We are excited to announce the release of our Software Composition Analysis (SCA) offer, the latest addition to GitGuardian’s code security platform. It scans the dependencies of your applications to detect vulnerabilities, automatically prioritizes incidents depending on their context, and guides developers in fixing them throughout the entire software development lifecycle.
Its additional capabilities ensure code licensing and regulatory compliance, for example, by generating a comprehensive SBOM (Software Bill of Materials).
Open-source usage is growing… but so are the security and legal challenges it poses
Whether you like it or not, your software engineering team didn’t write 80% of your code.
Developers often use pre-existing code components created and tested by the open-source community to build projects, turning these components into dependencies of their code. This approach saves developers and organizations time and resources.
Understand how open-source transitive dependencies can become a security threat
Open-source software is not less secure than proprietary code. Both can include vulnerabilities leading to security issues. However, developers often unquestioningly trust community-validated open-source projects, which can make their dependencies a considerable security liability for organizations.
Even the most used libraries are vulnerable. Log4Shell is a critical security vulnerability that existed unnoticed from 2013 to 2021, affecting Apache Log4j, a widely used logging library in Java applications. CISA said it was one of the worst vulnerabilities seen in many years.
When Log4Shell was exposed, 93% of cloud environments were vulnerable. However, only half of them were patched within the 10 following days.
