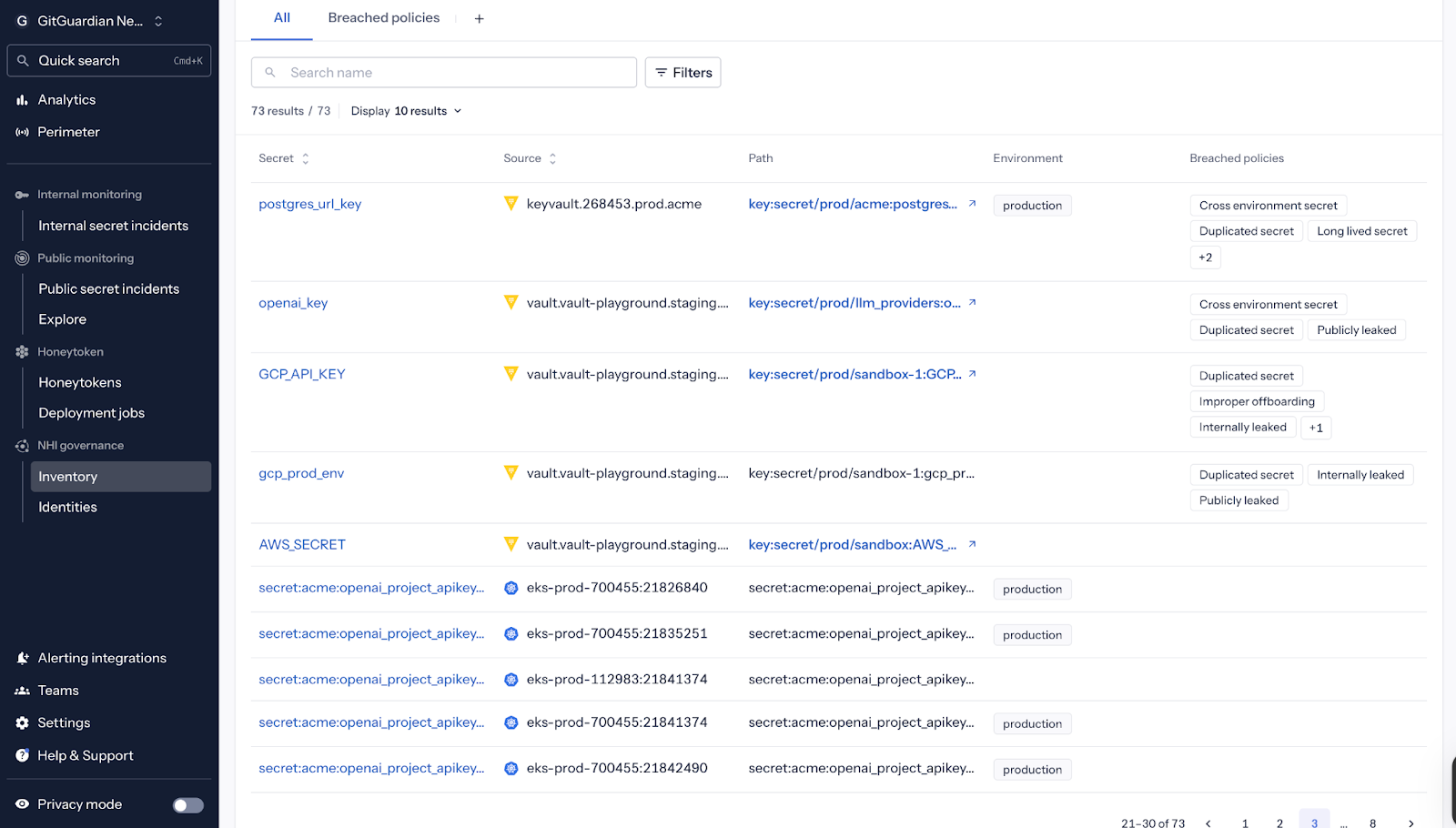
When a secret leaks, the incident in GitGuardian can point back to a specific vaulted item, the non-human identities that consume it, and the systems it touches. That is the difference between “some token leaked” and “this is a staging key for a single workload” or “this is part of a high-privilege production path.”
This same context powers the “vault or revoke” choice at incident time. GitGuardian can let responders revoke directly from the incident view for certain providers, as well as allow the responder to push unvaulted secrets into a vault without bouncing through multiple consoles.
GitGuardian carries that institutional memory and gives responders a clear, consistent path to follow.
Closing the gap between “found a secret” and “made the right call”
When you pair that context with clear playbooks and governance, something important happens. On-call engineers stop fearing the “what if I break prod” button. Security stops chasing the secret's owner one by one during critical moments.
The organization moves from reacting to secrets to managing them as a living system, with GitGuardian quietly keeping the map up to date in the background.