As organizations race to automate everything from CI/CD pipelines to cloud orchestration, the number of Non-Human Identities (NHIs) has exploded. These identities now outnumber human users 144 to 1, and every one of them depends on a secret to authenticate.
But what happens when these secrets outlive their usefulness?
Improper Offboarding isn’t just an operational hygiene issue. It’s a growing security and compliance liability, now formally recognized as the #1 risk in OWASP’s Top 10 NHI for 2025. It refers to the failure to fully remove NHIs and their credentials when they’re no longer needed, such as after a project ends, an app is deprecated, or a DevOps engineer leaves.
GitGuardian and Delinea have partnered to combat this silent, yet dangerous issue by providing automated lifecycle management, from discovery through decommissioning, with full visibility and control.
The dangers of improper offboarding
When human employees leave a company, their access is typically revoked through integrated offboarding workflows. NHIs, however, are rarely tied to identity platforms like Okta or Azure AD. Instead, here’s what makes them so risky and creates a growing problem:
1. Secrets that live forever
A staggering 68% of tokens in GitHub have no expiration date. NHIs are often provisioned without automated expiry, leading to orphaned credentials that stay valid for years.
2. No clear ownership
Many NHIs don’t have a named human owner. That makes offboarding impossible during employee transitions or post-project cleanup. It also creates serious audit and compliance gaps.
3. Manual and inconsistent processes
Nearly 40% of companies report that revoking API keys or offboarding NHIs takes weeks or more. With no automation and no single source of truth, offboarding becomes inconsistent and error-prone.
These ghost credentials increase blast radius, enable lateral movement, and create blind spots in incident response.
How to address this issue?
1. Identify stale identities
NHIs are scattered across vaults, CI/CD tools, cloud IAMs, and hardcoded into config files. You can’t offboard what you can’t find. Without a single, comprehensive record of all Non-Human Identities (NHIs) and their associated metadata (e.g., last used date, linked service, owner), it becomes nearly impossible to determine which identities are no longer active, necessary, or have excessive permissions. You simply lack the visibility to spot the orphaned ones amidst the scattered and undocumented credentials.
