Picture this: You're a hacker, thinking you've hit the jackpot with some stolen AWS credentials. But surprise! It's a trap sweeter than your grandma's apple pie. That's right, you've just licked a honeytoken, and now you're caught like a fly in digital honey.
Want to see this sticky situation illustrated? Check out our latest comic strip! It's got more layers than a honey baklava, and it's just as sweet. Don't forget to subscribe for more security treats that'll make your funny bone tingle and your firewalls stronger!
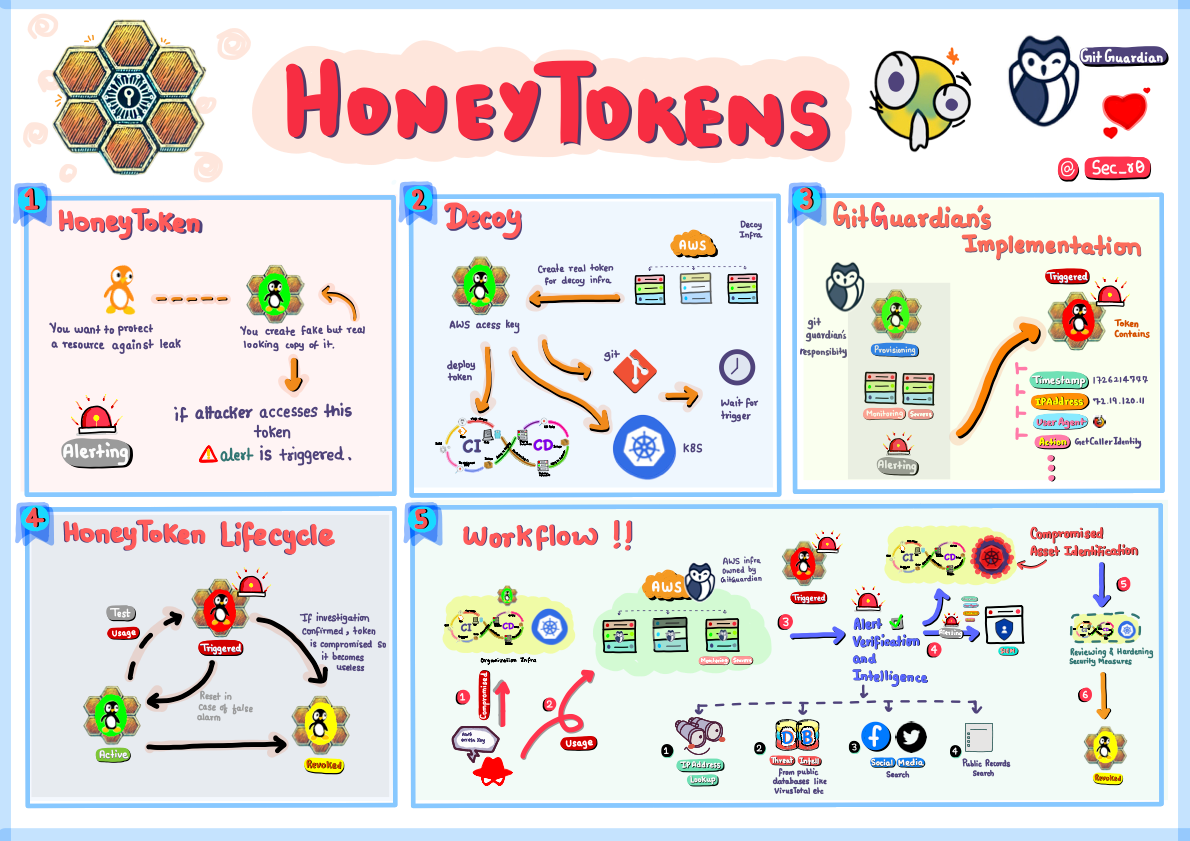
Zine summary:
- Honeytoken are delicious-looking decoy credentials you deploy in your git repos, CI/CD, and K8s infra etc... to detect a breach. In the world of cybersecurity, sometimes it pays to be a little honeytrap!
- These clever little decoys don't just catch bad guys; they're like the CSI of the cloud world. When triggered, they spill the beans faster than your office gossip, giving defenders the attacker's IP address, user agent, timestamp, and even the AWS action they tried to pull off. It's like getting the hacker's entire life story in one fell swoop!
- Defenders can then go all Sherlock Holmes, using this info to dig deeper. Public databases? Check. Social media stalking? You bet. It's like playing "Guess Who?" but with cybercriminals!
- But here's the kicker - honeytokens are the ultimate shapeshifters. False alarm? No problem! Just reset and redeploy. Real threat? Poof! That token becomes as useless as a chocolate teapot.


![Honeytokens [Security Zines]](/content/images/size/w2000/2024/09/Honeytokens.png)
![Precision & Recall [Security Zines]](/content/images/size/w600/2024/10/Recall-in-Detection.png)
![Software Composition Analysis [Security Zines]](/content/images/size/w600/2024/05/SOPS-Security-Zine--1-.png)
![SOPS [Security Zines]](/content/images/size/w600/2024/03/SOPS-Security-Zine.png)
![Has My Secret Leaked? [Security Zines]](/content/images/size/w600/2024/01/Security-Z.png)
