Continuing with our series on initial access techniques, this blog post is going to be focusing on credential access. When we talk about credentials this means things like usernames, passwords, PINs, and any other piece of authentication material you would use to login to an account. When attackers use credential access as a means to get access to the company, they use different techniques such as keylogging to capture the credentials and then they can access the network via legitimate user accounts. It’s been proven to be a very effective and popular technique, according to Verizon over 80% of breaches caused by hacking involve brute force or the use of loss or stolen passwords. In addition to being extremely effective, this type of activity is much harder to find than other types of initial access techniques because it will look like a legitimate use of a user account. Detecting this activity will be very difficult so the focus needs to be on preventing the credentials from being taken. Here we’re going to go over some of the main technique’s hackers use to gain access to user credentials:
Brute Force

This is the simplest type of attack for getting user credentials. In a brute force attack, a hacker tries to guess a user’s password. This can be done directly on the target service or offline against previously acquired credential data such as a password hash. Since it involves randomly guessing at a password it’s not a very efficient attack and it can take a very long time. The best way to prevent brute force attacks is to use strong passwords that are at least 12-16 characters in length and use a variety of characters. This ensures that the password will be very difficult to guess even with specialized software or using a list of commonly used passwords. You should also configure account lockouts if someone enters an incorrect password more than 3 times and lastly proactively reset account passwords if they are leaked in a data breach. An example of a threat group that commonly used brute force attacks is a suspected Iranian threat group called OilRig that would carry out supply chain attacks.
Credentials from password stores

Another technique for obtaining user passwords is for a hacker to check the usual locations where a password is stored on your computer. Most operating systems or applications save passwords in a particular location, so if a hacker gets access to the computer they can go to that location and get the stored passwords. To prevent this type of attack you want to focus on preventing the hacker from getting access to the machine in the first place by having good endpoint security. Additionally, you can change the passwords for a user’s login keychain (where the password is stored) so that it is different from the user’s login password. This way even if someone gets access to the machine, they won’t be able to access all of the stored passwords on the machine. An example of this technique being weaponized was a piece of malware called stealth falcon, which would gather passwords from multiple locations on the computer including Windows Credential Vault and Outlook.
Exploitation for Credential Access
Hackers can also gain access to user credentials by exploiting a software vulnerability. This usually means a hacker takes advantage of some programming error in a program or service to get remote code execution and extract the credentials that they need. The main defense for this is to ensure that all of your software is kept up to date with the latest version to limit the amount of software vulnerabilities available for exploitation. You may also want to develop a threat intelligence program so that you can be aware of new vulnerabilities and threats as they get discovered. Your last line of defense would be to invest in some endpoint exploit protection and isolate your applications. This way an attacker will be limited in their ability to move laterally if they get access to a usable password.
Forced Authentication
Another way hackers get credential material is to invoke or force a user to automatically provide authentication through a mechanism that can be intercepted. For example, if your organization uses SMB for single sign-on an attacker can try to intercept the authentication process and retrieve passwords or password hashes that they can use to login to other network resources. Some common way a hacker will set this up is through the use of a phishing attachment containing malware. The common defense for this type of attack is to filter network traffic, you should block traffic such as SMB and WebDAV from exiting your enterprise network by blocking the associated TCP ports. This way it will be harder for someone to intercept the traffic. A prime example of this is the malware dragonfly 2.0, which gathers hashed user credentials over SMB using spear-phishing attachments with external resource links and modifying.
Forge Web Credentials
Rather than trying to get legitimate login credentials, a hacker may look to forge web credentials such as session cookies or SAML tokens in order to authenticate and access protected resources. This is only possible if the credential data your application generates has a predictable pattern or is persistent across multiple sessions. Therefore, a good defense is to make sure that your software is configured to delete persistent credentials. Also, you can configure an active directory FS server to restrict permissions and access to only privileged workstations so that even if the credentials are forged it won’t work from the attacker’s computer.
Input Capture
Another option for getting user credentials is to use some type of input capture to record a user’s credentials when they are inputted. This is usually done through a keylogger, which is capable of recording keystrokes. However, it can be done through GUI input capture, web portal capture and capturing API calls that contain user credentials. The best mitigation is endpoint protection that can detect and quarantine potential malicious programs that may be recording input, however, this technique is difficult to detect because it usually takes advantage of system failures.
Man in the Middle (MITM)
In this type of attack, the attacker positions them between two or more networked devices and attempts to intercept traffic in order to gain credential information. The best defenses for this type of attack are to disable or remove legacy network protocols, encrypt sensitive information, and filter network traffic to prevent people from outside the environment from eavesdropping on conversations. A threat actor that commonly uses this technique is Kimsuky, a North Korean based group that typically focuses on think tanks and DPRK/nuclear-related targets.
