On November 1st 2022, Dropbox has confirmed they suffered a data breach involving a bad actor gaining access to credentials, data, and other secrets inside their internal GitHub code repositories. This article will explain exactly what has happened, what has NOT happened, and what the potential impact is for Dropbox users.
How did the Dropbox Data Breach Happen?
A threat actor gained access to a GitHub account belonging to a Dropbox developer who had fallen for a phishing attempt. That compromised developer in turn provided the attacker with access to approximately 130 internal code repositories. Dropbox claims these code repositories were not connected to their core applications, instead that these repo's contained modified third-party libraries, internal prototypes, and other internal tools. While the repos may not be connected to their core applications, Dropbox did admit that some plain text secrets, including API keys and other credentials, were inside the code along with a “few thousand names and email addresses belonging to Dropbox employees”.
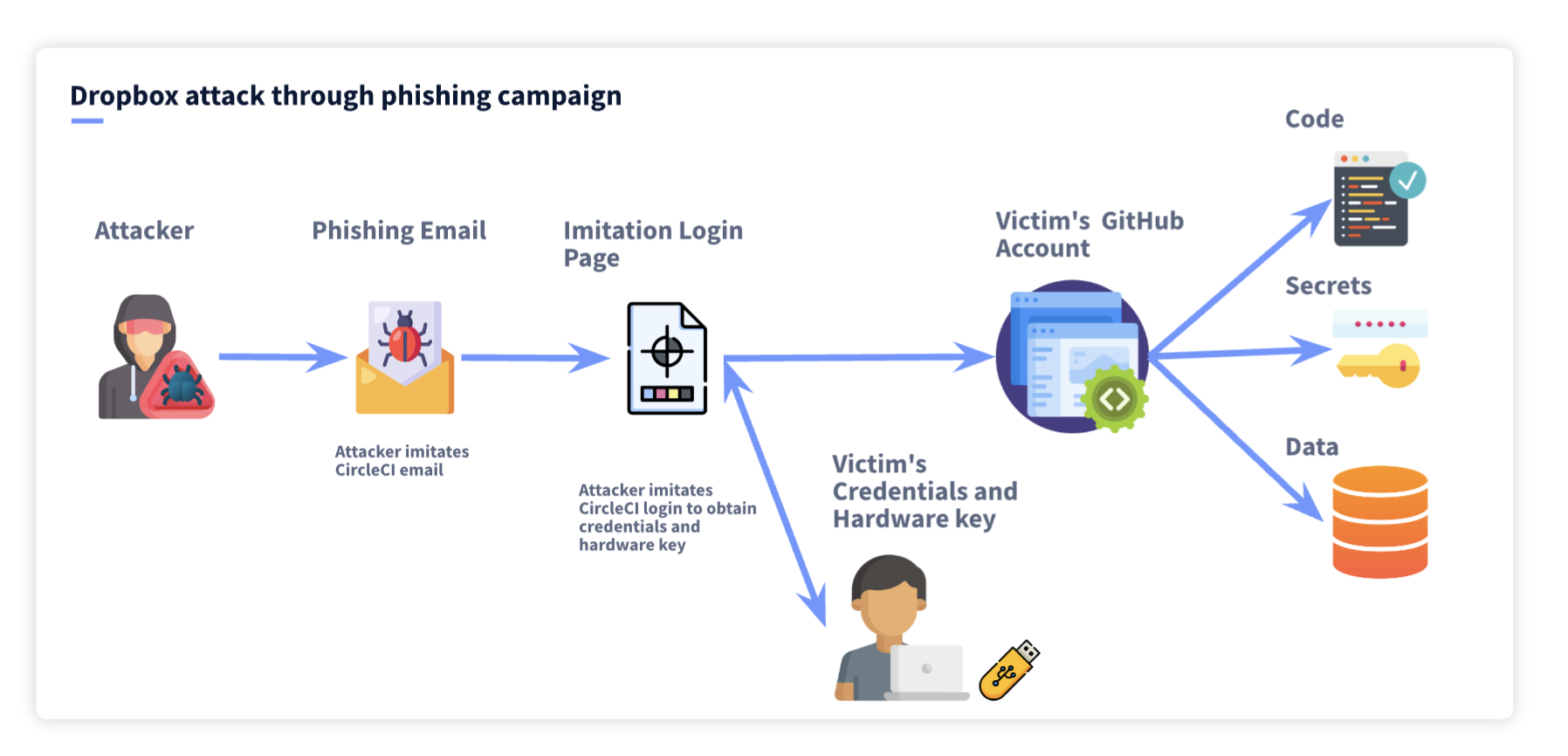
Step by step
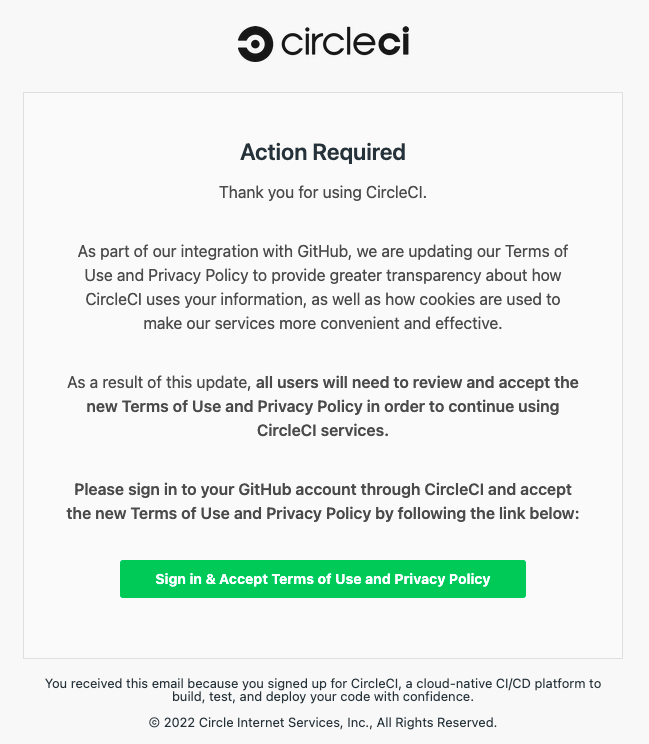
- The attacker sent a widespread phishing email imitating CircleCI, a popular CI/CD platform used internally by Dropbox.
