In this guide, we'll dive into the details of mTLS, exploring how it works, the risks it can mitigate, implementation strategies, and best practices.
First, let's start with a question: Why is mTLS becoming more and more important now?
1. Why mTLS, Now?
Traditional security measures are not enough to protect sensitive data and infrastructure. As threats evolve and become more sophisticated, a more reliable authentication method is needed: enter mutual TLS (mTLS). Why is mTLS gaining so much attention now? Several factors have been driving its wide adoption:
- Microservices architectures and API-driven systems have created a complex web of both internal and external network traffic, which requires stronger authentication than simple username/password.
- Zero-trust security models operating on the principle of "never trust, always verify" are becoming more popular, which means we need authentication at every layer of our infrastructure.
- Sophisticated attacks like man-in-the-middle (MITM) attacks, data breaches, and other consequences have pushed us to search for a more secure solution.
mTLS directly addresses the above challenges by providing a secure identity for every connection, bidirectionally, which reduces the attack surface significantly and improves the overall security posture. Before diving into the details of how mTLS works, first, let's have a look at these specific threats mTLS is designed to mitigate.
2. Threat Model & Common Failure Modes: How mTLS Enhances Security
2.1 Unauthorized Access
TLS offers no protection against malicious or compromised clients. Any client that can establish a TLS connection can potentially access the server's resources, regardless of its legitimacy or authorization level.
mTLS mandates client authentication. The server can verify the client's identity based on its certificate and enforce authorization policies. Only clients with valid certificates and the necessary permissions will be granted access, effectively preventing malicious clients from accessing protected resources, allowing APIs to verify the identity of the calling application, and ensuring only authorized microservices can communicate with each other.
2.2 Man-in-the-Middle (MITM) Attacks
In a Man-in-the-Middle (MITM) attack, an attacker intercepts the communication between a client and a server, posing as both to eavesdrop on or manipulate the data being exchanged. The client believes it's communicating with the legitimate server, and the server believes it's communicating with the legitimate client, but in reality, all traffic is flowing through the attacker.
Traditional TLS, the standard form of TLS used for most HTTPS connections, helps mitigate MITM attacks by verifying the server's identity, but the issue is the server doesn't verify the client's identity, which creates a vulnerability: If an attacker can intercept the connection initiated by a client to a server, present a valid certificate (obtained by ways of a compromised CA, stolen cert, misissued, cert, domain hijacking, etc.) to the client and pretend to be the server, the connection is compromised.
mTLS adds another layer of defense because the server also needs to verify the client's identity. The attacker has to forge the client's identity, trusted by the server as well, to be able to talk to the legitimate server, making it significantly harder to impersonate both the client and the server.
2.3 Credential Theft and Replay
Traditional auth methods often rely on bearer tokens (API keys, JWTs, etc.). If these tokens are leaked, an attacker can replay them to gain unauthorized access. Because these tokens are often long-lived, they can be used for an extended period, causing significant damage.
mTLS eliminates the need for long-lived bearer tokens. The client's private key is used to prove its identity during the TLS handshake, but the private key itself is never transmitted over the network. The private key remains securely stored on the client device. Therefore, there's no "credential" to steal and replay. The client's identity is tied to its cryptographic key pair, which is much more difficult to compromise than a simple token.
By addressing these common failure modes, mTLS significantly strengthens the security posture of our apps and infrastructure, particularly in zero-trust environments where every connection must be verified.
3. How mTLS Works: Enhanced Security Through Bidirectional Verification
Unlike traditional TLS, where only the server's identity is validated, mTLS takes security a step further by requiring both the server and the client to authenticate each other, which also eliminates the need for password-based auth or other shared secrets. This bidirectional verification is significantly more secure, especially in zero-trust environments.
In the previous blog, we detailed how the handshake of TLS authentication works. A quick recap: Client and server exchange "hello" messages with random values, cipher suites, and the server's certificate. The client validates the certificate. If valid, the client sends an encrypted "premaster secret." Both sides derive session keys from the random values and premaster secret, then exchange "finished" messages to establish a secure, encrypted connection.
