Security engineers, are you tired of switching between multiple security tools to find and fix all sorts of vulnerabilities in your codebase? Kondukto and GitGuardian joined hands to provide you with an integration between both platforms, bringing together their knowledge in AppSec orchestration and automated secrets detection.
"GitGuardian is an excellent solution to detect secrets in your repositories. With Kondukto's integration, you can make it a part of your application security operations within a few minutes; create JIRA tickets to code committer or break the build if it doesn't match your security criteria."
Suphi Cankurt, Kondukto
GitGuardian's detection engine already helps organizations find and remediate hardcoded secrets at every step of the software development lifecycle. With the new integration, security engineers can view incidents detected by GitGuardian in their Kondukto Application Security Orchestration & Correlation (ASOC) dashboard alongside vulnerabilities detected by a SAST, DAST, SCA, and all sorts of other security scanners. This means security engineers can now easily access all the information they need in one place to take action and address issues quickly. No more juggling between 4 or 5 dashboards or tools!
Static and dynamic app testing are cornerstones for any comprehensive AppSec program. Yet, they rarely rise up to the challenges of fully securing modern software. Read on to learn why secrets are one of their critical blind spots.
Why you should connect GitGuardian and Kondukto
Centralizing GitGuardian's alerts in the Kondukto dashboard gives you a comprehensive view of your application security posture, enabling you to take a more holistic approach to de-risk your organization's software development lifecycle. Plus, the Kondukto open-source CLI, KDT, makes integrating and orchestrating security tests into your DevOps pipelines easy, streamlining your security without sacrificing speed or productivity.
With GitGuardian's engine continuously monitoring your code repositories, DevOps tools, and infrastructure-as-code configurations, you can be sure that no hardcoded secrets are slipping through the cracks. And when an incident occurs, Kondukto's ability to retrieve the alert and all corresponding metadata ensures a centralized, fast, and efficient resolution process.
Get started with GitGuardian and Kondukto
All it takes to get started is an API token issued by GitGuardian, for Kondukto to retrieve incident metadata and centralize it in the Application Security Orchestration and Correlation (ASOC) dashboard. With this integration, security teams can effortlessly scale their AppSec program and enhance their security posture without disturbing existing development processes.
Step 1 – Sign up for a GitGuardian account
Throughout this guide, we'll assume you already have a Kondukto workspace. If you don't, please get in touch with the Kondukto team to start your free trial.
Getting started with GitGuardian is easy. Signing up via your GitHub account is recommended, but you can also fill out the signup form with an email address and password. Visit https://dashboard.gitguardian.com/auth/signup to sign up.
Step 2 – Add your code repositories
Add at least one Version Control System (VCS) integration to detect hardcoded secrets. GitGuardian integrates with GitHub, GitHub Enterprise, GitLab, Azure Repos, and Bitbucket (server/data center).
Follow our documentation if you need help integrating your repos.
Once you have added your first repositories to your monitored perimeter, GitGuardian will run a first scan to unearth the secrets hiding in the commit history. From there on, it will continuously monitor new commits for secrets.
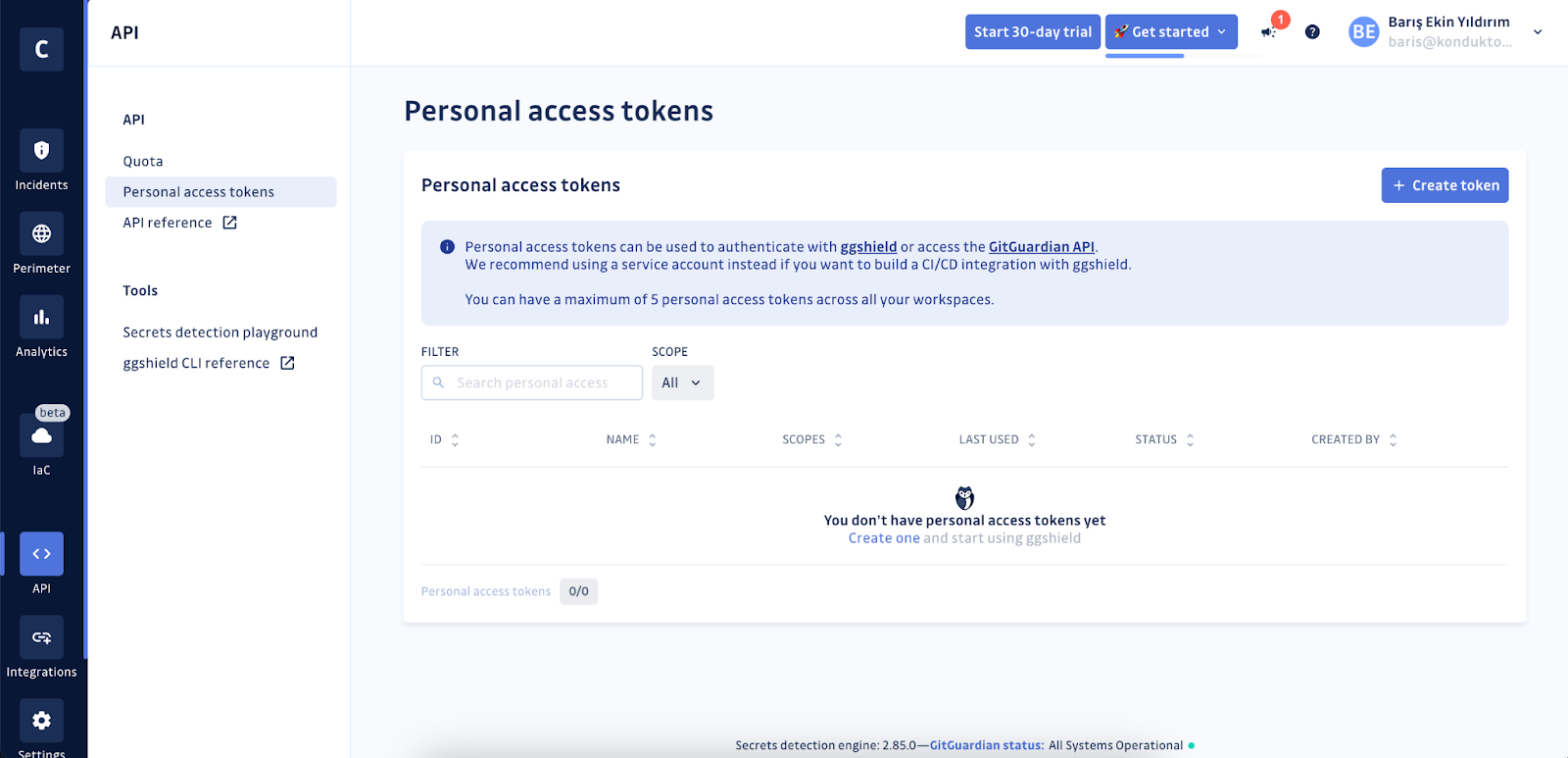
Step 3 – Generate an API key from GitGuardian
The integration requires the use of a read-only API token issued by GitGuardian.
- If you are on the GitGuardian Business plan, we recommend creating a dedicated service account for this integration.
- Otherwise, if you are on the Free plan, create a Personal Access Token (PAT).
