Introduction to CSPM
In practice, CSPM essentially means monitoring configuration for everything an organization runs on AWS, Azure, GCP, and other cloud providers. Securing an organization's underlying infrastructure has always been important, but how that happens has shifted dramatically. When everything lived on-premise, physical security or a “Guards, Guns, Gates” mentality was enough to keep things locked down. Now, in our everything-is-always-connected world, where the perimeter is undefined and ever-shifting, it has become critical to adopt a new security posture that protects an organization’s cloud infrastructure.
The Challenges that gave rise to CSPMs
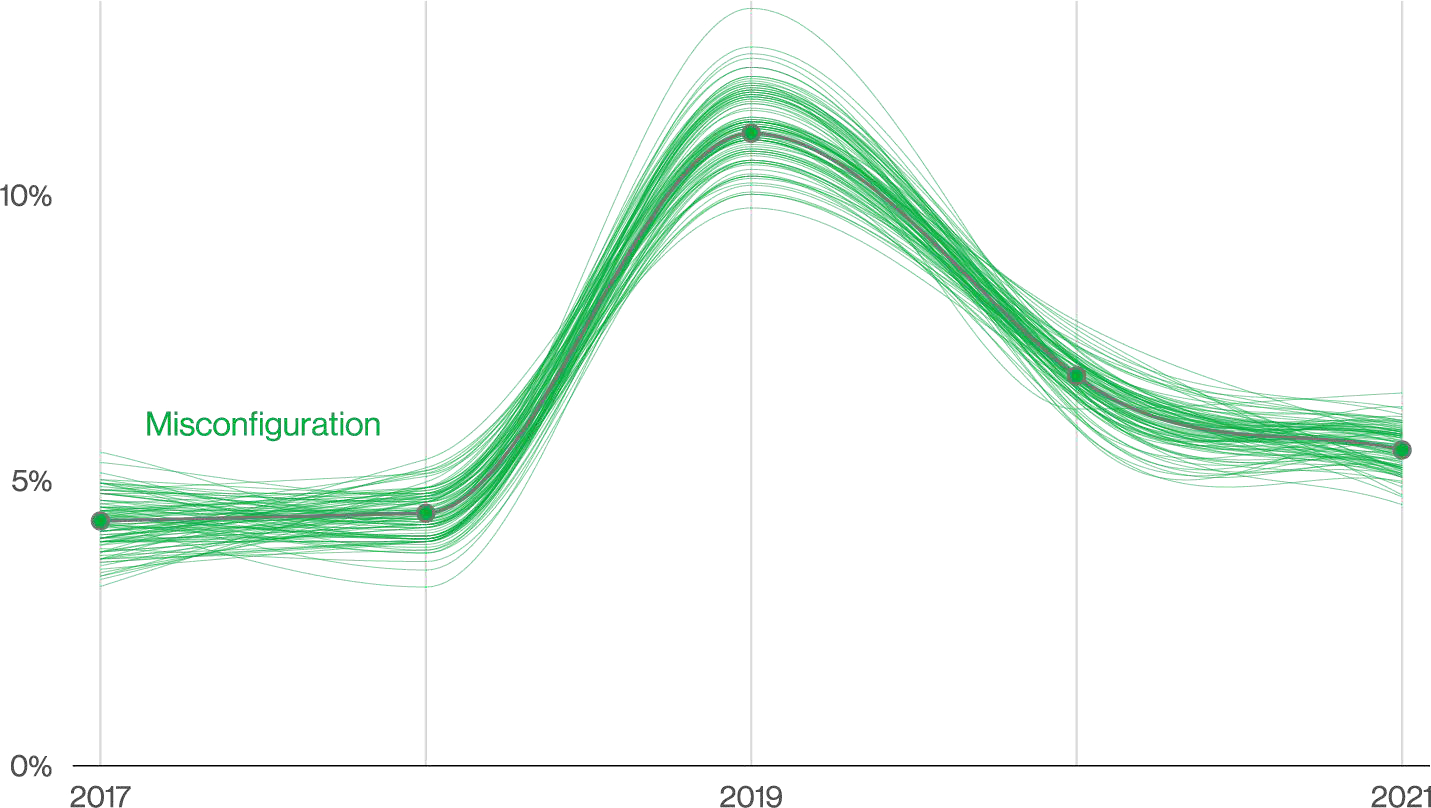
As organizations began their digital transformation to cloud-based applications, it became apparent that misconfigurations were a significant cause of breaches. The benefits developers experienced, like being able to spin up infrastructure on demand, often meant adoption outpaced the ability to track or secure that infrastructure. Without proper technical cleanup procedures, forgotten and unused keys, identities, and infrastructure build up over time, leaving teams unaware of these avenues for attackers to exploit.
