IAM is no longer just about humans.
With all the interconnected services and apps, Non-Human Identities (NHIs)—also called machine identities—play a pivotal role in facilitating machine-to-machine communication. To claim their identity, machines authenticate via secrets like API keys, OAuth tokens, database credentials, usernames and passwords, and certificates. With an average organization having approximately 45 to even 100 times more machine identities than human identities, they’ve become the number one vector for a successful attack, frequently overlooked.
GitGuardian, already a recognized leader in detecting and remediating leaked secrets, is stepping forward with a comprehensive action plan to address this escalating risk. Building on its proven expertise, GitGuardian now provides visibility, control, lifecycle management, and security for non-human identities and their secrets. Let’s examine the problem, its scope, and the approach we are taking to redefine security for non-human identities.
The Explosion of Non-Human Identities and Secrets Sprawl
As machine identities proliferate due to microservices architectures and more and more interactions with external services, their management has grown exponentially complex. Scattered across environments, these NHIs rely on secrets to access resources securely. So secrets are the keys to the kingdom—a critical piece of the non-human identity security puzzle.
And secrets sprawl doesn’t stop at public GitHub. Private repositories are even more dangerous because on average, they are 8x more likely to reveal at least one incident. Developers, driven by tight deadlines, also often unintentionally share secrets across tools like Slack, Jira, or Confluence.
Public leaks, combined with secrets scattered throughout the internal tech stack, showcase how secrets security has become a critical issue that also compromises compliance with standards such as GDPR, PCI-DSS, NIST, or HIPAA.
Why Non-Human Identities Demand Immediate Attention
With 80% of breaches tied to identities and 83% involving compromised credentials, attackers increasingly exploit machine identities. They can be created, stored, used, and shared in many places. When secrets are leaked or mismanaged, attackers gain unauthorized access, escalate privileges, and move laterally within systems to collect data that they shouldn’t access and cause ecosystem-style supply chain attacks. They can create a huge data breach with just one leaked secret. In the past year, breaches tied to secrets have impacted enterprises with repercussions ranging from lost development time to fines in the hundreds of millions. Some incidents from past months:
- Business intelligence company Sisense has seen secrets compromised in its GitLab repositories
- The New York Times had their entire codebase leaked
- Nation-state hackers accessed Microsoft source code and stole secrets
- Stolen Okta Auth tokens led to Cloudflare breach
As NHIs and secrets continue to be largely unmonitored, these attacks are likely to increase in both number and impact.
Existing Solutions Fall Short
Existing tools designed to secure machine identities and secrets do not provide a holistic approach and often address only part of the problem:
- IAM tools focus on human identities. Machine identities can be created by anyone and stored in plain text. They are often decentralized and harder to track. They don’t rely on MFA and are overprivileged. They fall outside their purview.
- CSPMs (Cloud Security Posture Management tools) prioritize cloud environments, leaving gaps in other areas where secrets reside, such as developer repositories and messaging platforms.
- Secrets managers and vaults securely store secrets but don’t tackle secrets sprawl, leaks, or their lifecycle management required across diverse environments.
Without comprehensive management, secrets can quickly become liabilities. We have seen that organizations use multiple secrets management tools at the same time. Vault sprawl in enterprises complicates the situation, making centralized governance nearly impossible. Often, there are platform-specific secrets managers in use from AWS, Azure, and GCP, plus multiple other secrets management tools in use. A typical organization uses at least 6 vaults.
As the number of vaults increases, so does the challenge of managing these vaults. So organizations are still struggling with critical security questions, such like:
- Are all our secrets vaulted?
- Where are our secrets stored?
- Have our secrets been publicly exposed?
- Are our secrets in use? And if so, where?
- Where should I deploy my vaults?
Hence, the industry needs more robust, structured, and automated solutions designed specifically to manage NHIs' lifecycles.