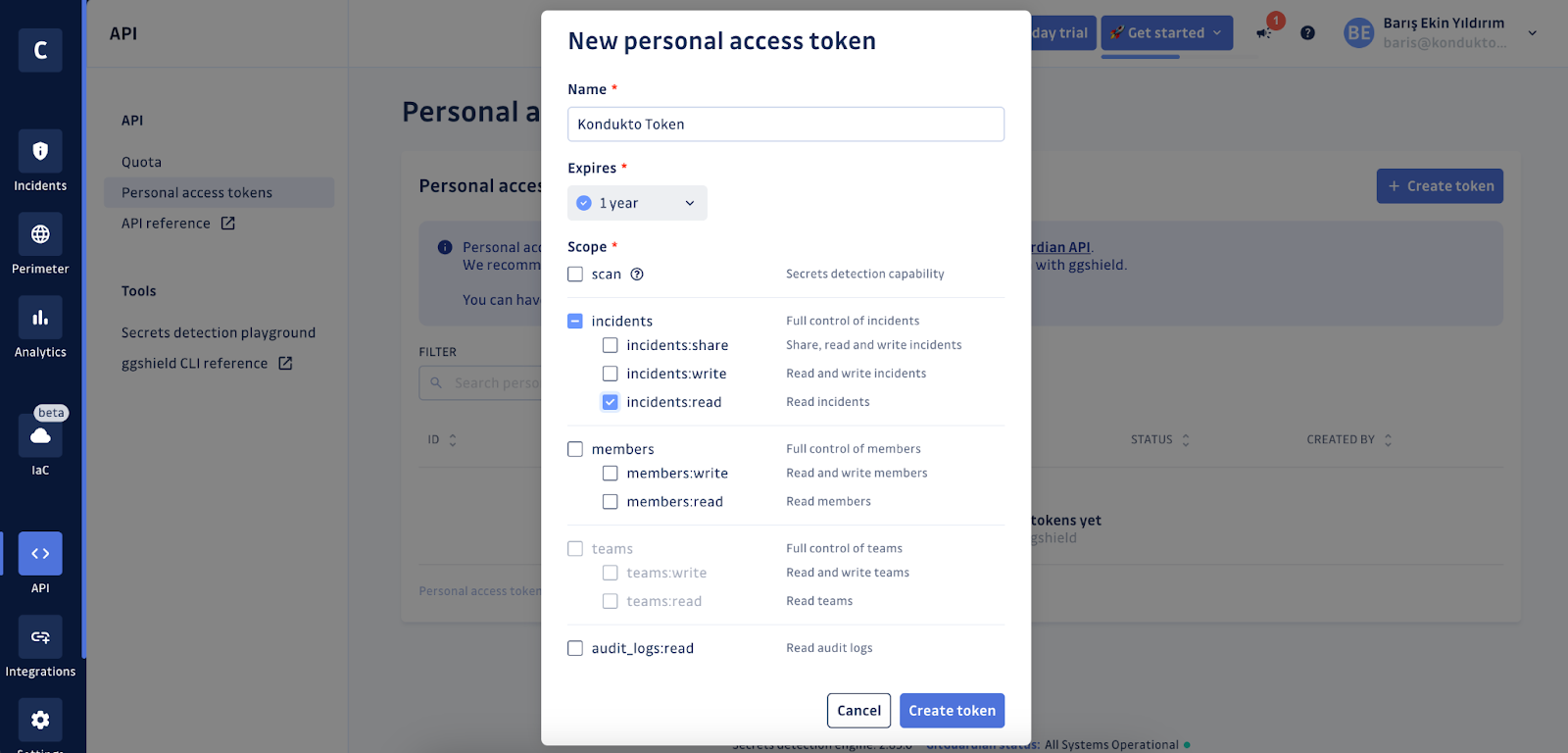
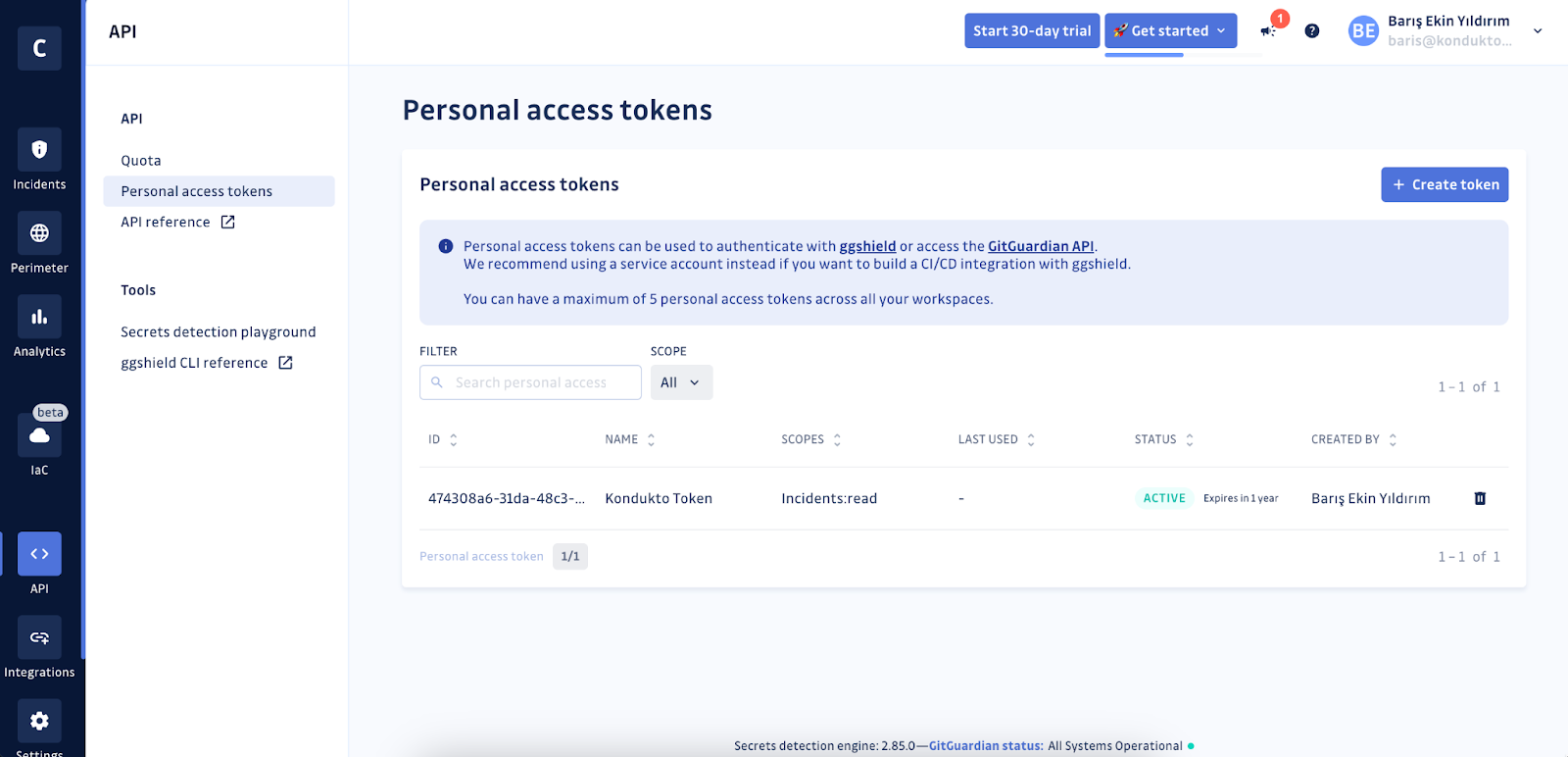
Step 4 – Connect GitGuardian and Kondukto
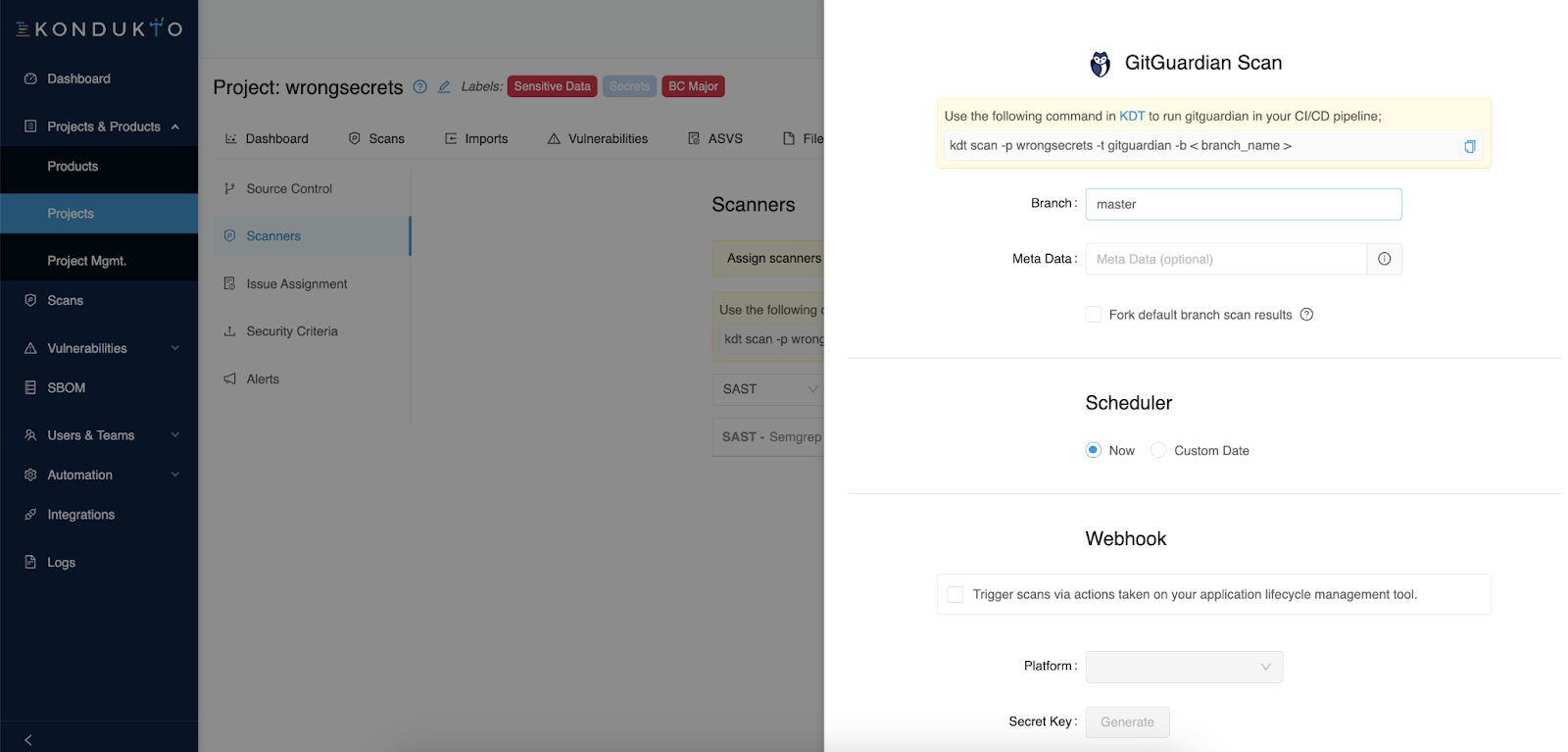
Once you have your GitGuardian API token, you can connect both platforms. Go to the Integrations section in your Kondukto dashboard and look for GitGuardian.