Modify Authentication Process
Attackers also have the option of modifying the authentication mechanism of your organization directly to access user credentials or enable access to accounts of their choosing. This way they can access services or systems without going through valid accounts. The best defense against this is to restrict file and directory permissions to prevent people from being able to alter the authentication process. Additionally, you can use privileged account management, audit your local account permissions to look for any situation where an attacker could use one of these accounts to modify the authentication process.
Network Sniffing
This is when someone sits on the computer network and captures traffic while inspecting the data packets for any information of interest. Usually, this is done using a network interface that has been set to promiscuous mode, which allows it to passively access all data sent over the network. In this situation, they would be looking for any usernames or passwords being sent in cleartext. The best way to defend against this type of attack is to use encryption for sensitive information to ensure that it will be unreadable to anyone listening on the network. One of the most famous examples of this attack is the Emotet malware, which has been observed to hook network APIs to monitor network traffic.
OS Credential Dumping
This is the process of getting account login and password information from the operating system and software, usually in the form of a hash or cleartext password. Make sure your active directory permissions are secure to limit the number of cached plaintext credentials and consider disabling or restricting NTLM and Wdigest authentication. One threat actor that has been known to employ this technique to dump password hashes is leviathan.
Steal Application Access Token
Attackers can steal user application access tokens and use that to get credentials that will give access to systems or services. In order for this attack to work, it typically requires the user to grant access and this makes phishing one of the main attack vectors for delivering this attack. As a result, good mitigation for this is to train users not to authorize third-party applications that they don’t recognize. They should be taught to pay particular attention to the URL to be wary of URL redirects. Also, administrators can block end-user consent to Oauth applications and force administrative consent for all requests. You can also block end-user registration of applications by your users and this prevents people from being tricked altogether. You can find a step-by-step guide here.
Steal or Forge Kerberos Tickets
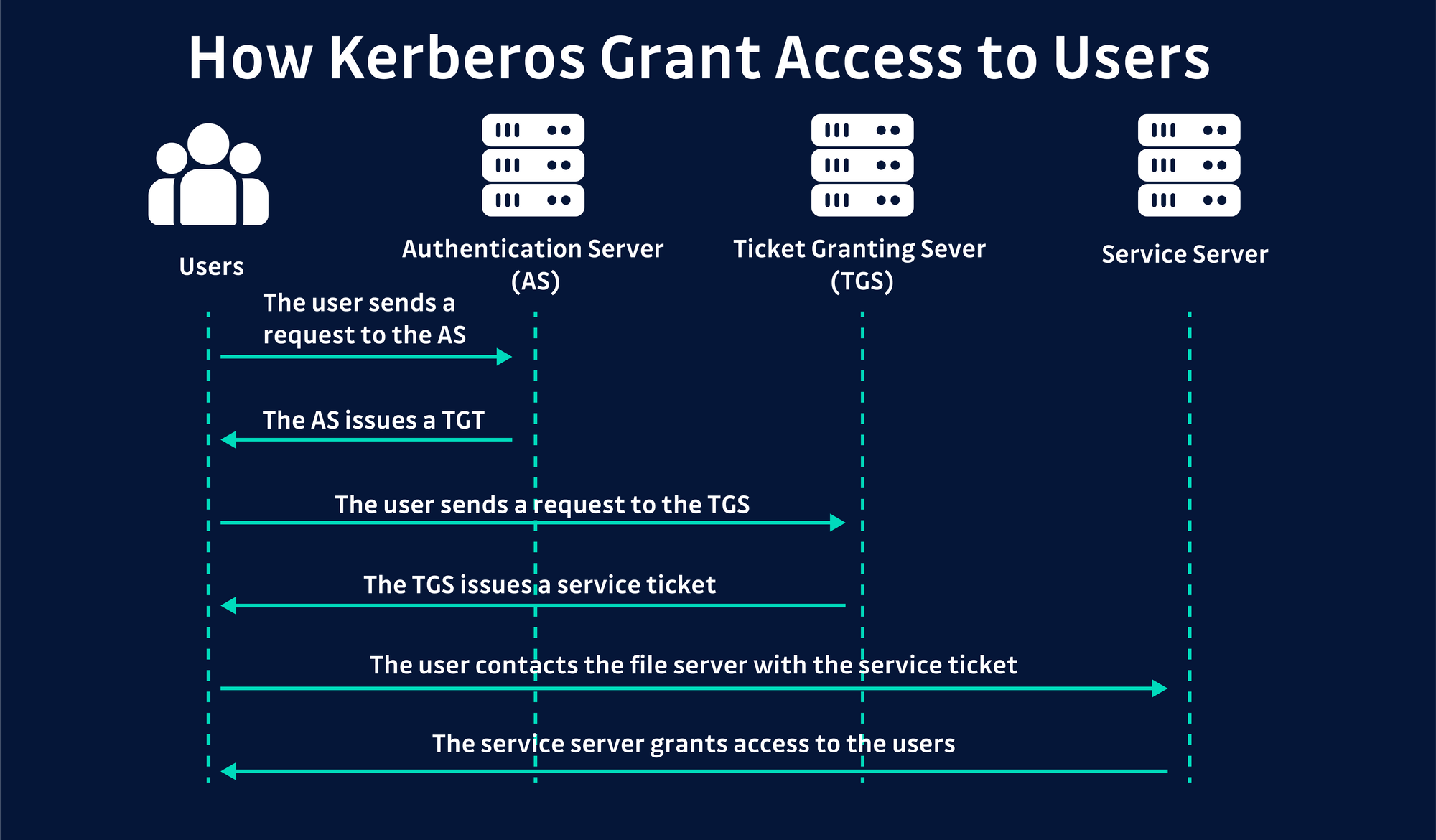
Here the attacker will either steal or create a fake Kerberos ticket and pass that to the authentication service in order to get access to network resources in what’s called a pass the ticket attack. To mitigate this, you should enable Kerberos encryption and rotate the KRBTGT password at least every 180 days or following a suspected data breach.
Steal Web Session Cookies
This is where an attacker steals a web application or service session cookie and uses them to gain access without the need for user credentials. This problem comes from the fact that some services use persistent cookies, which allow them to be reused by an attacker. To defend against this, you should configure your browsers or tasks to regularly delete persistent cookies and train users to identify phishing attempts where they are asked to enter credentials into a site with an incorrect domain. An appropriately named malware that is famous for this is called cookieminer, it’s a mac-based malware that targets information associated with cryptocurrency exchanges.
