In the words of Sun Tzu, the ancient Chinese military strategist, 'If you know the enemy and know yourself, you need not fear the result of a hundred battles'. In the realm of cybersecurity too, where each technological advancement unveils new vulnerabilities, understanding both the enemy and yourself becomes crucial for effective defense.
Each technological advancement opens a door, leaving behind an "attack surface" that cunning adversaries exploit to breach defenses. In this world of cyber threats, external Attack Surface Management (EASM) has emerged as a vital pillar of modern cybersecurity. Many market developments, like Google's $5.4B acquisition of Mandiant, underscore the growing significance of EASM in cybersecurity practices.
Respected industry analysts, including Gartner, Forrester, and KuppingerCole, have all outlined the rapidly expanding EASM, dubbing it a top concern for security teams across industries.
Are you fully aware of your external attack surface?
There are several core components to consider.
- First, asset discovery and inventory management should lay the groundwork, enabling you to identify and catalog all your internet-facing assets, like websites, applications, and servers.
- Once identified, vulnerability risk management becomes paramount; regular vulnerability scans to uncover weaknesses, monitoring emerging threats, and keeping your assets updated with the latest patches and configurations are essential.
- From there, it's a strategic dance, assessing web applications and network security, securing against external threats to your cloud infrastructure, and preparing for swift incident response.
Together, these measures can strengthen your defense, ensuring you stay one step ahead of the relentless adversaries lurking in the shadows.
Cyber attackers exploit vulnerabilities to infiltrate systems and sow chaos. That’s why understanding your entire attack surface mapping is paramount. It's not just about exposed assets; externally exposed information is equally vulnerable.
When in the hands of malicious actors, this information becomes a weapon to penetrate your defenses. They can move laterally by gaining access, compromising critical services, and inflicting substantial financial and reputational damage. With this in mind, comprehending all the assets and information exposed to potential attackers is the linchpin of your security strategy.
That’s why you need a strategic plan to uncover your organization's entire attack surface, enabling you to address vulnerabilities head-on and reduce attack surface. By identifying every weak point and taking proactive measures to fortify your assets and safeguard sensitive information, you can significantly reduce the overall risk of a successful cyber attack.
Should public GitHub monitoring be in your External Attack Surface Management strategy?
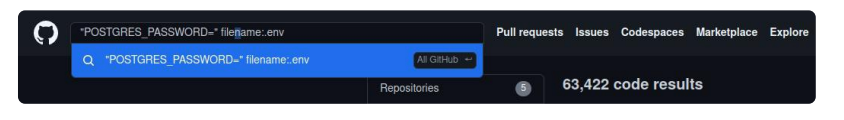
We did a GitHub search, scanning a number of repositories, and were alarmed to find more than 1000 results related to PostgreSQL credentials. Secrets found in public GitHub repositories are readily available to anyone on the internet. Yet, monitoring public repositories remains largely overlooked in today's external attack surface scanners.
A real-world example of a data breach due to publicly exposed secrets:
Toyota Data Breach - October 7, 2022
A contractor exposed a credential giving access to user data on GitHub for five years.
Sensitive information is at risk on public GitHub
Developers utilize GitHub to collaborate and share code, which turns it into a significant attack surface. Accidentally committing API keys, OAuth tokens, and passwords to public repositories opens the door for exploitation. Remember - hackers scour your code for secrets, leaving your systems vulnerable.
T-E-N Million! (you read that right!) We have observed that secrets sprawl has been accelerating yearly since 2020. Hard-coded secrets have surged by 67% compared to the previous year, with the volume of scanned commits rising by 20%. Download this report for comprehensive stats and insights on secrets sprawl.
You need to protect your sensitive information from falling into the wrong hands. There are various scenarios where sensitive information can be exposed, such as code pushed to the wrong branch or misconfigured tools. Even if your developer or subcontractor realizes and deletes a secret from the current code version, cybercriminals can still exploit historical commits to extract sensitive information that was previously committed and deleted.
GitHub is a breeding ground for security vulnerabilities
GitHub is a goldmine of open-source code, but it's also a potential breeding ground for security vulnerabilities. Hackers can easily search public repositories for code that contains known vulnerabilities or outdated dependencies, making it crucial to manage your attack surface on public GitHub. You need to follow best practices for securing your code, regularly auditing your code for potential security vulnerabilities, and using secure storage solutions for secrets.

There are risks of non-compliance
Depending on your organization or project type, regulatory requirements may govern how data is handled and stored. Managing the attack surface on public GitHub is crucial for compliance with these regulations, as it can help ensure that sensitive data is not accidentally exposed in public repositories.