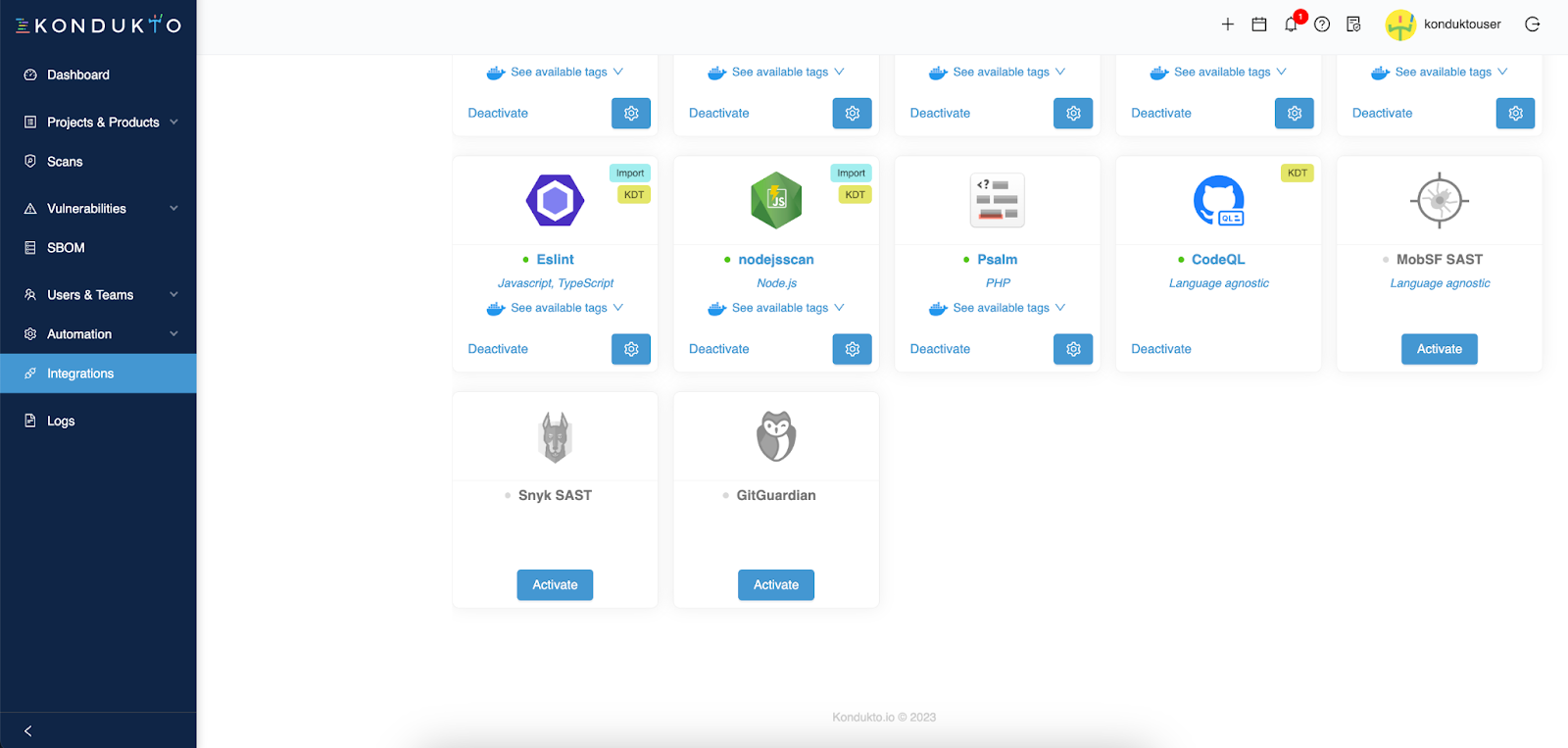
Now activate the integration. A side panel will open and ask you to input your GitGuardian API token.
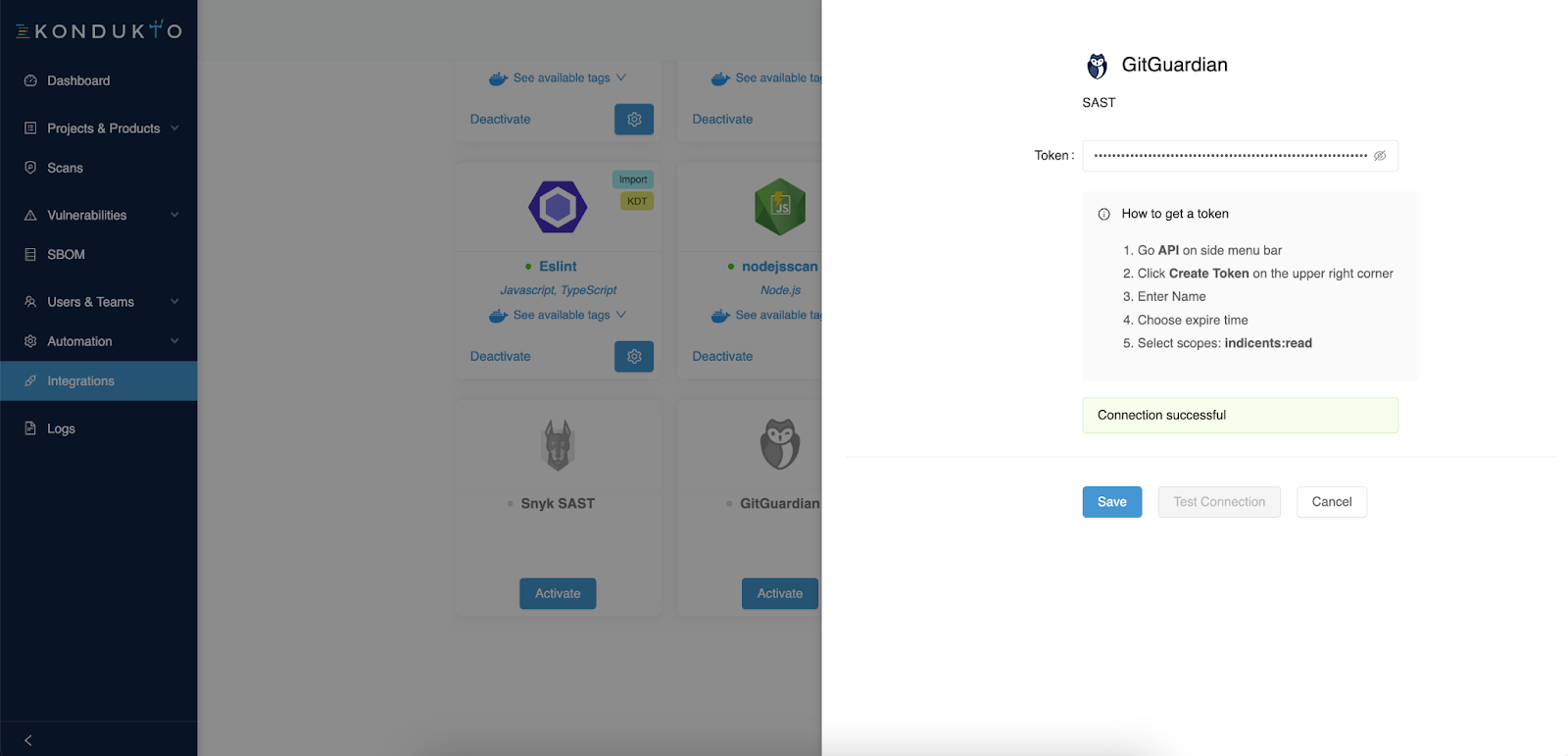
Now go to Projects and select one for which you want to add GitGuardian as a scanner. In our case, we have added a clone of the WrongSecrets repository from OWASP, a project featuring a vulnerable app with examples showing how not to use secrets (and which we are proud to sponsor at GitGuardian!).
Go to the project's settings and click on the Scanners tab. Follow the instructions below to add GitGuardian as a scanner to your project.
