In the Detector of the Month series, we will be featuring our favorite projects or services our secrets detection engine supports–and for this second installment, we chose Okta, the identity provider for the internet!
Okta, the one-stop-shop for all your auth needs
What does Okta do? Looking at Okta’s platform and its 11 products, it’s a tough question! Okta is an Identity and Access Management (IAM) platform. It provides comprehensive solutions for organizations to handle user authentication and management for their workforce or their customers and end-users, API authentication and authorization, server access, identity for on-prem and hybrid cloud applications, and much more.
Okta’s promise for organizations is painless authentication and authorization, it helps their developers quickly set up and deploy auth that protects apps, APIs, and infrastructure. Organizations can build what matters to their core business and leave the tough challenges around identity and security requirements for Okta to take care of.
If you’re looking for a quick way to set up auth for your next project, give it a try here. Okta’s Developer Edition is free with no time limit for apps with 100 MAUs or less!
GitGuardian keeps Okta API tokens and secrets out of your code!
At GitGuardian, we aim to help every developer solve the problem of secrets-in-code. To get there, we’re regularly growing our library of built-in specific and generic detectors, covering as many types of secrets as there are.
Identity and access management is ultimately a security product, Okta helps developers build the foundation for secure connections between people and the technologies they use. This foundation itself can be compromised at the source, that is the software development lifecycle – from developer workstations to artifact registries via CI pipelines, and become an easy target for attackers. With GitGuardian’s specific detectors, developers are alerted if the following Okta credentials are exposed:
How to handle Okta secrets-in-code incidents
If you receive an alert from GitGuardian mentioning a leaked Okta API token or client secret, follow the steps below:
-
Understand the implications of the incident. A bad situation can be made worse if a secret is revoked without understanding how it is currently being used, what services it gives access to, the privileges it has.
-
Rotate and revoke the secret!
- If it’s an Okta API token
Go to your Okta dashboard. Under the Security > API section, you will find a list of all your API keys, create a new token first to replace all occurrences of the compromised one in your source code. Revoke the exposed token.
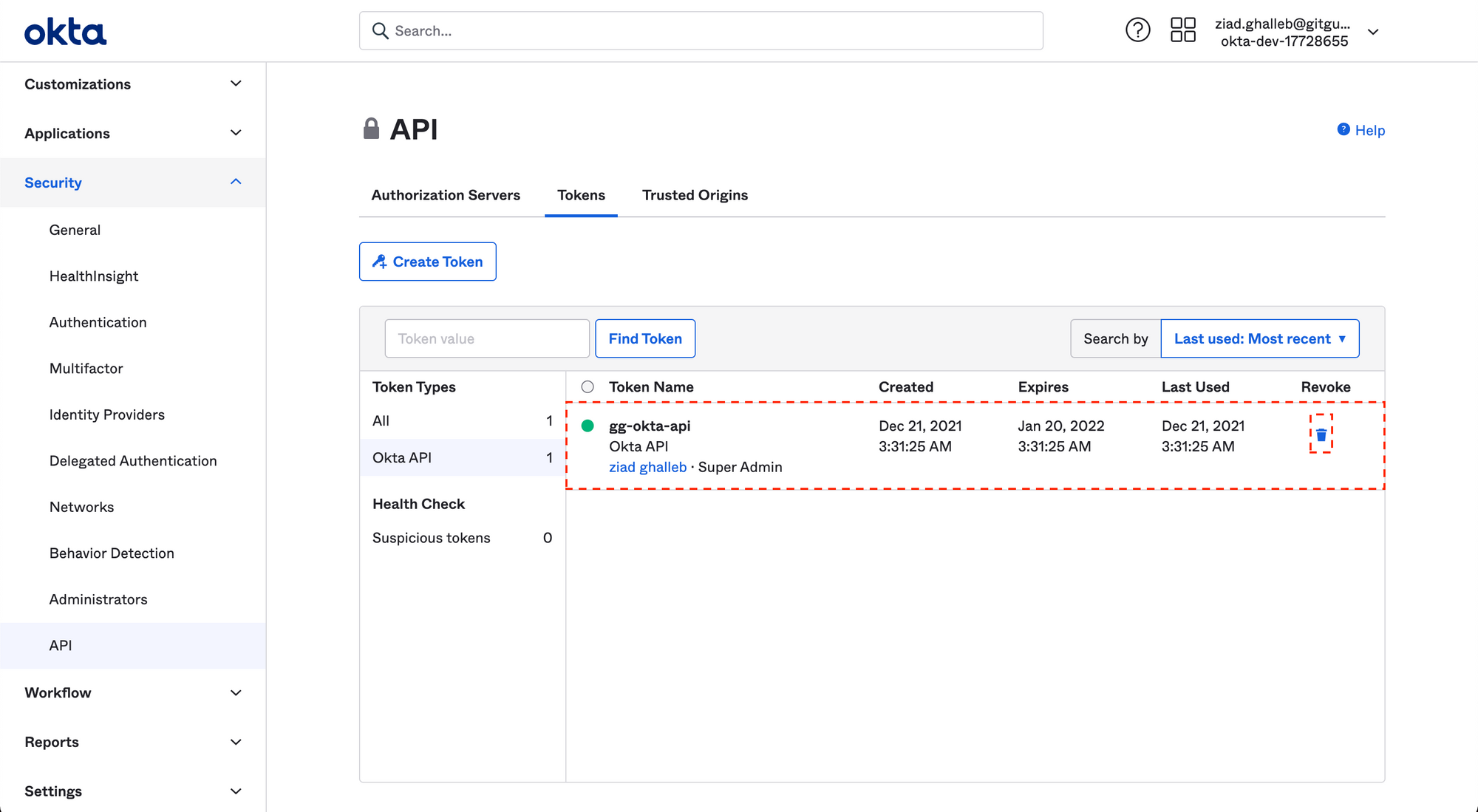
To learn more about Okta's Core API, please visit the developer docs.
