What is application security and why is it critical
Application security also known as AppSec is the process of securing your company’s software applications so that critical data within those applications are protected from external threats. Application security occurs throughout every phase of the software development life cycle (SDLC). It begins in the preparation phase and continues all the way through to the end of the life of your application. It’s important to know that security doesn’t end when an application is given to the end-user.
The past decade has seen a huge increase in web applications as we rely more on the internet, application security has become one of the most important elements of a company’s security posture. Given that websites and web applications are open to the public they are exposed to cybercriminals and give hackers a great way to target your business. Therefore it’s imperative that any company that has a web application take the proper steps to build a secure web app so you reduce the chances of your business being negatively affected. Here are some of the top web application vulnerabilities you should be aware of (statistics provided by veracode):
SQL Injection: Attackers use SQL queries submitted through web forms to submit SQL commands to your backend database. This gives the attacker the ability to create, read, update, alter or delete data and is found in roughly 24% of all applications.
Cross-Site Scripting (XSS): This is when an attacker inserts malicious scripts into a website that will be executed when someone visits that webpage. This is typically performed using javascript and results from weaknesses in client-side scripting languages as well as poor or little data sanitization in your applications input forms. This vulnerability is found in about 50% of all applications.
CRLF: This stands for carriage return line feed (CRLF) and it’s any vulnerability that occurs when attackers inject a CRLF character sequence where it’s not expected. CRLF can be used to modify application data, compromising integrity and enabling the exploitation of other vulnerabilities like XSS, proxy and web server cache poisoning and more. It’s found in roughly 60% of all applications.
Credential Mis-Management: As we have seen a shift towards web applications there has also been a change in software architecture which has seen s shift away from monolithic software development and towards an architecture of distributed individual services. Secrets or digital credentials like API keys are what connect all these services together. But these secrets are highly sensitive which has led to a significant increase in how exposed credentials are being found and used by attackers.
What are the existing frameworks or maturity models
OWASP Devsecops Maturity Model: OWASP stands for open web application security project and is a community-led open-source project dedicated to helping companies secure their web applications. It’s a great place to find information on protecting your web apps and they even have a full maturity model to help people understand where they rank when it comes to devsecops and where they should be trying to get to.
NIST Cybersecurity Framework: NIST is the national institute for innovation and technology, one of the leaders when it comes to technology frameworks and cybersecurity is no exception. They have a good cybersecurity framework that is used by several organizations and it’s definitely worth referencing to see what your company should be doing for cybersecurity.
ISO 27001 Information Security Management: ISO is the international organization for standards and guidelines, they have their own security framework specifically for information security.
STRIDE: STRIDE is a threat model created by Microsoft for helping companies meet the security directives of the CIA triad (Confidentiality, Integrity and Availability). Threat modeling frameworks are an essential part of application security by helping you to identify what type of attacks you are likely to face so that you can plan out your defense.
What are the critical investments that need to be done
There are many things that you can invest in when you’re looking to build out an effective web application security program. The first thing we recommend you invest in is proper training and coaching for your software developers. Keep in mind that a developer’s job is to create software, not to be an expert in cybersecurity. Therefore it’s important that you give your developer’s the training they need to build secure software applications. A survey from Veracode found that vulnerability fix rates increased by as much as 6X when developers were given remediation coaching and e-learning options around vulnerabilities in software.
The second best thing you can do to get a good ROI on your investment is to start doing formal security testing. This can be static code tests where you have your source code reviewed by an industry expert to look for vulnerabilities or it can be an active code test such as a penetration test where you have security experts try to hack into your web application to determine what vulnerabilities are there. By doing these exercises you can find and fix security issues before it is exploited by someone outside of the company, which would cost you a lot of money.
Thirdly, you want to invest in ongoing monitoring of your web application. You should have a means for people to report security bugs that they find in your web application, have a process for remediating them and a means of pushing out updates quickly. You can take this a step further by having a bug bounty program where people are compensated for reporting issues in your application after it has gone live. It’s unlikely that all issues will be found during the development of the application so continuous testing is always needed.
