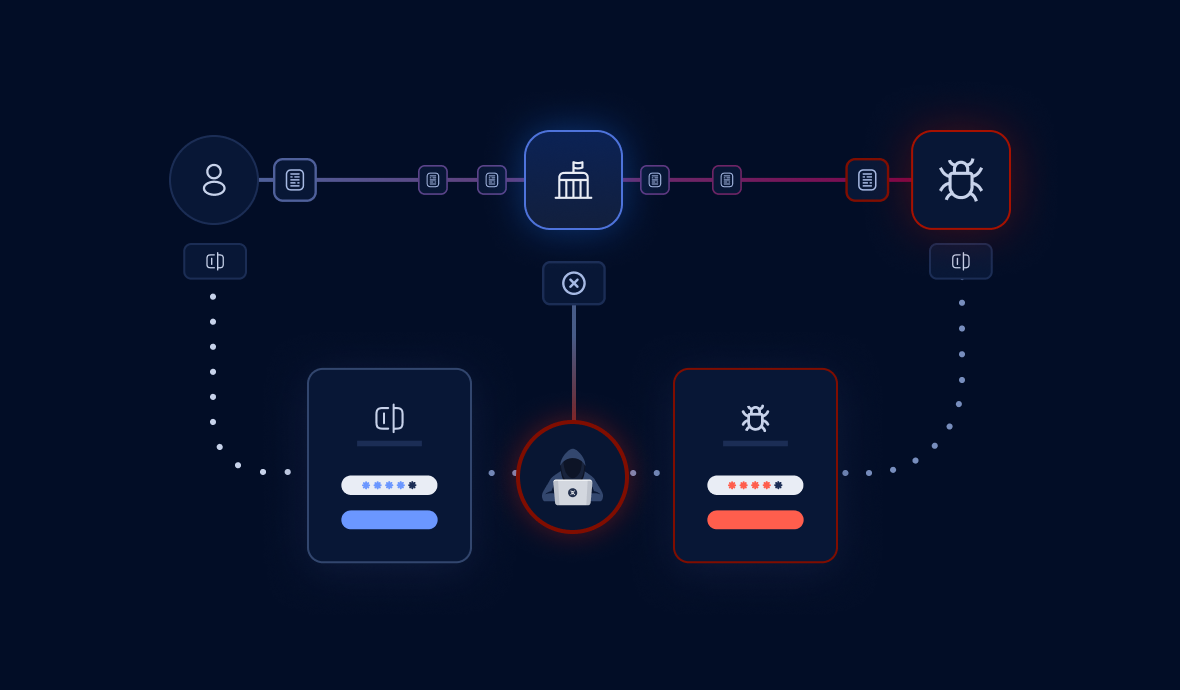
Advanced Malware
The BlackCat ransomware is notorious for being an avid user of stolen credentials. Several researchers have identified that it infects its victims not only by abusing vulnerabilities but also by using credentials that they likely acquire on the dark web. Unfortunately, for the past four years, BlackCat has been constantly evolving and gaining new functionalities. On September 4th, 2024, Morphisec published an analysis of the Cicada3301 that shares some similarities.
This likely new breed of the BlackCat ransomware includes enhanced functions and tools developed to bypass the detection offered by EDRs. In addition, it uses stolen credentials with legitimate tools to pivot within the compromised environment, gaining deeper access to sensitive data and critical infrastructure while encrypting files on the way.
Credentials Stealers
There are many examples of malware dedicated to credential stealing. Their main objective? To gather logins and passwords as close as possible to the users to be sure that they are valid and useful. The Redline and Arkei malware families, among others, target passwords, cookies, and tokens stored in Web Browser. Other families employ various techniques, such as key logging, to intercept credentials as soon as they are used and exfiltrate them immediately to their Command & Control Infrastructures. Depending on the actor, these credentials and the associated personal information are used to carry out new attacks or simply sold on the dark web.
AntiViruses and EDRs can help protect you from these credentials stealers. However, like most security solutions, they are not perfect and could be bypassed by attackers using various techniques to avoid detection. These techniques include making direct system calls, injecting malicious code into legitimate processes, executing malware entirely in memory, or leveraging legitimate tools for malicious purposes.
Early breach indicators could, therefore, be difficult to get. Deployed in web browser password managers, GitGuardian Honeytoken could help you detect such leaks. As soon as the attacker attempts to use it to get access, GitGuardian will notify your security and SoC teams.