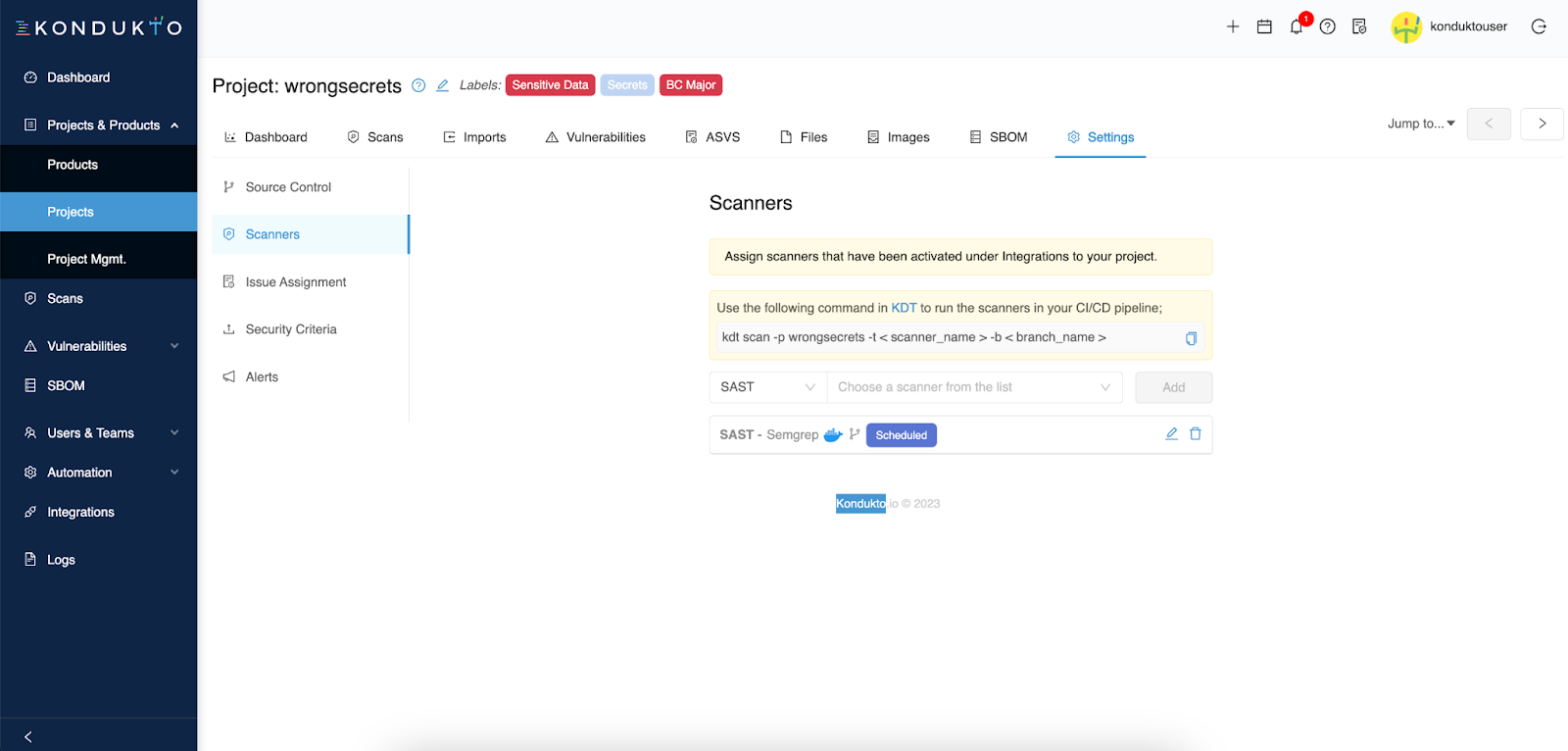
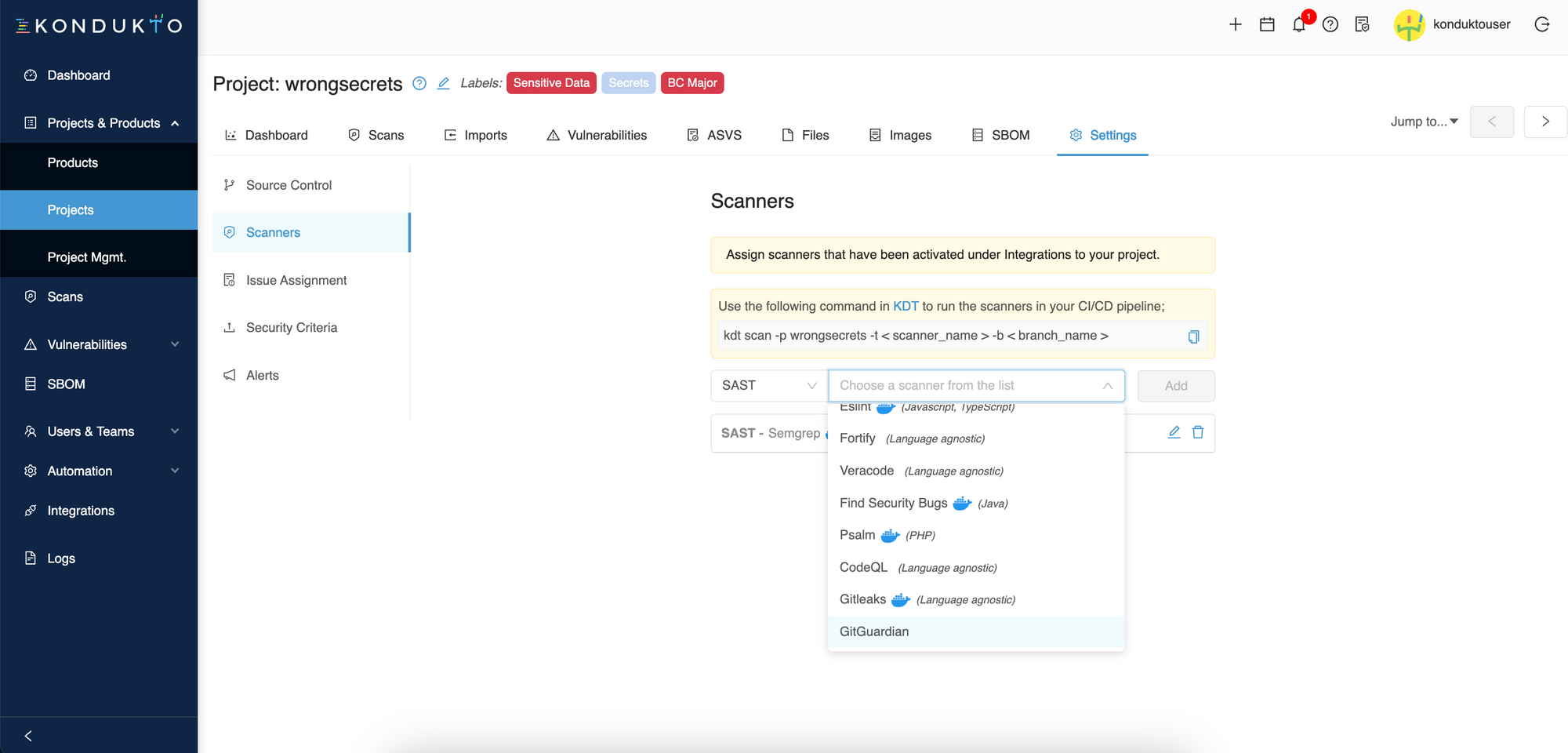
That's it!
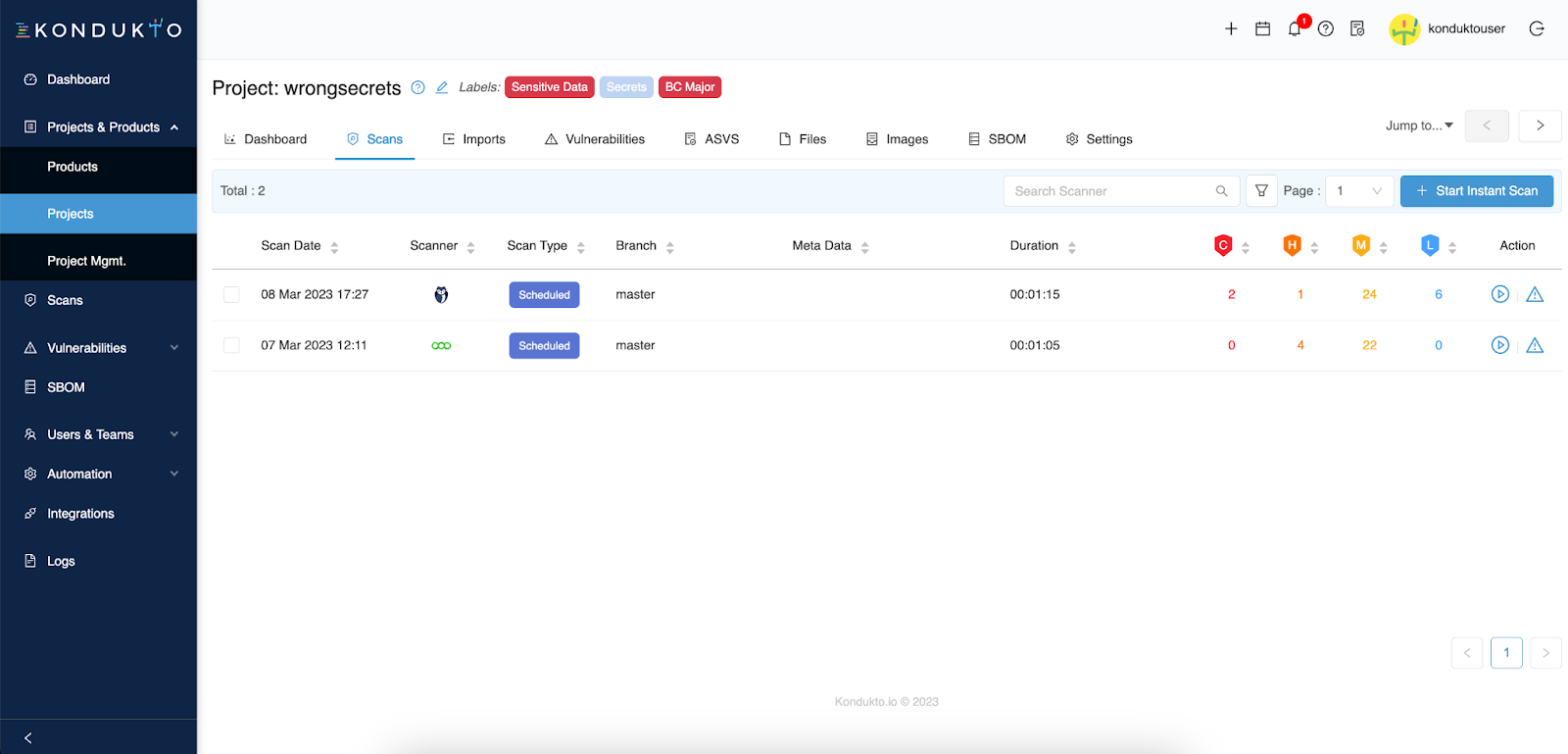
After setting up GitGuardian for your project, you can see it running alongside other existing scanners. In our case, we already had Semgrep SAST securing our WrongSecrets project.
