You can't see The Golden Gate Bridge from downtown San Francisco, but if you stand at the right intersections, you can see The San Francisco-Oakland Bay Bridge. While not as famous as its ocean-facing sister, the Bay Bridge, as most people call it, carries almost twice the number of daily commuters back and forth between SF and the East Bay. It felt very appropriate that it was closer to this bridge that so many security practitioners got together to find common ground and discuss how to make a better and safer future together at BSides SF 2024.
This year marked the largest BSides San Francisco has ever held, bringing together 2682 total participants, including 105 presenters and 203 volunteers. Over the two days before the RSA Conference, cybersecurity professionals had the chance to talk about the state of the industry, share what we have learned about the rapid evolution of AI and LLMs, and, of course, have a lot of fun and make many good memories at the Metreon, in the heart of downtown SF.
It would be impossible to thoroughly report on every amazing detail that made this year so special, so here are just a few highlights from BSidesSF 2024!

Investing in the future of AI means investing in our vision of tomorrow
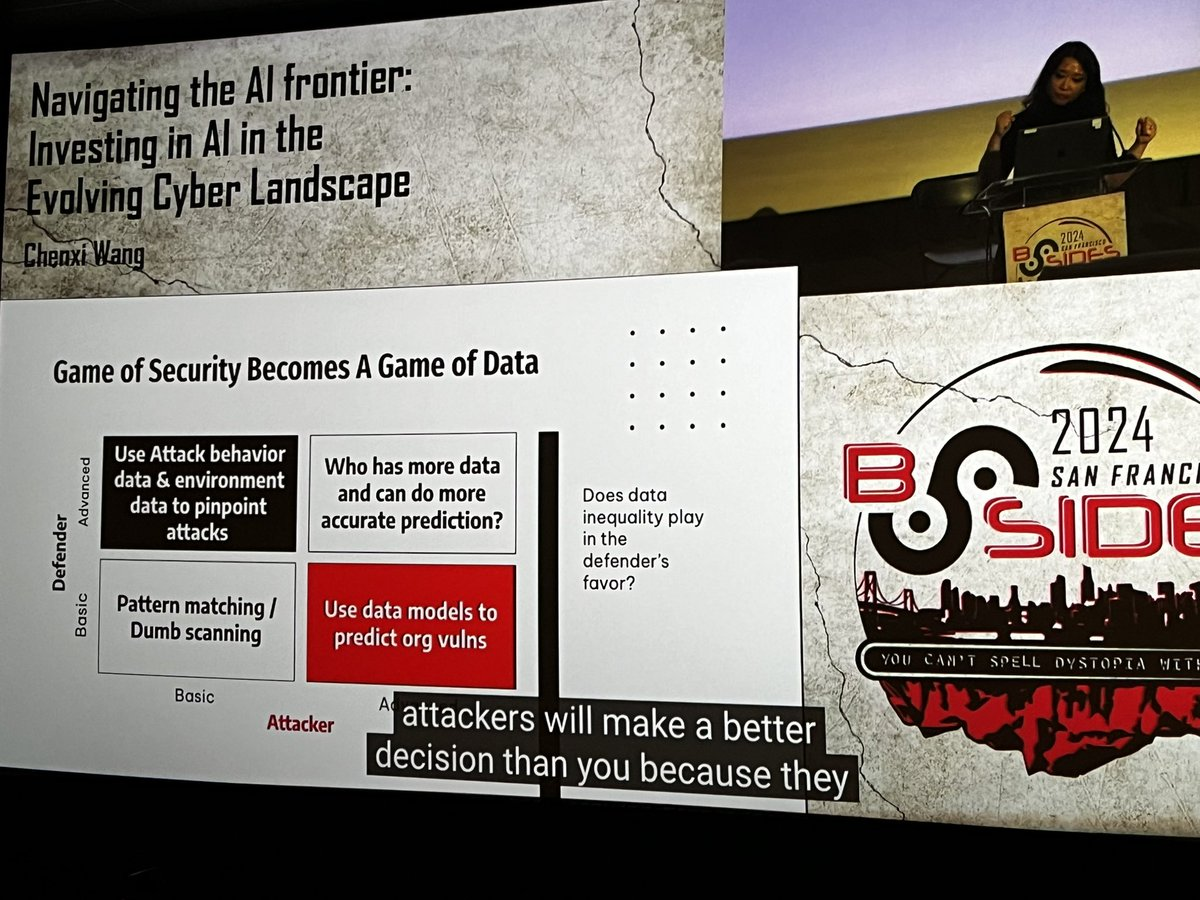
In her talk, "Navigating the AI Frontier: Investing in AI in the Evolving Cyber Landscape," Chenxi Wang, Ph.D., Managing General Partner of Rain Capital, discussed the rapid adoption and growth of AI technologies like ChatGPT and where the money is currently being spent on and around it. We are still in the early stages of building foundational AI infrastructure; application usage is still relatively minor compared to most technologies.
The potential for AI to transform and create a new era in technology and security is immense and has many investors interested. For example, she shared how one healthcare company was able to use AI to answer patient questions much more accurately, especially when dealing with complex situations involving insurance. From a security tooling perspective, she described how AI could revolutionize threat detection by using advanced data analytics to predict and pinpoint attacks more accurately.
She talked about where investors are focused and what they have researched at Rain Capital. She noted that if an AI application can be written over a weekend by a couple of engineers, then there is not going to be anyone who likely would invest, as that tech can be easily recreated. On the other hand, companies that are building new infrastructure and finding novel ways to deal with the unique challenges of training and running AI will attract a lot of interest right now. She concluded that today, approximately $200 billion is spent on AI in the market. Half of that is spent on services, which will only increase in the near term.
Not all advanced persistent threat actors are nation-states
Senior Staff Security Engineer Benjamin Hering's session "Advanced Persistent Teenagers: Understanding the Lapsus$ Playbook" detailed how a group of young adults in the UK and Brazil rewrote the book on attack paths. The sophistication and impact of this group may seem crude in some ways, but it has proven highly successful.
Primarily utilizing advanced social engineering tactics, exploiting multi-factor authentication fatigue, voice phishing, and help desk impersonation, these attackers have gained significant unauthorized access into companies like Uber and Okta. And while there is no evidence that Lapsus$ was behind the MGM breach of 2023, the playbook the attacker used seems to be copied from Lapsus$.
Benjamin also stressed the need for organizations to adopt phishing-resistant multi-factor authentication (MFA) solutions to counter these new approaches. We also need to re-evaluate the human element in our security protocols. For example, if the call center at MGM had a passphrase system, then the person impersonating them would have been blocked, and no new password or MFA token would have been issued. Fortunately, the Lapsus$ playbook is known and well-researched, so enterprises can also leverage it to prepare for these new types of attacks.
Advice from those who learned the hard way
BSidesSF featured some serious talent on the panel discussion "Titans of Scale: Strategies to Scale Security in Expanding Organizations." The panelists included:
- Mukund Sarma, Senior Director, Product Security at Chime
- Jeevan Singh, Director of Security Engineering at Rippling
- Ariel Shin Engineering Manager, Product Security at Twilio
- Jacob Salassi, Director of Product Security at Snowflake
- Julia Knecht Senior Manager, Security Platforms Engineering at Netflix
Together, they shared their experiences in scaling security measures within rapidly growing enterprises. Each of the panelists tension between centralized and decentralized approaches to security. One by one they all shared stories of times they failed while trying to scale security, with multiple panelists saying they found out that practices that worked well with small teams rarely translated successfully to larger teams or across the whole organization.
While the term 'shifting left' was not said out loud, almost all the participants discussed the criticality of embedding security early in the development lifecycle. One other common note was that we need to, as one panelist put it, "Work with people as people first." We need to assume good intent and help enable people as security practitioners; that is the only way we can really scale. ,

