Nearly 200GB of source code from Samsung and the source code from Nvidia's latest DLSS technology has been published online by The Lapsus$ hacking group.
Internal source code being leaked online by adversaries is happening with alarming regularity in recent years. Only a few months have gone by since Twitch’s source code was leaked online which not only leaked income from the top streamers but as GitGuardian showed, also contain over 6,000 secret keys that attackers potentially could have used in further attacks.
GitGuardian scanned the leaked Samsung source code for sensitive information such as secrets and found that in the Samsung source code there were 6,695 secrets. This was during a scan that used over 350 individual detectors each looking for the specific characteristics of that specific type of secret which gives us reliably high accuracy results. In this case, we excluded results from generic high entropy detectors and generic password detectors as these can typically include false positives and therefore give inflated results. With that in mind, the true number of secrets could be much higher.
Disclaimers. Usually, GitGuardian would validate keys found in a repository to remove false positives. Because of the ongoing investigations that will undoubtedly be going on, GitGuardian decided not to validate any keys as not to mislead the forensics teams. This means we cannot give a percentage of the keys which were valid at the time of the leak.
As you can see from the snapshot of the results, the 8 top results account for 90% of the findings and whilst these are still very sensitive, can be more challenging for an attacker to use as likely refer to internal systems. That leaves just over 600 authentication tokens which grant access to a huge range of different services and systems that an attacker could potentially use to move laterally into more systems.
“Of the more than 6,600 keys found in Samsung source code roughly 90% are for Samsung's internal services and infrastructure, whilst the other 10%, critically, could grant access to Samsung's external services or tools such as AWS, GitHub, artifactory and Google” Mackenzie Jackson Developer Advocate GitGuardian
This is very much in line with what you would expect from a company of this size and actually is better than the average amount of secrets we generally find when a comparable organization does an initial scan. A recent report from GitGuardian showed in an organization with an average of 400 developers over 1,000 secrets are found within internal source code repositories (Source State of Secrets Sprawl 2022). If such secrets are leaked it could affect Samsung's ability to securely update phones, grant adversaries access to sensitive customer information or allow them to access Samsung's internal infrastructure with the potential of launching further attacks.
“These attacks are publicizing a problem many in the security industry have been sounding the alarm for, internal source code contains an increased amount of sensitive data yet remains a very leaky asset. Source code is widely accessible by developers throughout the company, backup onto different servers, stored on developers' local machines and even shared through internal documentation or messaging services. This makes it a very attractive target for adversaries which is why we are seeing a persistence in the frequency of these attacks are occurring”. - Mackenzie Jackson Developer Advocate
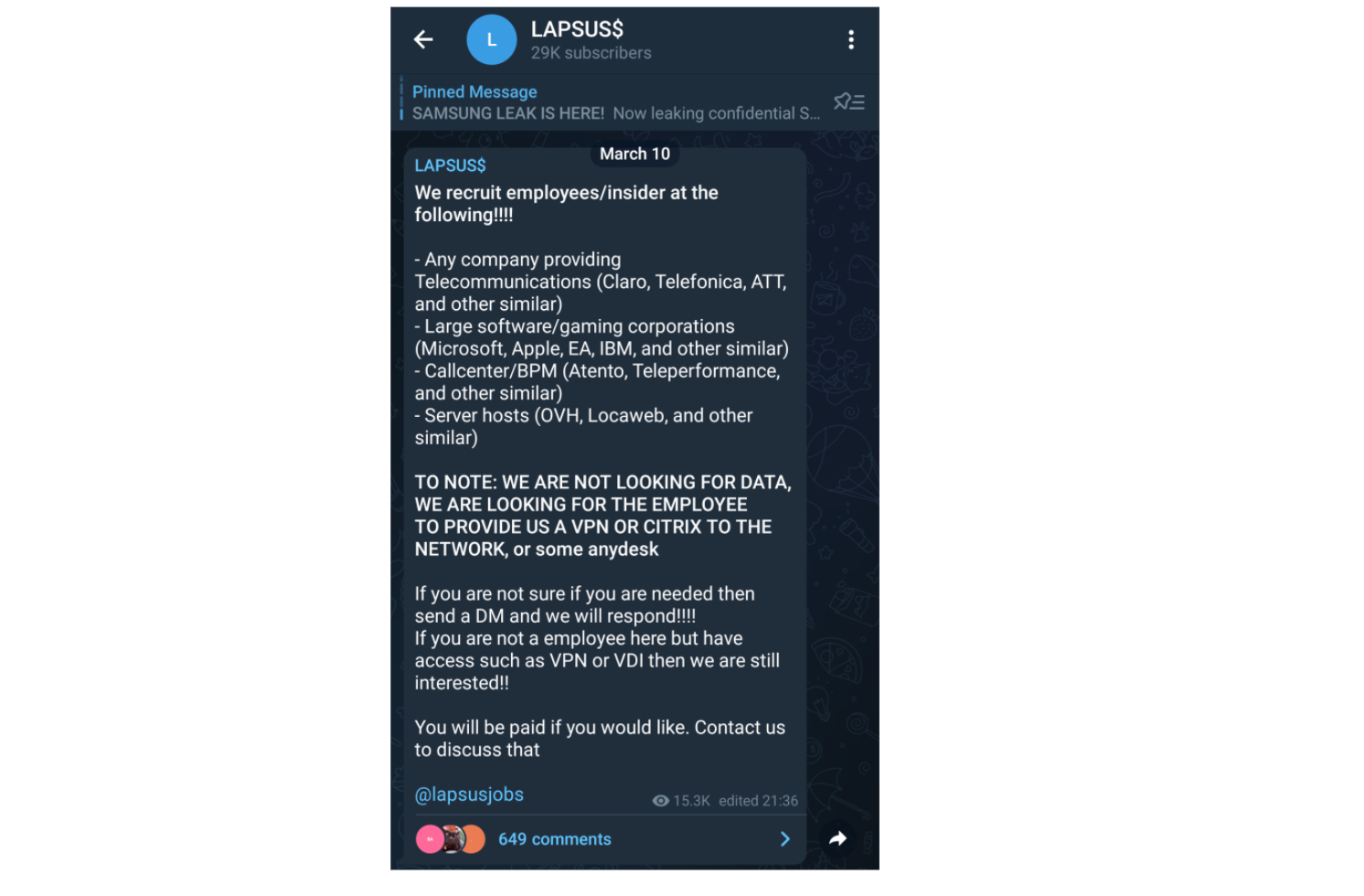
On the Lapsus$ telegram channel, we can get a hint at how the hacking group is actually gaining access to these repositories sending out what is essentially a call to action from employees of large organizations to grant them access.