GitGuardian’s Full-Cycle Approach to Non-Human Identity Security
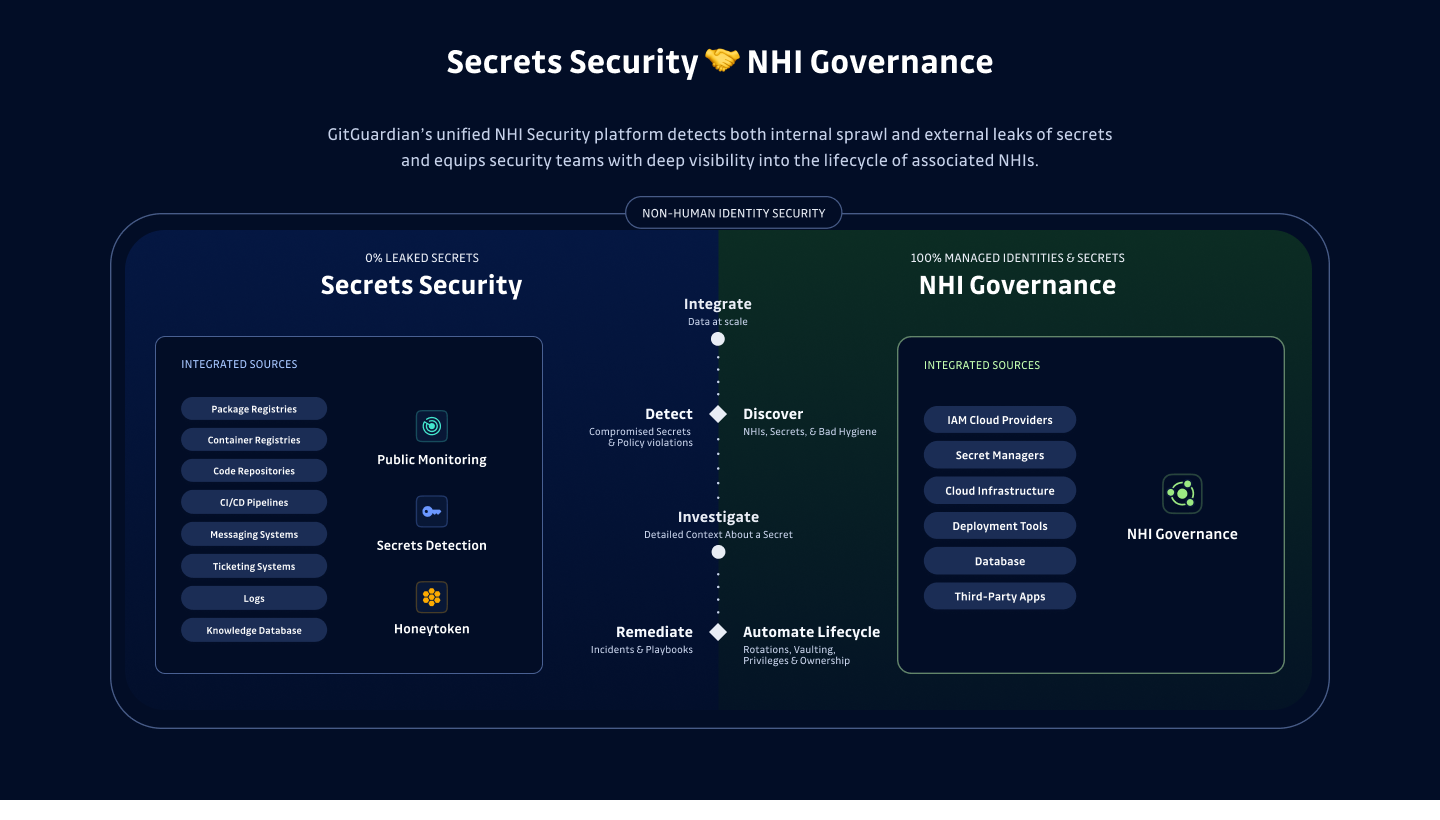
GitGuardian’s product strategy is built on two core pillars: Secrets Security and NHI Governance, delivering a holistic approach to NHI security. This bridges the gaps in the above tools, targeting the core needs of application security and IAM teams with solutions that scale alongside today’s modern digital infrastructure. Our offerings ensure visibility, governance, and actionability across the entire lifecycle of secrets:
- Public Monitoring of Leaks: Public repositories are an open gateway for attackers. GitGuardian scans billions of commits on platforms like GitHub, detecting and alerting on exposed secrets. By proactively notifying developers, we help prevent breaches at their earliest stage.
- Secrets Detection in Internal Tools: Securing internal environments requires more than just monitoring the source code. From Slack to Jira to container registries, our solution detects secrets wherever they exist. This reduces internal sprawl and strengthens overall secrets security hygiene.
- Proactive Protection through Honeytoken: Honeytokens are decoy secrets, tricking attackers into revealing themselves during NHI-related breaches. This layer of proactive protection provides warning signals in real-time, minimizing the time attackers have to cause damage after a breach.
And now, GitGuardian is introducing the missing piece to solve the Non-Human Identity conundrum.
"Our commitment is to empower security and development teams with actionable insights, scalable solutions, and robust governance. Our new NHI Governance capabilities are a natural extension of our deep-rooted expertise in secrets security. It not only enables the remediation of leaked secrets but also strengthens overall NHI management and hygiene,” said Eric Fourrier, CEO of GitGuardian.
4. NHI Governance (in private beta):
This solution delivers an integrated view of how secrets are disseminated, used, and secured across an organization’s infrastructure. By combining GitGuardian’s expertise in secrets security with continuous monitoring and full contextual analysis, NHI Governance creates a comprehensive risk assessment for all secrets and NHIs.