In mTLS, the first few steps are the same, but the server also requests and validates a certificate from the client, ensuring mutual authentication.
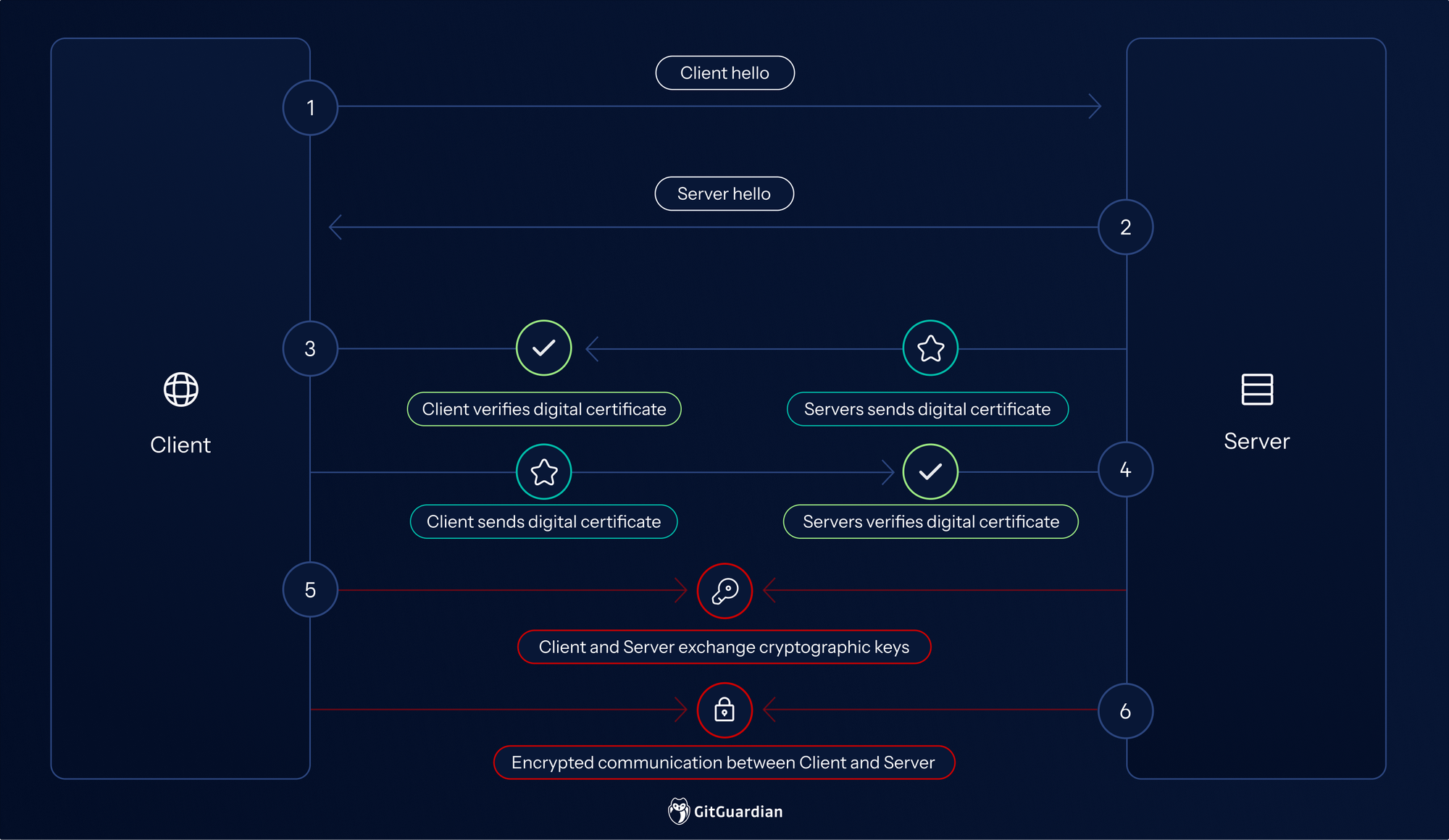
A breakdown of an mTLS handshake:
- "Client Hello": The client initiates the connection, sending a client random, a string of random bytes, with its supported TLS version and cipher suites.
