With more than 350 individual detectors, GitGuardian’s library ensures extensive coverage of the types of secrets that could find their way to your source code.
It all started with specific detectors for clearly identifiable patterns, prefixed ones like AWS keys (AK_IAIOSFODNN7EXAMPLE) or found within a very specific context like MongoDB database connection URLs. Such detectors offer high recall and high precision, meaning that they will catch all specific patterns with almost zero false positives.
But what about the other half of secrets? We went further and built detectors for more generic, random-looking strings, ones not associated with any particular service. Think contextless passwords, combinations of username/password pairs for internal components, or simply basic auth strings and JWT tokens.
Completing the puzzle with custom patterns
In hindsight, generic detection was a very successful bet. Our dozen generic detectors are now responsible for raising about 40% of overall secrets exposure alerts. But we knew we weren’t done yet.
Thousands of organizations and developers from all over the world kept flocking in to try GitGuardian’s secrets detection engine, scanning all their Git repositories and adding real-time monitoring to every code commit.
Demand for new detectors was always high to keep up with and the need for catching proprietary secrets used by internal services emerged. To increase our coverage, we decided to let users extend GitGuardian’s secrets detection engine and configure their custom patterns to scan for.
Starting today, custom detectors are in public beta and can be requested by users with a Manager role for workspaces under our Business plan, or currently in Business trial.
Bring Your Own Detector to GitGuardian
Follow the steps below to create custom detectors in GitGuardian Internal Monitoring.
-
Navigate to
Settings > Secrets Detection -
In the navigation bar, click
Table of Detectors(or scroll down until you get there) -
Click
Add a custom detector, a modal will open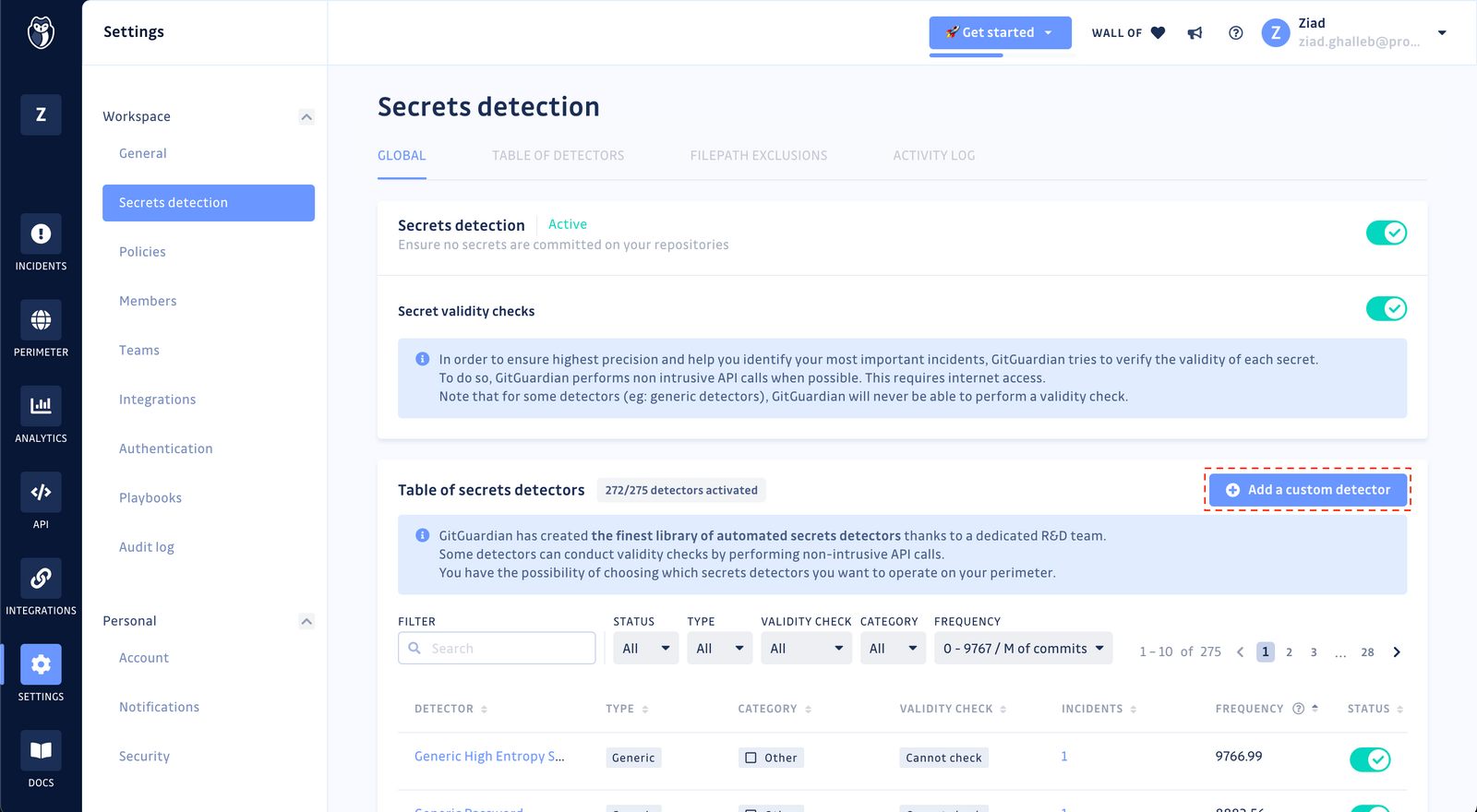
-
Enter the details for your new custom detector:
- You must at least provide the name for your detector, and a set of examples for the format of your internal secret pattern.