“If one of your buried dependencies becomes vulnerable, the blast radius could be gigantic. With an average of more than 500 direct and transitive dependencies per code project, it’s crucial to have a proactive strategy. You should shift left and consider implementing monitoring of your entire software supply chain. GitGuardian SCA offers automated context-based vulnerability prioritization and actionable remediation guidance. Without efficient tooling, your team will waste valuable time on minor issues while critical incidents remain unaddressed,” said Eric Fourrier, co-founder and CEO of GitGuardian.
Dependency vulnerabilities are only one dimension of the problem. Most code libraries have licenses dictating how they can be used, modified, distributed, and commercialized. Compliance with these licenses is mandatory to avoid legal issues and to protect intellectual property.
Additionally, due to recent government regulations in the US and Europe, legal teams now require developers to be more transparent and provide lists of code components in their projects, also known as SBOM.
Align application development and security teams in one platform
GitGuardian SCA is specifically designed for use in fast-paced DevSecOps environments. It equips security and developer teams with a unified vulnerability remediation solution, capitalizing on cross-team collaboration, incident visibility, and business context.
An application can use multiple programming languages, which is why SCA supports Java, PHP, JavaScript, Ruby, Python, Go, and Rust.
It integrates with your VCS, such as GitHub and GitLab, where the code is created, to provide a comprehensive view of the application and ensure no part is overlooked. It couldn’t be closer to your developer teams.
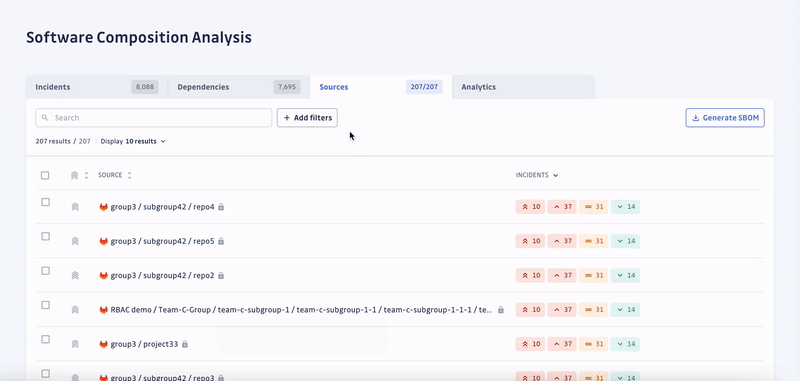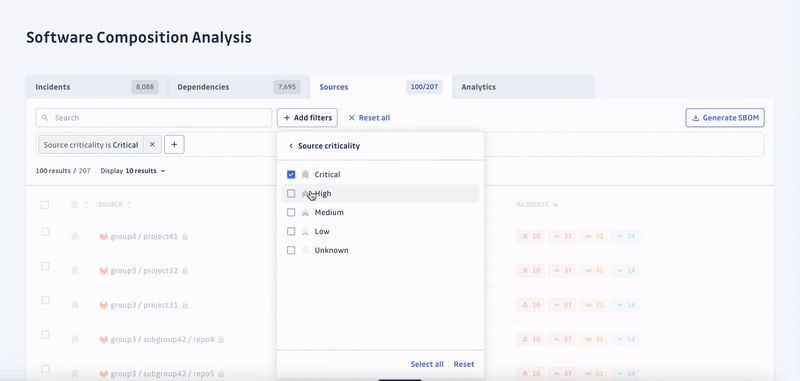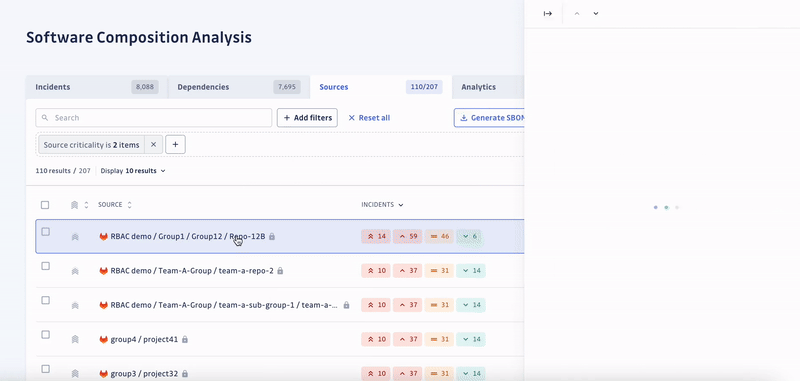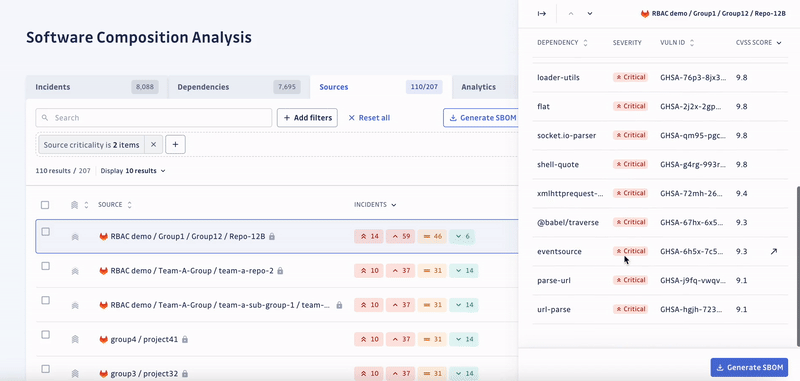
SCA enables security engineers to swiftly identify all applications with unsafe dependencies, consider the context to automatically prioritize incidents by severity, and prompt developers to fix them.