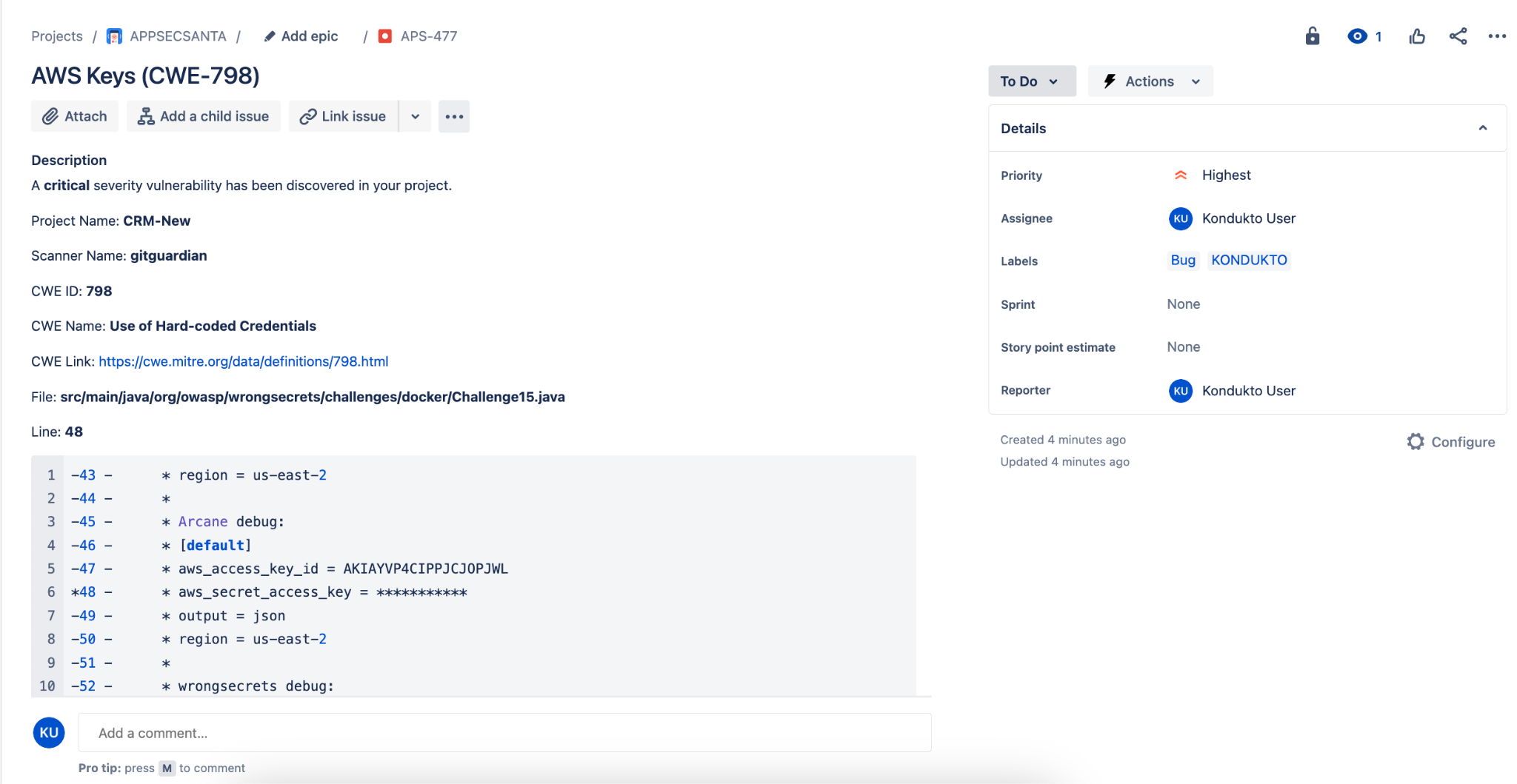
You can now view all the hardcoded secrets incidents GitGuardian picked up in your project from the vulnerabilities view and even inspect the details of any incident with metadata like the commit sha and commit author email, the location (branch, file, and line), the severity, and other tags (like "publicly exposed" or "from historical scan") for contextual remediation.
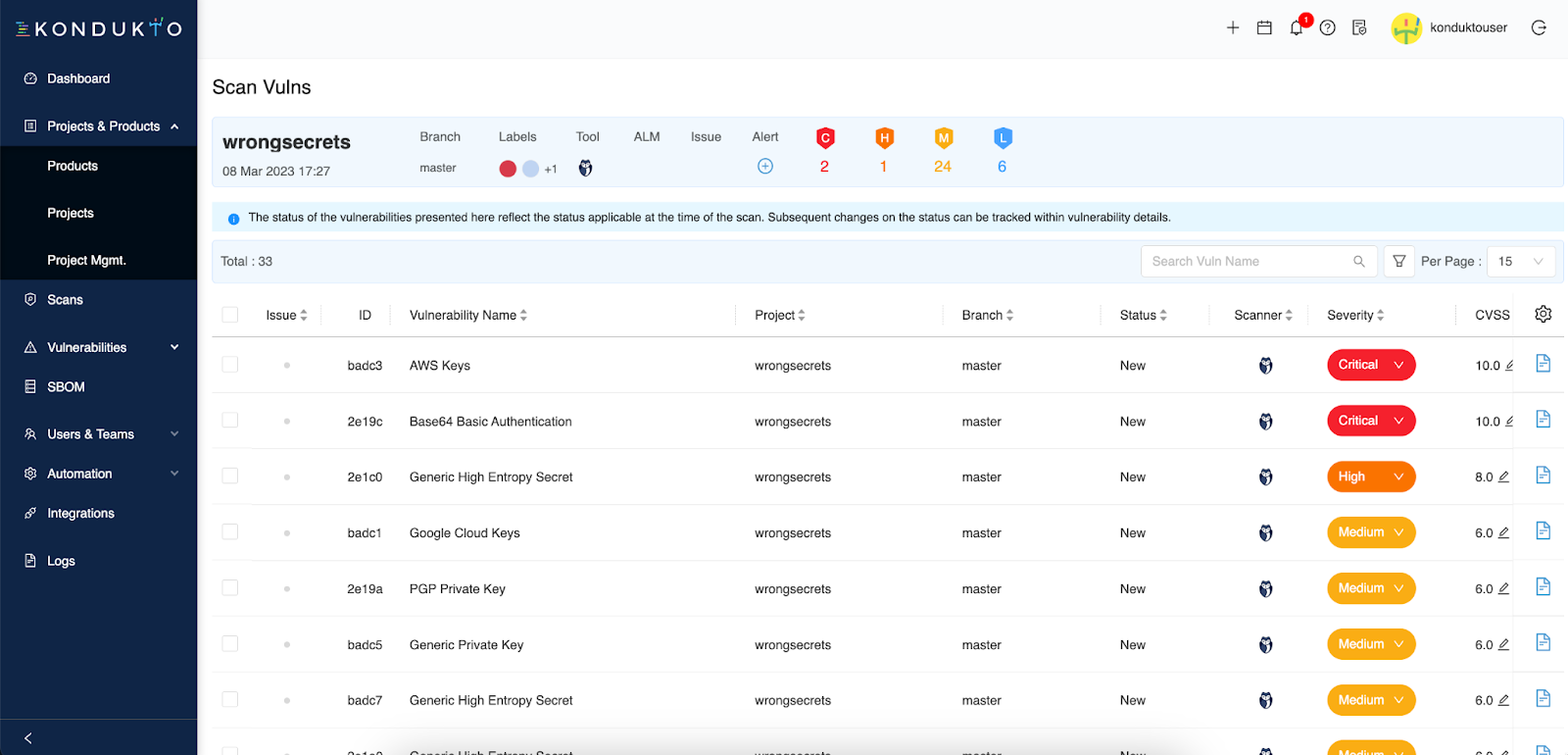