Two-Factor Authentication Interception
2FA or MFA is one of the best protection for user credentials, but it isn’t full proof. In this type of attack, an attacker tries to intercept the authentication mechanism and use it to authenticate as the user. The only way to defend against this is to teach users how to protect their authentication mechanisms such as their phone, smart card, hardware tokens etc. A threat group that has been known to use this technique is a Chinese-based threat group called chimera. They have been known to register alternate phone numbers for compromised users in order to intercept 2FA codes sent via SMS.
Unsecured Credentials
In this type of attack, an attacker will search compromised systems for insecurely stored user credentials. For example, if a user stores their passwords in a word file on their desktop, if an attacker compromises that machine they will have access to that password. Good defenses for this type of attack are to encrypt your sensitive information, use secure password managers and audit your environment for files containing passwords or other credentials.
General Tips for preventing Credential Access
Password Policy: The first tip that we can use across multiple techniques is having a good password policy. This means that you should mandate that passwords:
- Be 12-16 characters long
- Use lowercase, uppercase, numbers and special characters
- Rotate passwords every 90 days or if they are leaked in a data breach
2FA: Wherever you can enable 2FA to make sure that even if any of your user credentials are compromised there is another layer protecting their accounts.
Encryption: Properly encrypting user credentials in transit and at rest can prevent attackers from being able to use them even if they are able to get access to them.
Use least privilege on user accounts: In order to mitigate the damage caused by compromised user credentials, it’s important that you limit user account privileges. This way even if the account gets accessed by an attacker, they will be very limited in the information they can access and the actions they can perform.
Conclusion
Credential access is a set of techniques that attackers use to steal user credentials like account names and passwords. It’s dangerous because when an attacker can get access to a user account, they get access to all of the resources and privileges of that account. Also, it’s hard for the security controls of the organization to detect because it will just look like legitimate activity. The best way to prevent credential access is to have a strong password policy, enable 2FA and MFA, use encryption wherever possible and make sure that all of your accounts have the least amount of privilege and access needed to perform their business function. Another important aspect is that you want to monitor the web so that if any of your company’s passwords or password hashes are leaked you can reset them right away before someone gets a chance to use them against you. GitGuardian has a tool that can monitor GitHub for any accidental commits of company secrets and alert you right away. If you’re interested in this solution you can request a demo here.
This article is a guest post. Views and opinions expressed in this publication are solely those of the author and do not reflect the official policy, position, or views of GitGuardian, The content is provided for informational purposes, GitGuardian assumes no responsibility for any errors, omissions, or outcomes resulting from the use of this information. Should you have any enquiry with regard to the content, please contact the author directly.