1. Introduction
TLS auth is the process where a client verifies the server's identity before exchanging data, fundamental to ensuring confidentiality, integrity, and authenticity for data in transit. TLS does more than just encryption of data: It uses certificates to verify the identities of the communicating parties, ensuring authenticity. The process guarantees the information sent arrives unaltered, preserving its integrity.
This blog aims to work as a comprehensive guide to the world of TLS authentication. We'll begin with the concepts and protocols involved. We will then briefly look at mutual TLS (mTLS; there will be a detailed blog on this later). Certificate management, a critical aspect of TLS, will be thoroughly examined as well. Furthermore, we'll explore implementation best practices and the integration of TLS with other technologies.
Without further ado, let's get started.
2 TLS Auth Fundamentals
2.1 Core Concepts and Terminology
TLS auth relies on asymmetric cryptography and trusted third parties. Let's define the key concepts.
- (Digital) Certificate: Electronic "ID" that binds a public key to an identity. It contains info like the cert holder's name, the public key, the issuing authority, the validity period, etc..
- Certificate Authorities (CAs): Trusted entities that issue and sign certificates. By embedding their trust into operating systems and browsers, they vouch for the authenticity of the certs they issue.
- Trust Chains: Hierarchical structures of certificates, starting with a root certificate issued by a trusted CA. The client verifies the server's certificate by tracing it back to a trusted root certificate in its trust store. This process validates the authenticity and integrity of the server's certificate.
- Public and Private Keys: A matched pair of cryptographic keys, fundamental to asymmetric cryptography. The public key is shared openly and is used to encrypt data or verify a digital signature. The private key is kept secret and is used to decrypt data or create a digital signature.
2.2 Authentication Modes
- Server-only Authentication: The standard mode for HTTPS websites. The server presents its certificate to the client, and the client verifies its authenticity, protecting users from impersonation. Note that this only works one-way; it only verifies the server's identity, but does not verify the user's identity to the server.
- Mutual TLS (mTLS): a stricter, more robust mechanism where both the client and the server verify each other's certificates, providing stronger security by ensuring that both parties are who they say they are. Often used in high-security environments, critical for API security and microservices communication (again, there will be a dedicated blog on mTLS later).