- "Server Hello" and Certificate: In reply to the client hello, the server sends a message containing the server's SSL certificate, the server's chosen cipher suite, and the server's random, another random string of bytes generated by the server.
- Certificate Validation (Server): The client performs a series of checks, including trust chain validation, signature verification, revocation status check, expiration, and domain check, etc.
- Certificate Request (Server): At this step, it starts to differ from the TLS handshake. The server sends a "CertificateRequest" message to the client, specifying the types of certificates it will accept (e.g., the acceptable CAs). This signals that the server requires client authentication.
- Client Certificate: The client sends its own SSL certificate to the server.
- Key Exchange and Secure Channel: If all validation checks pass, the client generates a premaster secret (another random string), encrypted with the public key and can only be decrypted with the private key by the server, and sends it to the server. Both client and server generate session keys from the client random, the server random, and the premaster secret, and apparently, they should be the same.
- Certificate Validation (Client): The server validates the client's certificate, performing similar checks to those the client performed on the server's certificate.
- Certificate Verify (Client): The client sends a "CertificateVerify" message, which includes a digital signature calculated using the client's private key over the handshake messages. This proves that the client possesses the private key associated with the certificate it presented.
- At this time, the client sends a "finished" message that is encrypted with the session key, telling the server that it's ready, and the server does the same. Now, the handshake is completed, a secure symmetric encryption is achieved, and communication continues using the session key.
Key differences between TLS and mTLS:
| Feature | Standard TLS | mTLS |
|---|---|---|
| Authentication | Server authenticates to client | Server and client authenticate to each other |
| Certificate | Server presents certificate | Server and client present certificates |
| CertificateRequest | Not used (usually) | Used by the server to request the client's certificate |
| Security | Protects against eavesdropping and man-in-the-middle attacks, verifies server identity | Stronger security: Protects against eavesdropping, man-in-the-middle attacks, and unauthorized clients accessing the server |
4. mTLS in Operation
Implementing mTLS effectively requires careful planning and attention to operational details.
4.1 Choosing the Right CA
First, choosing the right Certificate Authority (CA) is crucial for establishing trust in your mTLS infrastructure. Common options include public CAs, private CAs, and self-signed certificates. For most production environments requiring mTLS, a private CA is the recommended approach due to the control and flexibility it offers. For more information on public/private CAs, see the previous blog on TLS.
4.2 Certificate Lifecycle Management
Proper certificate lifecycle management is crucial for the security and reliability of mTLS infrastructure as well; issuance, renewal, and revocation should be automated as much as possible. For more information and best practices about certificate management, see the previous blog on TLS.
4.3 Server-Side Configuration
Make sure mTLS is configured correctly on the server side. For example, if Nginx is used, the option ssl_client_certificate specifies the path to the CA certificate used to verify client certificates, and ssl_verify_client on enables client certificate verification, while optional or optional_no_ca are less secure options. API gateways often provide plugins or built-in support for mTLS. Refer to the specific gateway's documentation for configuration details. For more details about how API gateway helps implement TLS/mTLS, see the previous blog on TLS.
4.4 Client-Side Configuration/Code Samples
Clients need to be configured to present their certificates during the TLS handshake. The exact configuration depends on the client type and programming language. General Steps are:
- Obtain a client certificate and private key.
- Store the certificate and key securely.
- Configure the client to use the certificate and key when connecting to the server.
- Trust the server's CA certificate (or disable certificate verification for testing purposes only).
