When you first think of Denver, the "Mile(1.6 KM) High City", you might envision the fantastic mountain backdrop of the skyline or their famous airport, but the theater and the arts might not be high on the list. For the folks who founded Denver, the humanities were very much at the forefront of their minds, as they had a performance of "Macbeth" before it had a school or hospital. Today, there are at least 56 theaters in the metro area, reinforcing the continued community spirit of getting together to explore what it means to be human. This made Dever the ideal backdrop for a gathering of cybersecurity security experts to meet and learn from one another at Wild West Hackin' Fest (WWHF) @ Mile High 2025.
WWHF's home base is Deadwood, South Dakota, where it originated in 2017. This expansion of the fest to Denver for the Mile High edition saw 800 in-person attendees and hundreds more online virtual participants gather for 4 days of workshops, hands-on labs, sessions, and, most importantly, community building. This is a very offensive security-forward event, with most content focusing on red teaming and pentesting, but all were welcome, and the defensive realms of forensics, DevSecOps, and Security Operations were definitely part of the conversations.

Many backgrounds and shared greater goals
Your author was there to give a new talk, "What I Learned From Building A Tabletop Security Exercise," based on my experience building and running a tabletop, paper card-based exercise at DEF CON 32, diving deeper than I could in my conference blog post. The experience, more than anything else, made me realize that there is no such thing as a 'traditional' background or path in the world of security.
Having a diverse background strengthens our community, as it lets us see problems from a wide array of angles and with different experiential lenses. At the same time, it demands being familiar with a world of specialized knowledge that we all too often assume everyone else already knows. It is easy to lose sight of the fact that no one knows everything, and everyone is on the same path of learning as they go.
It was good to hear other speakers acknowledge this as well, such as Nick McClendon, Principal Red Team Consultant at Mandiant, in his talk "Developing Better Payloads with Automated Testing." He began with a great high-level overview of what developers mean by testing before digging into the tool his team has built.
My talk focused on three areas where I had falsely assumed people were on the same page.
Assumptions prevent learning
The first area where reality did not meet my presupposition was everyone was aware of the issue of secrets sprawl. Plaintext credentials throughout the SDLC is a topic your author thinks about quite a lot. I am endlessly quoting stats from our State of Secrets Sprawl and Voice of the Practitioner reports. It is easy to forget not everyone has as much familiarity with this topic.
While definitely not a new problem, the term "secrets sprawl" itself has only been popularized over the last few years. It is not something many people have directly dealt with, even though almost all breaches now involve credential abuse in some manner. GitGuardian is here to help you with this. We would love to chat about maturing your secret security strategy.
Everyone learns technology differently
97%+ of all development utilizes Git for version control; it is the lynchpin of all DevOps workflows. This is a fundamental technology everyone making, running, and security code should be familiar with. Yet, at the same time, everyone assumes everyone already knows Git without stopping to think about what "knowing" it really means.
Git is magnificent in so many ways, allowing teams of any size and skill level to collaborate in a decentralized way. It is also unique in so many ways that it can be complex to grasp what is going on when a commit is made and pushed. It can be hard to see where the dangers lie. What other technology allows for time travel and transversal of parallel universes, all from the command line?
Without understanding that a shared commit is, essentially, eternal, especially in public, we can be lulled into a false sense of security that just overwriting an offending commit that contains a secret or making an accidentally exposed repo private again will fix the leak. Without understanding that all commits are cached even if disconnected from their parent commit and any branch, we might not put the right emphasis on rotation, the only safe and proven remediation path for exposed plaintext secrets.
Fortunately, there are a lot of free resources for learning Git, including the official Git SCM book and countless online videos that go well beyond the commit. We encourage everyone to learn at least how to implement git hooks to help developers bake security scanning as an automatic and non-disruptive step into their workflows.
Understanding the people you are securing
The paths people take into working in security rarely go through development and DevOps. At WWHF, I asked a room of practitioners how many people had ever deployed any code to production via a pipeline. Two hands went up out of about 40, or 5% of the room. This very unscientific survey does feel in line with the general conversations I have across the many conferences I am fortunate enough to attend.
The majority of folks in security don't have a DevOps background and have not been employed on a development team. That is one factor behind some of the miscommunications and arguments that devs and security seem to have, leading to the sentiment that security is "The Department of No."
Without the human empathy to understand the tradeoffs every deployment requires to meet deadlines, functional requirements, the complexity of interconnecting multiple third-party platforms, and meeting all uptime requirements, it can be easy for people in security to wonder why on earth they would do something in anything less than the most secure way possible.
My great hope is that more security professionals will meet the developers, platform engineers, DevOps teams, and really everyone, where they are. We need to strive to understand how others in our organization work and how security can help, not just where they can push back. And this extends well beyond traditional IT. Shadow IT makes up over 50% of the overall technical budget spent in the modern enterprise. Security teams need to widen their definition of a "developer" in the organization when they are raising awareness and providing training opportunities.
