What Happened?
On October 1, 2025, the cybercrime group "Crimson Collective" publicly disclosed a significant breach of Red Hat's consulting GitLab instance. The attackers claimed to have exfiltrated 570GB of compressed data from over 28,000 repositories, including sensitive Customer Engagement Reports (CERs) affecting approximately 800 organizations worldwide.
Red Hat confirmed the security incident, clarifying that it specifically involved "a GitLab instance used solely for Red Hat Consulting on consulting engagements, not GitHub" as initially reported by some sources.
💡 Disclaimer: This analysis is based on publicly available information from multiple cybersecurity sources and Red Hat's official statements. GitGuardian has not independently verified the attackers' claims or accessed any compromised data.
Timeline of Events
- September 24, 2025: Crimson Collective Telegram channel created
- September 24, 2025: Group claims Nintendo website defacement
- September 25, 2025: Claims breach of Claro Colombia telecommunications
- October 1, 2025: Public disclosure of Red Hat breach on Telegram
- October 2, 2025: Red Hat confirms security incident and begins remediation
- October 2, 2025: Belgium's Centre for Cybersecurity issues advisory warning
What Was Exposed?
According to the threat actors and cybersecurity researchers analyzing the disclosed information, the stolen data includes:
Customer Engagement Reports (CERs)
- Infrastructure configurations and network topologies
- Security assessments and vulnerability details
- Authentication tokens and API keys
- Database connection strings and credentials
- CI/CD pipeline configurations
- VPN settings and network access details
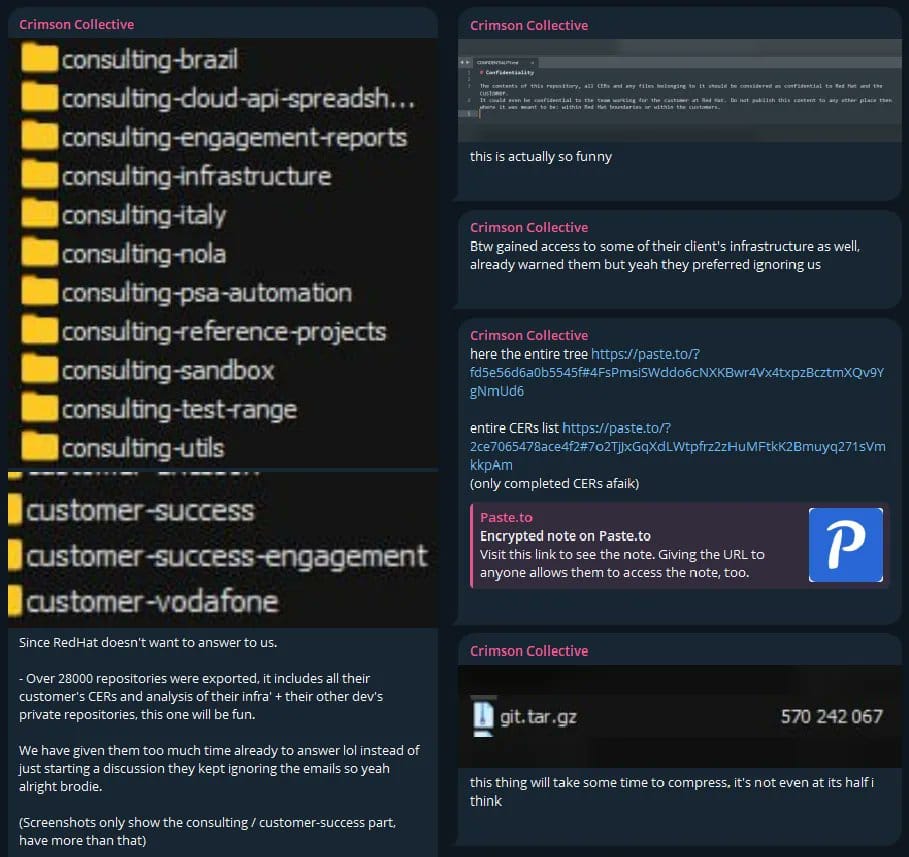
Affected Organizations
The leaked file structures reportedly reference major organizations across multiple sectors:
Financial Services: Bank of America, Citi, JPMorgan Chase, HSBC, Santander, BBVA, Bank of Canada, American Express, Fidelity Technology: IBM, Cisco, Adobe, Siemens, Bosch Telecommunications: Verizon, Telefonica, T-Mobile, AT&T, Atos Group, SFR Government: U.S. Navy, NSA, Department of Energy, NIST, U.S. Senate, Department of Defence Healthcare: Mayo Clinic, Kaiser Permanente Other: Boeing, 3M, Walmart
The Attack Pattern
This incident follows a concerning pattern we've observed in consulting firm breaches:
- Initial Access: While the exact attack vector remains unknown, the attackers gained access to Red Hat's internal GitLab instance
- Data Harvesting: Systematic extraction of consulting repositories containing client infrastructure details
- Credential Mining: Discovery of hardcoded secrets within Customer Engagement Reports
- Lateral Movement: Claims of pivoting to customer infrastructure using harvested credentials
- Extortion Attempt: Initial contact with Red Hat followed by public disclosure when ignored
The Secrets Sprawl Problem
Based on GitGuardian's analysis of similar consulting firm breaches, these repositories likely contained thousands of embedded secrets. Our research consistently shows:
- Internal repositories contain 8-10x more secrets than public GitHub repositories
- Consulting engagements frequently embed customer credentials in proof-of-concept code
- Infrastructure-as-code configurations commonly contain cloud access keys
- Long-lived, overprivileged credentials are standard practice in enterprise environments
- Lack of pro-active detection systems, like honeytokens
The Crimson Collective specifically mentioned finding "authentication keys, full database URIs, and other private information" that enabled access to downstream customer infrastructure.
Industry Response and Impact
Belgium's Cybersecurity Warning
The Centre for Cybersecurity Belgium issued a high-risk advisory, specifically warning:
There is high risk to Belgian organizations that use Red Hat Consulting services. There is also potential supply chain impact if your service providers or IT partners worked with Red Hat Consulting.
Red Hat's Response
Red Hat's official statement emphasized:
The security and integrity of our systems and the data entrusted to us are our highest priority. At this time, we have no reason to believe the security issue impacts any of our other Red Hat services or products and are highly confident in the integrity of our software supply chain.
Critical Actions for Red Hat Customers
If your organization has engaged Red Hat Consulting services, take immediate action:
Immediate Credential Rotation
- All authentication tokens shared with or used in Red Hat engagements
- Database credentials and connection strings from consulting projects
- API keys and service account credentials
- SSL/TLS and SSH keys used in Red Hat configurations
- Cloud access keys (AWS, Azure, GCP) from infrastructure-as-code projects
Security Audit Requirements
- Review all access logs for suspicious activity since September 2025
- Scan internal repositories for hardcoded secrets from Red Hat engagements
- Audit network configurations and VPN access mentioned in consulting reports
- Verify integrity of systems referenced in Customer Engagement Reports
Enhanced Monitoring
- Deploy honeytokens in systems mentioned in Red Hat consulting documents
- Implement continuous secrets scanning across all code repositories
- Monitor for unusual API usage patterns on rotated credentials
- Review third-party access permissions and service integrations
Lessons for the Industry
The Consulting Firm Vulnerability
This breach highlights a critical blind spot in enterprise security: consulting firms as credential aggregation points. When external consultants work across multiple customer environments, their repositories become high-value targets containing secrets from dozens of organizations. Enterprises should avoid giving access to production environment during PoC when possible.
Supply Chain Cascade Effects
A single compromised consulting firm can trigger a cascade of breaches across its entire customer base. This incident demonstrates why supply chain security governance must extend beyond software dependencies to include service providers with infrastructure access.
Strengthening Your Defenses
For Organizations Using Consulting Services
- Implement strict credential hygiene policies for external engagements
- Use short-lived, least-privilege credentials for consulting projects
- Deploy continuous secrets monitoring across all repositories
- Implement comprehensive NHI governance for service accounts and API keys
- Require consultants to use your secrets management solutions rather than hardcoding credentials
- Establish clear incident response procedures with consulting partners
For Consulting Firms
- Segregate customer environments with dedicated instances
- Implement automated secrets scanning on all repositories
- Use customer-provided secrets management systems when possible
- Establish robust incident response teams beyond bug bounty platforms
- Encrypt sensitive customer data at rest in all storage systems
The Broader Implications
This incident represents more than just another data breach—it's a wake-up call about the interconnected nature of modern cybersecurity risks. As organizations increasingly rely on consulting partners for digital transformation projects, the attack surface expands exponentially.
The Crimson Collective's ability to potentially pivot from Red Hat's repositories to customer infrastructure demonstrates the cascading impact of secrets sprawl. One compromised consulting firm can become the gateway to hundreds of customer environments.
