This supply chain attack combines credential theft, environmental sabotage, and novel attack vectors, offering a glimpse into future threats. The malicious Nx packages systematically scanned infected systems for valuable credentials, including GitHub tokens, npm authentication keys, SSH private keys, environment variable API keys, and cryptocurrency wallet files. The scanning routines searched common file locations and environment variables, demonstrating a comprehensive approach to credential harvesting to facilitate lateral movement.
Once harvested, stolen credentials underwent a double-base64 encoding process before exfiltration to public GitHub repositories following a distinctive "s1ngularity-repository" naming pattern, each containing a single "results.b64" file with the encoded data. This encoding choice suggests an attempt to evade basic detection mechanisms while maintaining data integrity during the GitHub-based exfiltration process.
According to external research, the attackers also implemented destructive payloads that modified users' shell startup files (~/.bashrc and ~/.zshrc) with shutdown commands, creating systems that would crash when new terminal sessions were opened.
One particularly novel element was the attempt to leverage LLM (Large Language Model) clients as vectors for enumerating secrets on victims' machines. The attackers specifically targeted configuration files and authentication tokens related to popular AI CLI tools like Claude, Gemini, and Q, recognizing that these tools often require elevated permissions and access to sensitive development environments.
UPDATE 3: August 29, 2025
In a second phase that took place on August 28, 2025, the attackers used the valid GitHub tokens collected in the first phase to make private repositories public, named s1ngularity-repository- followed by 5 random letters.
It's very likely that the attackers only used the GitHub API for this second phase. GitHub events provide interesting information. A PublicEvent event is associated with each repository that has been made public. Given the repository IDs, we believe that the attackers renamed them before making them public.
GitGuardian detected 2,399 repositories containing at least a secret. In total, 82,901 secrets, including 11,168 valid ones. According to our data, 10,767 repositories were made public; this corresponds to around 20% of repositories containing a hardcoded secret. This is a huge proportion and far beyond what we usually see.
We want everyone to stay safe, and our Good Samaritan Program already sent 482 emails to the developers that are concerned; without exceeding 10 emails per repository.
UPDATE 2: August 28, 2025
GitGuardian has released a free, open-source tool called S1ngularity Scanner to scan local environments for files that may have been compromised in this attack, including environment variables and files that are known to be exploited.
UPDATE 1: August 28, 2025
Our continued analysis of the Nx "s1ngularity" attack has revealed several details about both the attack methodology and victim demographics.
LLM Tool Prevalence
Of the compromised systems, 33% had at least one LLM client installed, confirming the attackers' prescient focus on AI development tools. This represents a significant adoption rate that validates the attackers' strategy of targeting this emerging attack surface.
LLM Compliance Resistance
of the 366 systems where LLM tools were targeted, only 95 actually wrote the requested /tmp/inventory.txt file. Our analysis suggests that many LLM clients refused to comply with the malicious requests, with some explicitly stating they wouldn't execute commands that appeared to be credential harvesting attempts. This unexpected defensive behavior from AI tools may represent an unintentional but valuable security control in the modern development stack.
85% of infected systems were running macOS
Analysis of the exfiltrated data reveals that 85% of infected systems were running macOS, highlighting the attack's particular impact on the developer community where Apple's platform dominates. This concentration suggests either targeted selection of the developer ecosystem or simply reflects the natural distribution of Nx users.
GitGuardian's Public Monitoring: What We Found
While most "s1ngularity-repository" exfiltration repos were rapidly deleted by GitHub, GitGuardian's monitoring infrastructure provides unique visibility into these ephemeral artifacts. Because GitGuardian sees everything that happens on GitHub—including deleted files, and repositories—we were able to analyze the actual exfiltrated data, assess which secrets were exposed, and validate their status.
At the time of writing, our platform lists 1,346 repositories whose names contain the string “s1ngularity-repository”. GitHub, meanwhile, lists only about ten repositories. This indicates two interesting things: the repositories are being deleted, and developers are continuing to use the vulnerable package.
Out of these repositories, we detected that 1,079 of them contain at least a secret leaked between August 27, 2025 at 00:32:48 and August 27, 2025 at 15:36:57.
In total, this represents 2,349 distinct secrets. The most common types of credentials we found correspond to GitHub, NPM, AWS, and OpenAI. They all appear to be related to nx's orchestration capabilities.
Half of these secrets were valid at the time of writing. The most numerous are GitHub OAuth App Keys. This result, surprising at first glance, is in fact linked to the functioning of nx, for which a GitHub application exists and facilitates interactions between NX Cloud and GitHub.