2. Overcome the fear of breaking production
Many teams are afraid to revoke an NHI credential they don’t fully understand. One NHI might be powering workflows across staging and production. Pull the plug too quickly, and you risk breaking everything.
Security leaders know that visibility without action is insufficient. At the same time, acting blindly, like rotating a credential without understanding where it's used, can break production.
This is exactly why GitGuardian and Delinea partnered: to give organizations the visibility, context, and automation they need to safely offboard NHIs without breaking the business.
We solve this in three key steps
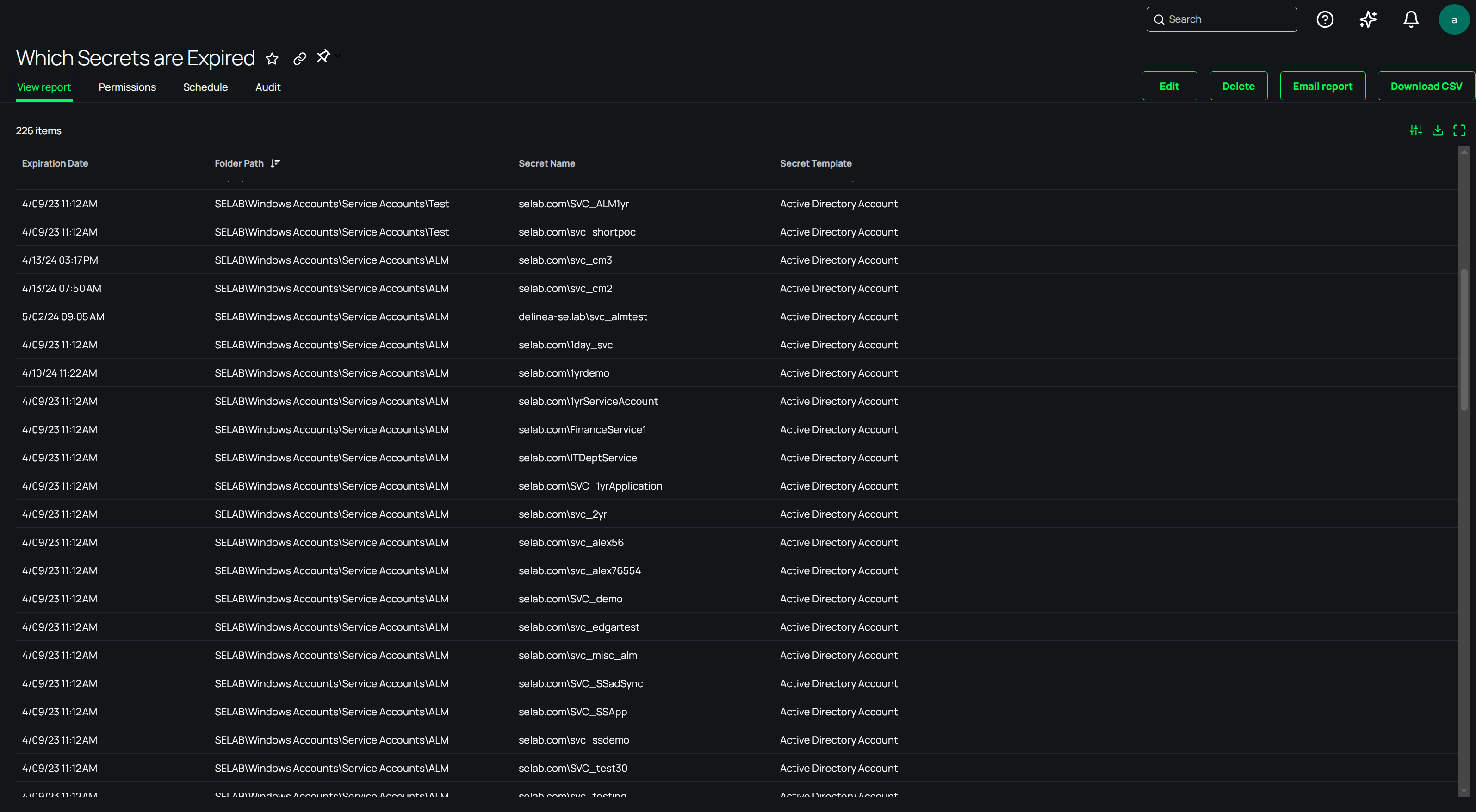
Step 1: GitGuardian detects dormant secrets in Vaults
GitGuardian NHI Governance performs automated discovery across secrets managers, infrastructure, and codebases. When integrated with Secret Server on Delinea Platform, it retrieves rich metadata about each secret, including:
- Creation and rotation timestamps
- Vault path and type of environment
- Associated services or repositories
- Number of times exposed in code or config files
You finally get the insight needed to make informed decisions about what should be off-boarded.
By applying heuristics and signals (e.g., unused + exposed + over-permissioned), GitGuardian flags the secret as high-risk.
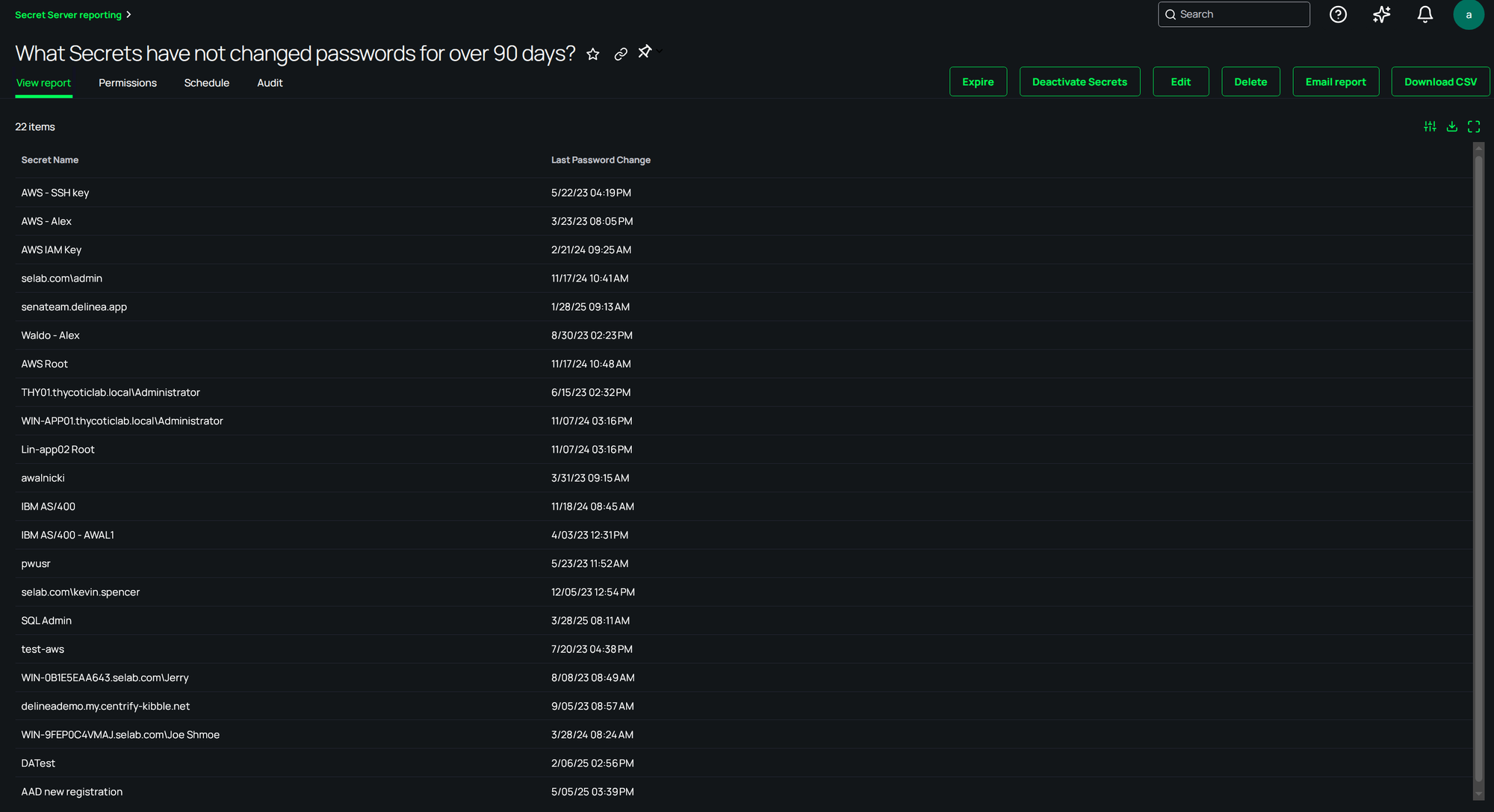
Step 2: Secret Server on Delinea Platform facilitates offboarding workflow
After GitGuardian has flagged the secret as high-risk, Secret Server on Delinea Platform enables users to take remediation actions. Here’s how it works:
Based on the context of GitGuardian’s findings (such as first detected, who’s involved, where it’s used, and remediation recommendations), the IT Admin in Secret Server can make a more informed decision on how to handle this high-risk secret. These could include:
- Rotating the secret
- Disabling or deactivating the secret
- Erasing the secret
- Revoking access to the secret
In the case of a secret rotation, the old credential can be automatically archived in an encrypted audit vault or permanently erased if your compliance rules dictate, ensuring there is no lingering risk.