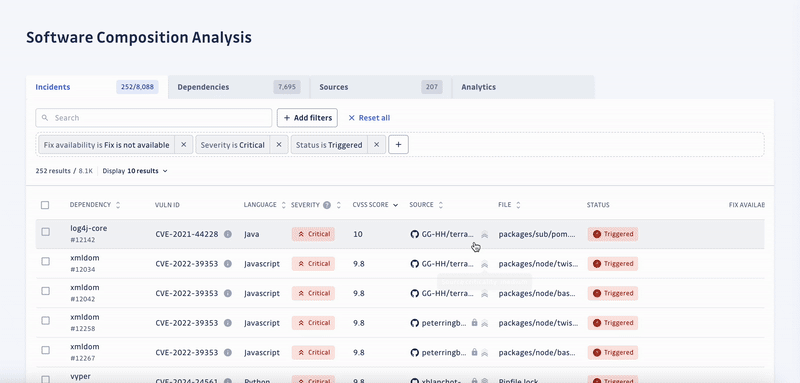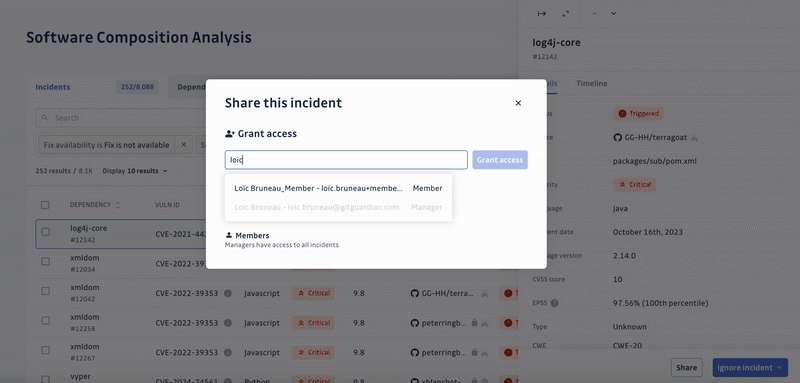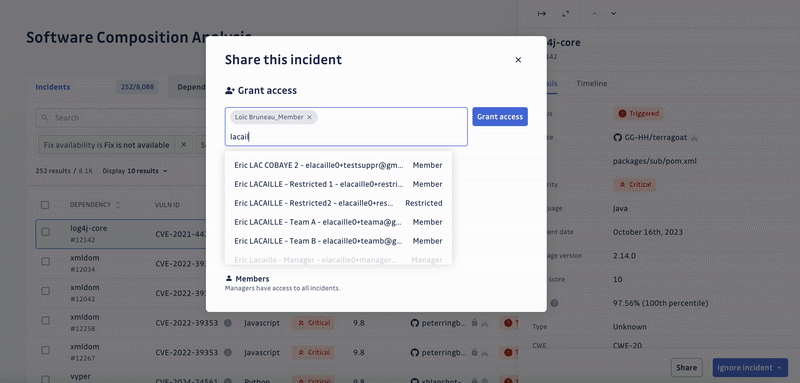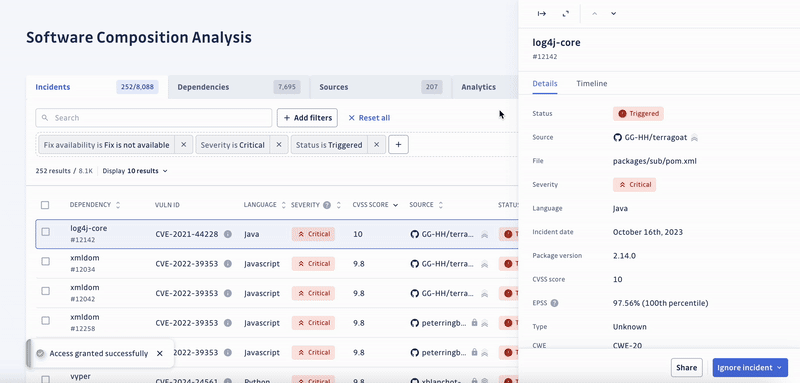
Detecting and prioritizing incidents is only the first step towards solving the underlying problem. Unfortunately, developers tend to neglect the remediation of vulnerabilities, which is the second half of the process. Yet, it’s critical to fix the incidents with the highest priority to ensure the security of the software supply chain.
GitGuardian addresses these concerns by offering actionable remediation guidance to software engineers without compromising delivery speed and agility.