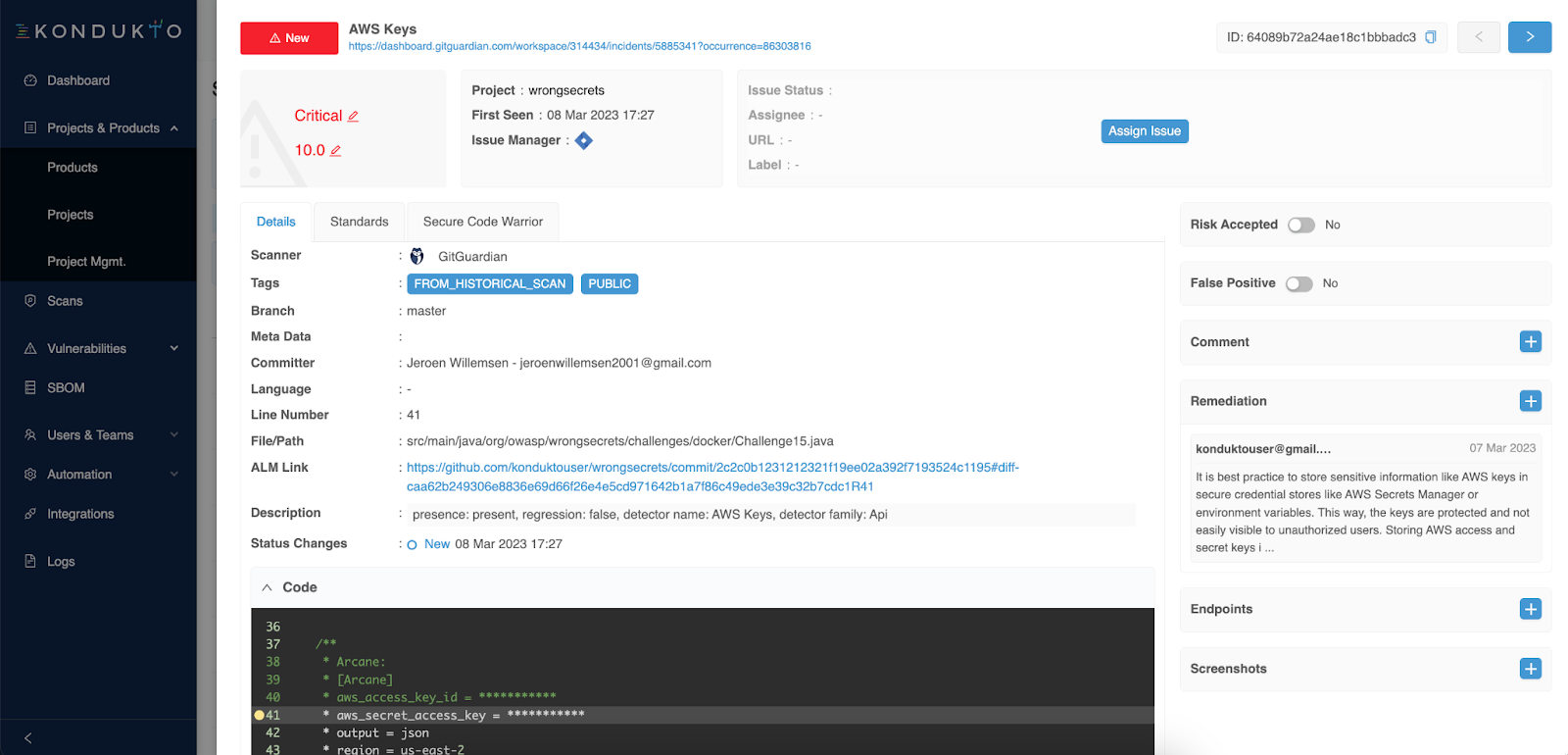
Step 5 – Orchestrate remediation workflows in Kondukto.
Lastly, if your security teams rely on Jira for incident management and response, Kondukto has you covered! You can configure your workspace to forward your hardcoded secrets incidents to Jira.
To do so, go to the Workflows section of your dashboard and click the Add Preset button.
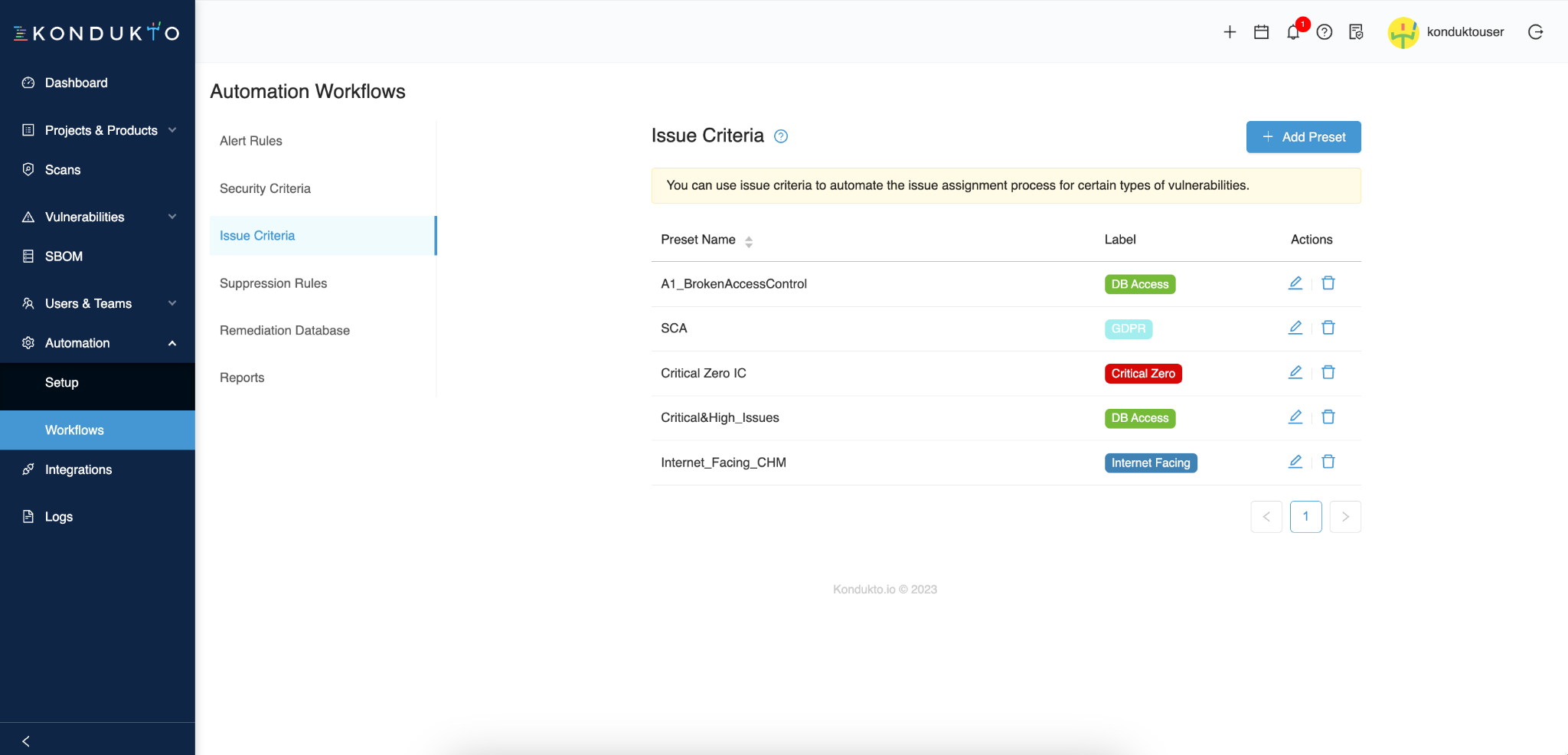
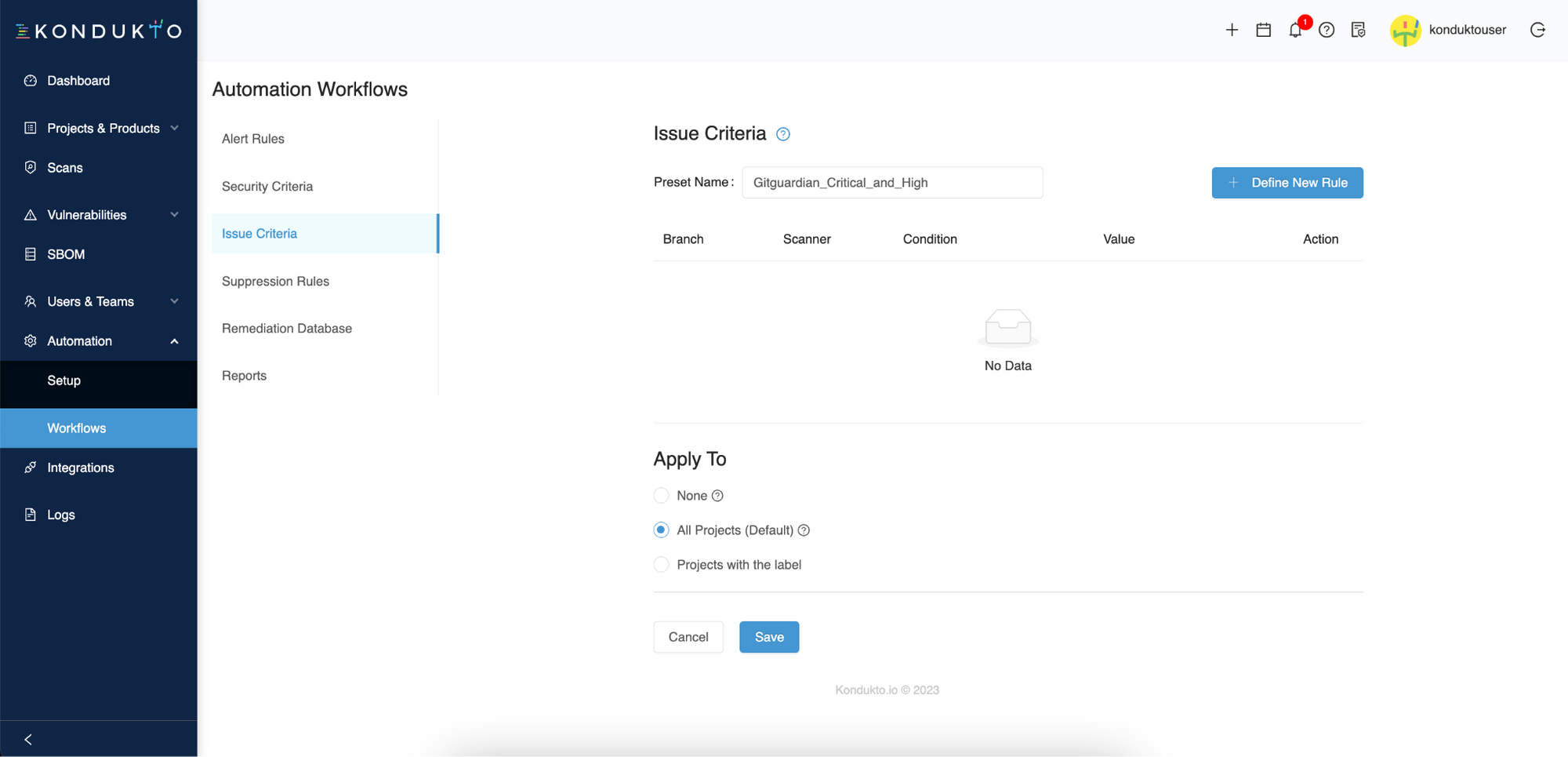