2.3 How TLS Authentication Works
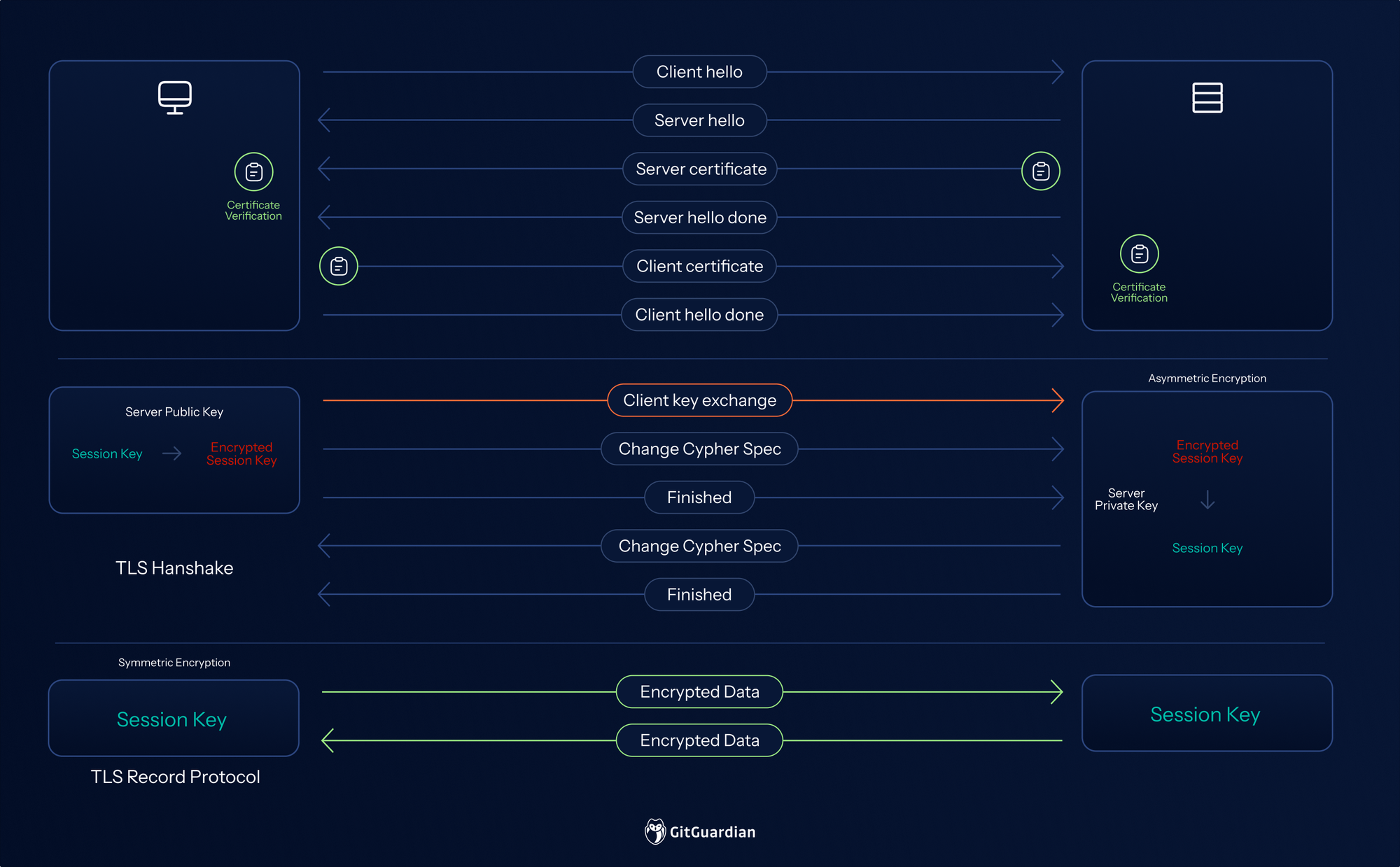
A breakdown of a TLS handshake:
- "Client Hello": The client initiates the connection, sending a client random, a string of random bytes, with its supported TLS version and cipher suites.
- "Server Hello" and Certificate: In reply to the client hello, the server sends a message containing the server's TLS certificate, the server's chosen cipher suite (sets of cryptographic algorithms), and the server random, another random string of bytes generated by the server.
- Certificate Validation: The client performs a series of checks:
- Trust Chain Validation: It verifies that a trusted CA issued the certificate.
- Signature Verification: It uses the CA's public key to verify the digital signature on the server's certificate, proving it hasn't been tampered with.
- Revocation Status Check: Use mechanisms like Certificate Revocation Lists (CRLs) or Online Certificate Status Protocol (OCSP) to ensure that the certificate has not been revoked due to compromise or other reasons.
- Expiration & Domain Check: It confirms the certificate is still valid and that the server's hostname matches the "Subject" or "Subject Alternative Name" field in the certificate.
- Key Exchange and Secure Channel: In modern TLS, the key exchange is primarily based on Diffie-Hellman (DH) or Elliptic-Curve Diffie-Hellman (ECDH). If all validation checks pass, the client and server use asymmetric primitives to establish a shared symmetric session key. This completes the handshake, establishing a secure, symmetrically encrypted channel, and communication continues using the session key.
2.4 Why TLS Authentication Matters
TLS authentication is not just a best practice; it is a fundamental security control. Its primary value lies in preventing man-in-the-middle (MITM) attacks. Without it, an attacker could intercept communications by impersonating the server, gaining access to all transmitted data. By verifying identities cryptographically, TLS assures that you are communicating with the intended party. This identity assurance, combined with strong encryption, forms the basis of trust for the modern infrastructure.
3. TLS Certificate Management and Validation Processes
A TLS certificate is not a "fire-and-forget" component; it has a finite lifespan.
3.1 Certificate Provisioning
A certificate begins with a provisioning request, typically done through a Certificate Signing Request (CSR), a block of encoded text that contains information about the entity requesting the certificate, including the domain name, organization details, and the public key. The CSR is then submitted to a Certificate Authority (CA).
There are two primary CA models: public CAs and private CAs.