Why an AppSec program does not slow down the development progress
The key to keeping an AppSec program from slowing the development process is to have it built into the workflow. The only time application security will cause serious issues for your timeline is if you build out an application and then try to add the proper security features afterward. For example, let's take a look at using third-party code libraries. If you outline for your developers what code libraries have been vetted and approved for a project in the beginning, the developers can build the application using the appropriate libraries and that won’t be an issue going forward. If you wait until after the application is developed, look at the code libraries and find out insecure code was used, at that point, it will require a lot of extra work to go back and fix that mistake.
Also, it’s much easier to ask a developer to fix an issue in something they recently coded than it is to ask them to fix something they coded 6 months ago. It will take time for them to get familiar with the code again, which will add to the delay. Proper integration with the Software Development LifeCycle is a characteristic of a top-class AppSec program. The key to avoiding excessive delays is to be proactive and have the security tasks added into the workflow during the preparation phase of application development.
Different types of tools to implement into a mature AppSec program
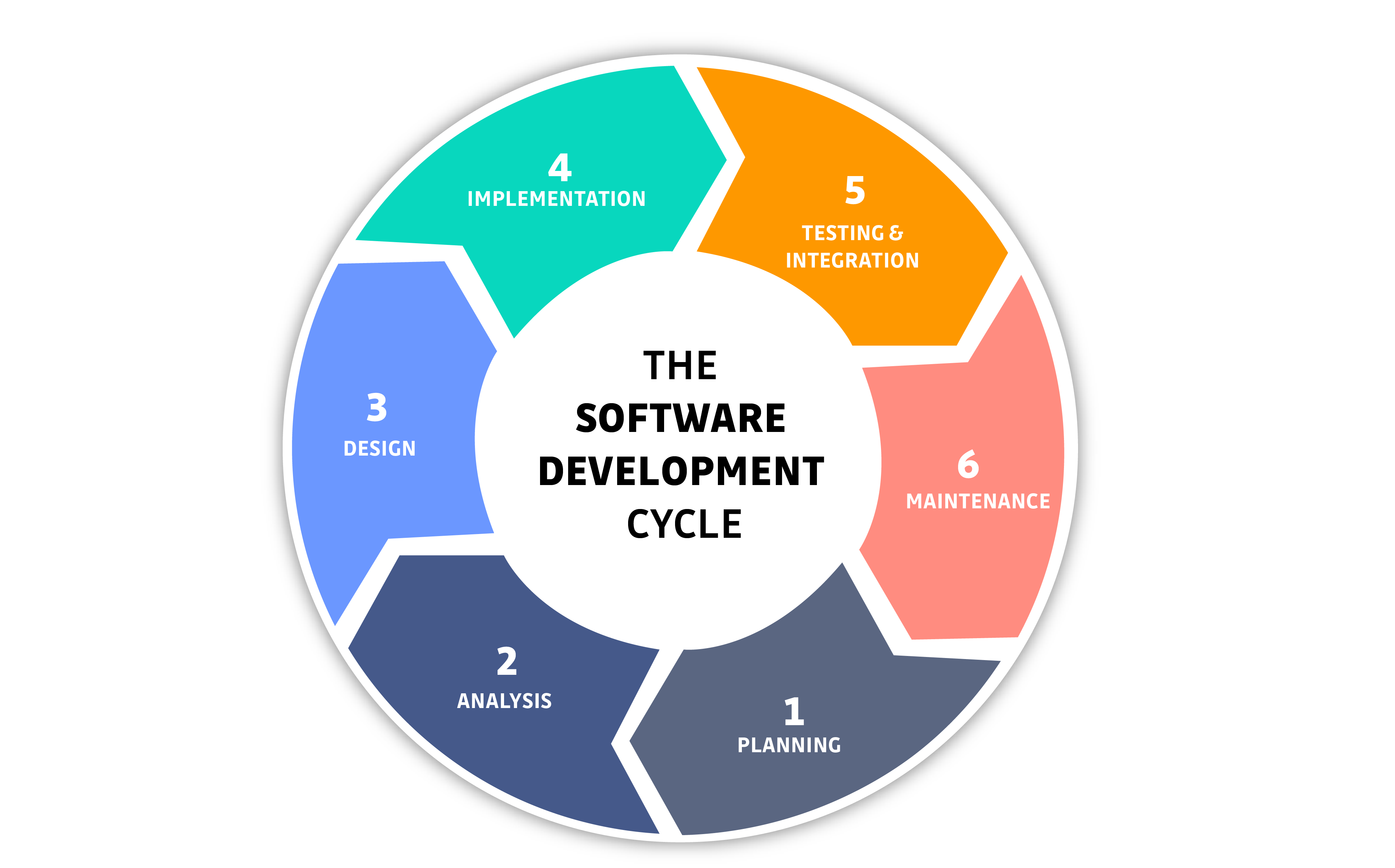
Now that we have discussed the benefits of a good application security program, let’s go over some of the key features of a mature AppSec program. Before discussing the tools it’s good to have an understanding of the software development lifecycle (SDLC). Each phase of the SDLC has different security tools and processes that you want to use to ensure that you build a secure application.
For the planning and analysis phases, you want to outline the security requirements for your application. This means compliance requirements as well as security requirements based on the type of application that you are building. This is typically done through the process of threat modeling, where you look at the type of data your application will hold as well as its function to identify the possible vulnerabilities.
For design and implementation where you start doing the actual coding of the application, you want to use Static application scanning tools (SAST). These tools can scan your application’s source code for vulnerabilities without ever having to run the application.
For the testing and integration phase of the SDLC you want to use Dynamic Application Scanning tools (DAST), these tools simulate attacks during runtime. One important way they do this is through fuzzing, which is a technique that generates random, invalid or unexpected data as inputs into a software application. The goal here is to ensure that your application can correctly handle any type of user input and isn’t vulnerable to common cyber-attacks like SQL injections or cross-site scripting.