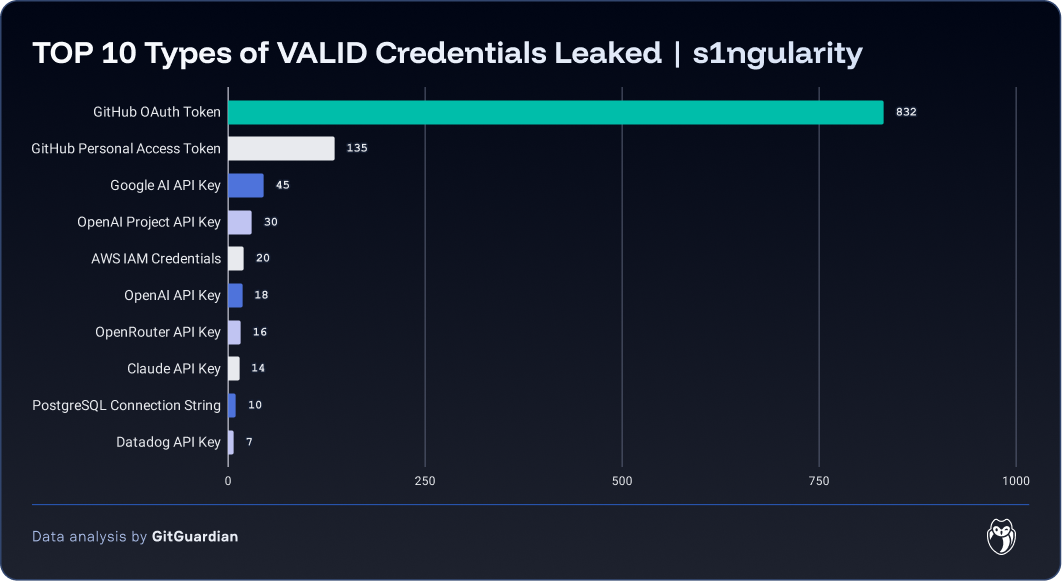
The fact that these secrets are still valid raises interesting questions on both the offensive and defensive sides.
First of all, it must be noted that exfiltration on GitHub is effective. At the height of the wave, nearly 1,400 repositories were publicly accessible via GitHub. It's a safe bet that the attacker retrieved them all in time before they were deleted, not to mention opportunistic attackers who took an interest in this leak. Our initial investigations indicate that they are now in a position to attack large companies whose infrastructure secrets, such as Artifactory, are at their mercy.
On the defensive side, we can only note the obvious delay in revoking the leaked secrets. While most of these secrets are no longer publicly accessible, they remain valid. It is highly likely that developers are unaware of the leaked secrets and have therefore not revoked them. Although we know the names of the repositories that leaked secrets, it is likely that they will never be revoked or rotated. To go beyond this analysis, our teams are mobilized to attribute these secrets to companies in order to make responsible disclosure.
Check If Your Secrets Were Compromised: HasMySecretLeaked
Following our analysis of the Nx "s1ngularity" attack, we added the hashed versions of all discovered stolen credentials to our HasMySecretLeaked database. This privacy-preserving service allows developers to check whether their specific secrets were among those exfiltrated during the attack—without ever exposing the actual secret values.
How to check your credentials:
Web Interface. Visit hasmysecretleaked.com and use the secure search function. Your secret is hashed locally before being checked against our database, ensuring GitGuardian never sees your actual credentials.
# Install ggshield
pip install ggshield
# scan env variables with
ggshield hmsl check --type env <(env)For bulk checking, use the GitGuardian CLI
cat results.b64 |base64 -d |base64 -d > results.txt
ggshield secret scan path --show-secrets --json /tmp/results.txt |jq -rc '.entities_with_incidents[].incidents[].occurrences[].match' > secrets.txt
ggshield hmsl check secrets.txtScan results.b64 as published on the GitHub repositories
Why this matters: Even though GitHub has deleted most "s1ngularity-repository" exfiltration repositories, the stolen credentials may have been harvested by other actors before removal. HasMySecretLeaked provides definitive answers about whether your specific tokens, API keys, or other secrets were compromised, enabling you to prioritize rotation efforts and assess your exposure risk.
Again, we already identified over 1,100 valid credentials from the Nx attack across GitHub tokens, OpenAI API keys, AWS credentials, and other sensitive secrets. If you used any of the malicious Nx versions (20.9.0-21.8.0), checking your credentials through HasMySecretLeaked should be your first step in incident response.