Secrets exposure can damage the reputation of MSPs
Hardcoded secrets are copied and shared across environments with little to no control, and they pose a major threat to companies. Protecting customer data is crucial for Managed Service Providers (MSPs), as secrets exposure can significantly damage their reputation. Safeguarding sensitive customer information is not only a responsibility but also an opportunity to establish trust and build long-lasting relationships. Public GitHub repositories can be a reflection of your organization's reputation and brand. By taking proactive steps to audit your customers' perimeter on public GitHub, you can ensure that your customer data remains secure and your reputation remains intact.
How to protect your secrets on public GitHub?
Secrets are like the crown jewels of your company. But how do you protect them from accidentally leaking onto GitHub's public space?
Educate Developers
Educate your developers on best practices for securing code and managing secrets, including training on secure coding practices and regular code auditing for potential security vulnerabilities. Developers can protect sensitive information in Git repositories by creating a ".gitignore" file to exclude files or directories, such as API keys, passwords, and configuration files, from being committed to the repository.
Implement Tight Access Control
Limit repository access to authorized personnel only, assigning permissions to specific users or teams. Two-factor authentication adds an extra layer of security to ensure that only authorized individuals can access the repository.
Use Encryption, Secrets Management, Code Reviews
Encrypting data at rest and in transit, and utilizing tools like HashiCorp Vault, AWS Secrets Manager, or Doppler for secure storage and access control, adds a layer of protection. These tools enable dynamic secrets that auto-rotate, giving you greater control over who can access your secrets. They also offer access logs, allowing you to track who has accessed your secrets and when. Leveraging third-party tools for code reviews can also help identify code containing secrets.
Audit your perimeter on Public GitHub
Even if you've taken the above steps to secure your GitHub public space, that's still insufficient. You need to enforce automated secrets detection and secrets management systems like Hashicorp Vault or Doppler to stay ahead of malicious actors who might be targeting your organization.
But the sheer volume of commits on public GitHub can be overwhelming. How can you filter through the noise to understand the anatomy of your attack surface and possibly keep track of everything important?
Enter GitGuardian Public Monitoring.
It is dedicated to protecting your company's official open-source repositories and the personal repositories of your entrusted developers and subcontractors. With a focus on monitoring, detecting, remediating, and threat hunting, GitGuardian maps your attack surface, monitors developers' public activity, rapidly alerts you when a secret is committed, and layers context onto the alerts for prioritization. Our automated secrets detectors can identify over 350 types of secrets, filtering out false positives with built-in validity checks.
GitGuardian also offers keyword monitoring capabilities to enhance security. Two types of incidents can be triggered based on keywords: secret graspers and incident raisers. Secret graspers allow defining specific keywords related to your company to identify exposed secrets. Incident raisers, on the other hand, raise alerts when specific keywords are found on public GitHub, regardless of secret presence.
Our Explore feature empowers you to conduct offensive security searches on GitHub. With access to a vast repository of files spanning years of history, you can discover unsanctioned sensitive data, schedule regular queries, and run the secrets detection engine on the results. You can gain valuable insights and metrics through our analytics dashboards, empowering you to combat secret sprawl effectively.
By adopting a multi-faceted approach to protecting secrets on public GitHub, you can ensure the confidentiality of your sensitive information, minimize risks, and maintain a robust security posture.
