Today, after months of hard work and discovery with security teams, we are excited to launch the new Honeytoken module to protect your software supply chain against attackers targeting Source Control Management (SCM) systems, Continuous Integration, Continuous Deployment (CI/CD) pipelines, and software artifact registries...
With Honeytoken, we are expanding our platform's capabilities to help you detect and limit the impact of data breaches and code leaks in your DevOps environments.
What are honeytokens, and why should you use them?
Reduce breach detection time 🕰️
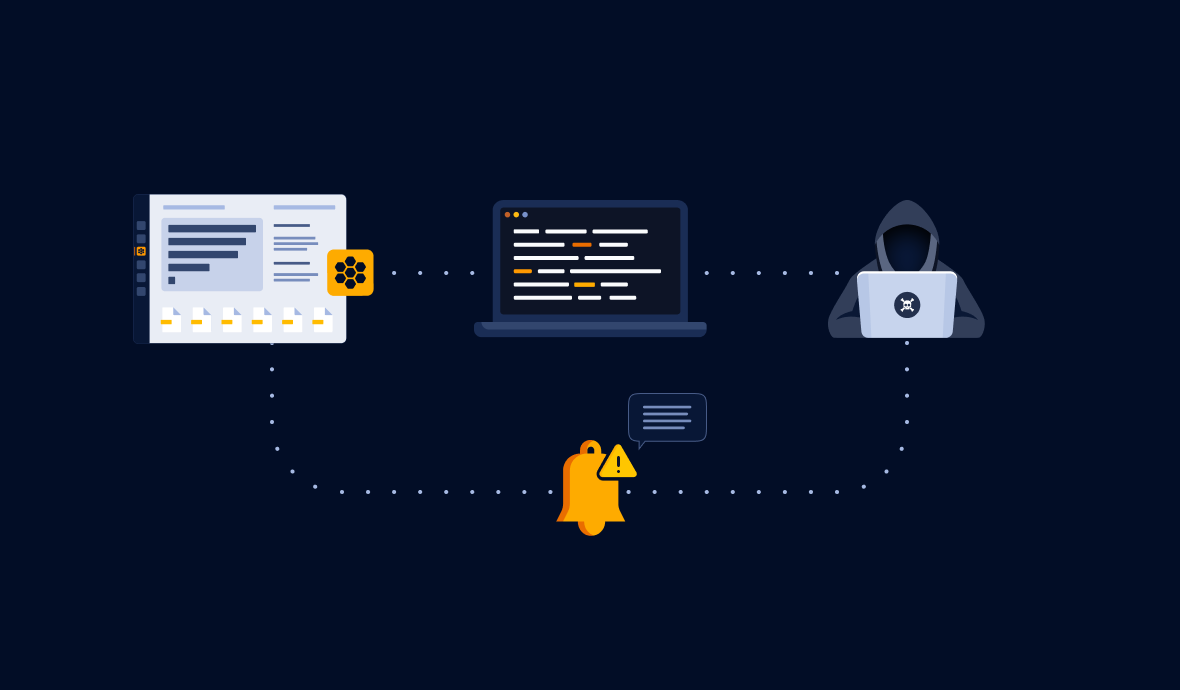
Imagine yourself as a mischievous attacker trying to gain unauthorized access to a company's system. You're searching through their code repositories, third-party apps, and cloud infrastructure when suddenly, you strike gold! You find some AWS secret keys in the code, waiting for you to snatch them up.
Feeling like you've hit the jackpot, you eagerly try to use one of the keys to gain entry to the system. But when you try to use it, you're promptly booted from the system.
What do you think just happened?
What happened was that you had fallen right into the honeytrap. Those weren't real AWS keys you found, but GitGuardian honeytokens designed to be deceptive and catch you in the act!
Since these honeytokens are not real, legitimate workers would never use them, so any attempt to access a resource using the honeytoken is a strong indication of a security breach in your environment.