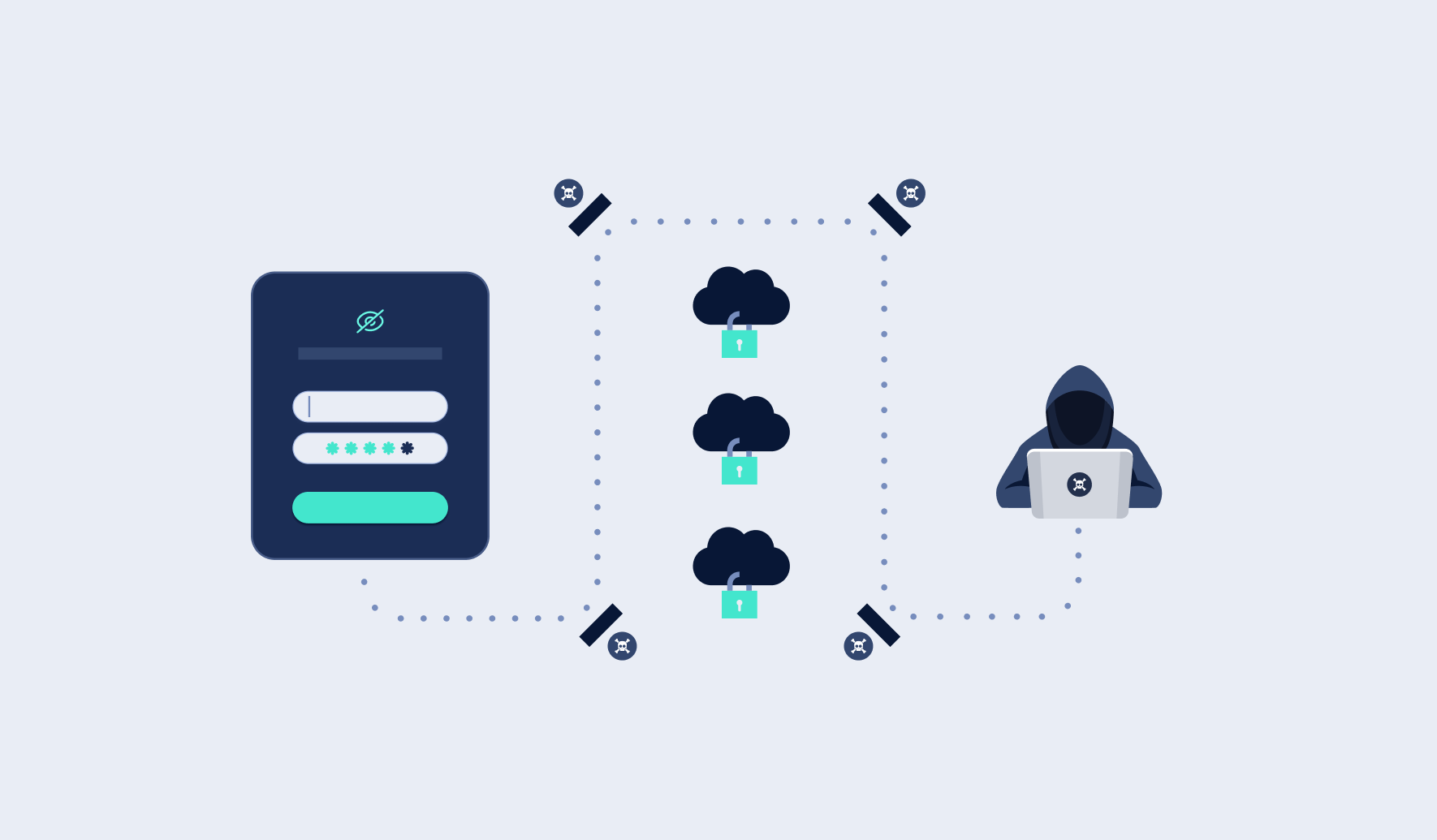
Simplified Lateral Movements
Attackers will take advantage of any weakness they find. The easier, the better. As such, using stolen valid credentials is a game-changer that simplifies lateral movements, avoids detection, and escalates privileges while blending in with normal users’ activity to remain undetected for extended periods.
Reusing passwords between different accounts makes the work of attackers even easier. For example, using the same strong password on a personal Gmail account and on a business account can have disastrous consequences in the context of password spraying.
Broader Security Posture
Attackers and criminals are constantly developing new techniques, making it necessary for organizations to adapt to keep up. The traditional model of long-lived credentials is no longer sufficient. Instead, organizations must adopt a more dynamic approach, utilizing short-lived keys frequently rotated and easily revoked, and implement Multi-Factor Authentication (MFA) wherever possible.
When it comes to new threats, malware detection and remediation are not enough. Organizations need a broader, more comprehensive security posture. This includes ensuring that all applications have access to a minimized set of credentials.
If you are not there yet, GitGuardian can help you automate secret detection and remediation through source code and systems, gathering as much information as the validity of the credentials.