GitGuardian’s Automated severity scoring engine for hardcoded secrets is out of beta and now GA.
Reviewing hundreds of hardcoded secrets incidents can be time-consuming and tedious for most application security engineers. Fortunately, GitGuardian is now the first secrets detection and remediation platform to offer a solution to this problem – thanks to our new automated severity scoring engine! Dwayne McDaniel, Security Advocate at GitGuardian, put together this short demo for you to get the gist of this new release.
Automated Severity Scoring with GitGuardian
This new capability automates assigning severity levels to each incident (where applicable), allowing security teams to quickly identify the most critical ones and prioritize their response accordingly. With GitGuardian’s automated severity scoring engine, application security teams can save time, reduce the risk of critical exposure, and improve their overall security posture by focusing on what truly matters!
After detection comes remediation
Hardcoded secrets are a common problem in software development, where sensitive data such as API keys, passwords, and certificates is embedded directly into the code. If exposed, unauthorized users and, more dangerously, attackers can use these secrets to gain initial access to sensitive systems or move laterally from one to another.
Our solution to this problem was first to build a best-in-class detection engine to scan code repositories for hardcoded secrets and alert developers when they are found. With that goal now achieved (GitGuardian is the #1 security app on the GitHub Marketplace 😉), we are now committed to providing security engineers and developers the best experience to remediate fast and in full.
Automated severity scoring, a first for hardcoded secrets!
Our new automated severity scoring engine takes the remediation experience a step further by assigning a severity level to each incident, helping security teams avoid inconsistent manual scoring and prioritize their response.
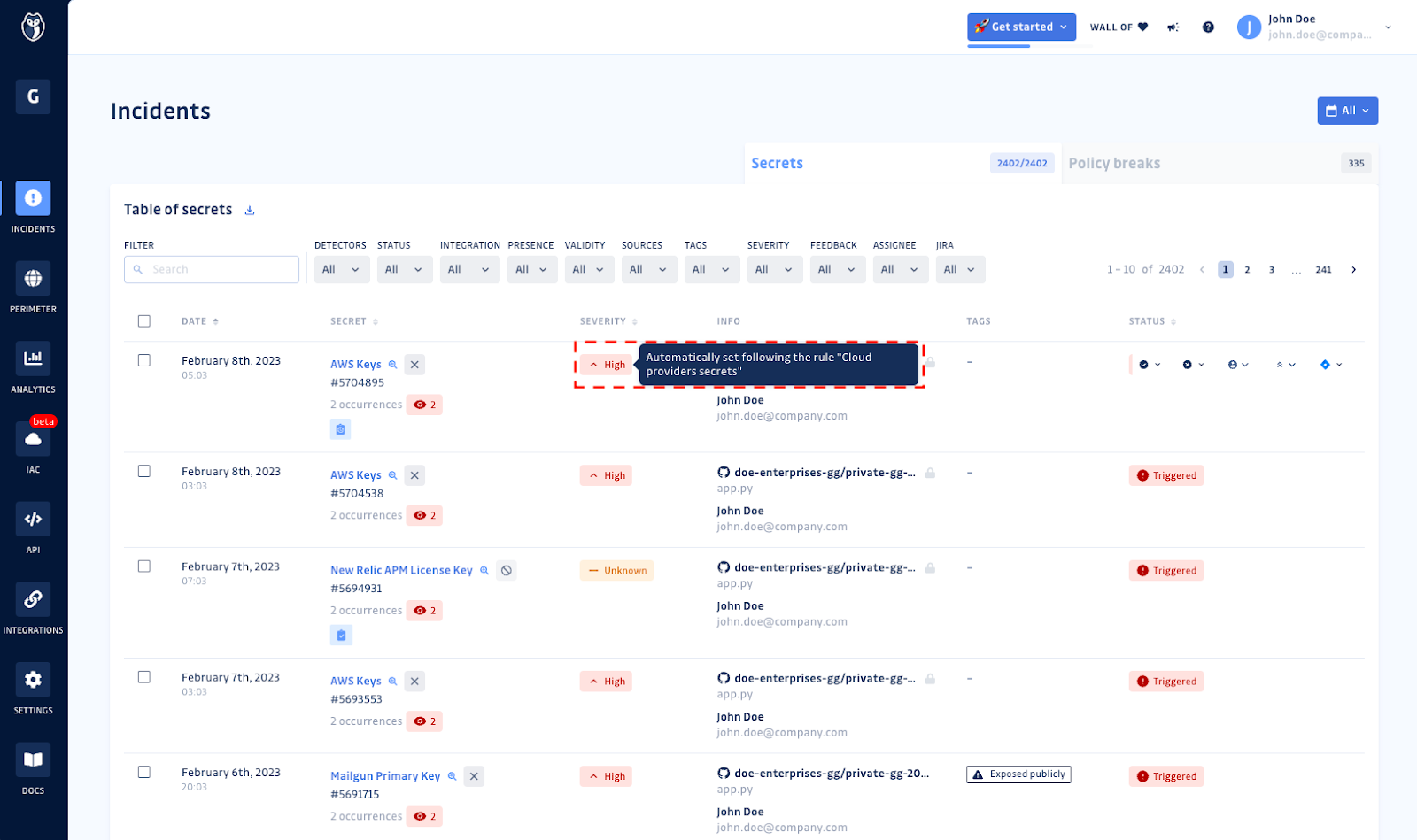
Our severity scoring engine comes with 15 default rules out-of-the-box. Each rule uses a combination of one or more factors to determine the severity of each incident, including:
- The type of secret: Some secrets, such as Cloud Service Providers’ API keys or database connection URLs, are more critical than others and require immediate attention.