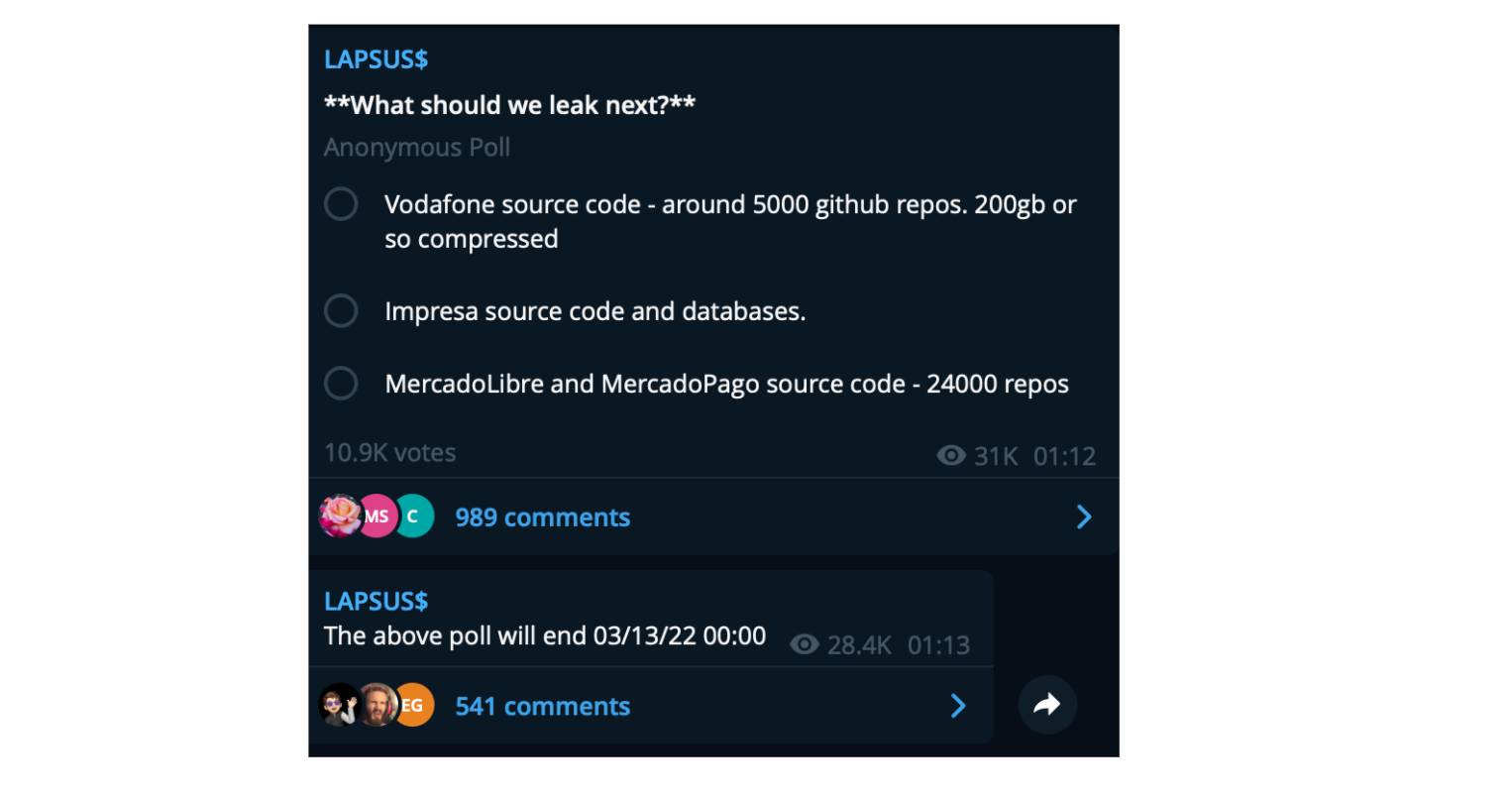
Unfortunately, I do not believe we are at the end of seeing attacks like this, the group now sharing polls, again through their telegram channel asking followers what source code should they leak next indicating many more leaks of internal source code are likely to come in the future.
Read more on why source code in internal repositories is such a problem in GitGuardian’s State of Secrets Sprawl Report