When teams realize the risk of misconfigurations and start looking to adopt a security posture for their environments, they quickly realize that large swaths of it are untracked and unknown. Skunkwork projects and ad-hoc solutions have created unknown resources, often referred to as Shadow IT, which can be exploited since this rogue infrastructure has no oversight.
Benefits of CSPM
This problem grew alarmingly quickly, becoming a leading contributor to breaches, so new security tools were developed to track all of those cloud assets and provide visibility into their configuration. These tools were eventually categorized as Cloud Security Posture Management (CSPM), and their widespread adoption across large enterprises has helped to drive down the number of breaches related to misconfigurations in recent years.
Runtime Visibility
Cloud Security Posture Management focuses on runtime visibility, providing information that reflects the actual live environments. A corollary to the prevalent shift-left security mindset, which adopts security best practices from the earliest stages of application development, is verification. A CSPM shouldn't replace other security tools but work as a companion to provide real-time running visibility.
It’s important to understand that runtime is different from production; runtime refers to anything running in the cloud. With cloud service providers, staging is usually a run-time environment, and if not part of your security posture, it can be exploited just like production. The good news is that once all cloud assets are correctly included, teams can know what their security posture looks like and how to improve it.
Asset Discovery
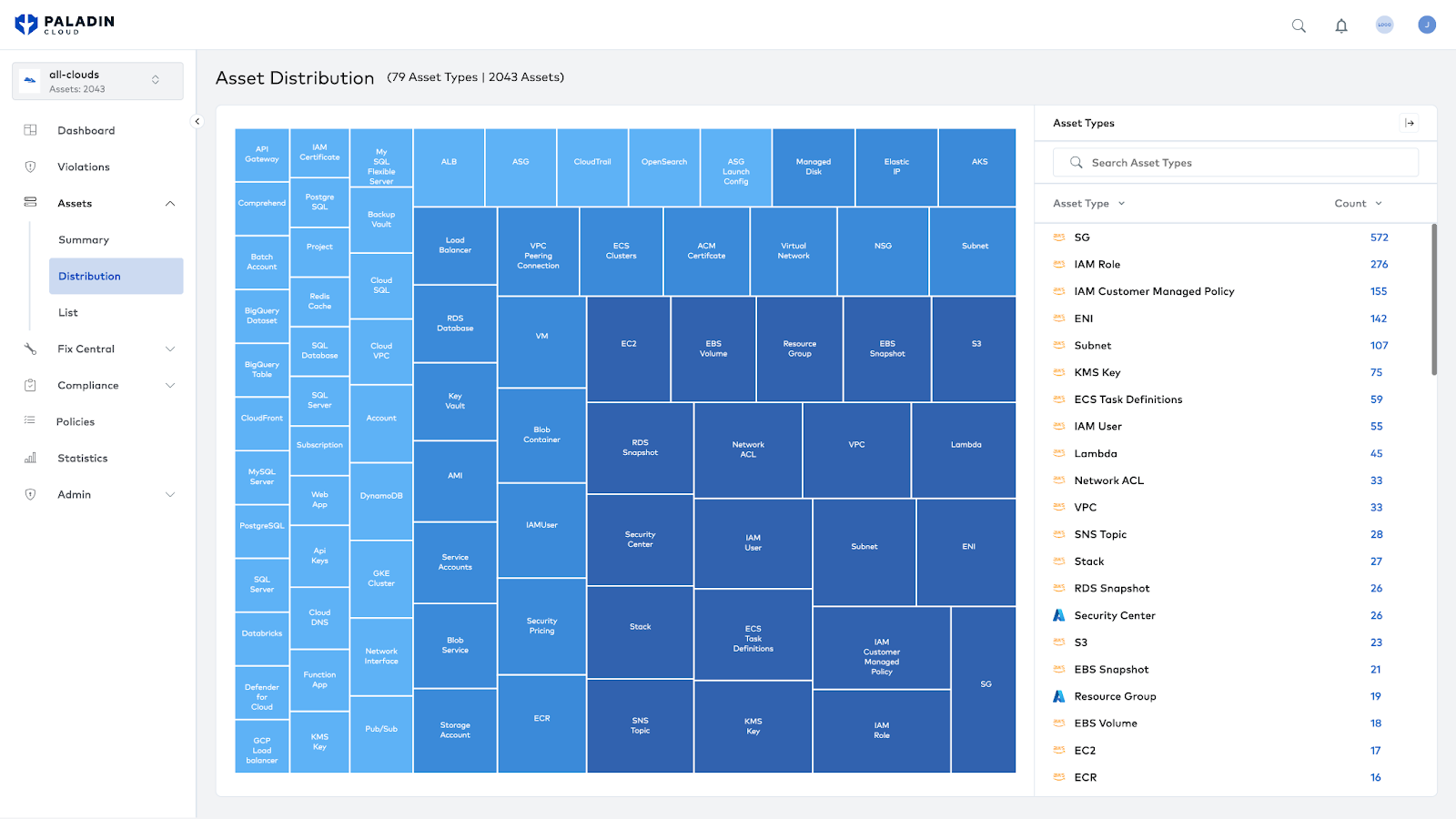
To provide that level of visibility, CSPMs must first ingest assets from across the cloud. Assets refer to the computing, networking, storage, and services cloud provider services offer. By connecting all of an organization’s accounts, subscriptions, or whatever provider-specific term refers to the owning logic, a CSPM can map all available assets. This data is beneficial, as it can identify Shadow IT, forgotten assets, and anomalies that are either anti-patterns or evidence of intruders.