- The validity of the secret: Valid exposed secrets are exploitable and thus represent a more significant risk than others.
- The visibility of the secret: Secrets exposed to the public are more severe than those hidden in private repositories.
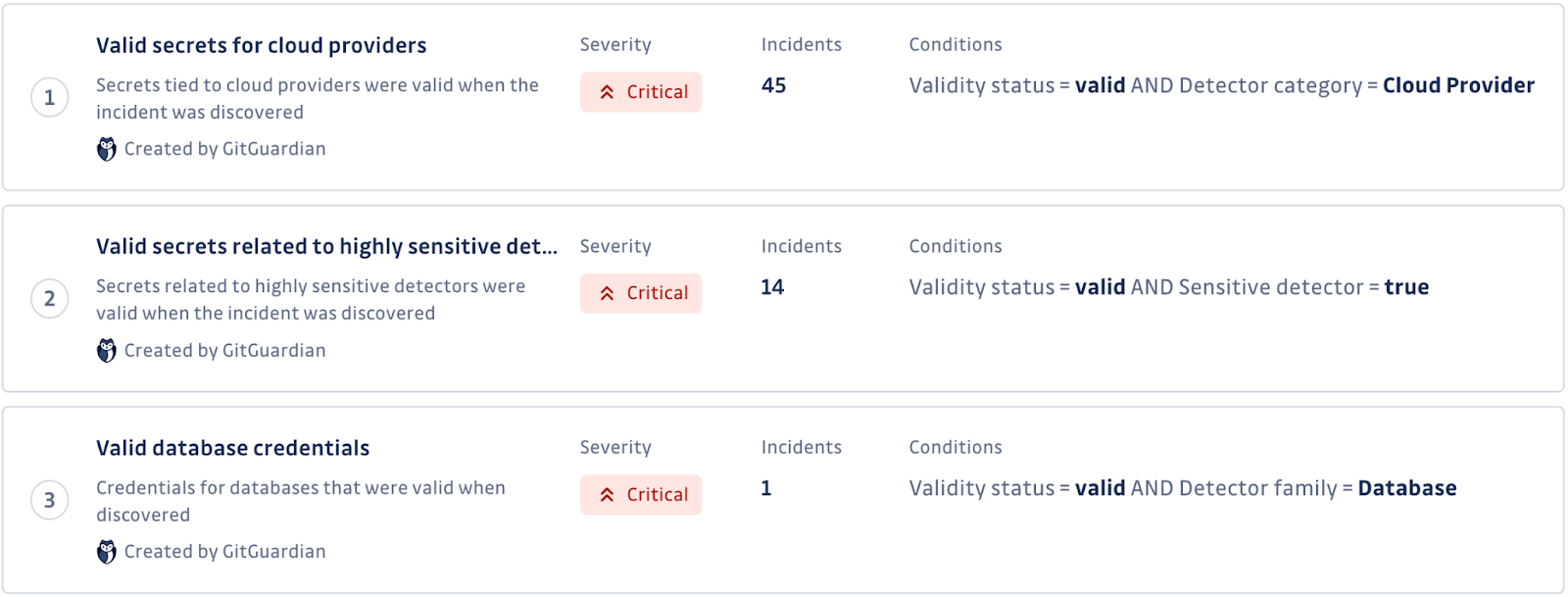
Based on these factors and others, each incident is assigned a severity level of “low,” “medium,” “high,” “critical,” or “unknown.” Security engineers and developers can then use this information to prioritize their response and address the most severe incidents first. Using GitGuardian’s automated severity scoring engine, application security teams can:
- Quickly identify the most severe hardcoded secrets incidents, significantly reducing the risk of their exploitation.
- Prioritize their response based on the severity of each incident, saving time and resources.
- Stay on top of security risks and improve their overall security posture.
