On August 23, 2023, Sophos released its 2023 Active Adversary Report for Tech Leaders. The findings of their Incident Response team show a few disconcerting trends around the overall state of security posture, though there were some positive notes as well, especially when it comes to reacting to attacks. It is an illuminating report and deserves a full read, but we wanted to share a few highlights and expand upon some of the findings we thought were particularly relevant to GitGuardian's customers and our mission.
Leaked credentials take the lead for initial access
There are a lot of paths attackers can take to get a foothold in an organization. A quick look at the OWASP Top 10 suggests that poor credentials management has long been a route for attackers to gain access to environments. Unfortunately, according to the report, "For the first time, compromised credentials took the top spot in root causes. In the first six months of 2023, compromised credentials accounted for 50% of root causes, whereas exploiting a vulnerability came in at 23%." This fact is backed up by recent CISA data as well.
While it would be optimistic to believe this change was caused by patching exploitable vulnerabilities faster, what it really suggests is that the problem of secrets leakage is not getting better. This is in line with our annual findings in our State of Secrets Sprawl Report, where we saw an increase of over 67% in new secrets detected on GitHub public repos. This is not just from new developers or new organizations. In our Voice of the Practitioner Report, where we asked over 500 IT decision-makers about the state of their practice, 75% of respondents said they had experienced a secret leak.

Attackers find valid secrets in a variety of ways. Some gain access to certain services by brute force attacks or simply guessing the default password, as we saw with the recent Dell and VMware incidents. Phishing, and now Smishing, are also time-tested ways for attackers to gain access. There is a thriving market for stolen credentials on the dark web, as reported by DarkOwl. Adversaries are also always on the lookout for data breaches, as we saw with Samsung and Nvidia last year, where hardcoded credentials were baked into the source code, as it happens far too often.
Enable MFA today
One of the recommendations that the Sophos team made was to enable multifactor authentication, MFA. They report that MFA was missing in "39% of cases investigated so far in 2023". While not 100% foolproof, MFA can make it very hard to gain a foothold in a company. Phishing-resistant MFA, coupled with user training is no longer a nice to have. Fortunately, they also point to a maturing marketplace with more options for MFA continuing to become available, making it even easier for companies to implement.
Detecting and remediating secrets leaks are more important than ever
One of the best ways to ensure your credentials don't get stolen or leaked is to eliminate them wherever possible. If you can read an API key, webhook URL, or password in plaintext, then anyone else who ever gains access to that code or system can as well. The first major step toward removing secrets at scale is finding them. Just as importantly, you should start looking for any new secrets that enter your code. The GitGuardian Secrets Detection platform is designed to do exactly that.
First, when connecting a repository to GitGuardian for secrets scanning, the platform does a deep historical scan, looking through every branch and commit to alert you on the presence of over 390 specific types of credentials and dozens more generic secrets. The findings are organized and presented through the GitGuardian Workspace dashboard, your single point for coordinating the remediation process. Quickly see which secrets have tested as valid, which are public, and a lot of other critical data about each incident.
GitGuardian will, at the same time, start scanning for any newly added secrets that get added to the shared codebase. Get alerts that let you know what credential is at risk, where it is, and how long ago it was pushed. The GitGuardian dashboard makes it very easy to share that incident with the developer involved to get it resolved quickly and efficiently.
Developers and engineers can use ggshield, the GitGuardian CLI, to scan for secrets locally, stopping secrets from ever entering the git history in the first place. They can also use ggshield to scan any arbitrary file, such as logs and config, that might live outside of source control.
Dwell times and attack speeds
Another startling part of the report was how short dwell times have become recently. They found that the average overall dwell time, the amount of time a malicious actor is in the system before they are detected, was less than 16 days. The median time, the middle number in a set of values when those values are arranged from smallest to largest, was only 8 days.