And you can even create filters only to create Jira tickets for incidents that respect a set of defined conditions, such as a severity equal to "critical" or "high". For this, click the Define New Rule button.
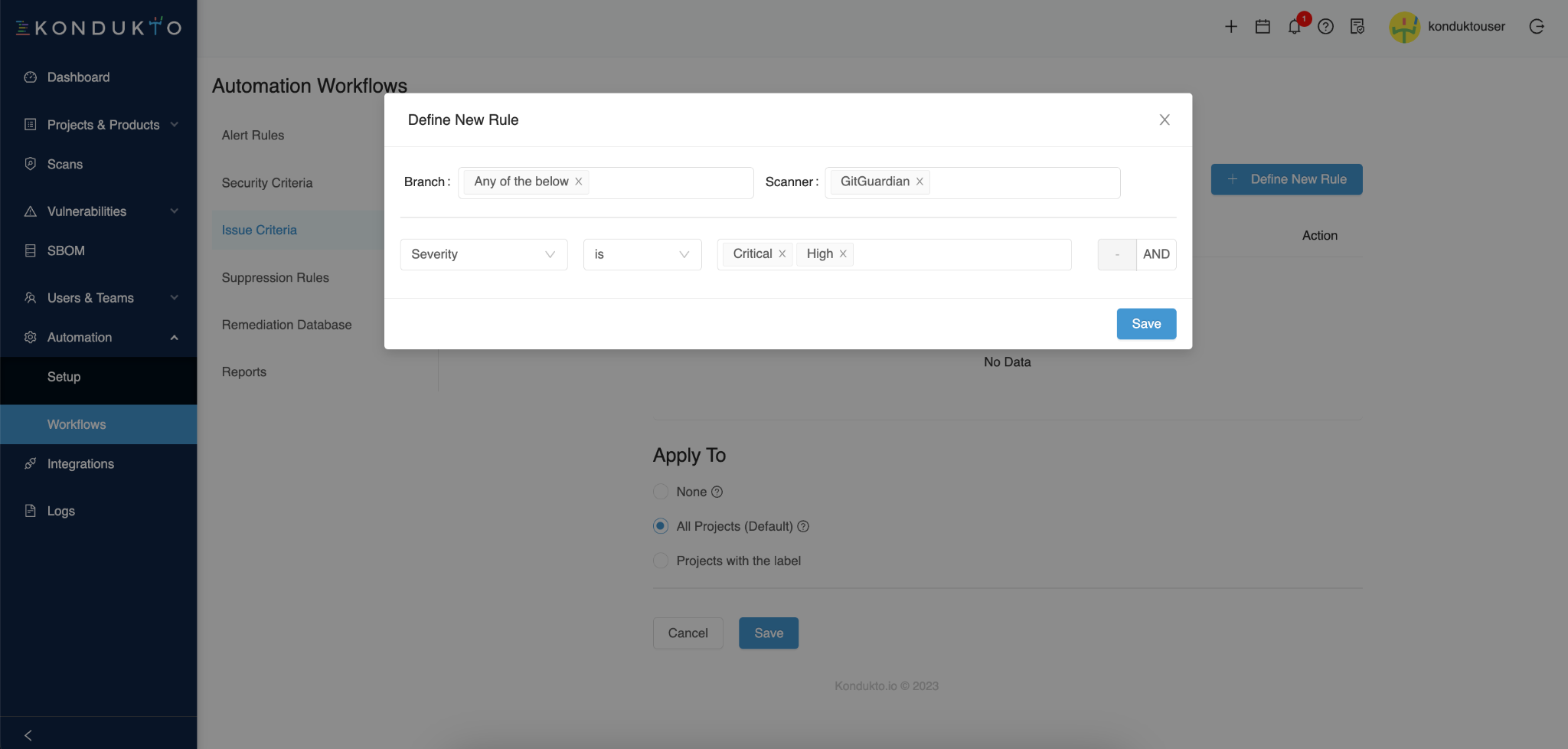
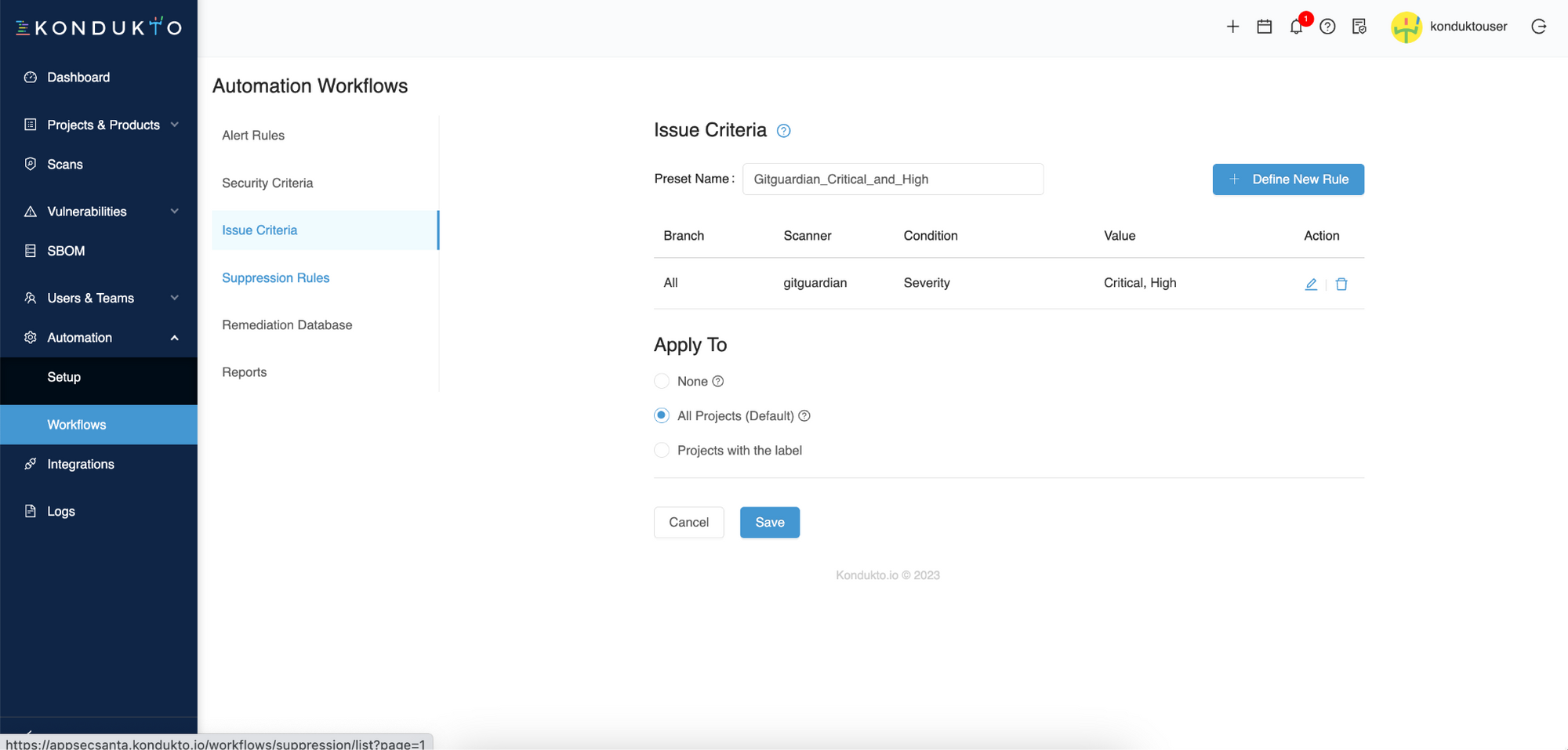
Finally, you can apply this automation to all projects monitored by GitGuardian, or only select projects to which you have attached a label beforehand.