The engine's coverage
In addition to assigning severity levels to each incident, GitGuardian’s automated severity scoring engine also includes a coverage metric. Coverage represents the percentage of incidents that the engine was able to assign a severity level to out of the total number of outstanding incidents. This metric provides users with a clear picture of the engine’s overall effectiveness and helps them identify any gaps in their security coverage. With GitGuardian’s automated severity scoring engine, users can have confidence that they are fully protected from the risks of hardcoded secrets.
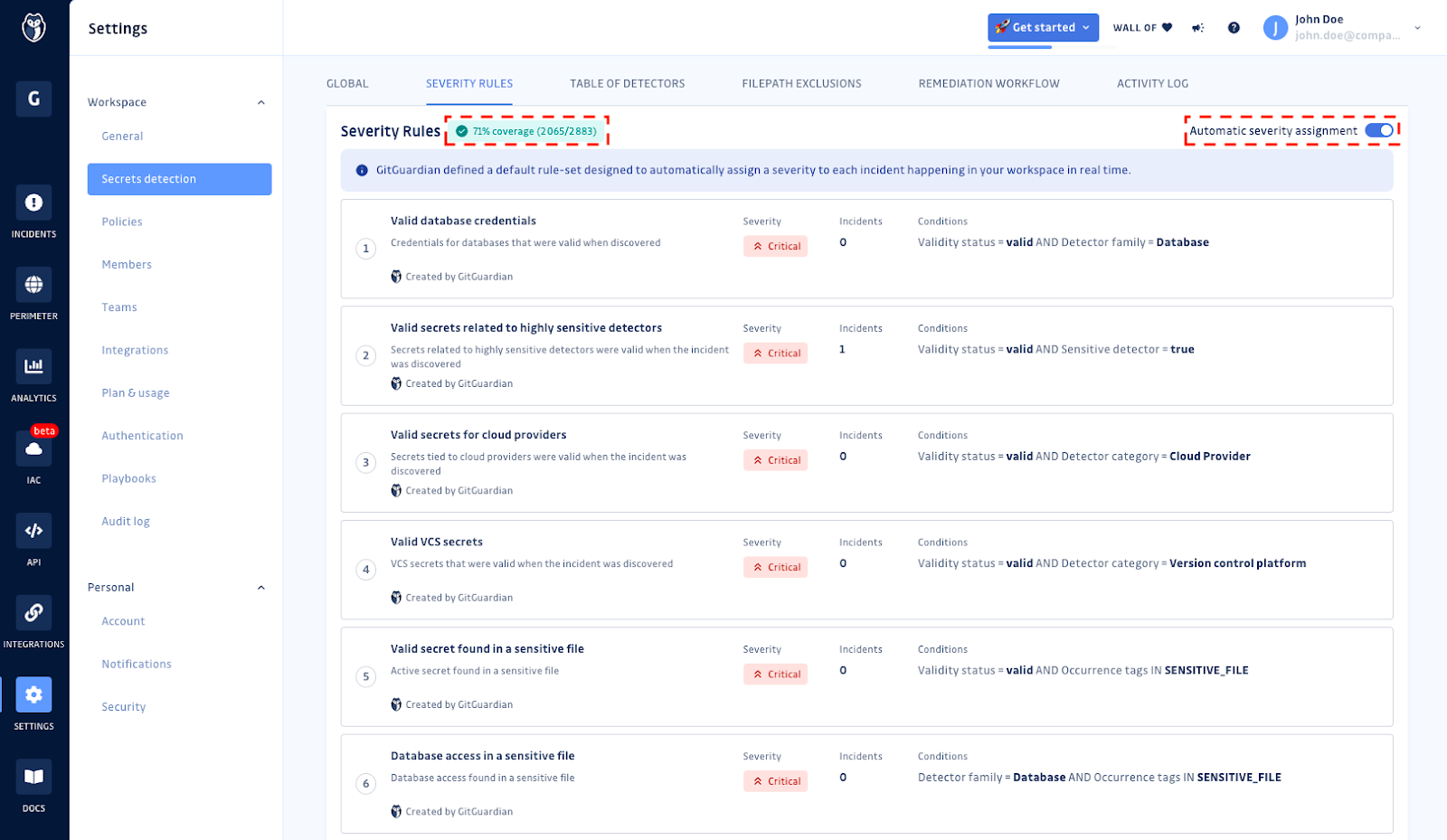
Turn it on, and let us know what you think!
We’re excited to bring this new feature to our users and help them protect their software development lifecycle from hardcoded secrets. If you already have a GitGuardian account, you can turn it on from your workspace settings. Also, stay tuned for the release of the next version of our automated severity scoring engine, in which you will be able to define your own severity rules and conditions!
If you don’t have an account yet, learn more about GitGuardian and how we can help you protect your organization’s software supply chain from exposed secrets at https://www.gitguardian.com. You can also learn more about our approach to automating manual steps in the remediation process with our no-code playbooks in this post: Automate your way out of code security incidents with GitGuardian’s playbooks.