AWSCompromisedKeyQuarantine Policy is not a security feature
While all the talks were great, one session presented some startling information related to AWS and identity and access management. Bleon Prokods, Cloud Security Researcher at Permiso Security, presented "Breaking Free From the Chains of Fate - Bypassing AWSCompromisedKeyQuarantineV2 Policy." He also shared a recent blog post on this topic and the tooling they created in their research.
When an AWS User Key and Secret are leaked, a new account policy is placed on the account once detected by AWS. The policy denies access to a specific set of actions. It does not, however, revoke the credential or deny access to many of the actions allowed by the user. In his conversations with the AWS team, he reported this oversight, and their reaction is that this policy is not a security mechanism; to them, it is an anti-fraud issue to prevent unauthorized charges.
You can see this policy applied to any GitGuardian honeytoken when it is exposed publicly. This normally happens within seconds.
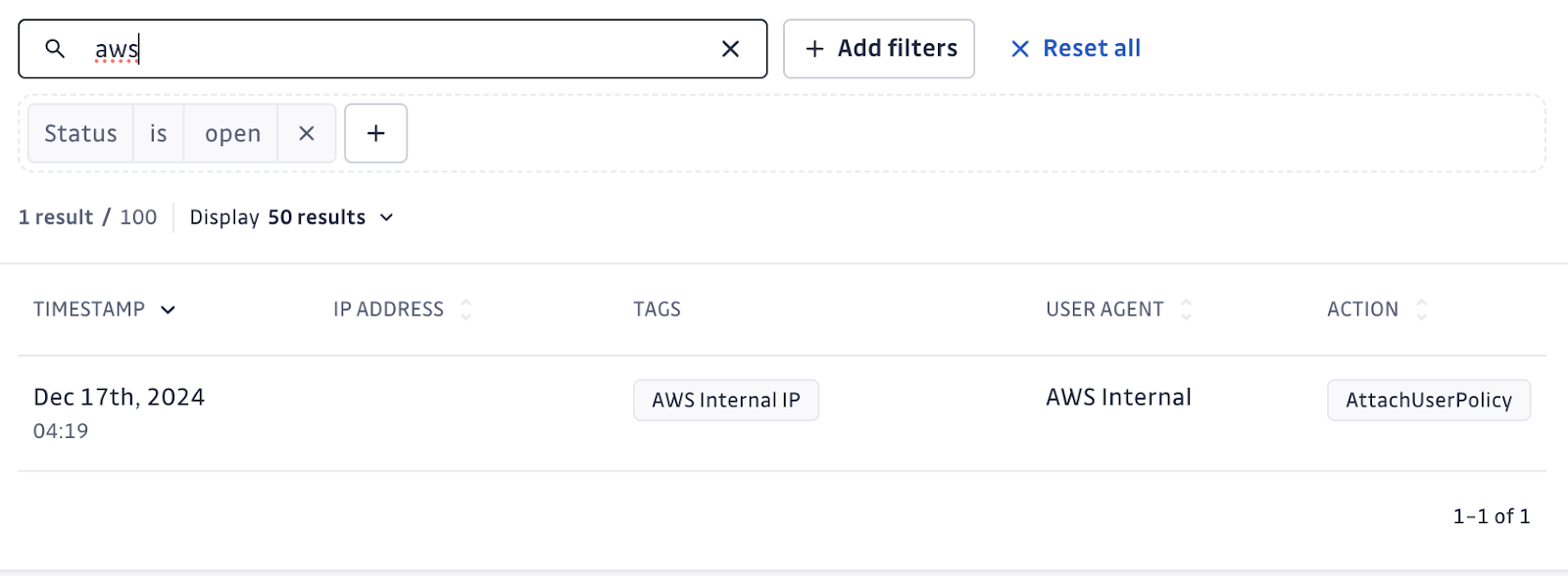
Bleon reminded us the only true remediation for a leaked credential is the swift rotation of the secret. There is a lot that can be done with an exposed AWS key, even if this policy is attached.

Finding common ground in Security
The importance of having a place to gather for security practitioners, which is generally an isolating and overwhelming role, can not be overstated. Getting to be part of conversations where individuals who have been collaborating online for years get the chance to meet in person for the first time was joyous and reinvigorating. The heart of security is not proving you are smarter than the next person; it is that we are doing our best, as people, to protect the people we care about. WWHF @ Mile High 2025 was a shining example of that community spirit in action.
No matter how long we have been in the industry or what area you focus on, we are all on this journey together. Let's work to continue finding common ground and work to make the world safer and more connected.
You don't need to wait for the next Wild West Hackin' Fest to meet your contemporaries and connect over your shared passion. There is likely a community event near you soon. Maybe we will even see you there.