- Public CA (like DigiCert, Let's Encrypt, or Google): Root certificates are embedded in all major browsers and operating systems, suitable for securing public-facing websites and applications.
- Private CA (runs internally using tools like Microsoft AD CS or HashiCorp Vault): For authenticating internal systems and services. Private CAs are not trusted by default and require clients to trust the issuing CA explicitly.
CAs offer different validation levels for public certificates:
- Domain Validation (DV): The CA simply verifies that the applicant controls the domain. This is a fast and inexpensive method for obtaining a certificate suitable for enabling HTTPS on a website.
- Organization Validation (OV): The CA performs additional checks to verify the organization's legal existence. OV certificates display this verified identity, building greater user trust, and are standard for enterprise and business websites.
- Extended Validation (EV): The CA conducts a rigorous vetting process to verify the legal identity of the organization requesting the certificate. This can be important for organizations that require a higher level of trust, such as financial institutions and e-commerce sites.
The choice of validation type primarily depends on the level of identity assurance required and the trust relationship the website owner wants to establish with its users.
As we can see, the provisioning of certificates can be complex, so, for modern, agile DevSecOps environments, we want automated provisioning. The ACME (Automated Certificate Management Environment) protocol is gaining popularity for automating certificate issuance and renewal. "Let's Encrypt" is a well-known CA that provides free DV certificates using the ACME protocol, simplifying the process of obtaining and managing TLS certificates.
3.2 Deployment and Storage
Once a certificate is issued, it must be deployed securely across systems and services, which involves installing the certificate and its corresponding private key on the server or device that will be using it. The concern is the protection of the private key, because if compromised, any trust in the associated certificate is compromised. Best practices for deployment and storage include:
- Secure Key Storage: Private keys should never be stored on shared file systems, checked into version control, or sent over unencrypted channels. For max security, especially in regulated business sectors, use a Hardware Security Module (HSM) or a cloud-based Key Management Service (KMS). These dedicated devices or services generate, store, and manage keys in a hardened, tamper-resistant environment.
- Automated Distribution: Manually copying certificate files is error-prone and does not scale. Integrate certificate deployment into configuration management toolchains (e.g., Ansible) or secrets management platforms (e.g., HashiCorp Vault, Azure Key Vault) for consistent and auditable rollouts.
3.3 Monitoring and Renewal
Certificates have a validity period; an expired cert is a common cause of downtime. Thus, proactive monitoring and renewal are non-negotiable. Implement:
- Certificate Lifecycle Management (CLM) Tools: Dedicated platforms can provide a centralized dashboard, track all certificates across the estate, and send proactive alerts well before expiration.
- Automated Renewal: Leveraging the ACME protocol or integrations with CLM tools to handle renewal requests, validation, and deployment automatically. This removes the human error factor and is the single most effective way to prevent expiration-related incidents.
3.4 Revocation and Transparency
Sometimes, a certificate must be invalidated before its natural expiration. For example, if the private key is compromised or a server is no longer needed. Revocation is the mechanism for this, and it informs the clients that the certificate should no longer be trusted. There are two primary mechanisms for certificate revocation:
- Certificate Revocation Lists (CRLs): Lists of revoked certificates periodically published by CAs that clients can check.
- Online Certificate Status Protocol (OCSP): A real-time protocol allowing clients to query the revocation status of a certificate directly from the CA (being deprecated as of 2025).
While revocation checks are crucial, they have limitations in browser compliance. This is complemented by Certificate Transparency (CT), a framework for publicly auditable logs from all issued certificates. Anyone can monitor and audit certificate logs, helping detect certificates that may have been issued maliciously or without authorization, to identify and respond to potential security threats.
4. Best Practices for TLS Authentication
A poorly configured TLS ecosystem creates a false sense of security. Moving beyond basic concepts and management practices, in this section, we will focus on the critical security considerations and must-dos to ensure TLS auth is resilient.
4.1 Cipher Suites and Protocol Versions
Legacy protocols, like SSL 3.0 and TLS 1.0/1.1, are known to be vulnerable. Our first line of defense is enforcing a strong cryptographic baseline by disabling SSL 3.0, TLS 1.0, and TLS 1.1.