Some of our design partners highlighted the pains of their current approach:
"MMMHHH…I don’t have a single source of truth for my secrets today...honestly I don’t know how to do that."
"It would be hard, it would take me at least 2-3 full days of investigation to perform an end-to-end mapping for a single secret today."
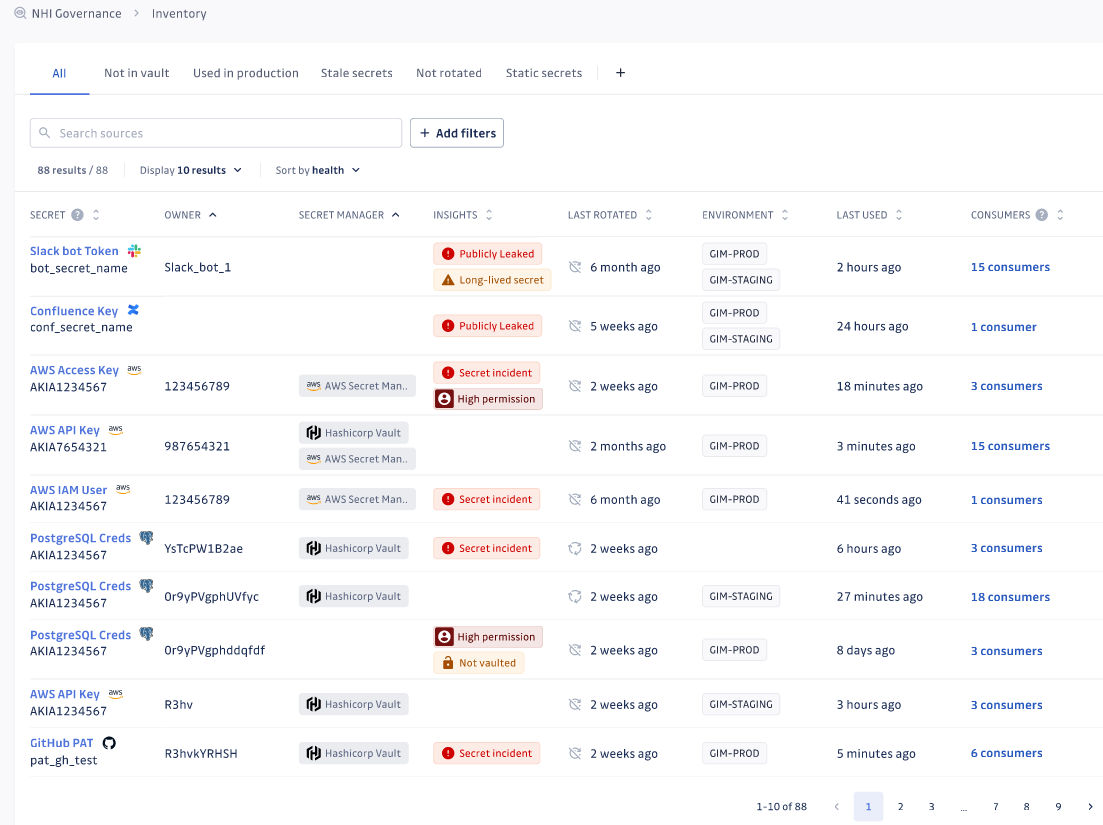
These challenges will now become manageable. GitGuardian is integrating directly with five leading secrets management platforms like CyberArk Conjur, Vault by HashiCorp, AWS Secrets Manager, Azure KeyVault, Google Cloud Secrets Manager, Akeyless Vaultless Secrets Management, and Delinea Secrets Server. This provides observability into legitimate usage of secrets, empowering organizations with real-time insights on secrets’ lifecycle such as:
- Where secrets are stored.
- Where secrets are distributed across multiple vaults.
- Who owns the secrets and their permissions.
- When they were last rotated.
- Which systems or services depend on them.
These integrations offer end-to-end mapping and a deep contextual understanding of secrets discovered in the infrastructure that can transform incident response and policy enforcement for companies.
This way, companies can plan remediation for compromised secrets without breaking production, purge stale secrets to reduce vault storage and access costs, enforce vault usage for non-vaulted secrets, and automate remediation tasks as much as possible, drastically reducing risk and operational strain.
To gain a deeper understanding of our use cases with vaults, I recommend reading this blog post.