During the maintenance phase it is important to make sure that all of your applications components or dependencies are fully patched and up to date. SCA software automatically scans all open-source components to check for policy and license compliance, security risks, and version updates SCA software also provides insights for remedying identified vulnerabilities, usually within the reports generated after a scan.
The last tool you should invest in is a tool for secret detection. Many developers use Github as a means to share code with other developers or just to build their own online portfolios. Often developers will unknowingly commit repositories to Github that have confidential information such as usernames, passwords, IP addresses, API keys and more. These can be used to do more than just hack your web application, they can give attackers direct access to your network so it’s important to invest in tools that can monitor the web for information like this and alert you when it comes up. A study of 13% of all Github repos by North Carolina State University found over 100,000 repos with leaked API tokens and cryptographic keys with thousands of new secrets being leaked every day.
Conclusion
As companies continue to integrate their business with the internet application security will continue to be one of the most important aspects of cybersecurity. Web applications are one of the biggest threat vectors used by hackers so it should be one of the most heavily invested areas for any business. The key is to build the proper security processes into the software development lifecycle from the beginning. This way you are able to create secure applications rather than having to add security later and secondly, you reduce time delays that would be created if you build the application and then ask your developers to go back and make major changes 6-12 months later. Lastly, it is essential that you monitor the web for any leaked company secrets. As developers share their work on Github they often accidentally post information on the web that can be used to hack into your company. If you’re interested in automated secret detection and remediation you can request a demo for GitGuardian here. You can also try GitGuardian for free for your internal repositories and if you’re a non profit or educational institution you qualify for a special discount on the commercial version.
This article is a guest post. Views and opinions expressed in this publication are solely those of the author and do not reflect the official policy, position, or views of GitGuardian, The content is provided for informational purposes, GitGuardian assumes no responsibility for any errors, omissions, or outcomes resulting from the use of this information. Should you have any enquiry with regard to the content, please contact the author directly