Secret Server on Delinea Platform has robust audit, reporting, and compliance capabilities. When a secret is disabled or archived, it’s not permanently removed. This ensures the audit trail remains intact. Administrators or authorized users can still view or reactivate the secret as needed. The purpose of disabling versus deleting allows your organization to maintain a full audit history, supporting long-term compliance and traceability.
Depending on the action taken on a particular secret, Secret Server supports automated notifications and reporting to notify relevant stakeholders.
All changes are fully auditable, and built-in RBAC ensures only authorized teams can perform sensitive operations. This end-to-end automation reduces mean time to remediate (MTTR) for stale credentials – eliminating blind spots and ensuring improper offboarding never becomes a compliance risk.
Step 3: Validate and confirm with continuous monitoring
Once the secret is revoked or rotated, GitGuardian confirms the update by:
- Scanning the codebase and CI/CD systems for legacy references
- Alerting developers to fix any hardcoded versions
- Tracking the resolution status in the Secrets Incident timeline
This creates a closed-loop workflow for machine identity offboarding. From detection to revocation to developer fix.
Why this matters
Together, GitGuardian and Delinea solve the hardest part of secrets management: dealing with secrets you’ve forgotten.
By combining discovery, metadata context, and automated remediation, the integration helps teams:
- Prevent improper offboarding
- Reduce lateral movement risk
- Enforce least privilege with confidence
- Shrink the secrets attack surface continuously
Final thoughts
NHI security can’t rely on manual processes or hope anymore. The longer a secret lives without being audited or used, the more likely it is to be exploited.
With GitGuardian and Delinea, you don’t have to guess. You see it. You own it. You fix it.
This goes beyond just meeting OWASP Top 10 compliance. It's about improving security, lowering breach risk, and saving your team time.
Next steps
Ready to eliminate ghost access?
Request a demo with GitGuardian
Learn more about OWASP Top 10 NHIs