Require TLS 1.2 (absolute minimum) or, ideally, TLS 1.3 (prioritize for all new deployments) for all connections.
TLS 1.3 provides significant security and performance enhancements by removing support for obsolete features and vulnerable cipher suites, mandating the use of strong, modern encryption algorithms, and employing a simplified handshake process. The number of round-trips between the client and server is reduced to one or two, weaker encryption options are removed, and key exchange and authentication are moved to earlier stages. These, along with other technical improvements, contribute to a more secure and efficient protocol.
Avoid cipher suites (sets of cryptographic algorithms) that use weak or outdated algorithms, such as those based on RC4, DES, or MD5. These algorithms are inherently insecure and should not be used. TLS 1.3 completely removes support for these weak algorithms. Regularly review and update cipher suite configuration to ensure that only strong and secure algorithms are enabled.
Enforce Strong Ciphers with forward secrecy: Configure servers to prefer cipher suites that support Forward Secrecy (FS), such as those using ECDHE (Elliptic Curve Diffie-Hellman Ephemeral). FS ensures that a compromise of the server's long-term private key does not allow decryption of past, recorded sessions.
4.2 Certificate Validation
Assuming a certificate is valid because it exists is a common (and catastrophic) error. Client applications must perform comprehensive validation:
- Enforce Full Chain Validation: Ensure clients (whether a browser, another service, or an API client) validate the entire certificate chain up to a trusted root CA. Do not accept self-signed or unknown certificates in production unless explicitly managed via a private CA.
- Verify Hostname and Intended Use: Check that the certificate's Subject Alternative Name (SAN) or Common Name (CN) matches the hostname you are connecting to. Plus, verify that the certificate is intended for server authentication (via the Key Usage and Extended Key Usage extensions).
- Respect Expiration and Revocation: Never disable checks for certificate expiration or revocation status (via OCSP or CRL). An expired or revoked certificate is a major red flag.
- Eliminate "Insecure" Overrides: Avoid "skip verification" or "insecure mode" options in your code. In development code, avoid temporary flags like curl -k or SSL_VERIFY_NONE. These could slip into production, completely disabling authentication.
- Eliminate "Insecure" Overrides: Avoid "skip verification" or "insecure mode" options in your code. In development code, avoid temporary flags like `curl -k` or setting `SSL_VERIFY_NONE`. These could slip into production, completely disabling authentication.
- Handling Untrusted Certificates (Development/Testing): If you need to connect to a server with a self-signed certificate or a certificate issued by an untrusted CA (e.g., in a development or testing environment), avoid disabling verification entirely. Instead, consider safer alternatives, like adding the specific certificate to your trust store or using a custom CA for development. But it’s important to remember never to use these techniques in production. In production, you should always rely on certificates issued by trusted CAs.
4.3 Private Key Protection
The private key is the most sensitive component of a TLS certificate. Protecting it is the most important task to maintain the security of the TLS ecosystem.
- Secure Storage with HSMs/KMS: Store private keys in a secure, access-controlled vault. For high-security environments, use a Hardware Security Module (HSM) or a cloud Key Management Service (KMS) to generate and store keys, preventing their export.
- Restrict Access to Private Keys: Implement the principle of Least Privilege. Restrict filesystem access to private key files so that only the service account that requires it has read permissions. Only grant access to the private key to those who absolutely need it, and ensure that they have the minimum necessary permissions.
- Rotate Keys Upon Certificate Renewal: Establish a key rotation policy to generate new private keys whenever certificates are renewed. This limits the impact if a key is compromised. Generating a new private key upon each certificate renewal is a recommended security practice. Revoke certificates immediately upon suspicion of compromise. This practice aligns with a robust secret management policy.
5. Integration with Modern Authentication Frameworks
While TLS authentication is a powerful piece of machinery on its own, it brings even more value when integrated with other frameworks. In modern architectures, most of the time, TLS does not operate in isolation, but acts as the base layer of trust upon which sophisticated identity and access management systems are built.
5.1 TLS + OAuth 2.0/OpenID Connect (OIDC)
Modern apps, more often than not, require a double-layered auth approach: verifying both machines (service identity) and human users (application identity). This is where token-based protocols such as OAuth 2.0 and OpenID Connect (OIDC) are widely used, and TLS (and particularly mTLS) comes in.