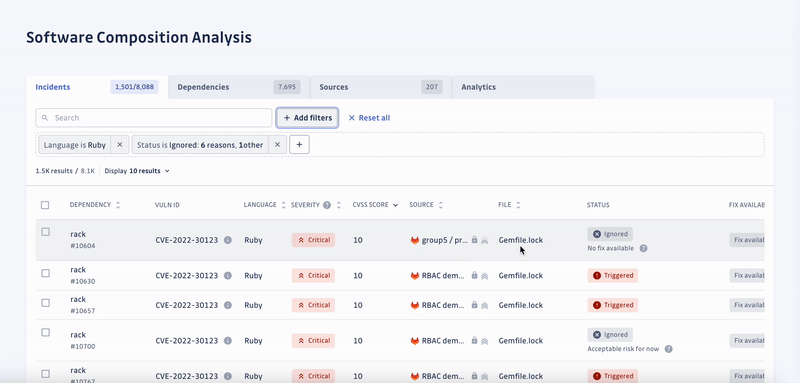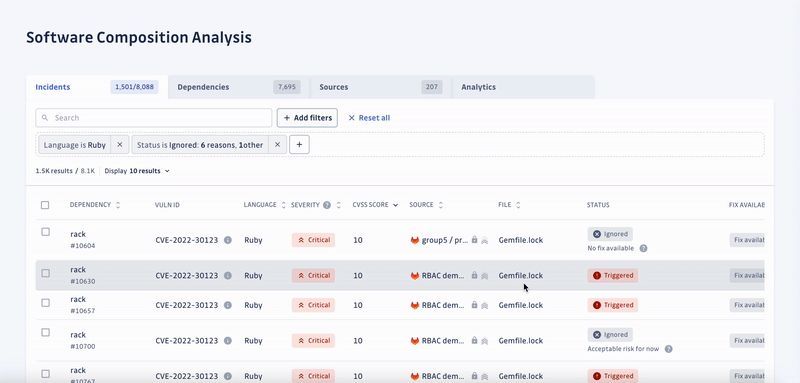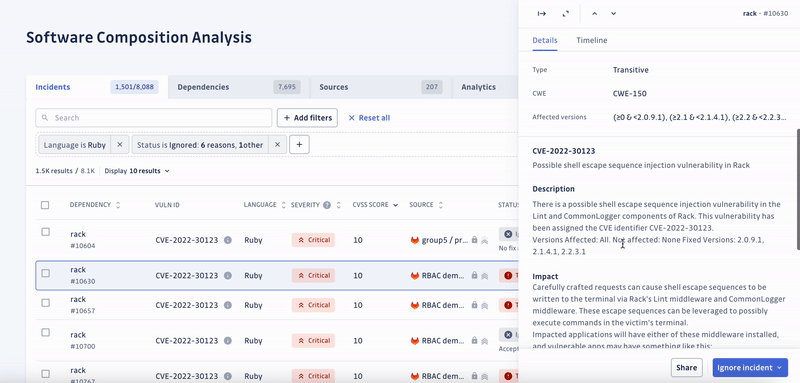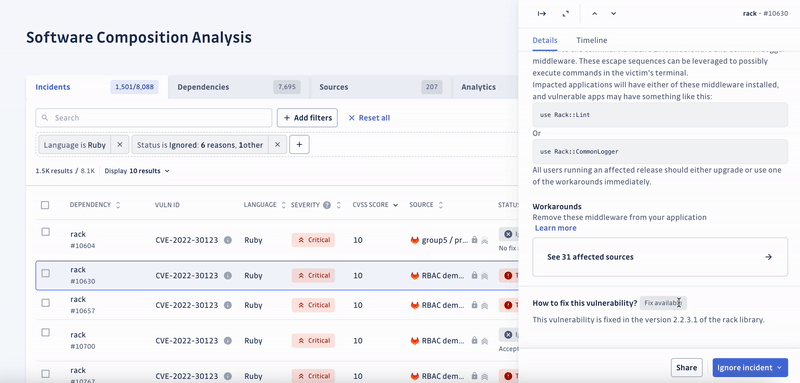
With organizations shipping faster than ever, you must assess how quickly you can respond to newly introduced threats.