A simple example with Python/requests:
result = requests.get(
'https://myserver.internal.net:443',
cert=('client.crt', 'client.key'),
verify='ca.crt')
# do something with result
Important Considerations:
- Error Handling: Implement robust error handling in your client code to handle certificate errors, connection failures, and other potential issues.
- Security Best Practices: Follow security best practices for storing and managing private keys. Avoid storing private keys in plain text.
- Testing: Thoroughly test your mTLS implementation in a development environment before deploying it to production.
- Logging: Implement logging to track mTLS authentication events and identify potential security issues.
Since mTLS and TLS both use certificates, for more best practices for mTLS deployment/certificate management, see the previous blog on TLS.
5. mTLS Considerations and Challenges
While mTLS significantly enhances security, it also brings challenges. A realistic understanding of these aspects will help us manage our mTLS deployment effectively. And it's crucial to recognize mTLS isn't a silver bullet and what mTLS doesn't inherently solve, including: compromised private keys on client or server hosts, weak or broken PKI implementations (untrusted CAs, mis-issued certificates, wildcard overuse), insufficient certificate validation, over-permissive trust stores, expired certificates leading to outages, revocation gaps, middlebox/proxy breakage, observability blind spots, operational rollback risks, and performance pitfalls.
- Complexity: Implementing mTLS inherently adds complexity to system architecture. It requires careful planning, configuration, and management of certificates, as well as modifications (maybe) to application code and infrastructure. This increased complexity can lead to potential misconfigurations and vulnerabilities if not handled properly. Debugging issues in an mTLS-enabled environment can also be more challenging due to the added layer of authentication.
- Certificate Management Overhead: Certificate management is an ongoing effort. This includes generating, distributing, renewing, and revoking certificates. Managing client certificates, in particular, can be complex, especially in large-scale deployments or environments with a high churn rate of clients. Automating certificate lifecycle management is essential to reduce manual errors and operational overhead, but it also requires investment in tooling and infrastructure.
- Performance Impact: mTLS introduces some performance overhead due to the additional cryptographic operations required for mutual authentication. The TLS handshake process is more involved with mTLS, potentially increasing latency and CPU usage. While the performance impact is usually minimal with modern hardware and optimized configurations, it's important to consider this factor, especially for high-throughput applications or resource-constrained devices. Careful monitoring and tuning of TLS parameters can help mitigate any performance issues.
- Client Compatibility: Compatibility with older clients or devices that may not fully support mTLS can be a concern. Some clients may not support the required TLS versions, cipher suites, or certificate formats. This can lead to connectivity issues and require workarounds or compromises in security. Thorough testing with a variety of clients is essential to ensure compatibility and identify any potential problems.
Addressing these gaps requires a holistic security approach of careful planning, robust tooling, certificate management, validation, comprehensive monitoring, skilled developers, and well-planned operational procedures. For more information on incident response, see here.
Now that we've examined the challenges of mTLS, let's explore how these can be mitigated, particularly within complex environments like Kubernetes and service meshes.
6. mTLS with Kubernetes and Service Meshes: Streamlining Security
Kubernetes and service meshes provide powerful platforms for simplifying and automating mTLS implementation, addressing many of the challenges outlined previously. They offer solutions for certificate management, performance optimization, and enhanced security posture in complex, dynamic environments.
6.1 Certificate Management in Kubernetes
While Kubernetes itself doesn't directly enforce mTLS, it provides the foundation for integrating mTLS solutions. For example, we can achieve certificate management with cert-manager, a popular Kubernetes add-on that automates the issuance and management of TLS certificates. It can integrate with various CAs, including Let's Encrypt, HashiCorp Vault, and custom private CAs.