The TLS/mTLS part verifies the machines (servers, microservices, identity of the client app or API gateway connecting to a resource server), and once this secure communication channel is established, the app can then use a token to authenticate human users. The backend services then verify both the mTLS certificate of the calling service and the OAuth token of the user, providing a layered approach to authn and authz.
5.2 TLS in APIs and Service Meshes
In distributed systems, the security of APIs and microservices communication is critical, and mTLS is the gold standard for mutually authenticating the services involved.
Service meshes like Istio and Linkerd have made the implementation of mTLS both seamless and scalable. They act as an infra layer that automatically injects sidecars, which handle all the complexity of TLS: they automatically generate and rotate short-lived certificates, negotiate mTLS connections, and enforce policy.
This drastically reduces the complexity and overhead for developers, and ensures all inter-service communication is authenticated and encrypted by default, without requiring code changes in all of those microservices.
5.3 TLS in Cloud-Native Environments
The dynamic nature of modern cloud-native platforms and modern container runtime platforms, like short-lived containers, auto-scaling, and constantly changing internal IP addresses, poses unique challenges for TLS certificate management, because it is difficult to manually manage certificates and ensure that they are always valid and up-to-date.
So, automated certificate issuance and renewal are essential for managing TLS certificates in a cloud-native environment. Integrations with Kubernetes or service meshes can automate the process of obtaining and renewing certificates, ensuring that services always have valid certificates. For example, cert-manager is a Kubernetes add-on that automates the issuance and management of TLS certificates. It can obtain certificates from various sources, including Let's Encrypt and private CAs, and automatically renew them before they expire. This simplifies the process of managing certificates in Kubernetes environments and ensures that services always have valid certificates.
6. Summary
Transport Layer Security (TLS) authentication acts as a critical basis for trust in an era defined by API-driven business and cybersecurity threats. It provides:
- Confidentiality, ensuring data remains private
- Integrity: guaranteeing data remains unaltered
- authenticity: verifying the identities of communicating parties
Proper implementation of TLS is not just one checkbox on the security to-do list that we can simply check without thinking about it, because achieving a truly secure TLS implementation requires a holistic approach:
- Automated certificate lifecycle management
- Continuous validation and monitoring, Integration with zero-trust and identity frameworks for a layered security architecture
Final takeaway: Strong TLS auth isn't an option; it's a must. It is a non-negotiable requirement for building and maintaining resilient, secure, and trustworthy systems. Mastering it is not just the responsibility of security teams, but of every architect and developer committed to safeguarding our digital future.
FAQ
What is TLS authentication and why does it matter?
TLS authentication is the process where a client verifies the server's identity before exchanging data, fundamental to ensuring confidentiality, integrity, and authenticity for data in transit. TLS does more than just encrypt data—it uses certificates to verify the identities of communicating parties and guarantees information arrives unaltered. Its primary value lies in preventing man-in-the-middle (MITM) attacks, where an attacker could intercept communications by impersonating the server. By verifying identities cryptographically, TLS assures that you are communicating with the intended party.
What is the difference between server-only authentication and mutual TLS (mTLS)?
Server-only authentication is the standard mode for HTTPS websites where the server presents its certificate to the client, and the client verifies its authenticity, protecting users from impersonation. However, this only works one-way—it verifies the server's identity but does not verify the user's identity to the server. Mutual TLS (mTLS) is a stricter, more robust mechanism where both the client and the server verify each other's certificates, providing stronger security by ensuring that both parties are who they say they are. mTLS is often used in high-security environments and is critical for API security and microservices communication.
How does the TLS handshake process work?
The TLS handshake involves several steps: 1) Client Hello - the client initiates connection, sending a client random with supported TLS version and cipher suites; 2) Server Hello and Certificate - the server sends its TLS certificate, chosen cipher suite, and server random; 3) Certificate Validation - the client verifies the trust chain, signature, revocation status, expiration, and domain match; 4) Key Exchange - using Diffie-Hellman or Elliptic-Curve Diffie-Hellman, the client and server establish a shared symmetric session key. If all validation checks pass, a secure, symmetrically encrypted channel is established for ongoing communication.