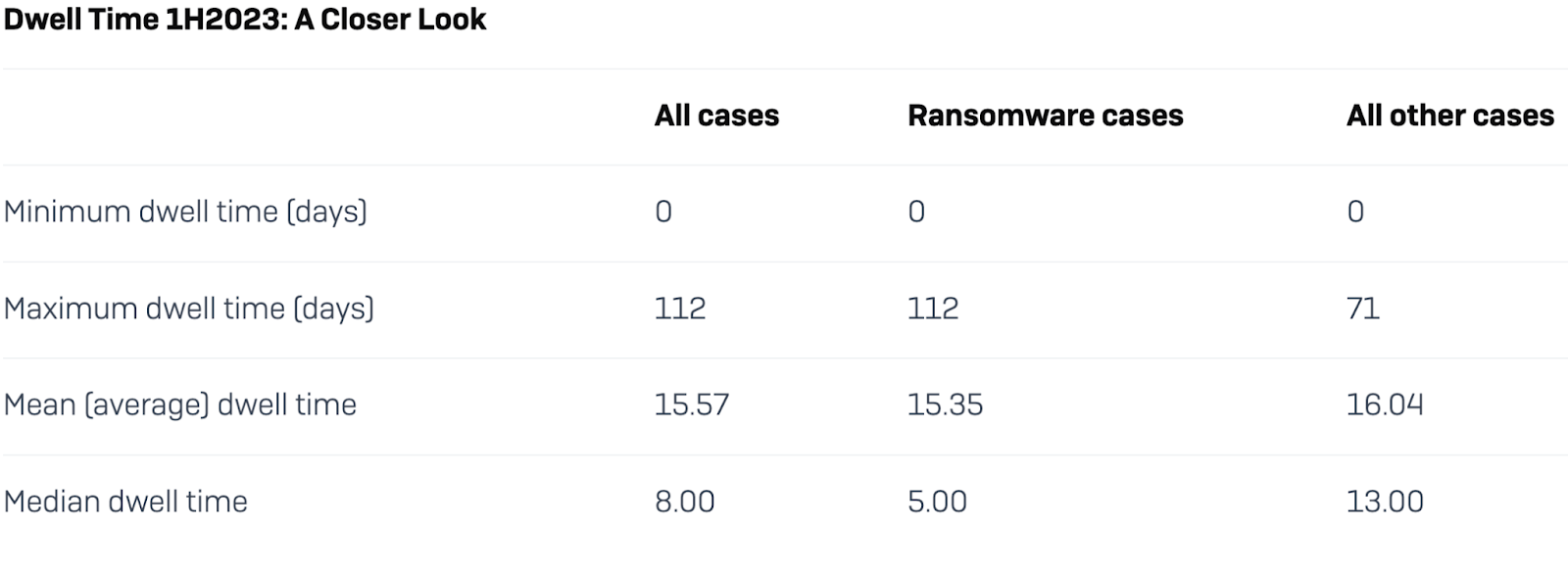
This is excellent news on the surface. We are collectively getting better as an industry at finding attackers quickly, especially when the average dwell time was just about 100 days as recently as 2018. Sophos attributes this, in part, to the success of "shifting left", moving the testing and detection earlier and more often in the DevOps cycle.
The bad actors know this as well and are speeding up their attacks overall. They reported that the median time for an attacker to gain access to Active Directory was 0.68 days, about 16 hours. Even while they are speeding up, they still are following a very well-established pattern of lateral expansion and privilege escalation. We can use that to our advantage.
Know about leaks and breaches right now
After gaining initial access, attackers will try to get into any other systems they can find. The easiest path is to find the key lying about. Attackers will very often scan any and all text files for anything resembling an API key, password, or certificate and immediately try it out. Deploying decoy credentials can give you a serious advantage here, which is why we created GitGuardian Honeytoken.
As they are real AWS tokens, attackers have no way of knowing they are walking into a trap. When an attacker does attempt to use one, you get an alert giving you the IP address, user agent, attempted action, and timestamps. These data points will help you quickly mount a defense when a breach or leak happens.
Adding GitGuardian Honeytoken into your code security practices can help you cut your dwell times down considerably, maybe even down to minutes.
Locking down privileges
The other common tactic used by bad actors is granting themselves more and more permissions. This is made easier for the attacker when credentials are not properly scoped and when too wide of access is granted. As we saw in the recent report from a bug bounty hunter who attacked a car company and found GitHub admin access to over 30 different organizations, it is all too easy to use root or admin user accounts or everything. This makes it all that more important to use MFA with these powerful passwords.
It can also be easy to overlook misconfigurations that would, for example, give sudo rights to a user, allowing privilege escalation attacks or granting a container privileged rights. These are just two of the things we check for in GitGuardian Infra as Code Security. The nature of IaC means a misconfiguration once might be propagated to dozens or hundreds of instances. Make sure you are double-checking for common missteps before deploying those Terraform or CloudFormation configurations.
Let's make it hard for attackers to win
The Sophos report has many other findings worth your time, including that only 9.2% of companies knew their data was definitely not exfiltrated, which is a huge increase from 1.3% in 2022. Overall though, it shows there is much more we can do to combat attackers who want to steal our data and machine resources. While there is no single best path to bulletproof security, we do know there are some common steps that many organizations take to tackle secrets management. Given the data is a good place to start. We call it the Secrets Management Maturity Model, and we intend it to be a roadmap to improving your code security posture.
Unfortunately, malicious actors and human error will likely always be with us. GitGuardian is here to help with your overall code security: We can empower your prevention and detection of hardcoded secrets. With GitGuardian Honeytoken, you can take a more proactive defensive posture, leaving decoy credentials for malicious actors to exploit at their own peril. We will also make it easy to scan for IaC misconfigurations locally or throughout your GitHub and GitLab repos automatically.
We are here to help you on your security journey.