Strengthen supply chain security 🔐
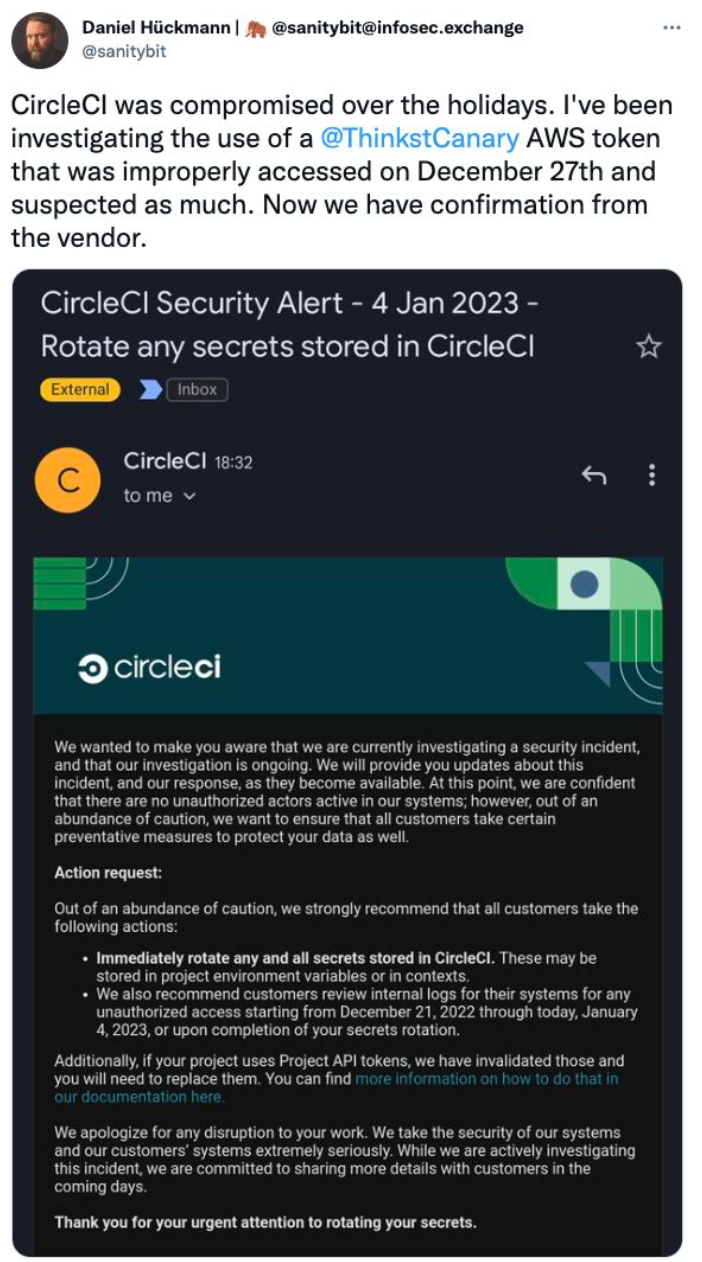
Do you remember when a security engineer, Daniel Hückmann, was alerted to an intrusion in his CircleCI account thanks to an AWS Canarytoken that he had planted? The decoy AWS key was triggered by the attacker, and Daniel was promptly notified via email, allowing him to take swift action and mitigate the risk.
We know from many other recent security breaches like Okta etc, that attackers are constantly looking for valid hardcoded credentials to gain access to various parts of software supply chains.
Nearly 50% of all breaches not otherwise due to user error or misuse make use of credentials, according to Verizon's "2022 Data Breach Investigations Report" (DBIR).
They then use these credentials for lateral movement within the network. As such, companies have various measures to fortify their defenses, including implementing SCM governance, IAM best practices, cloud security posture hardening, secrets scanning, and implementing frameworks like SLSA or NIST SP 800-161. However, even with all these measures in place, there is still a risk of getting breached. It's not just about implementing the right controls but also staying vigilant. Attackers are becoming more sophisticated by the day, and every SaaS vendor is a risk. As the saying goes, "It's not a matter of if, but when."
As a leading expert in code security and secrets detection, we understand that if attackers manage to penetrate your code or CI, they can leverage your secrets to gain access to even more valuable resources. Therefore, we think it is crucial to safeguard your code and software supply chain, as they are prime targets for attackers.
With our new Honeytoken capabilities in your security arsenal, you can intentionally disclose decoy secrets by placing them not only in your own tools but also in your SaaS vendor's systems to identify if a vendor in the supply chain has been compromised. In a world where third-party and supply chain threats are rampant, Honeytoken is a powerful capability that provides highly sensitive and early intrusion detection in your supply chain without the need to develop an entire deception system.
Our goal in building Honeytoken was to make it the easiest solution for your security and SOC teams to create and manage honeytokens on a large enterprise scale. This way, you, too, can play detective and proactively protect your systems against attacks.
But that's not all.
Swiftly identify public exposures of your code 🔍
Wouldn't you want to be notified immediately if your code is found on public GitHub? Leaked secrets can lead to unauthorized access and data breaches and spell disaster for you and your company.
At GitGuardian, we understand that code repositories and build systems are highly sought-after targets for attackers. We take pride in our real-time monitoring of public GitHub activity to detect and alert developers of any leaked secrets at no cost. With the addition of our Honeytoken capability, you can now take an extra step to safeguard your code and software supply chain.
GitGuardian Honeytoken is designed to detect immediately if a specific honeytoken you placed in your code appears in a public GitHub repository. When that honeytoken is triggered, if we recognize the source IP as one from GitGuardian’s infrastructure, it indicates that your code has been leaked on the public GitHub. We will trigger an event and notify you immediately. One of the key benefits of GitGuardian Honeytoken is its ability to create recognizable events that tag this honeytoken as "Publicly Exposed." This means you can quickly identify which honeytoken and repository have been exposed, enabling you to kick off the appropriate incident response to protect your sensitive data.