Your automation is set!
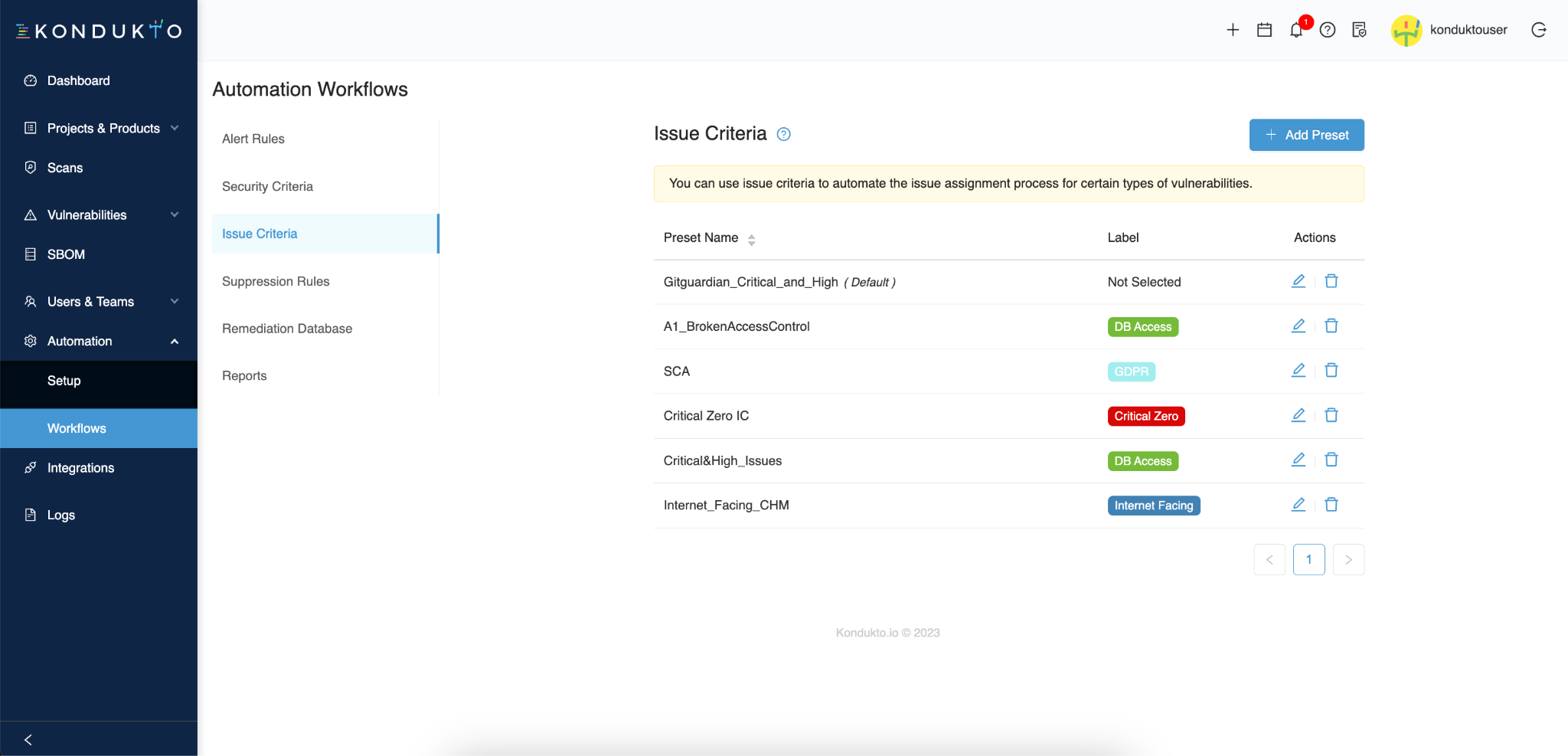
And you can now easily navigate from this…
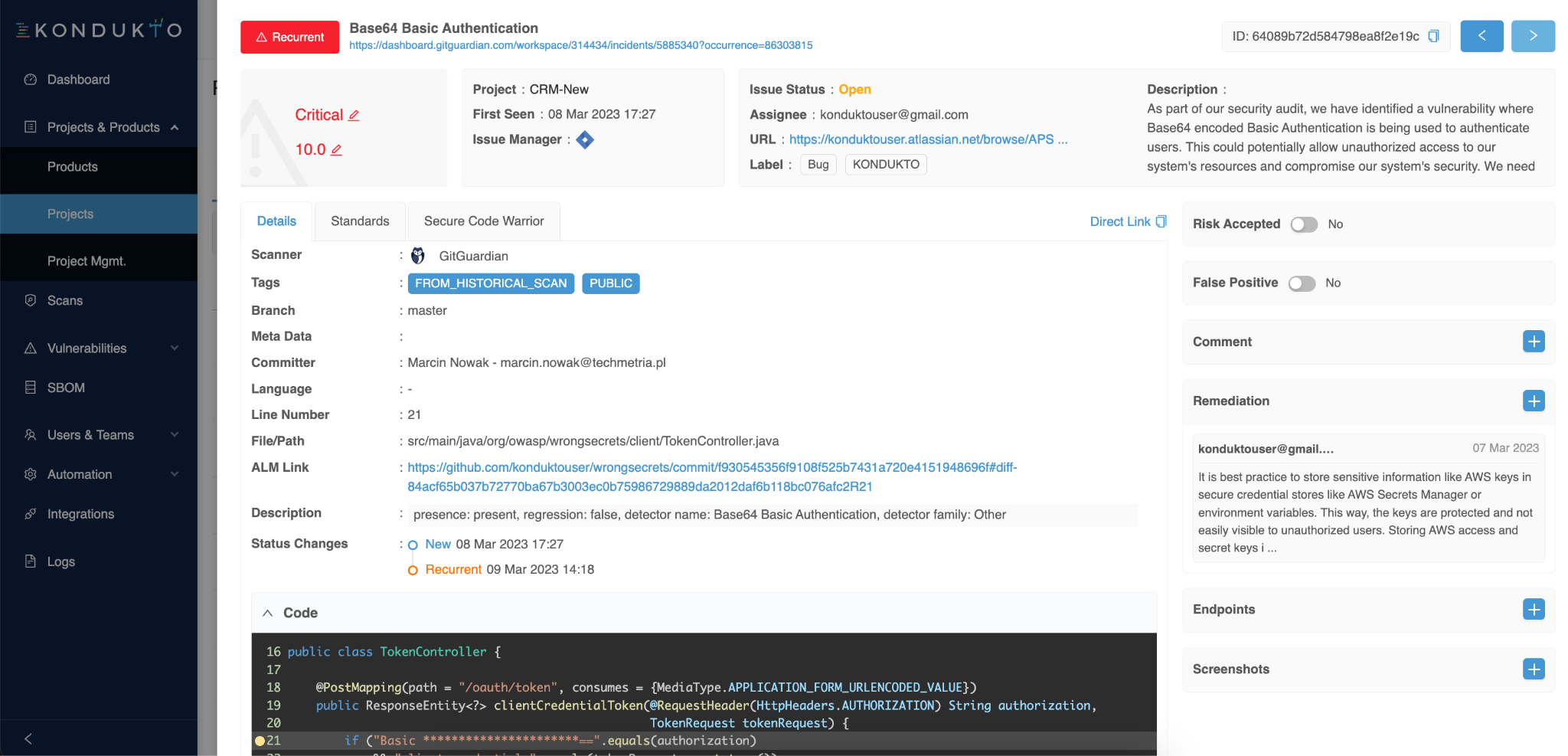
… to this!
Before you go!
Overall, the integration between GitGuardian and Kondukto will significantly benefit your security and development teams, including better visibility into security issues in your applications and faster remediation times. By bringing together two powerful tools in one platform, your teams can save time and effort while improving the security of the software supply chain across the board!
If you have any questions about the integration, GitGuardian, or Kondukto, email us at contact@gitguardian.com.