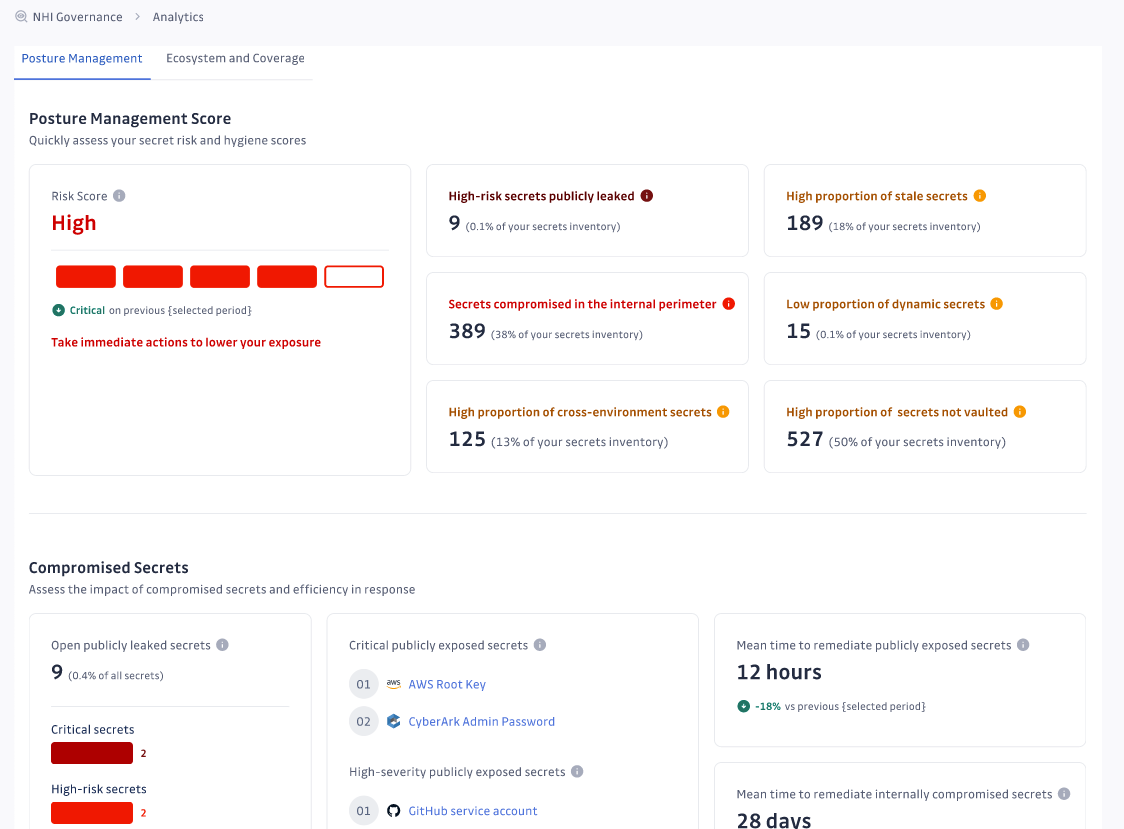
Alongside these capabilities, GitGuardian helps you understand your security posture with a risk score by tracking compromised secrets, improving response capabilities, and identifying gaps in secrets hygiene. It provides a unified view of your secrets landscape, enabling you to identify blind spots, optimize operations, and empower your executive teams with informed business decisions.
As one of our design partners remarked, “The posture analytics are exactly what I am looking for! Seriously, I dreamed about it and I see it there in your dashboard.”
The Path Forward
Non-human identities are not just an IT concern, they are as critical as human identities and must rise to the top of the CISO’s and CIO's priorities, as they are fundamental to enterprise security and operational integrity. GitGuardian’s mission is to ensure organizations can see and secure every secret and NHI in their ecosystem. As mentioned before, our dual approach combines:
- Comprehensive detection and remediation of exposed and hardcoded secrets. And proactive measures to mitigate NHI-related breaches.
- Centralized inventory of all NHIs across the environments, with their context and entire lifecycle management of the secrets.
Are You Truly in Control of Your Non-Human Identities?
Here are a few important questions that every organization should be asking:
- How well do we know where your non-human identities are located?
- How are their associated secrets being managed across multiple vaults?
- Are these secrets overprivileged or stale?
- What gaps exist in our current secrets management practices?
- What could it mean for our organization to have 100% visibility and control over your NHIs?
These aren’t just operational questions. Without clear answers to these, organizations often risk significant exposure. GitGuardian is committed to answering these questions and delivering solutions that map, monitor, and secure NHIs comprehensively, enabling organizations to see value rapidly. Stay tuned for more on our innovations, and join us in redefining security posture for the non-human identity era.
Non-human identity (NHI) or machine identity is not something new. Securing NHIs is not just a challenge—at GitGuardian, we see it as a turning point to build a safer, more resilient ecosystem.
Because one thing is certain: attackers won’t wait—why should you?
Ready to take control of your non-human identities? Read our press release and see how we’re redefining non-human identity security.