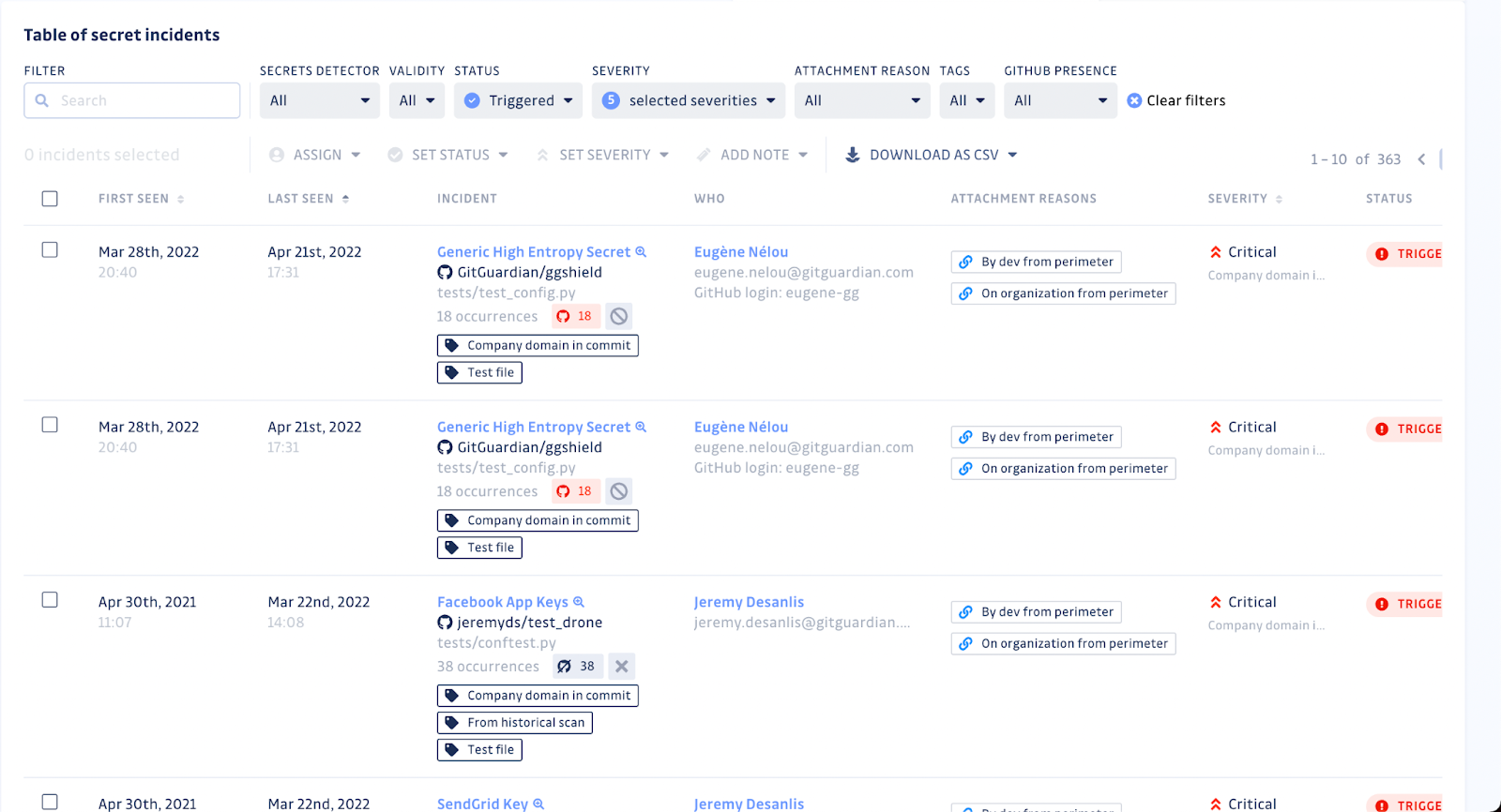
We have monitored GitHub for three years and can offer personalized data from your company's perimeter. The data is aggregated to remove sensitive content and allows you to assess whether our solution is worth evaluating. Every company that requests the report gains new knowledge about its GitHub attack surface.

Do you have any questions or want to discuss more about our product? Book a 1:1 discussion with us.
Know your attack surface and the enemy
Implementing the steps above can significantly mitigate the risk of sensitive information accidentally finding its way into GitHub's public repositories. It's essential to recognize that any discussion on the cyber attack surface management must encompass the vast realm of secrets on public GitHub. Without addressing this critical aspect, blind spots may persist, leaving your organization vulnerable to potential breaches. So next time, when presented with an "external attack surface report," take a moment to reflect and inquire whether public GitHub was included in the assessment.
As GitGuardian grows, its impact reverberates globally, reaching over 300,000 developers, including over 100 Fortune 500 companies. In the realm of GitHub Attack Surface Management, no other solution can match the breadth and continuous proactive coverage offered by GitGuardian.
But understanding one’s attack surface is only half the battle. To truly achieve resilience, it is essential to know the enemy. This is where Honeytoken comes into play, acting as a beacon, attracting potential adversaries and exposing their intentions. By strategically deploying our honeytokens across your software delivery pipeline, you can gain a unique vantage point into the minds of malicious actors, detecting and thwarting their attempts before they can inflict damage on your software supply chain, which is inseparable from third-party vendors today.
The convergence of GitGuardian Public Monitoring and GitGuardian Honeytoken represents a potent combination—a comprehensive understanding of one’s GitHub attack surface and the ability to anticipate the enemy's moves.
So, as you embark on your journey of securing your digital assets, remember the words of Sun Tzu, echoing through the ages: "If you know the enemy and know yourself, you need not fear the result of a hundred battles." With GitGuardian by your side, armed with Public Monitoring and Honeytoken, you stand poised to defend, protect, and prevail.