As we continue monitoring this evolving situation, one thing remains clear: the age of secrets sprawl demands immediate, comprehensive action. The question is whether you have the visibility and controls in place to detect and respond when they are.
FAQ
What happened in the Red Hat GitLab breach?
On October 1, 2025, the cybercrime group "Crimson Collective" publicly disclosed a significant breach of Red Hat's consulting GitLab instance. The attackers claimed to have exfiltrated 570GB of compressed data from over 28,000 repositories, including sensitive Customer Engagement Reports (CERs) affecting approximately 800 organizations worldwide. Red Hat confirmed the security incident, clarifying that it specifically involved "a GitLab instance used solely for Red Hat Consulting on consulting engagements, not GitHub" as initially reported.
What types of sensitive data were exposed in the breach?
The stolen data reportedly included Customer Engagement Reports (CERs) containing infrastructure configurations and network topologies, security assessments and vulnerability details, authentication tokens and API keys, database connection strings and credentials, CI/CD pipeline configurations, and VPN settings and network access details. The Crimson Collective specifically mentioned finding "authentication keys, full database URIs, and other private information" that enabled access to downstream customer infrastructure.
Which organizations were potentially affected by the Red Hat breach?
The leaked file structures reportedly reference major organizations across multiple sectors including financial services (Bank of America, Citi, JPMorgan Chase, HSBC), technology companies (IBM, Cisco, Adobe, Siemens), telecommunications (Verizon, Telefonica, T-Mobile, AT&T), government agencies (U.S. Navy, NSA, Department of Energy, NIST), healthcare organizations (Mayo Clinic, Kaiser Permanente), and other major enterprises (Boeing, 3M, Walmart, Fidelity). Approximately 800 organizations worldwide were potentially impacted.
What is the timeline of the Crimson Collective's activities?
The timeline shows rapid escalation: September 24, 2025 - Crimson Collective Telegram channel created and group claims Nintendo website defacement; September 25, 2025 - Claims breach of Claro Colombia telecommunications; October 1, 2025 - Public disclosure of Red Hat breach on Telegram; October 2, 2025 - Red Hat confirms security incident and begins remediation, Belgium's Centre for Cybersecurity issues advisory warning. This pattern shows the group's increasing ambition and capability over just one week.
What immediate actions should Red Hat consulting customers take?
Organizations should immediately rotate all credentials shared with or used in Red Hat engagements, including authentication tokens, database credentials and connection strings, API keys and service account credentials, SSL/TLS and SSH keys, and cloud access keys from infrastructure-as-code projects. They should also review access logs for suspicious activity since September 2025, scan internal repositories for hardcoded secrets from Red Hat engagements, audit network configurations mentioned in consulting reports, and verify the integrity of systems referenced in Customer Engagement Reports.
Why are consulting firms particularly vulnerable to becoming credential aggregation points?
Consulting firms become high-value targets because their repositories contain secrets from dozens of organizations. When external consultants work across multiple customer environments, they aggregate credentials and infrastructure details in centralized systems. Based on GitGuardian's research, internal repositories contain 8-10x more secrets than public GitHub repositories, and consulting engagements frequently embed customer credentials in proof-of-concept code. This makes a single compromised consulting firm a gateway to hundreds of customer environments.
What enhanced security measures should organizations implement when working with consulting firms?
Organizations should implement strict credential hygiene policies for external engagements, use short-lived, least-privilege credentials for consulting projects, deploy continuous secrets monitoring across all repositories, implement comprehensive non-human identity (NHI) governance for service accounts and API keys, require consultants to use your secrets management solutions rather than hardcoding credentials, and establish clear incident response procedures with consulting partners. Additionally, deploy honeytokens in systems mentioned in consulting documents and avoid giving access to production environments during proof-of-concept phases when possible.
What does this breach reveal about supply chain security risks?
This incident demonstrates that a single compromised consulting firm can trigger a cascade of breaches across its entire customer base, highlighting the interconnected nature of modern cybersecurity risks. The breach shows how consulting firms serve as credential aggregation points, making them high-value targets that can provide attackers with access to hundreds of customer environments through lateral movement using harvested credentials. It emphasizes that supply chain security governance must extend beyond software dependencies to include service providers with infrastructure access.




![Shai-Hulud 2.0 Exposes Over 33,000 Unique Secrets [Updated Nov, 27]](/content/images/size/w600/2025/11/shai-hulud--2--1.png)