- The phishing email took the victim to an imitation CircleCI login page where the user entered their GitHub credentials. CircleCi allowed users to log in with GitHub credentials.
- The imitation site also prompted users to enter a One-Time Password (OTP), generated by their hardware authentication key,
- The attacker would use the OTP and credentials provided by the user to gain access the victim's GitHub account.
- The attacker cloned 130 internal repositories, consisting of both public and private code.
- The next steps the attacker took are not immediately clear at this time, but in similar attacks, the attacker then searched for sensitive information like secrets to move laterally into more sensitive systems.
This attack wasn’t simply just a spray-and-pray phishing campaign that would come from a low-sophistication attack. The fact that the attacker seemingly knew Dropbox used CircleCI and was able to communicate with a hardware key and pass the one-time password to the attacker shows a higher level of sophistication.
“This attack shows how threat actors are conducting more and more sophisticated attacks to gain access to developers tools which are known to contain sensitive information” Mackenzie Jackson - Security Advocate
We also know that a very similar attack was happening around the same time in the wider GitHub community, also faking a CircleCI email and login screen, so it is suspected but not confirmed this was the same threat actor.
What Data was Hacked during this Security Breach?
The full extent of the breach is unknown at this time because the source code the hacker has stolen has not been released and Dropbox has not confirmed what system the API keys and other credentials could access.
Dropbox said in a statement “We believe the risk to customers is minimal. Because we take our commitment to security, privacy, and transparency seriously, we have notified those affected and are sharing more here,” and importantly they have also stated that “We also reviewed our logs, and found no evidence of successful abuse”.
This would indeed indicate a minimal risk to Dropbox customers but as we have seen in many other breaches, attackers can move laterally from internal tools into core infrastructure, at this stage there is no evidence to support this currently.
At the same time, Dropbox did disclose that" the code and the data around it also included a few thousand names and email addresses belonging to Dropbox employees, current and past customers, sales leads, and vendors".
Is Dropbox insecure?
Short answer, no.
While it is clearly a concern that plain text credentials and data are in Dropbox code repositories, this is not an issue isolated to Dropbox. At the same time, we can see that Dropbox has additional security measures in place, such as hardware tokens, that would have made this very difficult for attacks to succeed.
Finally, we also must consider that according to Dropbox, their logs showed no unknown access to critical systems, which shows the attack was caught in a timely manner. While this does not mean that Dropbox is immune to attacks it does show a clear trend that they take security seriously but do have some areas to improve on.
What should I do as a Dropbox user?
We would not see this breach as a reason to not be a Dropbox user. This is a good moment to reflect and ensure generally good security practices, such as regularly rotating passwords and setting up MFA on your dropbox account. Also, as always, be aware of any suspicious emails and unfamiliar URLs that end up in your email box.
The bigger problem
“Dropbox is the latest in an ever-growing list of companies such as Uber, Twitch, Samsung, and Nvidia that have had their internal code repositories targeted and exploited by hackers” Mackenzie Jackson - Security Advocate
What this attack shows is a continuation of an alarming trend of attackers targeting developer tools, in particular git repositories. As this breach shows, plain text secrets and credentials in source code are a huge problem. This can be seen in the recent Uber breach, or in the source code exposure of Samsung, Nvidia, Twitch, and many many more companies. It is crucial that companies scan their source code, including the full version history, for secrets to prevent attackers from being able to move from repositories into more critical infrastructure.
Sign up to scan your source code for free
"Any time a company has an incident involving stolen customer emails, there is a good chance that attackers will be launching phishing attacks sooner than later. Always be on guard for suspicious emails" - Dwayne McDaniel - Developer Security Advocate
If you are interested in other 2022 data breaches and attacks, you can find a detailed analysis of the Uber breach and of the Cloudflare breach.



![Shai-Hulud 2.0 Exposes Over 33,000 Unique Secrets [Updated Nov, 27]](/content/images/size/w600/2025/11/shai-hulud--2--1.png)





