Have you heard about canary (or honey) tokens? In his latest Security Zines, Rohit Sehgal explains what they are and how they offer a smart solution for implementing intrusion detection in any system.
We are also pleased to introduce ggcanary, the easiest way to create ready-to-disseminate AWS-based canary tokens.
ggcanary is a fully open-sourced project using Terraform to manage your canary tokens infrastructure. Using well-known AWS components, it is ready to be deployed in minutes.
- Use Terraform to manage canary tokens infrastructure
- Deploy up to 5,000 canary tokens on your perimeter
- Track every action with AWS CloudTrails logs
- Get real-time email alerts when canaries are triggered
Start now! Create your first canary token with ggcanary...
Canary tokens can be used everywhere on your infrastructure to lure attackers:
- Source control systems (Git repositories)
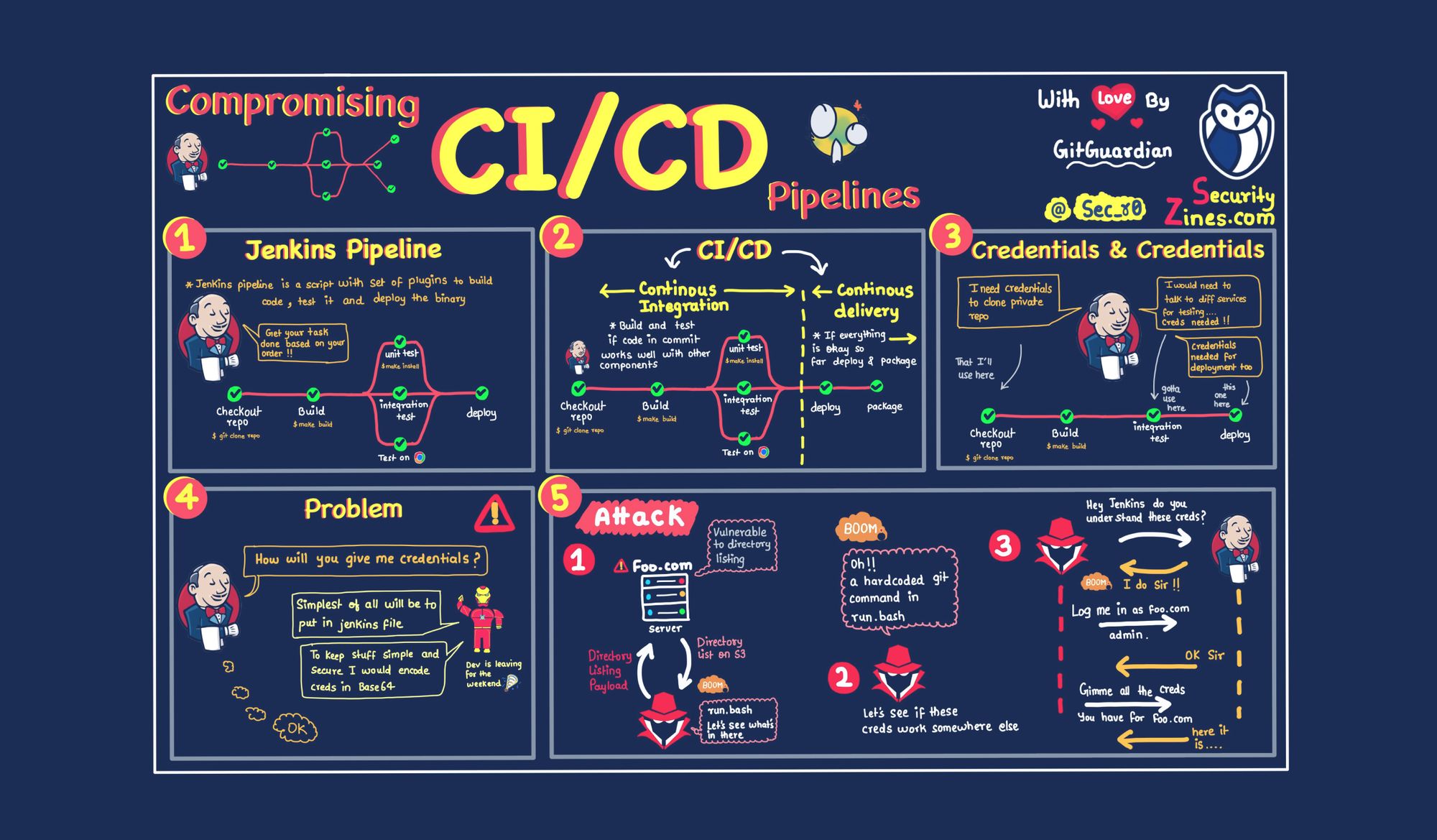
- CI/CD systems
- Internal registries & package managers
- Production environments
- Other places in the supply chain
Want to learn about supply chain attacks and why intrusion detection can prove useful?





![Canary Tokens [Security Zines]](/content/images/size/w2000/2022/08/blog-SecurityZines-CanaryTokens.jpg)


![Precision & Recall [Security Zines]](/content/images/size/w600/2024/10/Recall-in-Detection.png)
![Honeytokens [Security Zines]](/content/images/size/w600/2024/09/Honeytokens.png)
![Software Composition Analysis [Security Zines]](/content/images/size/w600/2024/05/SOPS-Security-Zine--1-.png)
![SOPS [Security Zines]](/content/images/size/w600/2024/03/SOPS-Security-Zine.png)