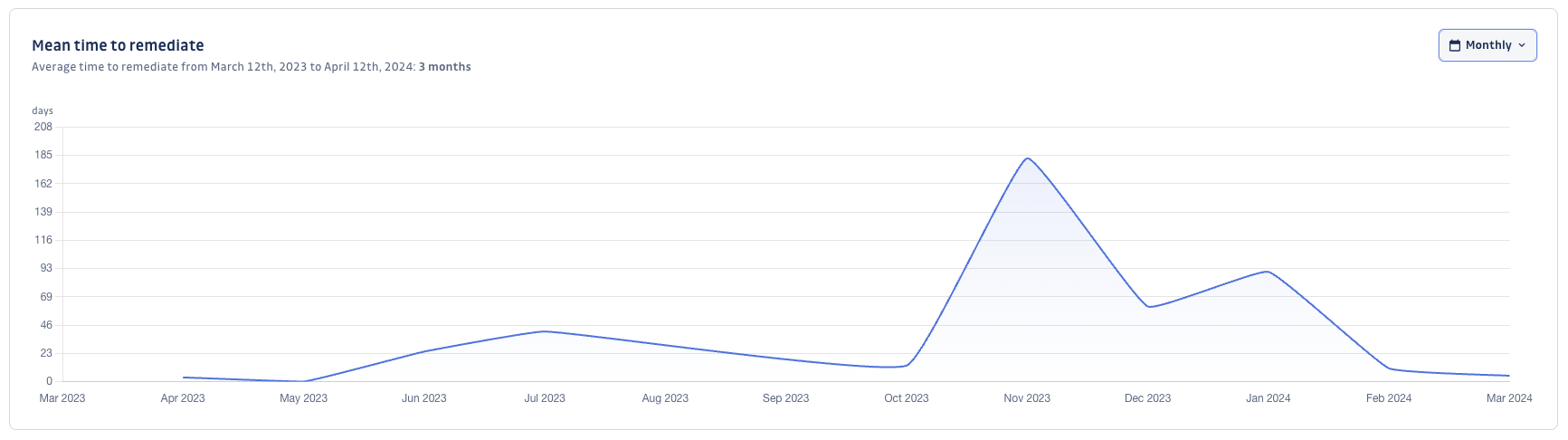
SCA detailed analytics allow application security teams to monitor their vulnerability exposure and track their remediation performance. GitGuardian empowers them to identify and eliminate bottlenecks for a streamlined development process.
Mitigate legal risks induced by application dependencies
Almost all open-source projects have a license attached to each of them. Many of these licenses encourage the adoption of Open Source, meaning that any changes to the code should be contributed back to the community.
Some licenses go even further with a copyleft clause, which requires that any software built using a copyleft-licensed library