- If you have the regular expression for the desired pattern, please provide it.
- You can provide additional information on the pattern, surrounding content, or additional match requirements for the secret format you're after.
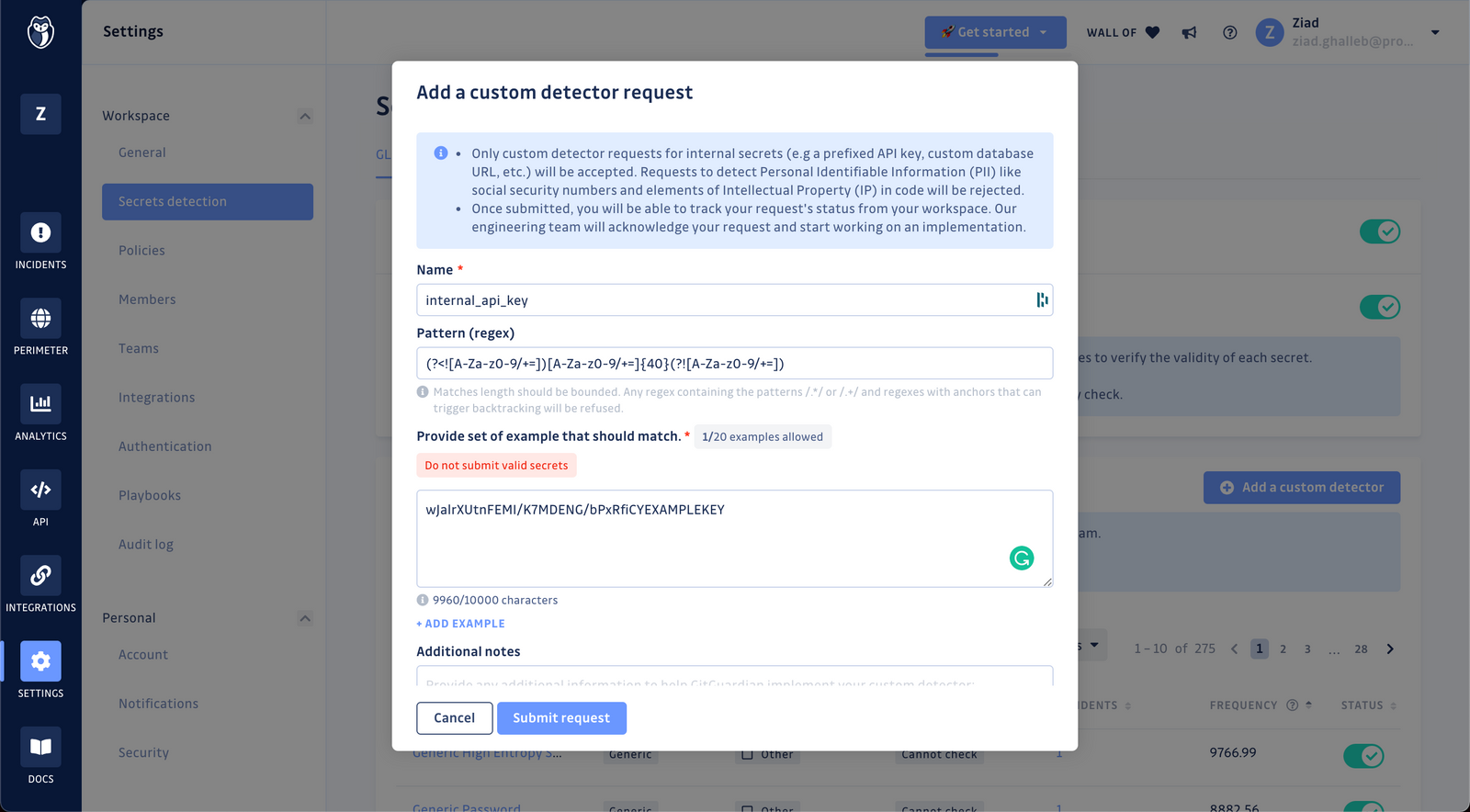
Once submitted, you will be able to track your custom secret detector request. Our engineering team will acknowledge the request and get in touch with you to validate the regular expression. Due to the nature of regular expressions and the potential for high volumes of alerts, we must review the results returned by your custom pattern to ensure precise and high fidelity alerts before deploying it to your workspace.