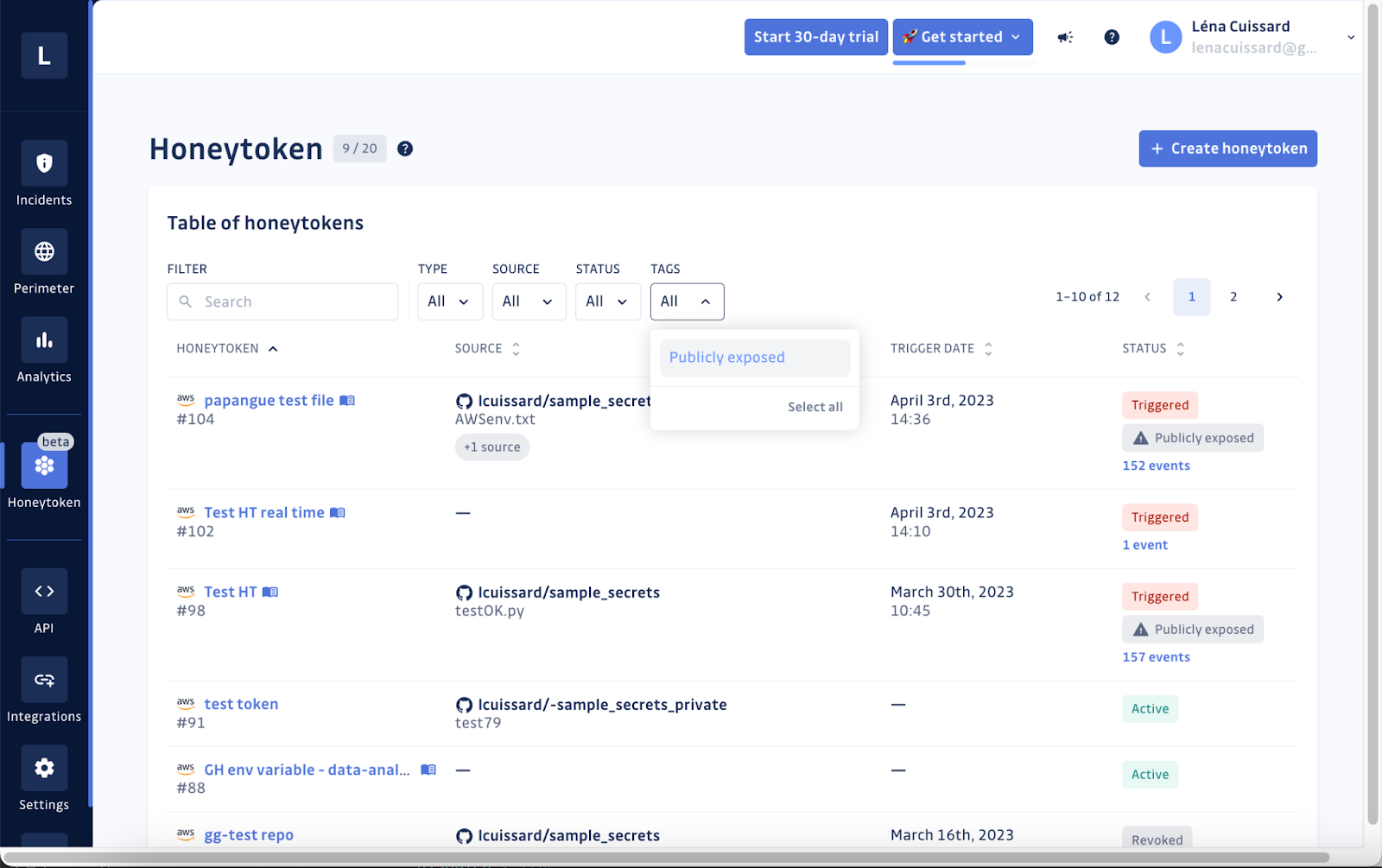
How does GitGuardian Honeytoken work?
Honeytokens can be created and managed entirely through the GitGuardian dashboard. We manage the whole provisioning and alerting infrastructure, so you can focus on creating your protective net. Follow the guide to get started creating your first honeytoken!
Don't wait for your secrets to be discovered - turn the tables on attackers with Honeytoken
We are on a mission to revolutionize code security for the DevOps generation, and Honeytoken is a testament to that. With the GitGuardian platform, we have already helped thousands of organizations reduce risks in the software development lifecycle. Now, Honeytoken and Secrets Detection will work synergistically to improve the security of your SDLC.
By continuously detecting and remediating exposed secrets with GitGuardian, organizations can significantly reduce their attack surface. And with the added power of Honeytoken, organizations can proactively detect intrusion in real-time and be alerted against even the most sophisticated attacks. We want to empower defenders like you by bringing deception technology to the SDLC space and ensure you always stay one step ahead of attackers with enhanced visibility and control over your SDLC system.
Honeytoken will be activated manually for specific workspaces, so if you have any questions about this new capability, please schedule a live demo or reach out to your GitGuardian contact. GitGuardian users can get 5 free honeytokens to try out this latest offering!
For more information, check out our documentation or watch this brief video.
To get real-time alerts on supply chain breaches in your favorite SaaS tools, check out SaaS Sentinel, our latest innovation powered by Honeytoken technology!