- If it’s an Okta client secret used in web applications (server-side)
Go to your Okta dashboard. Under the Applications section, you will find a list of all your apps. Select the affected app then generate a new client secret to replace all occurrences of the compromised one in your source code.
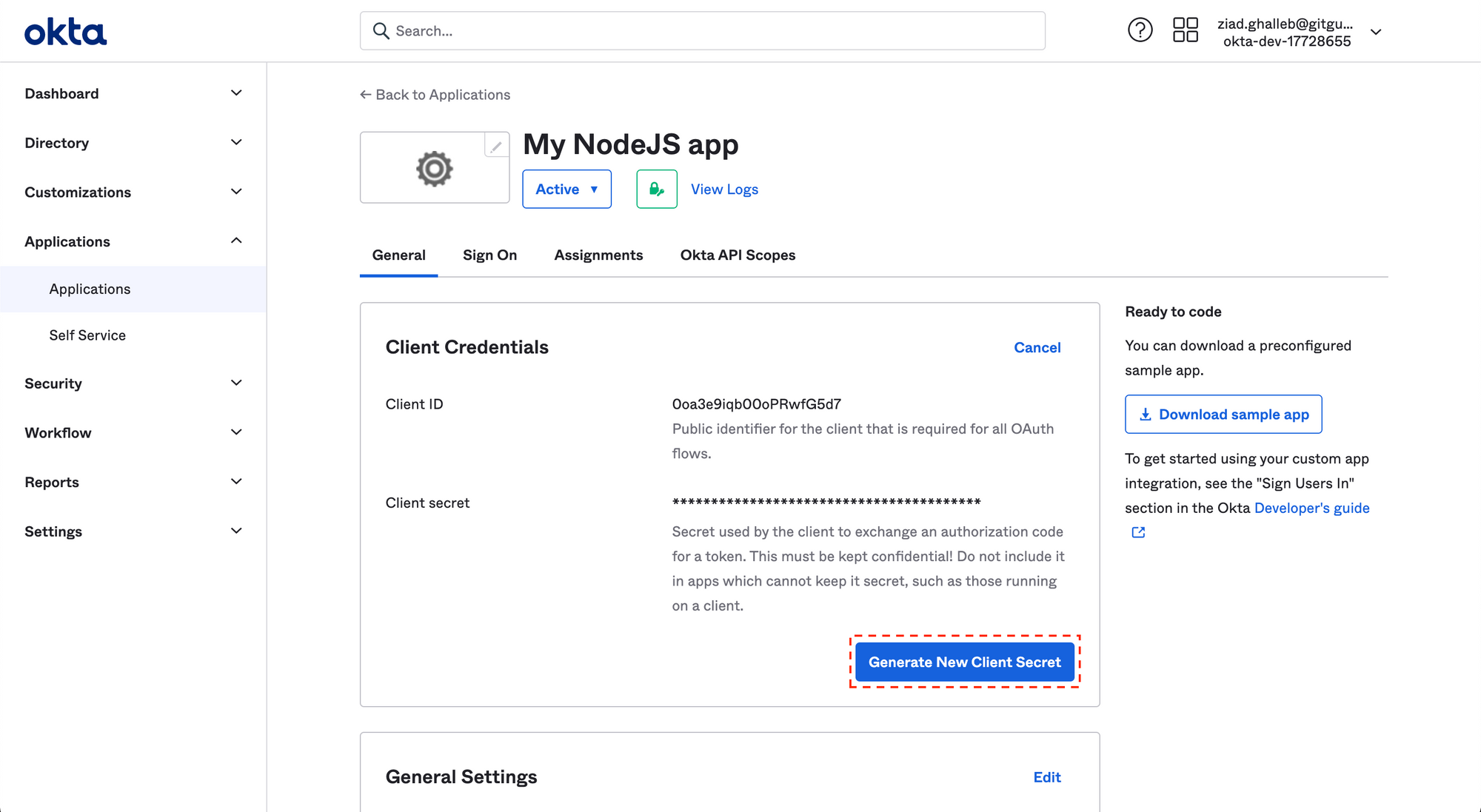
To learn more about Okta client secrets, please visit the developer docs.
- If it’s an Okta API token
-
Manage your secrets properly. Use a dotenv file or look for alternative Secrets Management solutions to avoid hardcoding credentials in the future.
-
Optional – Remove all evidence from your git history. Rewrite the git history or delete the entire repository. ⚠️ Such operations are not trivial and need to be discussed with your other team members if you have any.
-
Review access logs. Check for suspicious activity in the log data of your services impacted by the secret.
What about other secrets?
GitGuardian helps developers keep 300+ types of secrets out of source code. Our automated secrets detection and remediation solution secures every step of the development life cycle, helping you monitor your code for sensitive data:
- On developer workstations with Git hooks (pre-commit and post-commit);
- On Git repositories hosting platforms (GitHub, GitLab, and Bitbucket);
- In CI pipelines (Circle CI, Travis CI, Jenkins CI, GitHub Actions, and much more);
- In Docker images.