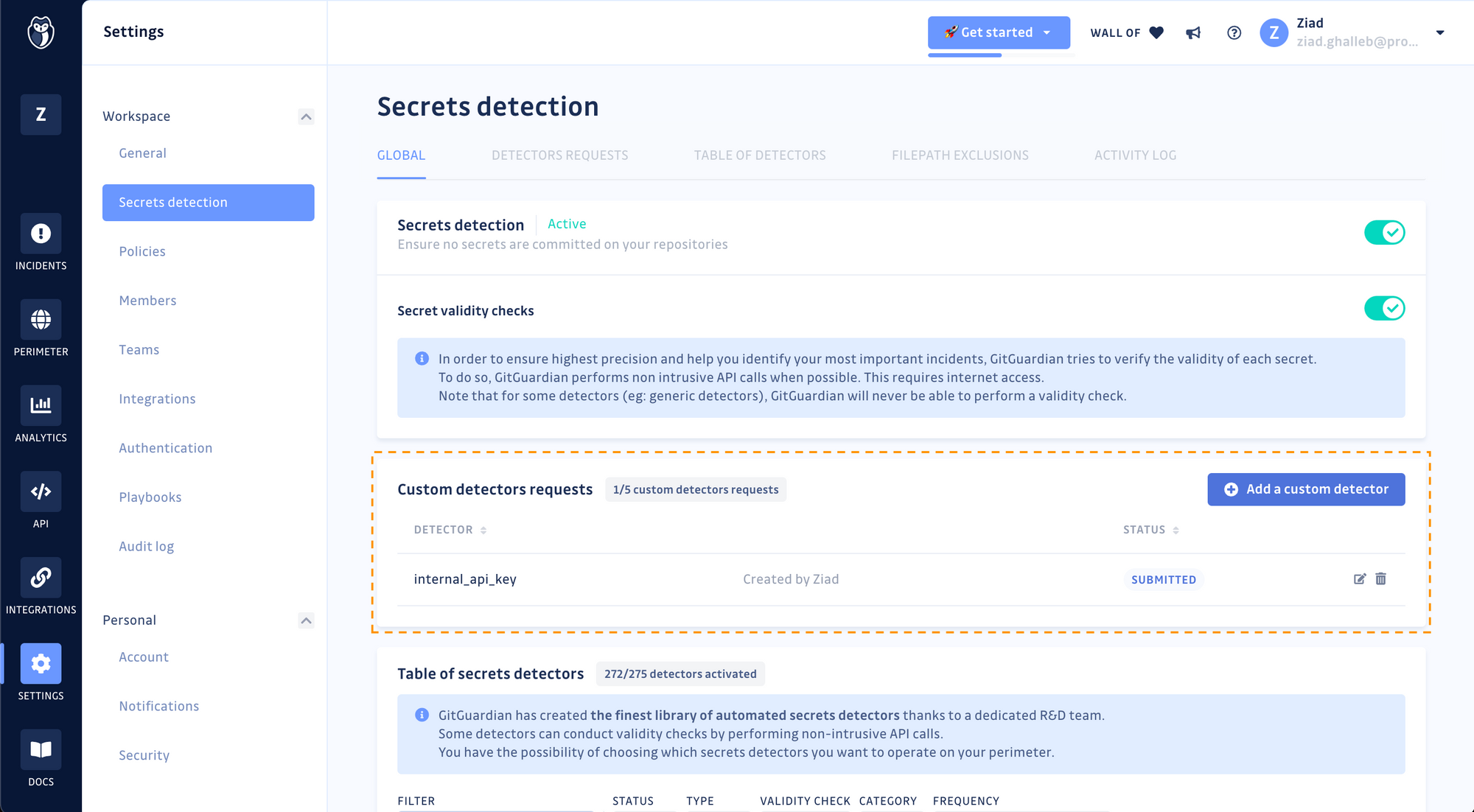
Extending GitGuardian’s engine was designed to help you detect secrets specific to your organization (e.g internal API tokens), all requests for detecting patterns like Personal Identifiable Information (PII) or Protected Health Information (PHI) will be rejected during the public beta.
For more information on this release, please consult available documentation or reach out to me at ziad.ghalleb@gitguardian.com.