Over the past few days, a discussion has been happening on HackerNews around counter-intuitive GitHub features that allow anyone to access commits you thought had been deleted. As reminded on this page, these behaviors are well-known and were reported to GitHub back in 2018.
For storage efficiency, GitHub places repositories and forks in a network where all commits are saved together, and each fork keeps references separately. When a commit is deleted from a repository, it stays visible within its network of forks.
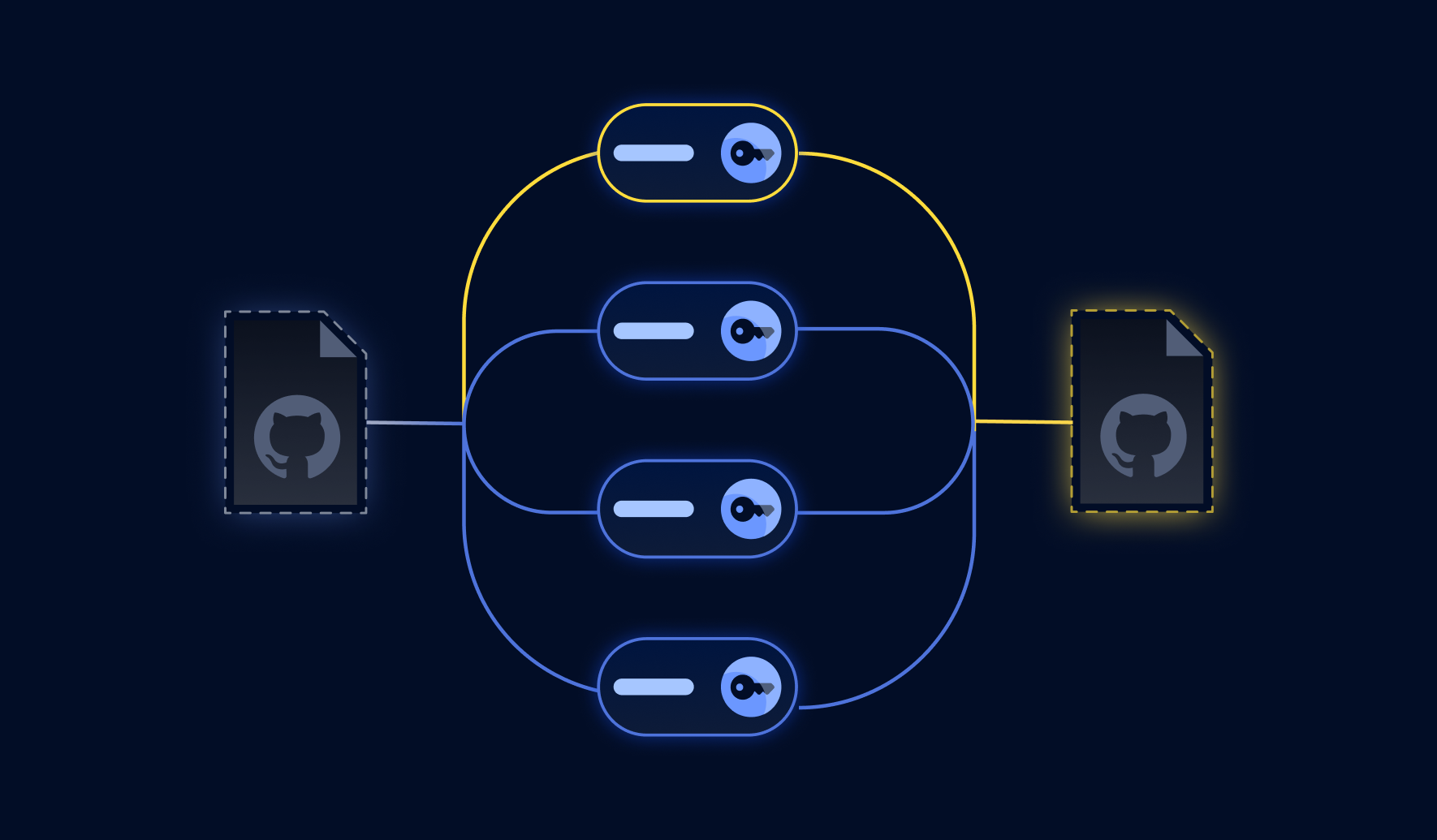
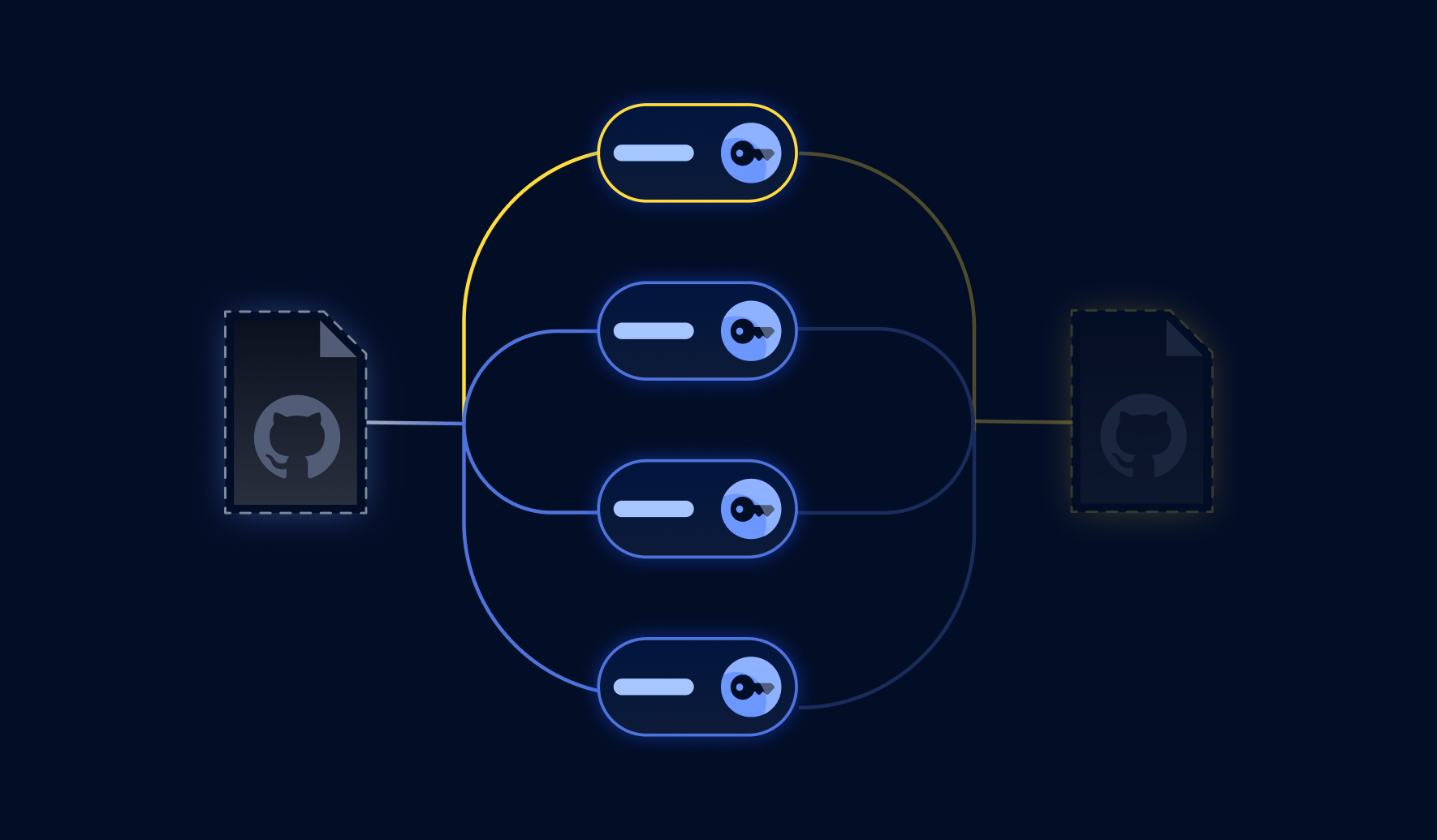
The yellow commit remains visible by the network even after the repository is deleted.
