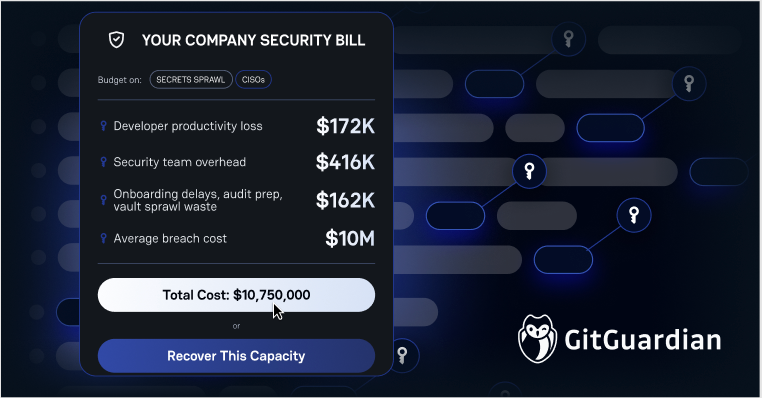
Your developers are probably making you lose more money than you think. Not through bad code or failed deployments, but through something much more mundane: managing secrets manually.
If you've got at least 10 developers on your team, you're likely losing over $172,000 annually just from the time they spend wrestling with API keys, database credentials, and access tokens. That's according to recent research from HashiCorp. They calculated 3 hours per week per developer at $120/hour fully-loaded costs, and honestly, it matches what we're seeing across the industry.
But here's the thing: that's just the tip of the iceberg.
The Problem Nobody Talks About
Here's what's happening in most organizations: secrets are everywhere. They're in repos, CI/CD pipelines, production environments, and about a dozen other places. Every time a developer needs to use one, they have to figure out where it lives, whether it's still valid, and how to reference it properly.
Security teams aren't having a better time. They're spending an average of 25 minutes investigating each secret alert that comes in. With hundreds or thousands of these alerts per year, that adds up fast. Over 80% of these alerts turn out to be false positives or require extensive manual digging to understand.
Where The Money Goes
Alert Investigation Overhead
Let's do some quick math. If you're processing 1,000 secrets alerts per year (which isn't unusual for a mid-sized company), and each one takes 25 minutes to investigate, that's over 400 hours of analyst time. That's a quarter of someone's entire year spent on manual triage.
One of our customers, a major cloud infrastructure company, cut its triage time in half by using “vaulted” status as a key prioritization factor. When they discovered exposed secrets, they could immediately distinguish between those with existing security controls (rotation, monitoring, access policies) and those that were completely unmanaged. This context allowed their security team to focus first on the highest-risk exposures - typically unvaulted secrets with broad permissions - while still addressing vaulted secrets that had been inadvertently exposed.
Another approach, focused on quick wins, can be to prioritize vaulted secrets first. The rationale: if a secret is already in a vault, it's a strong indicator that it's a valid, actively-used credential rather than test data or deprecated keys. Additionally, the remediation effort is often simpler - the secret path already exists, rotation mechanisms are likely in place, and the development team already has established workflows for that credential. This can deliver faster incident closure rates and immediate risk reduction.
Developer Productivity Drain
The HashiCorp study found that developers lose about 3 hours per week to secrets management. That works out to roughly $17,200 per developer per year in lost productivity. They're waiting for DevOps teams to provision secrets, hunting for the right references, and coordinating with security during incident response. While the precise monetary value may vary based on regional salaries and team efficiency, this figure powerfully illustrates the massive opportunity cost when developers are blocked by manual processes.
A large cybersecurity company we work with eliminated most of this wait time by giving developers direct access to vault references. Instead of filing tickets and waiting, developers could provision unvaulted secrets into a vault directly themselves. Cut the friction time in half.
The Onboarding Tax
Here's something most people don't factor in: new developers take 2-3 weeks longer to become productive when secrets management is complex. They need to learn different processes for different systems, figure out who has access to what, and understand the various workarounds that teams have built over time.
One company told us they were spending roughly 40 hours per new hire just on secrets-related training and setup. With developer turnover rates what they are, that adds up quickly.
The Breach Window Problem
IBM research shows that breaches involving stolen credentials take an average of 292 days to contain. Every unmanaged secret sitting in your environment extends that window. With the average data breach costing nearly $10 million in the US, this isn't just an operational efficiency problem. It's a business risk.
A UK fintech company told us something interesting:
"For the first time, I can show executives that Team A has 40% of leaked secrets outside vaults, while Team B is at 5%. This made the problem tangible for management."
But the real cost comes during incident response. When you discover a compromised secret at 2 AM, how long does it take to figure out which systems are affected? One customer spent 18 hours during a weekend incident just mapping the blast radius of a single leaked API key.
