Two critical zero-day vulnerabilities in Microsoft SharePoint have been actively exploited since July 7, 2025, targeting government agencies and technology firms worldwide. The vulnerabilities, tracked as CVE-2025-53770 and CVE-2025-53771, allow unauthenticated attackers to execute arbitrary code on on-premises SharePoint servers through deserialization of untrusted data.
What Happened
Security researchers first observed large-scale exploitation of this SharePoint flaw on July 18, with dozens of compromised servers identified globally. The vulnerability affects on-premises Microsoft SharePoint servers and enables attackers to gain full administrative access without authentication, execute malicious code, and maintain persistent access to targeted systems. Microsoft rushed an emergency out-of-band security update on July 19 to address the critical flaw.
The Hidden Secrets Problem
While the immediate focus has been on patching the vulnerability, organizations must also consider what sensitive information may have been exposed during these attacks. SharePoint environments often serve as repositories for far more than just documents—they frequently contain a treasure trove of hardcoded secrets that attackers can leverage for further compromise.
"SharePoint is extensively used for internal documentation containing code snippets where users often leave credentials," explains Philippe Gablain, Engineering Manager at GitGuardian. "Some teams also share spreadsheets containing credentials (the infamous passwords.xlsx) which is the total anti-pattern."
This reality makes the SharePoint zero-day particularly dangerous from a secrets security perspective. API keys, database passwords, service account credentials, and authentication tokens stored in SharePoint documents become immediately accessible to attackers exploiting this vulnerability.
Comprehensive Secrets Detection Across All Platforms
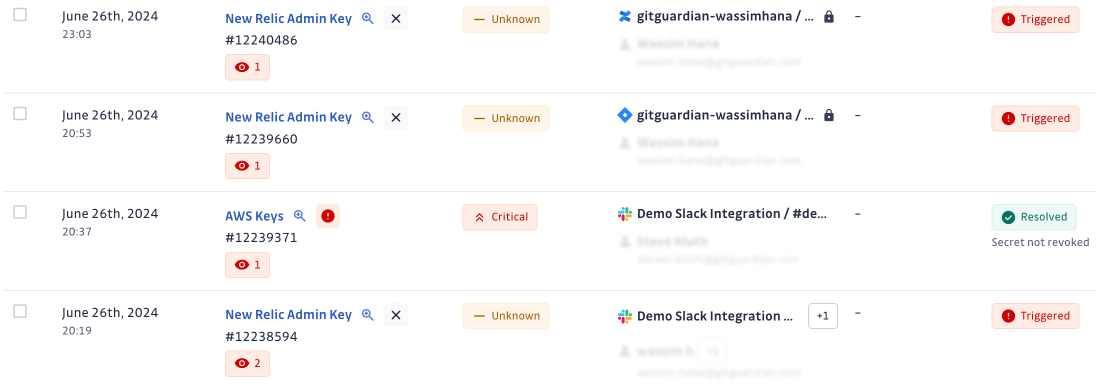
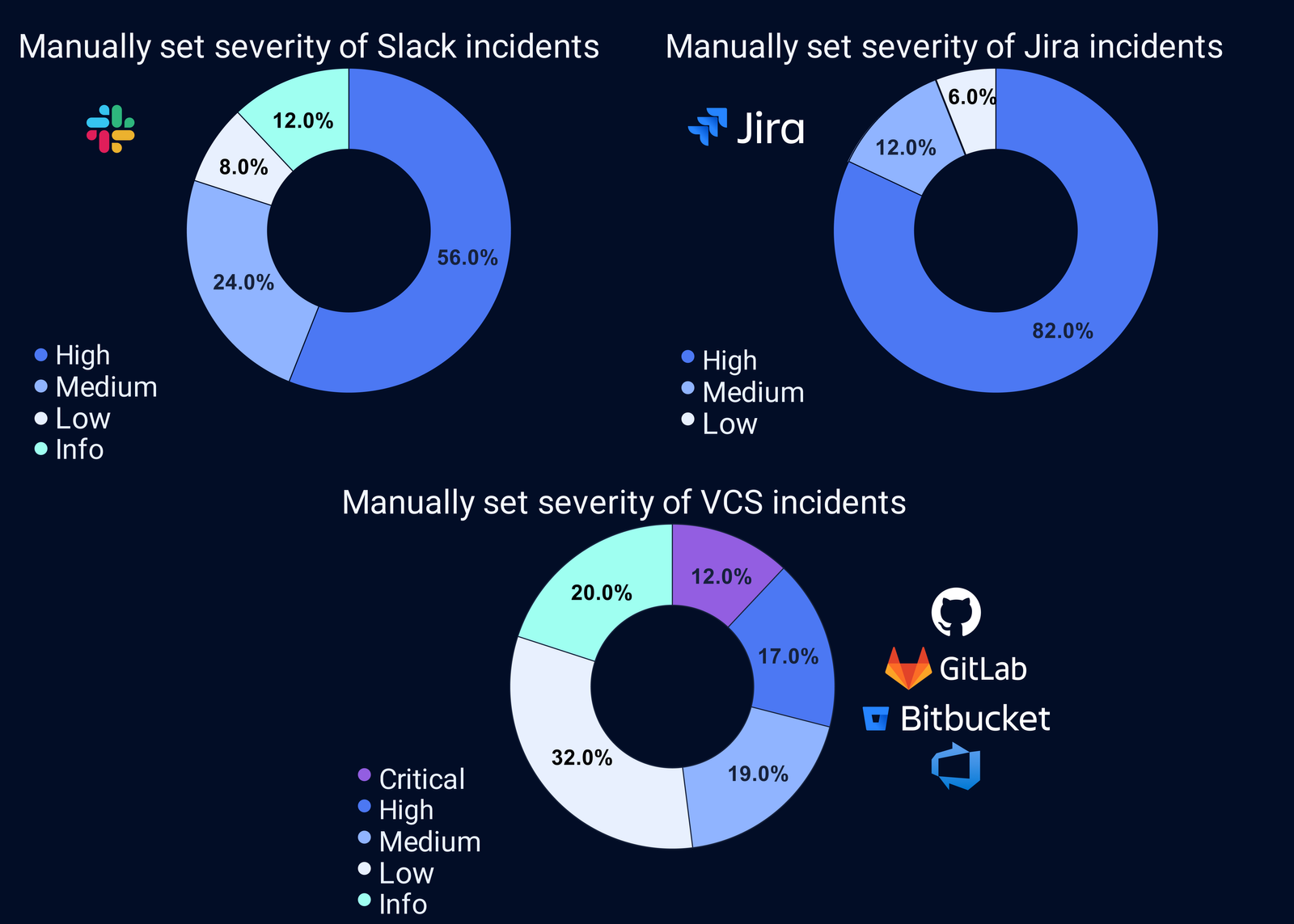
At GitGuardian, our research reveals a surprising trend: some users leak more secrets within their collaboration tools than in their source code. More concerning, the secrets found in collaboration platforms like Slack and Jira often have higher severity levels than those in version control systems, indicating teams are less cautious when using these tools.
Comprehensive Secrets Detection Across All Platforms
This reality is why GitGuardian has expanded beyond traditional code scanning to detect secrets in PDFs, Word documents, Excel spreadsheets, and other file formats. In addition to SharePoint, our platform integrates with Slack workspaces, Microsoft Teams tenants, Jira Cloud and Data Center, and Confluence Cloud and Data Center sites.