Security Monitoring
On top of the asset map, security checks are run to validate that assets are following best practices. Because cloud providers want to make their services as easy to use as possible, the defaults are nearly always as permissive as possible. It is helpful for the first-time developer trying to connect a database to their Hello World application, but extremely dangerous for an organization looking to secure confidential data. By monitoring each asset for security best practices and flagging violations, teams can rest easy knowing they haven’t mistakenly left a back door open.
Foundational Security Component
Cloud security posture management deals with the foundational blocks on which the rest of the organization’s security is built. Application, Identity, and Data Security all rest on top of cloud infrastructure. A simple misconfiguration in the underlying layer can compromise an otherwise well-secured asset. For example, you could have the best alarm and detection system, but if someone doesn’t turn it on, it does no good.
Best Practices in CSPM
Teams can get the most value from their security posture by following best practices when implementing and configuring their CSPM tool(s). optimizing coverage for your organization's unique footprint and team dynamics will provide the best results.
Multi-Cloud Support
When selecting a CSPM, it is crucial to consider your existing cloud footprint and how you expect to grow in the next few years. While the major cloud providers offer services to help manage security posture, over 85% of organizations use more than one cloud provider.
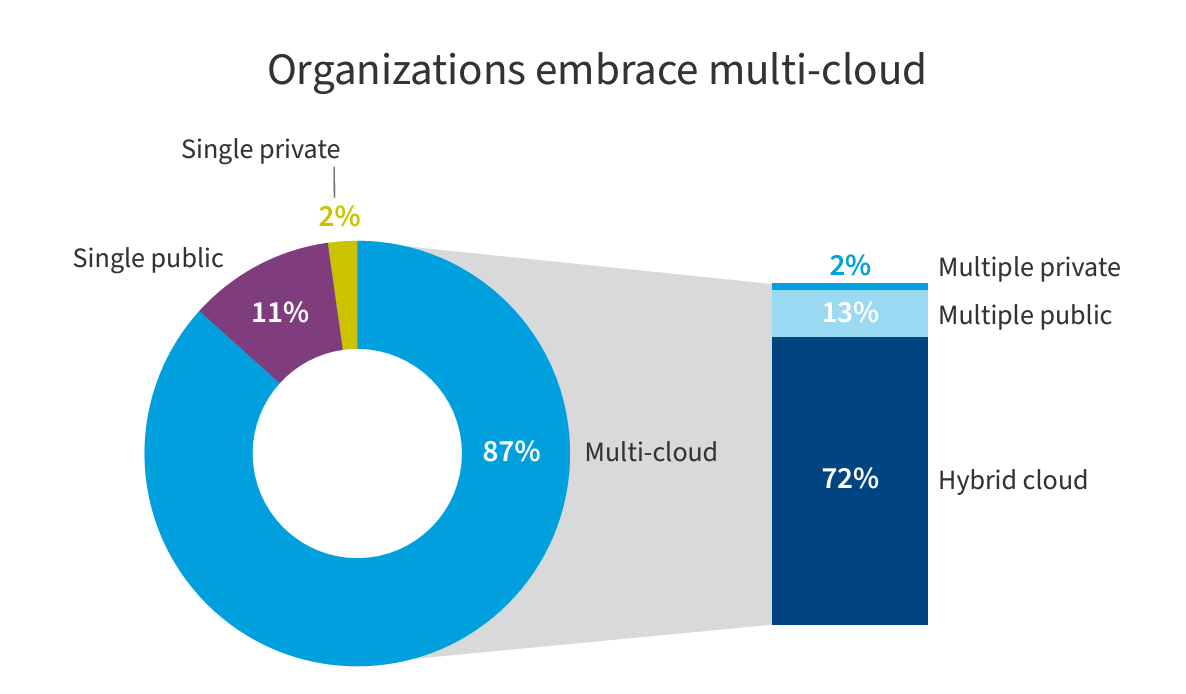
Finding a CSPM tool that can consolidate coverage across all your cloud environments will ensure the whole picture is visible and avoid the overhead of consolidating data across multiple CSPM tools or, worse, leaving gaps in coverage.