should be made fully available. This means that your business logic would also need to be made freely available.
SCA reduces risks to your intellectual property by identifying licenses in your direct and transitive dependencies.
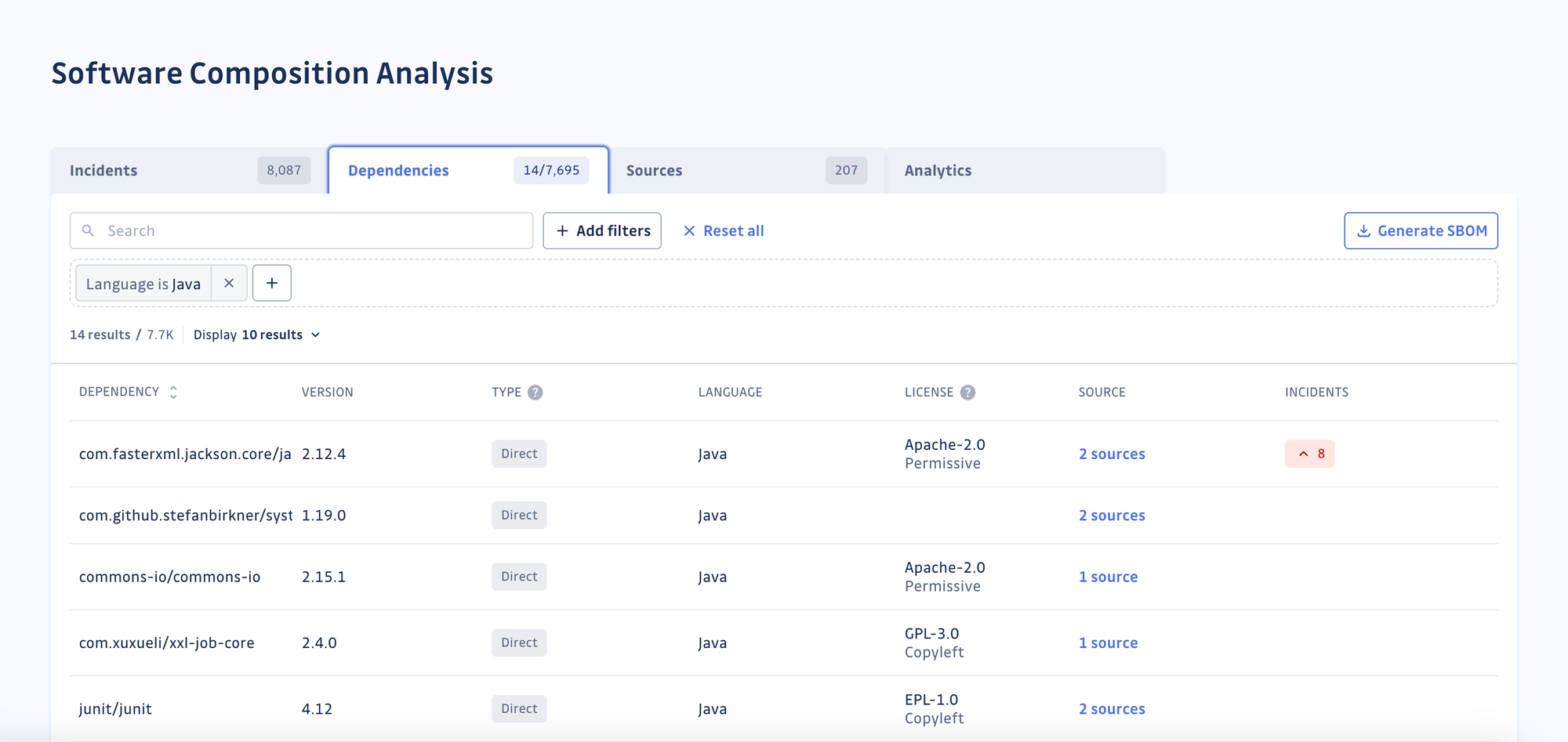
SCA can assess legal risks in the software supply chain. By generating a comprehensive SBOMs of applications’ open-source and third-party components, it helps organizations comply with license and security policies.
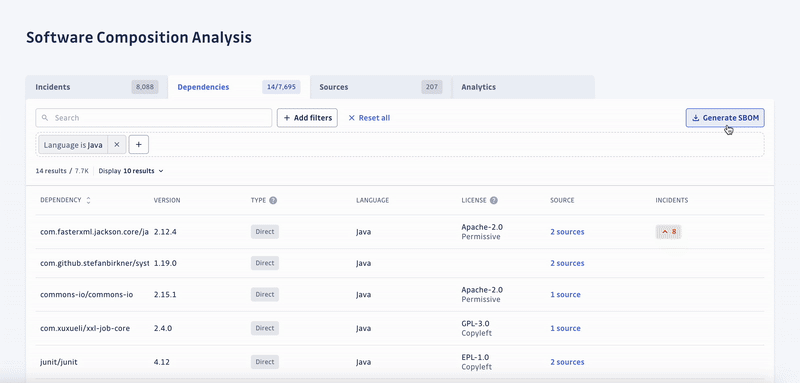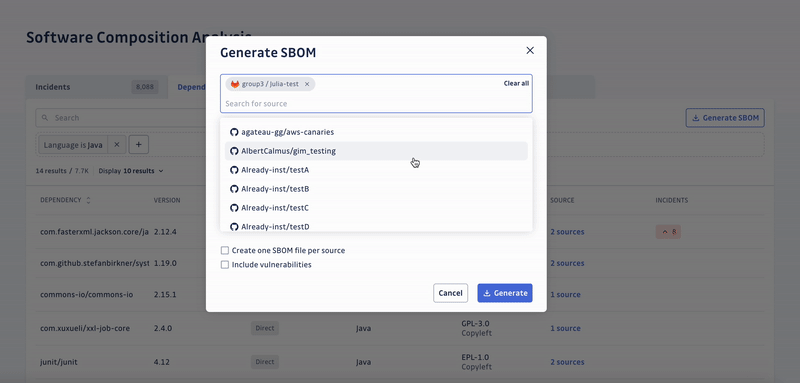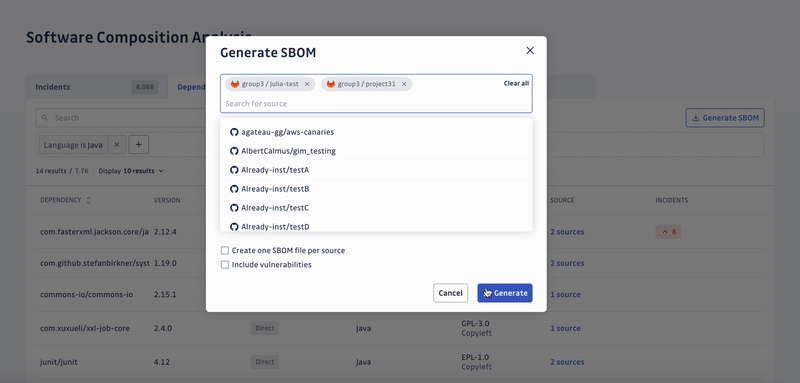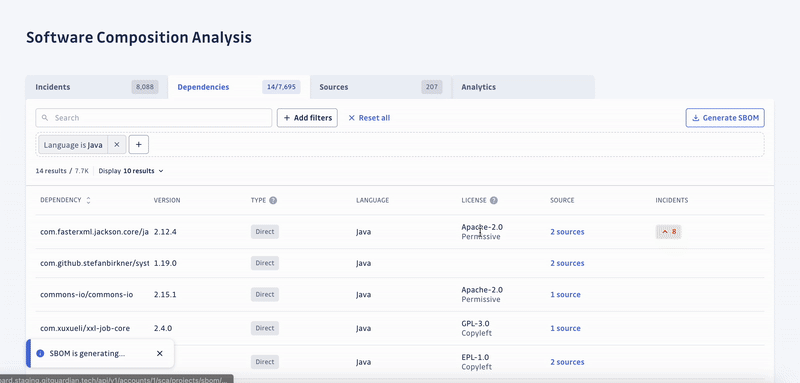
Beta testers of SCA were impressed by its ability to analyze deeply nested transitive dependencies, which are the dependencies of your dependencies.
A security architect at a health tech reported, “I have looked at another vendor saying they support direct and transitive dependencies. And when I scanned my repository, which had roughly 30 direct and some 3,000 indirect dependencies, they only found 35 of them.”
When the same repository was scanned using GitGuardian SCA, all 3,030 dependencies were detected with their expected distribution.
Stop piling on vulnerabilities
New CVEs will keep appearing. You’re going to introduce more dependencies to your code. That’s why you want to prevent threats as early as possible.
