The ethical hacking group Sakura Samurai recently gained access to private United Nations (UN) employee data and systems in a significant data breach. This article is going to run through exactly how this happened and what exploits the attackers used to penetrate into these systems, then run through the attack and analyze how the attackers were able to move laterally using publicly accessible credentials.
This attack started when Sakura Samurai noticed the UN Vulnerability Disclosure Program and Hall of Fame. This is interesting because it suggests that this is a targeted attack towards the UN and not an opportunistic vulnerability discovery. Also means we have additional information from the attackers about how they conducted the attack.
The attack as it happened
First the attackers set up a perimeter with all the domains covered under the UN’s vulnerability disclosure program.
Using internal tools they began fuzzing the URLs (URL fuzzing is a technique used to discover hidden files/directories in a webserver by injecting carefully chosen wordlists corresponding to potential hidden paths in an automated fashion) - One domain, ilo.org, was discovered to have a subdomain with an exposed .git repository at the root level. This is a common exploit where attackers often check to see if an application has any publicly exposed git content by navigating to the root git folder in the domain, for example www.mydomain.com/.git
Using the tool git-dumper, the attackers were able to dump the entire contents of the repository and scan the source code for vulnerabilities. They discovered multiple sets of hardcoded credentials which allowed them to take control of a MySQL data and an internal survey management platform.
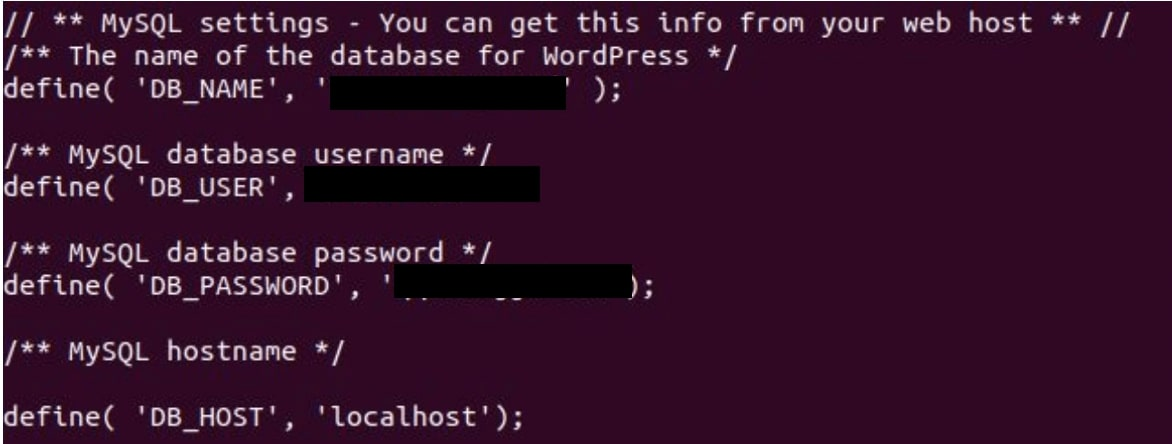
Following from this success the attackers continued to enumerate other domains and subdomains within the perimeter before eventually finding a subdomain connected to the United Nations Environment Programme (**.unep.org/) where the attackers discovered a publicly exposed .gitcredentials file granting them access to a password protected private GitHub repository.
Using the GitHub credentials they were able to authenticate themselves as valid users and make a complete clone of the repository to scan for vulnerabilities.
Private repositories are considered high value targets for attackers as they are known to contain a trove of sensitive information that attackers can use to launch additional exploits or move laterally deeper into the organization.
Within these repositories the attackers found 7 sets of credential pairs for internal databases belonging to the UNEP. In addition to the credentials the attackers also discovered backups of the databases within the repository which proved to contain a huge amount of sensitive personal identifiable information (PII) belonging to UN employees. Once this PII was discovered the Sakura Samurai stopped the attack and opted not to access the databases. This is because the hackers had already completed their goal of finding and exploiting an unknown vulnerability that led them to discovering sensitive information, giving them enough information to disclose to the UN.
Analysing the attack
There are a few reasons why this attack is really interesting. Firstly because the lateral movement is so clear. Attackers were able to move from public root level directories, through internal systems and then all the way to sensitive password protected git repositories.
Another reason this is interesting is that even though this attack was well planned and executed, it was relatively low tech and did not have a high infrastructure cost associated with it. This opens the attack path used by Sakura Samurai to a wide audience of potential attackers. In addition this makes the attack difficult to detect. When attackers use sophisticated techniques to evade detection or use brute force actions to disrupt systems, it can often trigger red flags and be identified with security tools. In this case, because the attackers were correctly authenticated they could have remained hidden in the systems undetected for extended periods of time. This leads us to the final reason the attack was so interesting.
The attack was stopped prematurely. Fortunately the attackers were ethical and didn’t want to cause unnecessary damage, had they been malicious actors, they could have kept the attack going and moved deeper into the UN organization. Taking over the MySQL databases, elevating privileges, creating accounts, using the the PII to launch internal spear phishing campaigns, or, just remaining hidden in the private git repository, transferring data and potentially inserting malicious code.
Wrap up
We can see that by exploiting vulnerable public applications, the attackers, Sakura Samurai, were able to launch a successful attack that was relatively low tech and low cost thanks to credentials that were publicly exposed. Using these credentials discovered by fuzzing URL's, the attackers were able to move laterally through the UN’s systems before ultimately being able to access a private git repository containing larges amounts of PII and additional credential pairs. This was an ethical hack with the indented purpose to disclose to the UN vulnerabilities that were discovered, the outcome could have been severe had a malicious actor been the first to exploit the vulnerabilities and could have continued through different exploits.
This attack clearly shows the need to ensure organisations establish a perimeter of assets, including git repositories both private and public, and conduct regular scanning to ensure that secrets such as credentials are not exposed and good credential management and hygiene is being used.
Discover Exposed Credentials Today