What are the different types of Certificate Authority validation levels?
Certificate Authorities offer three validation levels: 1) Domain Validation (DV) - the CA simply verifies that the applicant controls the domain, fast and inexpensive, suitable for enabling HTTPS on a website; 2) Organization Validation (OV) - the CA performs additional checks to verify the organization's legal existence, displaying this verified identity for greater user trust, standard for enterprise and business websites; and 3) Extended Validation (EV) - the CA conducts rigorous vetting to verify the legal identity of the requesting organization, important for organizations requiring higher trust levels like financial institutions and e-commerce sites.
What are the critical best practices for private key protection?
Private key protection is the most important task for maintaining TLS ecosystem security. Best practices include: 1) Secure Storage with HSMs/KMS - store private keys in Hardware Security Modules or cloud Key Management Services to prevent export; 2) Restrict Access - implement least privilege principles, restricting filesystem access so only necessary service accounts have read permissions; 3) Rotate Keys Upon Renewal - generate new private keys whenever certificates are renewed to limit impact if compromised; and 4) Never Store in Version Control - private keys should never be stored on shared file systems, checked into version control, or sent over unencrypted channels.
Why should organizations disable legacy TLS protocols and what should they use instead?
Legacy protocols like SSL 3.0 and TLS 1.0/1.1 are known to be vulnerable and should be disabled. Organizations should require TLS 1.2 as an absolute minimum or, ideally, prioritize TLS 1.3 for all new deployments. TLS 1.3 provides significant security and performance enhancements by removing support for obsolete features and vulnerable cipher suites, mandating strong modern encryption algorithms, and employing a simplified handshake process that reduces round-trips between client and server. TLS 1.3 completely removes support for weak algorithms based on RC4, DES, or MD5, and enforces forward secrecy to ensure past sessions remain secure even if long-term private keys are compromised.
What comprehensive validation steps should client applications perform for TLS certificates?
Client applications must perform comprehensive validation including: 1) Full Chain Validation - validate the entire certificate chain up to a trusted root CA; 2) Hostname Verification - check that the certificate's Subject Alternative Name (SAN) or Common Name matches the connecting hostname and verify it's intended for server authentication; 3) Expiration and Revocation Checks - never disable checks for certificate expiration or revocation status via OCSP or CRL; and 4) Eliminate Insecure Overrides - avoid "skip verification" flags like curl -k or SSL_VERIFY_NONE that could slip into production and completely disable authentication.
How does TLS integrate with OAuth 2.0/OIDC in modern authentication architectures?
Modern applications require double-layered authentication: verifying both machines (service identity) and human users (application identity). TLS and particularly mTLS verify the machines—servers, microservices, and the identity of client apps or API gateways connecting to resource servers. Once this secure communication channel is established, the application can use OAuth 2.0 or OpenID Connect tokens to authenticate human users. Backend services then verify both the mTLS certificate of the calling service and the OAuth token of the user, providing a layered approach to authentication and authorization that secures both service-to-service and user-to-service interactions.
How do service meshes simplify TLS implementation in microservices architectures?
Service meshes like Istio and Linkerd have made mTLS implementation seamless and scalable by acting as an infrastructure layer that automatically injects sidecars to handle TLS complexity. They automatically generate and rotate short-lived certificates, negotiate mTLS connections, and enforce policy without requiring code changes in microservices. This drastically reduces complexity and overhead for developers and ensures all inter-service communication is authenticated and encrypted by default, making mTLS the gold standard for mutually authenticating services in distributed systems.
What tools automate certificate management in cloud-native Kubernetes environments?
The dynamic nature of cloud-native platforms—short-lived containers, auto-scaling, and constantly changing internal IP addresses—poses unique challenges for manual TLS certificate management. Automated certificate issuance and renewal are essential. For Kubernetes, cert-manager is an add-on that automates the issuance and management of TLS certificates, obtaining certificates from various sources including Let's Encrypt and private CAs, and automatically renewing them before expiration. This simplifies certificate management and ensures services always have valid certificates, addressing the challenges posed by the ephemeral nature of cloud-native deployments.
In the next blog, we will have a detailed look at mutual TLS (mTLS), a stricter, more robust mode of TLS. Stay tuned!