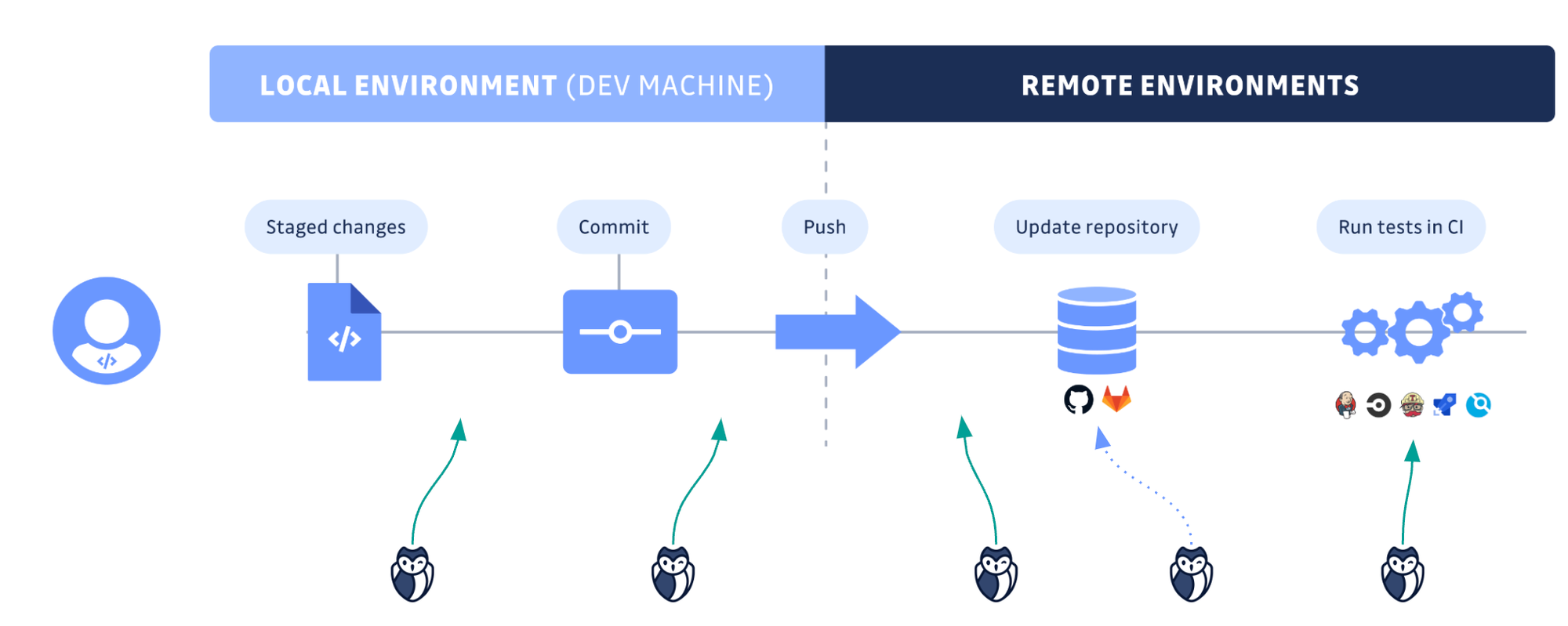
GitGuardian’s constant support of shift-left practices helps reconcile software and security engineer teams without sacrificing execution speed. As part of its ongoing efforts to reduce organizations’ attack surface, GitGuardian has extended SCA capabilities to its CLI tool ggshield.
It offers prevention at each stage of the software development lifecycle, from local engineer’s environments to continuous integration (CI) pipelines, without disrupting developers’ workflow. Finding and fixing vulnerabilities as early as possible is by far more cost-effective than post-release security.
GitGuardian SCA is quickly evolving to adapt to new risks
“We're not stopping here. Next on the roadmap is detecting malicious dependencies to prevent dependency confusion and typosquatting. That's exactly what happened when the Python package 'ctx' was hijacked to steal AWS keys. And we’re working on more dimensions to prioritize remediation, for instance, the likelihood of vulnerabilities being exploited," Eric Fourrier added.
And the list goes on! In the upcoming weeks, we’ll add the following features:
- Shift-left efforts evaluation to track your performance in safeguarding your repositories through ggshield,
- Activity-based metrics to help you prioritize remediation of the incidents for your most active repositories.
80% of organizations release code frequently, but less than 30% continuously audit it, often due to a lack of a comprehensive security platform.
GitGuardian’s product suite addresses this gap by integrating a range of security tools, including Secrets Detection, Public Monitoring, Software Composition Analysis, Infra as Code Security, and Honeytoken.
For more information, check out our documentation.
See upcoming sessions