The Audit Trail Nightmare
If you've been through a SOC 2 or PCI DSS audit lately, you know this pain. When auditors ask, "Show me all systems that had access to this database," how long does it take to answer?
One customer spent three weeks preparing for their SOC 2 audit, just gathering secrets documentation from different teams and systems. Companies fail their first PCI assessment because they can’t demonstrate proper secrets lifecycle management across their environment.
Vault Sprawl Hidden Costs
Most organizations run multiple secrets management tools. Maybe you acquired another company. Maybe different teams chose different solutions. Maybe you just never got around to standardizing.
This creates redundant licensing costs and operational complexity. Without a unified view, you can't tell which vaults are actually being used and which ones you could decommission. We've seen companies paying for five different secrets management solutions when they only needed two.
What Good Looks Like: 1.2 FTE Recovered
Noise Reduction (0.25 FTE saved): Automatically distinguishing real problems from false alarms saves over 250 hours of analyst time per year.
Faster Remediation (0.6 FTE saved): Giving developers direct vault references and self-service provisioning recovers 500+ hours of productivity annually.
Better Governance (0.1 FTE saved): Reducing the breach exposure window and streamlining compliance reporting.
Vault Consolidation (0.2 FTE saved): Direct licensing savings plus reduced operational complexity.
Total: about 1.2 full-time employees' worth of capacity recovered per year.
Real Examples From The Field
A major software platform provider uses vault integration specifically to reduce investigation time. They can automatically separate vaulted from non-vaulted secrets, which lets their team focus first on the secrets that are definitely problematic.
An enterprise software company considers its vault integration a success because it helps them identify which leaked secrets are likely to be valid.
A manufacturing technology company is particularly interested in secret rotation. They want to be able to rotate secrets directly from their security platform because it would simplify the entire process for their developers.
The Innovation Velocity Impact
Here's something that doesn't show up in most ROI calculations: how manual secrets management slows down everything else.
When developers spend hours wrestling with access credentials, they're not building features. When security teams are buried in false positive alerts, they're not working on strategic initiatives. When new team members take weeks to get productive, your time-to-market suffers.
One customer told us that streamlining secrets management was the single biggest factor in reducing their deployment cycle time from weeks to days. Not because secrets were the bottleneck, but because fixing secrets management eliminated dozens of smaller friction points throughout their development process.
More Data
Looking at a sample of 15 organizations we've worked with, here's what the numbers show:
- Only 1-3% of secrets incidents involve secrets that are already in a vault
- Typically, 10-15% of secrets in an organization's vault inventory will generate security incidents
- 70-80% of vaulted secrets have other issues:
- 62% are duplicated across multiple secret managers
- 25% have been around too long
- 18% are being used in multiple environments inappropriately
About Those $172,000 Numbers
You might be thinking that $172,000 for 10 developers sounds high. Let's break it down: that's $17,200 per developer, based on 3 hours per week at typical senior developer rates.
But the cost could in fact be higher because:
- The calculation doesn't include opportunity costs (the strategic work that doesn't happen)
- Context switching and coordination overhead aren't fully captured
- 3 hours/week may be underestimated for very complex environments
- Senior developers in some markets cost significantly more than $120/hour
If these numbers seem off for your organization, track actual time spent on secrets-related tasks for a few weeks. You might be surprised by what you find.
The Scale Problem
Everything we've talked about gets worse as you grow.
A 10-person startup with manual secrets management is inefficient. A 100-person company with the same approach is dysfunctional. A 1000-person company is actively dangerous.
The coordination overhead grows exponentially. More teams, more systems, more environments, more compliance requirements. What started as a small productivity tax becomes a strategic competitive disadvantage.
What's Next: Beyond Basic Secrets Management
Secrets management is evolving beyond simple vault integrations. The next step is comprehensive governance of non-human identities and their secrets. Once you know where your secrets are, you need to understand who owns them, what workloads use them, and whether they have appropriate permissions.
This includes:
- Complete mapping of all machine identities
- Automated lifecycle management from provisioning to deprovisioning
- Continuous access reviews for machine accounts
- Risk-based prioritization for remediation efforts
Getting Started
If you're ready to tackle NHIs and their secrets sprawl:
- Audit your current state: Figure out how many secrets managers you're running and how many alerts you're processing
- Measure the baseline: Track how much time your teams actually spend on manual secrets tasks
- Start with high-impact automation: Vault integration and automated triage usually provide the biggest immediate wins
- Plan for the bigger picture: Think about how secrets governance fits into your broader identity and access management strategy
The cost of doing nothing keeps growing. Organizations that get ahead of this problem will recover significant operational capacity and strengthen their security posture at the same time.
If you want to see what this looks like in practice, consider running a three-month pilot with GitGuardian to measure the specific impact in your environment.