
Balancing Security and Velocity in Modern Software Development
Developers don’t want to become experts at security, and slowing down for anything is a tough proposition. Security isn’t a problem that will just go away, though.

Developers don’t want to become experts at security, and slowing down for anything is a tough proposition. Security isn’t a problem that will just go away, though.

Securely managing secrets within the CI/CD environment is super important. Mishandling secrets can expose sensitive information, potentially leading to unauthorized access, data breaches, and compromised systems.

Learn how to automate Helm deployments with GitOps, using Argo CD for continuous delivery. Seamlessly handle secrets, pod auto-restart, and version propagation in Kubernetes with this production-ready integration.

Exciting news! Our first book, "Crafting Secure Software," is now available. Learn how to embed security throughout the SDLC, mitigate risks, and foster a security culture. Get your copy today and level up your software security game!

Have you heard about SOPS? If you have already been in a situation where you needed to share sensitive information with your teammates, this is for you. Today, let's have a look at how it works and how to use it with various key management services such as AWS KMS and HashiCorp Vault.
Using multiple cloud service providers isn't all benefits, it has its challenges. Today, let's have a look at multicloud: What it is, what are the challenges, especially security challenges, and what are the best practices towards a secure multicloud architecture.

DevSecOps Engineer Gene Gotimer explains why constant software dependency updates are crucial for security in DevSecOps practices.
Essential reading for developers and security professionals alike: a comprehensive comparison of vulnerability databases to help you cut through the noise.
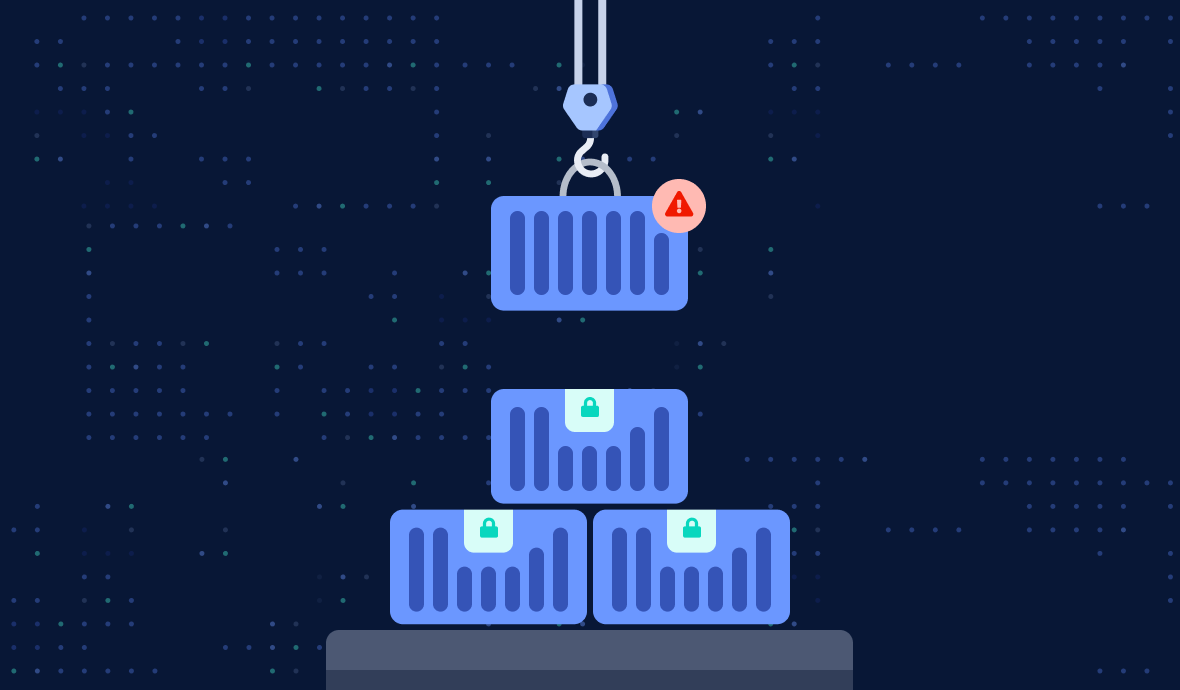
In this article we present a novel way to protect your container applications post-exploitation. This additional protection is called Seccomp-BPF.

Container security is crucial in the age of microservices and DevOps. Learn about common container vulnerabilities, container security scanning, and popular tools to secure your containers in this comprehensive guide.