From s1ngularity to Reality
A critical challenge emerges when developers discover exposed secrets, they often delete the files or commits containing the credentials but fail to revoke the actual secrets.
The Nx case is interesting because it shows unequivocally that simply deleting data is not enough. It is necessary to revoke the associated secrets. For a company, this means that it must now be able to inventory its secrets across all systems, automate rotation workflows at scale, and maintain comprehensive visibility into where credentials are used—not just where they're stored.
The ability to rapidly detect exposure, validate impact, and execute coordinated revocation across thousands of non-human identities has become the new baseline for resilient software delivery in an era where supply chain attacks can weaponize leaked credentials within hours of discovery.
FAQ
What was the Nx "s1ngularity" attack and which versions were affected?
The Nx "s1ngularity" attack was a sophisticated supply chain attack that occurred in August 2025, targeting the popular Nx build system with millions of weekly downloads. Attackers compromised Nx npm package versions 20.9.0 through 21.8.0, deploying malware that systematically scanned infected systems for valuable credentials including GitHub tokens, npm authentication keys, SSH private keys, API keys, and cryptocurrency wallet files. The attack combined credential theft, environmental sabotage, and novel techniques targeting AI development tools.
How did the attackers exfiltrate stolen credentials and what was unique about their approach?
Once harvested, stolen credentials underwent a double-base64 encoding process before being exfiltrated to over 1,400 public GitHub repositories following a distinctive "s1ngularity-repository" naming pattern, each containing a single "results.b64" file with the encoded data. What made this attack particularly sophisticated was its novel approach to targeting LLM (Large Language Model) clients as vectors for enumerating secrets, specifically hunting for configuration files and authentication tokens related to popular AI CLI tools like Claude, Gemini, and Q.
What did GitGuardian's analysis reveal about the scope and impact of the attack?
GitGuardian's analysis revealed 2,349 distinct stolen secrets from 1,079 compromised repositories, with over 1,100 credentials still valid at the time of analysis. The attack predominantly affected macOS users (85% of victims), and 33% of compromised systems had at least one LLM client installed. Interestingly, many AI tools refused malicious requests—only 95 out of 366 LLM interactions actually succeeded in writing the requested inventory files, with some explicitly stating they wouldn't help with credential harvesting.
Why are the stolen secrets still dangerous even after GitHub deleted the repositories?
Even though GitHub rapidly deleted most "s1ngularity-repository" exfiltration repositories, the stolen credentials may have been harvested by other malicious actors before removal. Half of the discovered secrets remained valid during analysis, meaning attackers could still use them for lateral movement and further attacks. The deletion of repositories doesn't automatically revoke the actual credentials—developers must manually rotate their tokens, API keys, and other secrets to truly secure their systems.
How can I check if my credentials were compromised in this attack?
GitGuardian has added all discovered stolen credentials to the HasMySecretLeaked database in hashed form. You can check if your secrets were compromised without exposing them by visiting hasmysecretleaked.com where your secret is hashed locally before checking against the database. For bulk checking, use the GitGuardian CLI with commands like `ggshield hmsl check --type env <(env)`. If you used any malicious Nx versions (20.9.0-21.8.0), checking your credentials should be your first step in incident response.
What immediate steps should I take if I suspect my system was compromised?
First, check your package.json and package-lock.json files for malicious Nx versions (20.9.0-21.8.0) and run `npm ls nx` to verify your current installation. If compromised, immediately remove your node_modules directory, run `npm cache clean --force`, and inspect your shell startup files (~/.bashrc, ~/.zshrc, ~/.profile) for malicious "sudo shutdown -h 0" commands. Most critically, rotate every credential that might have been exposed: GitHub tokens, npm tokens, SSH keys, API keys, and cryptocurrency wallet seeds. Check your GitHub account for "s1ngularity-repository" repositories and review audit logs for suspicious activity.
What does this attack reveal about the future of supply chain security threats?
The s1ngularity attack demonstrates several concerning trends: the targeting of AI development tools as new attack surfaces, the use of public platforms like GitHub for credential exfiltration, and the combination of credential theft with environmental sabotage. The attack shows that simply deleting exposed data isn't enough—organizations must be able to inventory secrets across all systems, automate rotation workflows at scale, and maintain comprehensive visibility into where credentials are used. The rapid weaponization of stolen credentials (within 2-4 hours) makes automated detection and response capabilities essential for modern software delivery.



![Shai-Hulud 2.0 Exposes Over 33,000 Unique Secrets [Updated Nov, 27]](/content/images/size/w600/2025/11/shai-hulud--2--1.png)