6.2 Service Mesh
A service mesh, such as Istio or Linkerd, is a dedicated infrastructure layer designed to manage, secure, and observe microservice communication. It acts as a transparent layer, intercepting network traffic between services and adding capabilities like traffic management (routing, load balancing, retries), security (authentication, authorization, mTLS), and observability (metrics, tracing, logging) without requiring changes to application code. One of the primary functions of a service mesh is to simplify and enhance the security of microservice interactions, often by automating mTLS and enforcing consistent security policies across the entire application.
6.3 How Service Mesh Works
Service meshes implement mTLS (typically) by deploying lightweight proxy servers, often referred to as "sidecars," alongside each microservice. These sidecar proxies intercept all incoming and outgoing traffic for their associated service. When a service attempts to communicate with another, the sidecar proxy automatically handles the mTLS handshake, performing certificate validation to verify the identity of both the client and the server. The sidecar then encrypts and decrypts the communication, ensuring secure and authenticated data exchange.
The service mesh's control plane plays a crucial role in managing this process by issuing and distributing certificates to the sidecar proxies, as well as enforcing security policies that dictate which services are authorized to communicate with each other. This separation of concerns allows developers to focus on application logic while the service mesh handles the complexities of securing inter-service communication.
6.4 Benefits of Combining mTLS with Service Mesh
mTLS and service meshes form a powerful synergy because service meshes simplify the deployment and management of mTLS within complex microservice environments. Service meshes automate the provisioning and rotation of certificates, eliminating much of the manual overhead associated with TLS/mTLS. This pairing offers several key benefits:
- Simplified configuration: Service meshes abstract away the intricacies of mTLS setup on individual services.
- Automated certificate management: Automatic issuance, renewal, and revocation.
- Centralized policy enforcement: Ensure consistent security policies across all services within the mesh.
- Improved observability: Grant visibility into mTLS connections and traffic patterns.
- Zero-trust: Every service interaction is authenticated and authorized, regardless of its location within the network.
7. Summary
mTLS stands as a cornerstone of modern security architectures, offering robust authentication and encryption that significantly enhances the security posture of applications and services. By verifying the identity of both the client and the server, mTLS provides a critical defense against unauthorized access and data breaches, especially in increasingly complex and distributed environments. As threats continue to evolve, embracing mTLS is no longer optional, but a necessity for organizations committed to protecting their data and ensuring the integrity of their systems.
We encourage you to explore the possibilities of mTLS and implement it within your own environments, leveraging the tools and techniques discussed in this guide to build a more secure and resilient future. For more information, see:


FAQ
What is mutual TLS (mTLS) and why is it becoming critical now?
Mutual TLS (mTLS) is an enhanced security protocol where both the client and server authenticate each other using certificates, unlike traditional TLS where only the server is authenticated. mTLS is gaining critical importance due to the rise of microservices architectures and API-driven systems creating complex network traffic, the adoption of zero-trust security models requiring "never trust, always verify" principles, and increasingly sophisticated attacks like man-in-the-middle (MITM) attacks and data breaches. mTLS directly addresses these challenges by providing secure bidirectional identity verification for every connection, significantly reducing the attack surface.
How does mTLS protect against man-in-the-middle (MITM) attacks better than standard TLS?
Traditional TLS only verifies the server's identity, creating a vulnerability where an attacker with a valid certificate (obtained through compromised CA, stolen cert, or domain hijacking) can intercept connections and impersonate the server. mTLS adds another critical layer of defense by requiring the server to also verify the client's identity. An attacker would need to forge both the server's identity to fool the client AND the client's identity trusted by the server, making it significantly harder to successfully execute MITM attacks. This bidirectional verification ensures both parties are authentic.
How does the mTLS handshake differ from a standard TLS handshake?
The mTLS handshake begins similarly to standard TLS with Client Hello and Server Hello messages, but adds critical mutual authentication steps. After the server sends its certificate, the server sends a "CertificateRequest" message specifying acceptable certificate types and CAs. The client then sends its own SSL certificate to the server. After key exchange, the server validates the client's certificate (performing trust chain validation, signature verification, revocation checks), and the client sends a "CertificateVerify" message with a digital signature proving it possesses the private key. Only after both parties successfully authenticate each other is the secure channel established.