Remove Information Silos
Tools in and of themselves aren’t enough to solve problems; success requires a human component. The information that CSPMs provide is essential to both security and DevOps teams. Those teams should have a strong working relationship to ensure the highest level of security cooperation.
Unfortunately, many organizations find these teams siloed with combative relationships. This siloing of departments and teams is often exacerbated by licensing seat restrictions limiting who can access what data. The result in these situations is a “throw it over the wall” approach where developers are periodically tossed a spreadsheet or report that lacks context and is expected to remediate an endless list of security items.
Instead, build a security-first culture across the organization. Democratize security by integrating the required collaboration and communication across all teams. Provide developers with the access they need to see the security posture of their applications so they can quickly remediate and learn from identified risks. Integrate your CSPM findings into existing developer ticketing tools so remediation is a part of their standard workflows.
Developers want to build secure applications but often lack the needed visibility. Time and again, I’ve seen that when organizations equip developers with the knowledge and tools required to secure their applications, they rapidly adopt far more secure development practices.
What’s Next for CSPMs?
As the cloud continues to evolve, so too must our security posture. CSPMs are part of a larger ecosystem of security tools, and the next generation of CSPMs is harnessing that aspect to enhance overall security.
Correlating CSPM Data with Other Security Tools
Since the infrastructure that CSPM monitors underpins the rest of an organization's security posture, CSPMs are starting to connect with other security tools and correlate the information to give a richer picture of an organization's vulnerabilities.
For instance, if an unpatched SSH vulnerability exists on an asset with an open SSH port, that’s a much more significant risk than either issue taken in isolation. The total risk is understood by correlating the CSPM finding (Open SSH port) with the finding from a vulnerability management tool (SSH CVE). In addition, a kill chain is identified, as closing the SSH port mitigates the risk until the more time-consuming process of patching the SSH port vulnerability can happen.
Another area is Identity and Access Management (IAM), which is a growing area for concern; in 2022, over 10 million keys were identified as exposed in code repositories. A CSPM tool will monitor if an organization requires key rotation regularly, but it doesn’t monitor how and where those keys are used. By integrating with the findings from a tool like GitGuardian, which identifies and remediates exposed secrets, an organization can be confident they are both rotating secrets regularly and that none are sitting exposed in a codebase.
Leveraging AI for Critical Risk Identification and Prioritization
AI is finding new uses in every sector, and security is no exception. Unsurprisingly, CSPMs are turning to AI to provide new insights and increased security. AI excels at working with large amounts of data, and one of the most prominent challenges teams face is the tremendous amount of security data coming in. This alert fatigue is pervasive for teams first adopting CSPMs; for large clouds, it’s common to see critical violation numbers in the 10s of thousands. These teams can struggle to understand where to start and what risks are most important.
