Making Sense of Open-Source Vulnerability Databases: NVD, OSV, and more
Essential reading for developers and security professionals alike: a comprehensive comparison of vulnerability databases to help you cut through the noise.

Essential reading for developers and security professionals alike: a comprehensive comparison of vulnerability databases to help you cut through the noise.
![Software Composition Analysis [Security Zines]](/content/images/size/w600/2024/05/SOPS-Security-Zine--1-.png)
For those feeling code-conscious about shady dependencies lurking in their apps, Software Composition Analysis is the software security wellness check you need!
SBOMs are security analysis artifacts becoming required by more companies due to internal policies and government regulation. If you sell or buy software, you should know the what, why, and how of the SBOM.
Typosquatting and dependency confusion are two common tactics used by hackers to exploit open-source package repositories. Understand how these attacks work and discover preventive measures to secure your infrastructure.
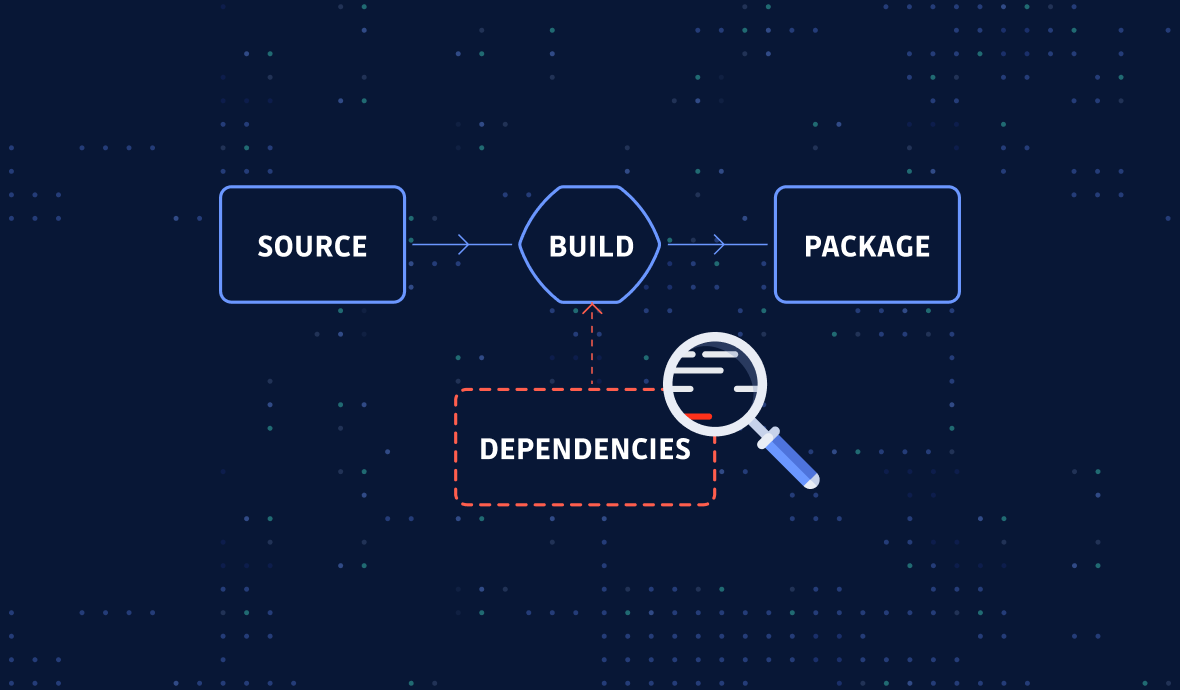
Software composition analysis is an essential part of application security. Here are the important factors to consider when selecting an SCA scanner to be sure it is well-suited to your needs.

Learn more about what is a Software Bills Of Materials, why use it, what are the standards and how to automate it with Continuous Integration.