It's time to stop hardcoding secrets in Git repos
The year is 2022, and secrets in Git repositories are still causing headaches for security engineers around the world. If you're a long-time GitGuardian follower, you already know how committed we are to fighting secrets-in-code with our tutorials, webinars, videos, and reports. This time, we decided to team up with @sec_r0 to raise awareness around the risks of hardcoding secrets, with the help of a drawing!
If you enjoyed reading this zine, spread the word and share it around!
For a thorough technical analysis on how the SUNBURST malicious code was inserted into Solarwinds Orion Platform software, you can refer to this report from CrowdStrike’s intelligence team.
Want to learn more about secrets sprawl?
Here's everything you need to go down the rabbit hole.
Understanding secrets sprawl


Best practices around secrets management and detection



More Git tutorials and cheat sheets!



I hope these resources will help you keep secrets out of your Git repositories in the future. Don't forget to bookmark them and share them with your developer friends and colleagues!
Read the next Zine
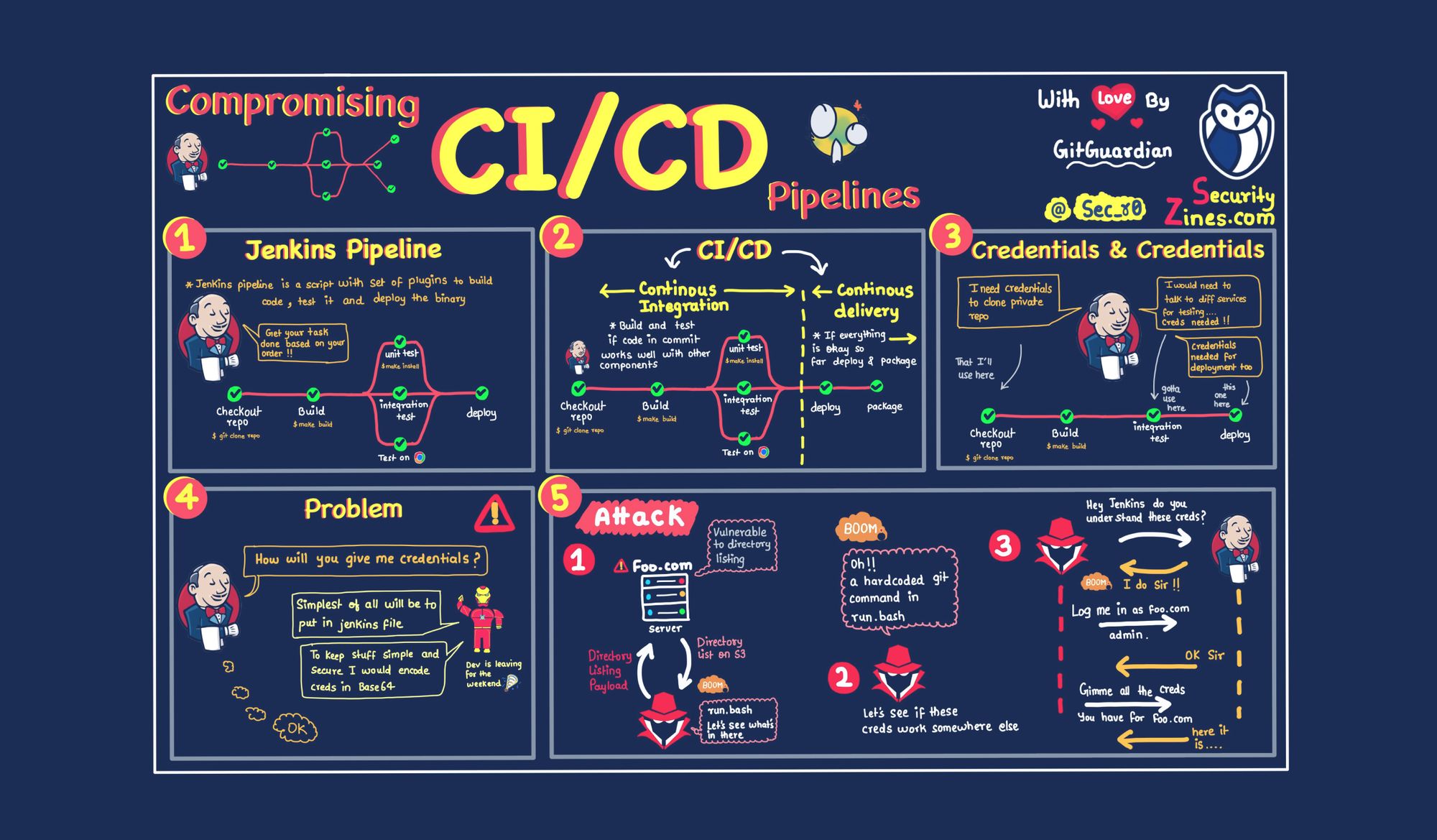


![Secrets in Git Repos [Security Zines]](/content/images/size/w2000/2022/03/22W10-blog-securityzines-1-1.jpg)


![Precision & Recall [Security Zines]](/content/images/size/w600/2024/10/Recall-in-Detection.png)

![Honeytokens [Security Zines]](/content/images/size/w600/2024/09/Honeytokens.png)
![Software Composition Analysis [Security Zines]](/content/images/size/w600/2024/05/SOPS-Security-Zine--1-.png)
![SOPS [Security Zines]](/content/images/size/w600/2024/03/SOPS-Security-Zine.png)