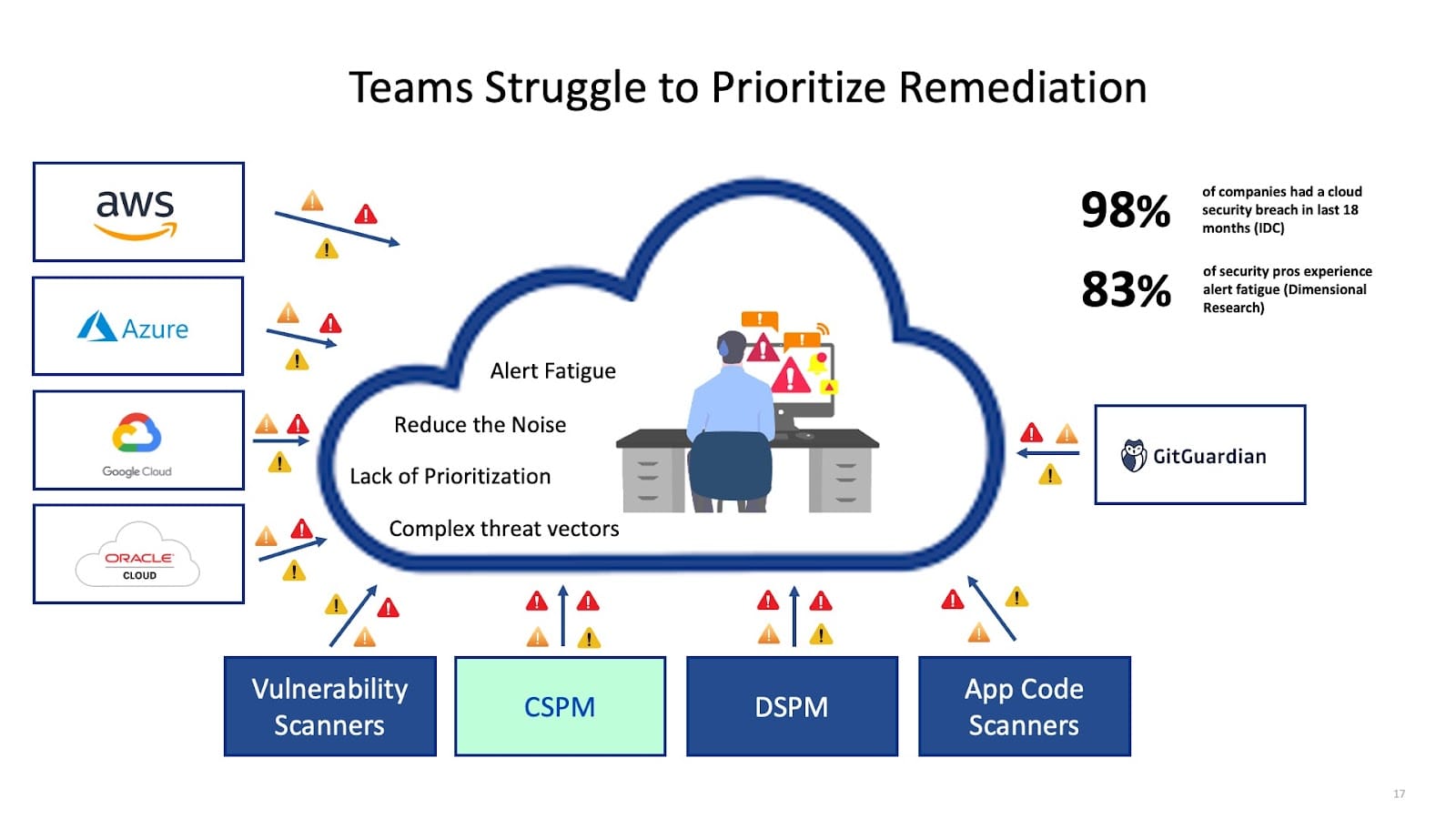
Platforms like Paladin Cloud use generative AI to analyze all the findings from your CSPM and connected tools to calculate a risk score. Those individual risk scores are correlated to calculating an overall risk score for each asset in an organization's cloud. Using these risk scores, teams can quickly identify their most significant risks and stay focused on having the largest impact.
Conclusion
Cloud Security Posture Management is critical to any organization's security infrastructure, and infrastructure is the foundation for everything else in the stack. CSPM helps organizations to identify and prioritize the security misconfigurations and risks to their cloud environments, providing a comprehensive view of cloud assets and driving remediation workflows.
With the right CSPM solution, teams can gain runtime visibility, asset discovery, security monitoring, and correlation across security tools to ensure a comprehensive and effective security posture. By adopting best practices in CSPM, organizations can reduce the risk of breaches, protect their cloud infrastructure, and cultivate a security-first culture.
This article is a guest post. Views and opinions expressed in this publication are solely those of the author and do not reflect the official policy, position, or views of GitGuardian, The content is provided for informational purposes, GitGuardian assumes no responsibility for any errors, omissions, or outcomes resulting from the use of this information. Should you have any enquiry with regard to the content, please contact the author directly.