As a developer, you may have already noticed that when you do a force-push, the corresponding Pull Request still mentions commits that were deleted.
These dangling commits are called GitHub Cached Views and can be accessed using a commit SHA-1 such as https://github.com/GitGuardian/ggshield/commit/1e820de77f3ee74a22eb834b6b6efd0c6b8ce4f0, where the following sentence warns you about the issue:
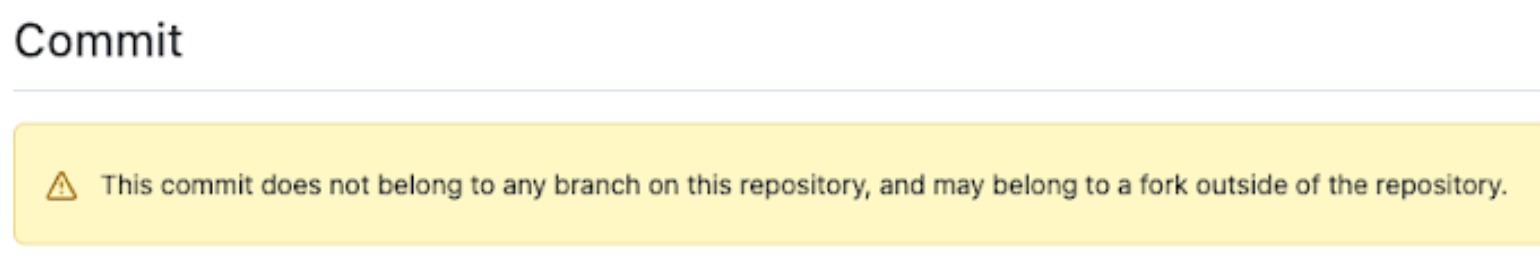
GitHub has documented several ways of accessing a commit after it has been deleted:
- in any fork
- using its hash in a cached view
- via a Pull Request that mentions it
The Hidden Danger
When it comes to secrets, these GitHub Cached Views are problematic because they remain publicly available while you believe they were not. Attackers don't even need to know the full hash of the commit. They can access GitHub Cached Views using the first four characters of the hash which makes it possible to enumerate all of the 65536 combinations, in about half a day per repository.
GitHub Cached Views are therefore dangerous blind spots for organizations as they expose commits supposedly deleted. Again, this emphasizes that once a secret has been leaked, it must be revoked. GitGuardian keeps track of all secrets including in GitHub Cached Views, and can help companies identify these blind spots.
Earlier this year, GitGuardian coined the term “zombie leaks” to refer to secrets being exposed—knowingly or not— but never revoked, representing a potential attack vector. GitHub Cached Views are a new materialization of this threat.
Hard-coded secrets are more of a threat than ever. They should be discovered timely, whether in public or private repositories. If you are concerned about private repositories that have recently been made public, contact us. We will scan your repositories for secrets and help you remediate efficiently.
GitGuardian Public Monitoring has your back, and will detect secrets leaked in public commits. We love and support open-source developers and our Good Samaritan Program will send you an email if you ever leak a secret on public GitHub.
Interested in checking your public secrets exposure?




![Shai-Hulud 2.0 Exposes Over 33,000 Unique Secrets [Updated Nov, 27]](/content/images/size/w600/2025/11/shai-hulud--2--1.png)