Getting the basics right in security goes a long way
Kevin Hanaford, Head of Trust Engineering at Discord, reminded us that perfect security is unattainable at the very beginning of his talk, "Imperfect Security: Doing Less to Achieve Better Security." Perfect is the enemy of the good, and we can get pretty good, but imperfect security by just focusing on the basics.
While we need to focus on real-world constraints and operational realities, we must put the user, who is human, at the center of all our efforts. Kevin said security is a human problem since almost all attacks involve human elements. Most people want to do good, but often, people don't know what the right thing to do is exactly. In the day-to-day work of most people, convenience often outweighs process. People are also slow to adopt change, so we must be patient as we help them establish new, safer habits.
Kevin said we should be creating "paved paths" with strong guardrails to empower teams, reducing friction in security processes. We have to get away from being the "Department of No.' If we say 'yes' more often then we become much more approachable. Then, as we gain trust, we can actually help improve their security posture. We also need to remember to have fun and bring a positive attitude back to security, as people like working with positive people.

Forging a new, safer path forward together
One common theme that popped up in a number of sessions was the pervasiveness of long-lived credentials, especially for machine identities. This was something that your author got to speak about in a session called "Long Live Short Lived Credentials" where I discussed auto-rotating secrets and finding all your secrets with tools like the GitGuardian Secret Detection platform. I also discussed the ways we can integrate with secret management platforms like CyberArk's Conjure.
Another theme that was persistent through every conversation and interaction was joy. BSidesSF is very special to so many people in the security community. New folks were made to feel welcome, and returning community members greeted each other with hugs and smiles. While the subject matter was troubling at times, as the security community faces a lot of challenges, the spirit of the event left us all feeling a little better that we are not facing these threats alone. I am already looking forward to next year, which might be the biggest BSidesSF yet.