How does mTLS eliminate credential theft and replay attacks?
Traditional authentication methods rely on bearer tokens (API keys, JWTs) that, if leaked, can be replayed by attackers to gain unauthorized access. These tokens are often long-lived, enabling extended exploitation. mTLS eliminates this vulnerability by using the client's private key to prove identity during the TLS handshake, but the private key itself is never transmitted over the network—it remains securely stored on the client device. Therefore, there's no "credential" to steal and replay. The client's identity is tied to its cryptographic key pair, which is significantly more difficult to compromise than a simple token.
What are the main operational challenges of implementing mTLS?
mTLS implementation introduces several challenges: 1) Complexity - requires careful planning, certificate management, and potential code modifications, making debugging more difficult; 2) Certificate Management Overhead - ongoing effort for generating, distributing, renewing, and revoking certificates, especially challenging with high client churn; 3) Performance Impact - additional cryptographic operations increase latency and CPU usage, particularly for high-throughput applications; and 4) Client Compatibility - older clients may not support required TLS versions, cipher suites, or certificate formats. Addressing these requires holistic security approaches, robust tooling, automation, comprehensive monitoring, and well-planned operational procedures.
What security gaps does mTLS NOT inherently solve?
While mTLS significantly enhances security, it's not a silver bullet. mTLS doesn't inherently solve: compromised private keys on client or server hosts, weak or broken PKI implementations (untrusted CAs, mis-issued certificates, wildcard overuse), insufficient certificate validation, over-permissive trust stores, expired certificates leading to outages, revocation gaps, middlebox/proxy breakage, observability blind spots, operational rollback risks, and performance pitfalls. A holistic security approach combining mTLS with careful planning, robust tooling, comprehensive validation, monitoring, skilled developers, and well-planned operational procedures is essential.
How do service meshes simplify mTLS implementation in Kubernetes?
Service meshes like Istio and Linkerd act as a dedicated infrastructure layer that automates mTLS by deploying lightweight "sidecar" proxies alongside each microservice. These sidecars automatically intercept traffic, handle mTLS handshakes, perform certificate validation, and encrypt/decrypt communication without requiring code changes. The service mesh control plane manages certificate issuance, distribution, and rotation while enforcing security policies. This provides simplified configuration, automated certificate management, centralized policy enforcement, improved observability, and true zero-trust architecture where every service interaction is authenticated and authorized regardless of network location.
What is cert-manager and how does it help with mTLS in Kubernetes?
cert-manager is a popular Kubernetes add-on that automates the issuance and management of TLS certificates, addressing one of the major operational challenges of mTLS. While Kubernetes itself doesn't directly enforce mTLS, cert-manager provides the foundation for mTLS solutions by integrating with various Certificate Authorities including Let's Encrypt, HashiCorp Vault, and custom private CAs. It automates certificate provisioning, renewal, and rotation, eliminating much of the manual overhead and reducing the risk of expired certificates causing outages in production environments.
Why is a private CA typically recommended for mTLS in production environments?
For most production environments requiring mTLS, a private CA is the recommended approach due to the control and flexibility it offers. Private CAs allow organizations to: issue certificates specifically for internal services and clients without external dependencies, maintain full control over the certificate issuance and validation process, implement custom policies and certificate attributes tailored to organizational needs, avoid costs associated with public CA certificates for internal infrastructure, and maintain the security boundary since private CA root certificates are not trusted by default outside the organization. This is particularly important for service-to-service authentication in microservices architectures.
This article is a guest post. Views and opinions expressed in this publication are solely those of the author and do not reflect the official policy, position, or views of GitGuardian, The content is provided for informational purposes, GitGuardian assumes no responsibility for any errors, omissions, or outcomes resulting from the use of this information. Should you have any enquiry with regard to the content, please contact the author directly.